- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
03-功能服务器
展开查看详情
1 .CS 5412/Lecture 3 Programming an I o T System Ken Birman Spring, 2019 http://www.cs.cornell.edu/courses/cs5412/2019sp 1
2 .How do we “Program” The I o T Cloud? This is a very rapidly evolving and exciting question! To give some context, let’s start with the same question as of 2005, to understand the answer today, but also the underlying reasons. But the quick summary is: very few things work well, and we need to stick primarily to techniques that industry is prioritizing and supporting. http://www.cs.cornell.edu/courses/cs5412/2019sp 2
3 .Programming prior to 2005 In the early period of cloud computing, there was a (mistaken) tendency to view the cloud like a very big distributed computing system. So people learned to program on smaller clusters, then joined companies like Amazon, Yahoo!, eBay, and so forth, and took this knowledge along. But in fact at cloud scale, those smaller techniques don’t work well! http://www.cs.cornell.edu/courses/cs5412/2019sp 3
4 .big web companies around 2005 To maximize concurrency, they started by spreading the work of building web responses over a set of side-by-side tier-one services. The next challenge was to optimize the -services. Remember Jim Gray’s paper! Some -services can adopt CAP, because for them, “weak consistency is safe”. Some can use Paxos /SMR, like “one-shot transactions on a single shard.” Some use transactional database solutions, but on sharded data. http://www.cs.cornell.edu/courses/cs5412/2019sp 4
5 .What happens when they gEt it wrong? Convoy effect : If some service runs slow, often a large amount of concurrent work “queues up” waiting for it and we lose all concurrency. Reboot storms : When such a big overload arises that everything times out, crashes, and restarts. Inconsistency storms : When a system that “normally” runs with good cached data suddenly finds that all cached data is extremely stale. http://www.cs.cornell.edu/courses/cs5412/2019sp 5
6 .Over time, this reshaped the cloud! In lecture 1 we saw how companies like Amazon invented the -service model. Now we can see that they had to go much further. They needed new families of -services, and ways to teach people to build them. Even with this, those -services can become hot-spots. They used special hardware accelerators and design tools to program the new hardware. This work wasn’t easy and required unusual expertise and luck. http://www.cs.cornell.edu/courses/cs5412/2019sp 6
7 .The issue this creates Today’s cloud-scale solutions really work well! But you really need to use them in the way the vendor anticipated. You generally download a “story book” that describes some end-user need and how the company helped solve it, and comes with sample code. The code mostly glues together existing services. Then you download that code and customize it to transform it into your own solution, for your case. http://www.cs.cornell.edu/courses/cs5412/2019sp 7
8 .Can you fully customize the first tier? In the 2006-2015 period or so, we saw increasingly sophisticated products emerge to help automate the creation of web pages. So often, the first tier is just one of these vendor-supplied solutions and you use some form of special design tool to tell it what you are hoping to do. For cases where this isn’t a good solution, we use a “hybrid cloud” in which applications inside the client company issue cloud requests directly. http://www.cs.cornell.edu/courses/cs5412/2019sp 8
9 .Hybrid Cloud (Web Services Model) Basically, the cloud vendor offers cloud-hosted services via APIs you can call via RPC from a networked application. This runs on HTTPS. So you can extend an application running inside your company to make requests to services up in the cloud, with good security. Then any style of application development your company uses becomes cloud-enabled. But it still requires a certain level of expertise. http://www.cs.cornell.edu/courses/cs5412/2019sp 9
10 .Internet of Things broke the model! With IoT, we encounter a slew of new issues. Customers lack a high quality way to securely manage huge numbers of IoT devices, which are often “dumb” sensors. These devices need to be actively managed, like to update their firmware each time a patch is issued, to protect them against hackers, … There are thousands of devices and each has its own special, vendor-defined options for remote control. They often need real-time responses, large machine-learned knowledge bases that are frequently updated, fault-tolerance and consistency. http://www.cs.cornell.edu/courses/cs5412/2019sp 10
11 .Canon EOS Rebel Camera… This is Ken’s SLR camera. What “events” can it generate? You don’t normally think of a camera as a device…. Now we want to imagine that this camera is being used as a cloud IoT peripheral with a stable source of power. Some possible events: http://www.cs.cornell.edu/courses/cs5412/2019sp 11 Event Meaning Issues On/Off/Idle Power mode When turned on, must authenticate NewIMG Took a photo Should we download it? How fast is the link? StorageWarning Low on space Which images to delete FocusWarning Dirty sensor Something is preventing auto-focus from working.
