- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 视频嵌入链接 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
Data Driven Payment Risk
Data Driven Payment Risk
展开查看详情
1 .Data Driven Payment Risk Sync Shan
2 .Agenda Payment Risk Introduction Real time evaluation Post transaction Risk Management
3 .Risk Assessment in Transaction Flow On-Boarding Pre -Auth Post - Auth Capture Risk & Fraud Blacklist Risk assessment Money Settlement Anti Money Laundry Stolen Financial based on auth Account Takeover Pre - Transaction Transaction Post - Transaction Auth Pre - Capture Accounts review KYC CVV/AVS verification Risk assessment Dispute management Compliance 3DS Fraud ring Buyer account review Seller account review Anti Money Laundry Risk in Marketplace
4 .Payment Risk Platforms Logs, Events, DBs Variable Center Decision Platform Action Analysis Profile Data Data Platform Streaming Logs & Feature Platform monitor for Transaction Data risk decision streaming Model Engine Action flow Blacklist Platform Behavioral Data AI platform Policy & Blacklist Data structure Business rule Account Linkage Logs, Events & DB Analysis Device Data A/B testing Location Based graph Profiles Customer Model & rule Service Service evaluation & Rule Engine optimization Third-party Risk Data Historical data Aggregate
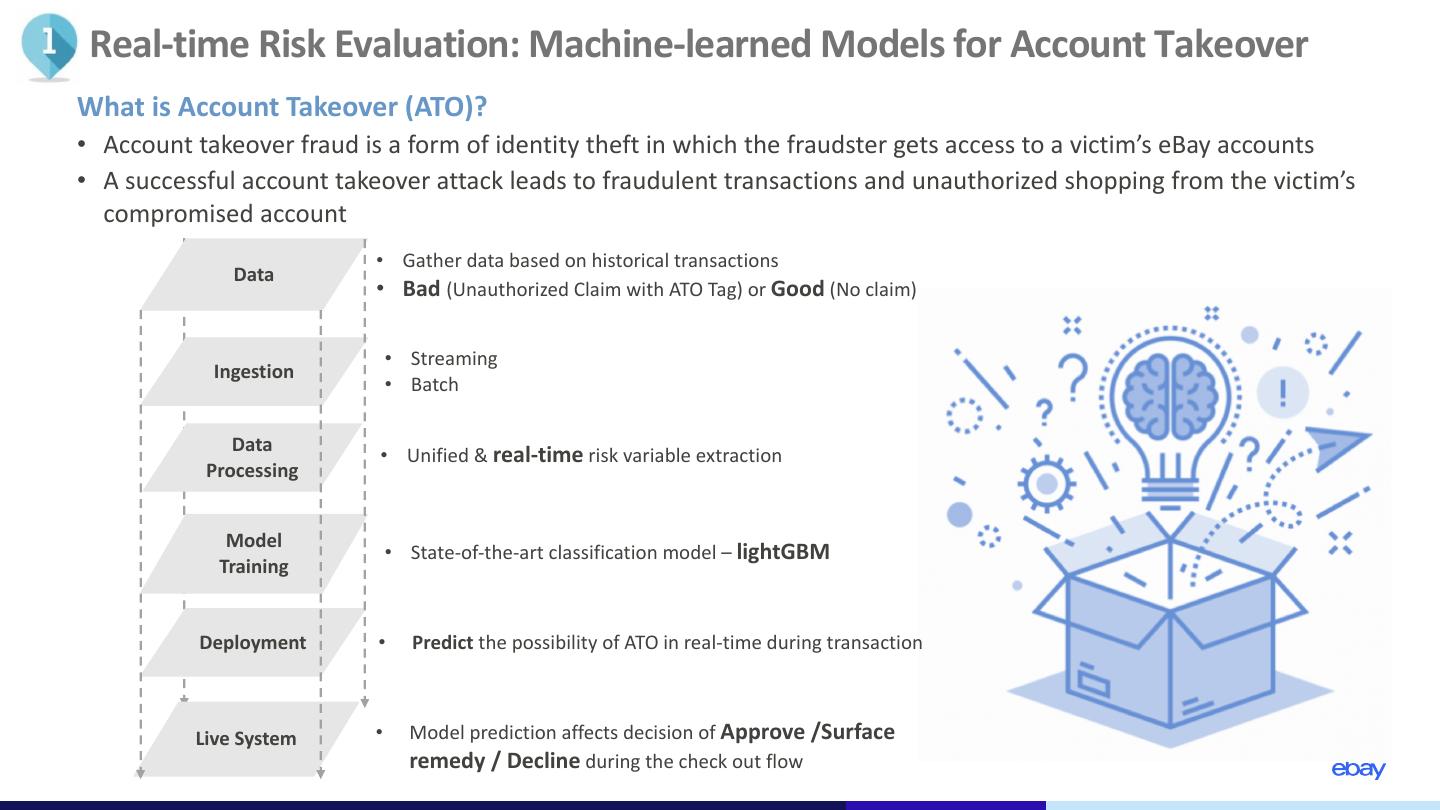
5 . Real-time Risk Evaluation: Machine-learned Models for Account Takeover What is Account Takeover (ATO)? • Account takeover fraud is a form of identity theft in which the fraudster gets access to a victim’s eBay accounts • A successful account takeover attack leads to fraudulent transactions and unauthorized shopping from the victim’s compromised account • Gather data based on historical transactions Data • Bad (Unauthorized Claim with ATO Tag) or Good (No claim) • Streaming Ingestion • Batch Data • Unified & real-time risk variable extraction Processing Model • State-of-the-art classification model – lightGBM Training Deployment • Predict the possibility of ATO in real-time during transaction Live System • Model prediction affects decision of Approve /Surface remedy / Decline during the check out flow
6 .Integrate Batch & Streaming Infrastructure for Real-time Risk Variable Extraction Velocity Aggregation Engine Core Storage NRT Pipeline Kafka/ Pre-auth Checkpoint Flink Message Variable Variable Sources Consumer Ingestion Aggregate Engine Couchbase NRT storage Ingest Query ATO Model Layer Engine Service Batch Pipeline Oracle Data Spark Batch ETL RT storage Warehouse Processing Transaction Variables Variables Ingestion Fetch TPS Ingestion 99P Fetch 99P 5M/day 10B/day 2B/day 150 <100ms <100ms