12 .An IoT Event would… Come from some specific device, securely attached to the cloud and with a clearly defined owner who bought it and services it. Have a device type and an event type and “tags” defining event meta-data , which is a term that just means that the event might talk about data but not include the raw data. Why not include the data in every event? Typical photo might be 3MB in size. A video could be 1GB or more. But sensors rarely have ultra-fast connections. http://www.cs.cornell.edu/courses/cs5412/2019sp 12
13 .In an IoT world… A typical end-user application (think of a hospital, or a small city, or a smart highway, or a smart farm) might have thousands or tens of thousands of smart sensors, of many kinds The devices would generally not be very smart, but each has its own superpowers, like on-camera storage for images, or image compression. Different vendors/models: many “user manuals” We have limited battery lifetimes and bandwidth to contend with, and perhaps can’t download every image or video. Some data may be more valuable than others. http://www.cs.cornell.edu/courses/cs5412/2019sp 13
14 .Programability You can’t run code right on the sensor itself: they aren’t very smart. You could build a specialized solution for each class of sensor, but this wouldn’t be cost-effective So companies wanting to be big players in IoT have begun to invent a new IoT-oriented first tier. http://www.cs.cornell.edu/courses/cs5412/2019sp 14
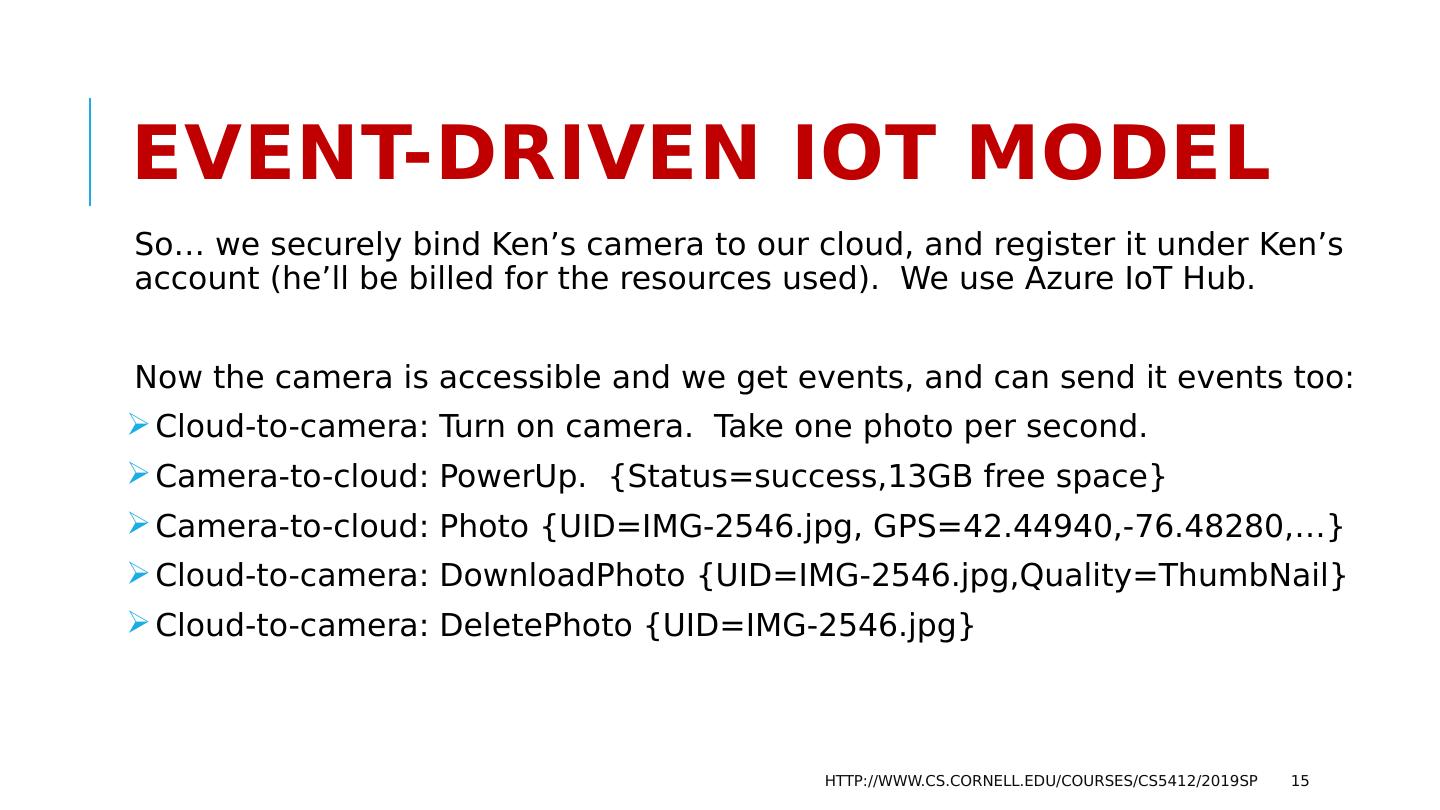
15 .Event-Driven IoT model So… we securely bind Ken’s camera to our cloud, and register it under Ken’s account (he’ll be billed for the resources used). We use Azure IoT Hub. Now the camera is accessible and we get events, and can send it events too: Cloud-to-camera: Turn on camera. Take one photo per second. Camera-to-cloud: PowerUp . {Status=success,13GB free space} Camera-to-cloud: Photo {UID=IMG-2546.jpg, GPS=42.44940,-76.48280,…} Cloud-to-camera: DownloadPhoto {UID=IMG-2546.jpg,Quality= ThumbNail } Cloud-to-camera: DeletePhoto {UID=IMG-2546.jpg} http://www.cs.cornell.edu/courses/cs5412/2019sp 15
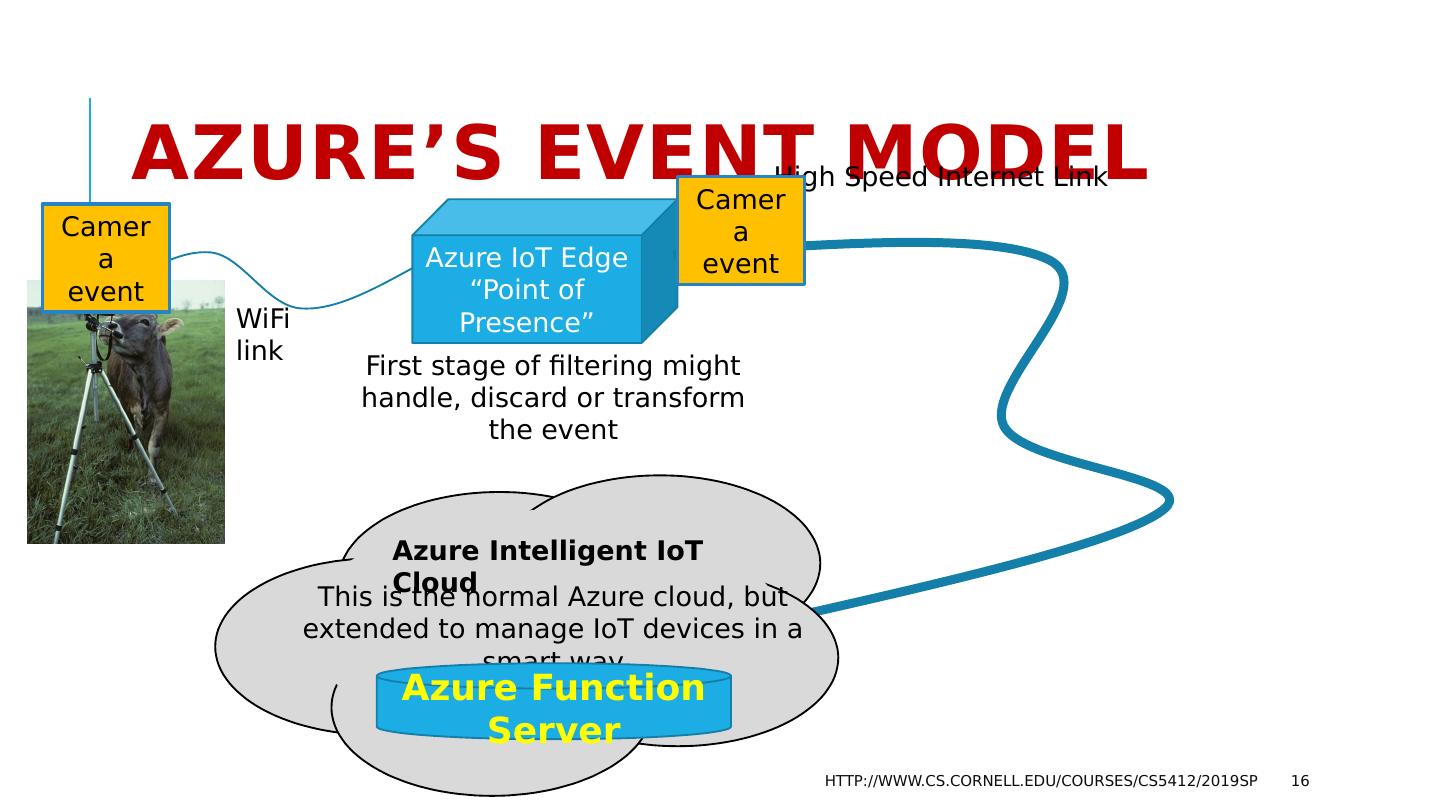
16 .Azure’s Event Model http://www.cs.cornell.edu/courses/cs5412/2019sp 16 WiFi link Azure IoT Edge “Point of Presence” High Speed Internet Link Azure Intelligent IoT Cloud This is the normal Azure cloud, but extended to manage IoT devices in a smart way Azure Function Server First stage of filtering might handle, discard or transform the event Camera event Camera event
17 .Function Servers A very simplified way to create event-driven first-tier solutions. In Amazon, called Amazon Lambda Microsoft calls it the Azure Function Server The server is an elastic set of machines that host very inexpensive containers running Linux or some other operating system of your choice. You provide simple programs that get triggered by events. http://www.cs.cornell.edu/courses/cs5412/2019sp 17
18 .Function Model The idea, then, is to write code to handle these functions, for “both sides” of the connection. Since the device itself is probably quite specialized and “dumb”, one side would be a kind of device driver that knows how to talk to it. Then the cloud would be the other side of the connection. http://www.cs.cornell.edu/courses/cs5412/2019sp 18
19 .How the event is passed to the function When an event occurs, a new instance of the event handling function you registered will be launched in a “clean” state. The event itself is available either as program arguments, or via an API You can also register a shell script if you wish. http://www.cs.cornell.edu/courses/cs5412/2019sp 19
20 .One function can handle multiple events This is a convenient way to avoid having to register hundreds of functions. But the handler for any single event is normally very simple and short. In Azure, the Visual Studio 2017 IDE can create a skeleton for you in C# or other .NET languages, with all the needed logic “sketched out”. Then you would just extend the skeleton with specific logic of your own. http://www.cs.cornell.edu/courses/cs5412/2019sp 20
21 .Example logic? Your function could be passed a thumbnail photo, then use a photo-analysis -service to decide whether the photo Has any “content”. A farm photo with no animals might not be useful. Is of “interest”. Here, you could use a pre-trained machine learning classifier that has learned which kinds of photos interest you. Then if the photo seems to be interesting, you could download the full version. If not, you might still leave the dull ones on the camera just in case. http://www.cs.cornell.edu/courses/cs5412/2019sp 21
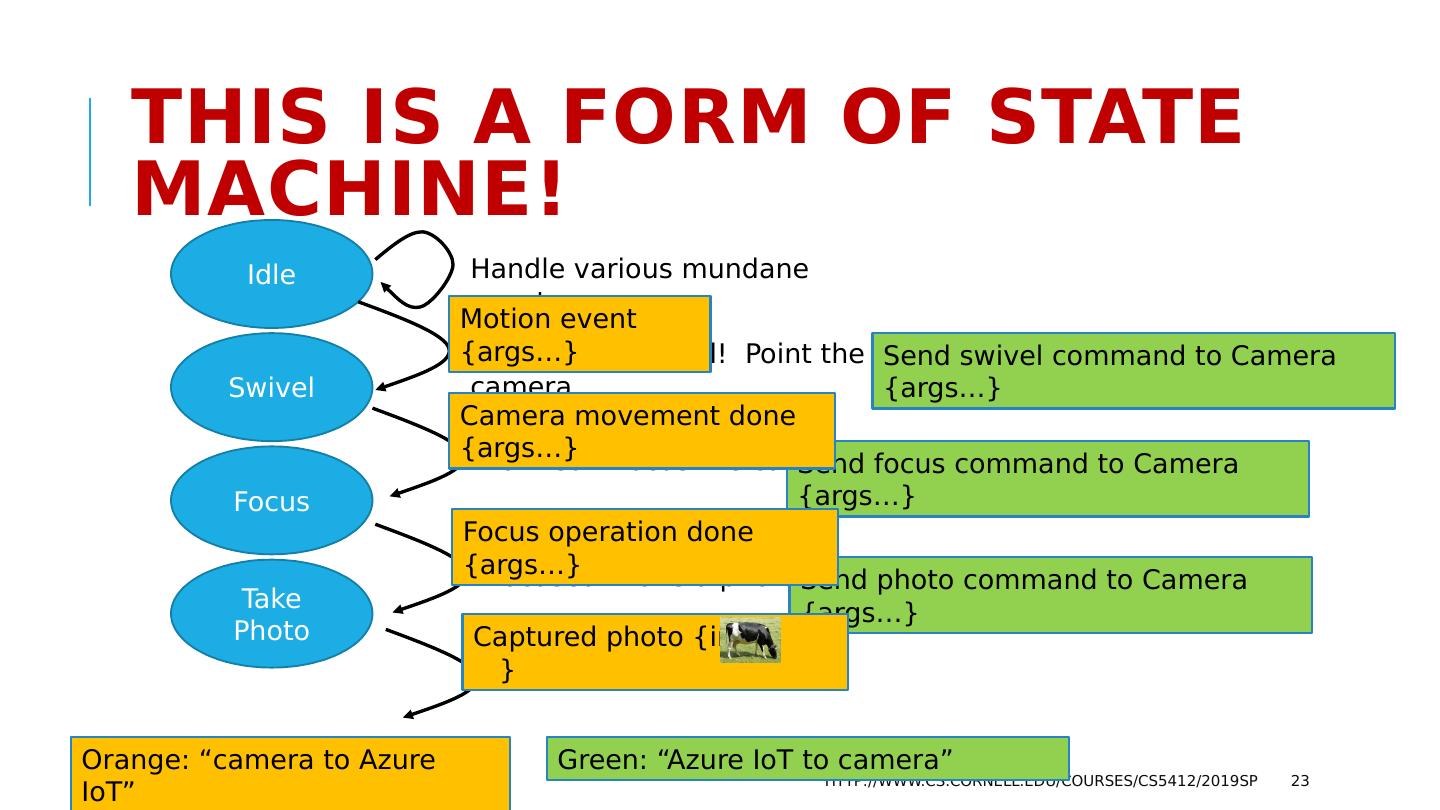
22 .Fancier Case: Point, Focus and Shoot Suppose that some event occurs: “Animal motion detected”. This will cause us to swivel the camera. When the camera is pointed towards the location, we should focus. When the focus converges, we shoot a photo. Now the thumbnail is sent to the server. If the photo is considered interesting, we’ll download it. http://www.cs.cornell.edu/courses/cs5412/2019sp 22
23 .This is a form of state machine! http://www.cs.cornell.edu/courses/cs5412/2019sp 23 Idle Swivel Focus Take Photo Handle various mundane events Movement sensed! Point the camera Send swivel command to Camera { args …} Motion event { args …} Pointed! Focus the camera Send focus command to Camera { args …} Camera movement done { args …} Focused! Take a photo Send photo command to Camera { args …} Focus operation done { args …} Captured photo {info, } Orange: “camera to Azure IoT” Green: “Azure IoT to camera”
24 .Building a state machine with functions. A function is “stateless”, which is a confusing idea for many people. Keep in mind: a function is simply an event-triggered program. It can access Azure -services (plus you can add extra -services). And so it can do persistent updates to the state in those -services. To implement a state machine, even a simple one, we would have to keep the state itself external to the function: load it, then update it, then store it. http://www.cs.cornell.edu/courses/cs5412/2019sp 24
25 .… the key-value store is the best option. An atomicity issue arises if concurrent events trigger two functions that try to make conflicting updates to the state machine state. If we solve this by adding locks to the key-value store, Jim Gray’s scalability warning applies! Solution? We use a kind of “atomic” conditional key-value put . http://www.cs.cornell.edu/courses/cs5412/2019sp 25
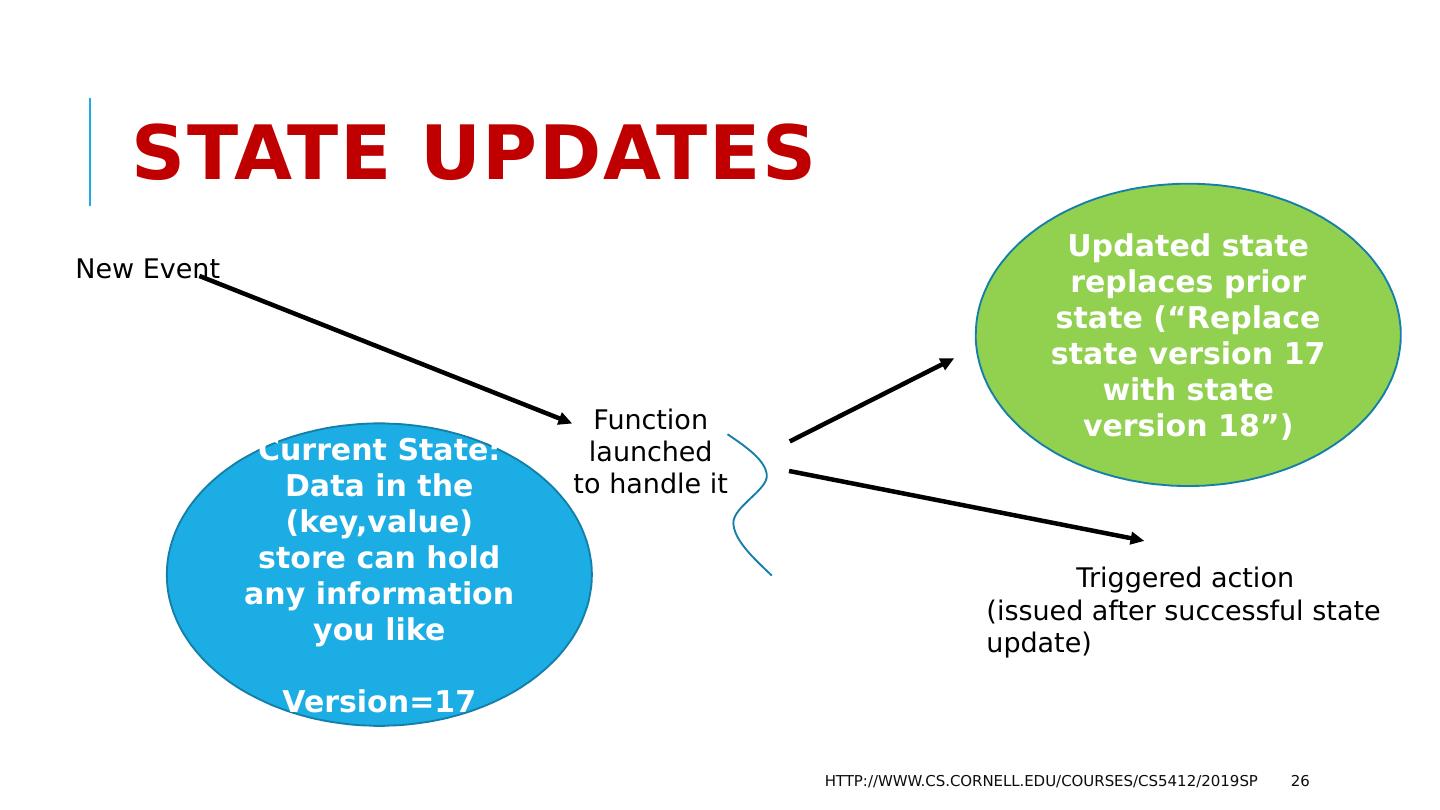
26 .State Updates http://www.cs.cornell.edu/courses/cs5412/2019sp 26 Current State: Data in the ( key,value ) store can hold any information you like Version=17 New Event Function launched to handle it Triggered action (issued after successful state update) Updated state replaces prior state (“Replace state version 17 with state version 18”)
27 .But you can also see that this is hard You wouldn’t encode long sequences of complex logic this way. So a function service has handlers limited to very simple direct actions, or very simple sequences. Anything more complex needs to be implemented in a -service http://www.cs.cornell.edu/courses/cs5412/2019sp 27
28 .How will you know which to use? Draw a diagram of the state machine you’ll need. If it only has a very small sequences of simple steps, implementing them purely with functions and saving state in a -service will be fine. But if the state machine seems at all complex, you’ll probably need to either build your own -service, or build a new -service that leverages existing ones but still “holds” the longer-term stateful interactions. http://www.cs.cornell.edu/courses/cs5412/2019sp 28
29 .Existing -Services Functions often use Message bus (pure notification) and queues (stored until deleted) File systems, key-value storage (with conditional updates!) Services for compressing big objects, photo segmentation & tagging Deduplication services (“did I already know this?”) Blockchains (like a tamper-proof audit trail, append-only) …. Easy to dream up more of them specialized for particular needs, but they might not be easy to implement! http://www.cs.cornell.edu/courses/cs5412/2019sp 29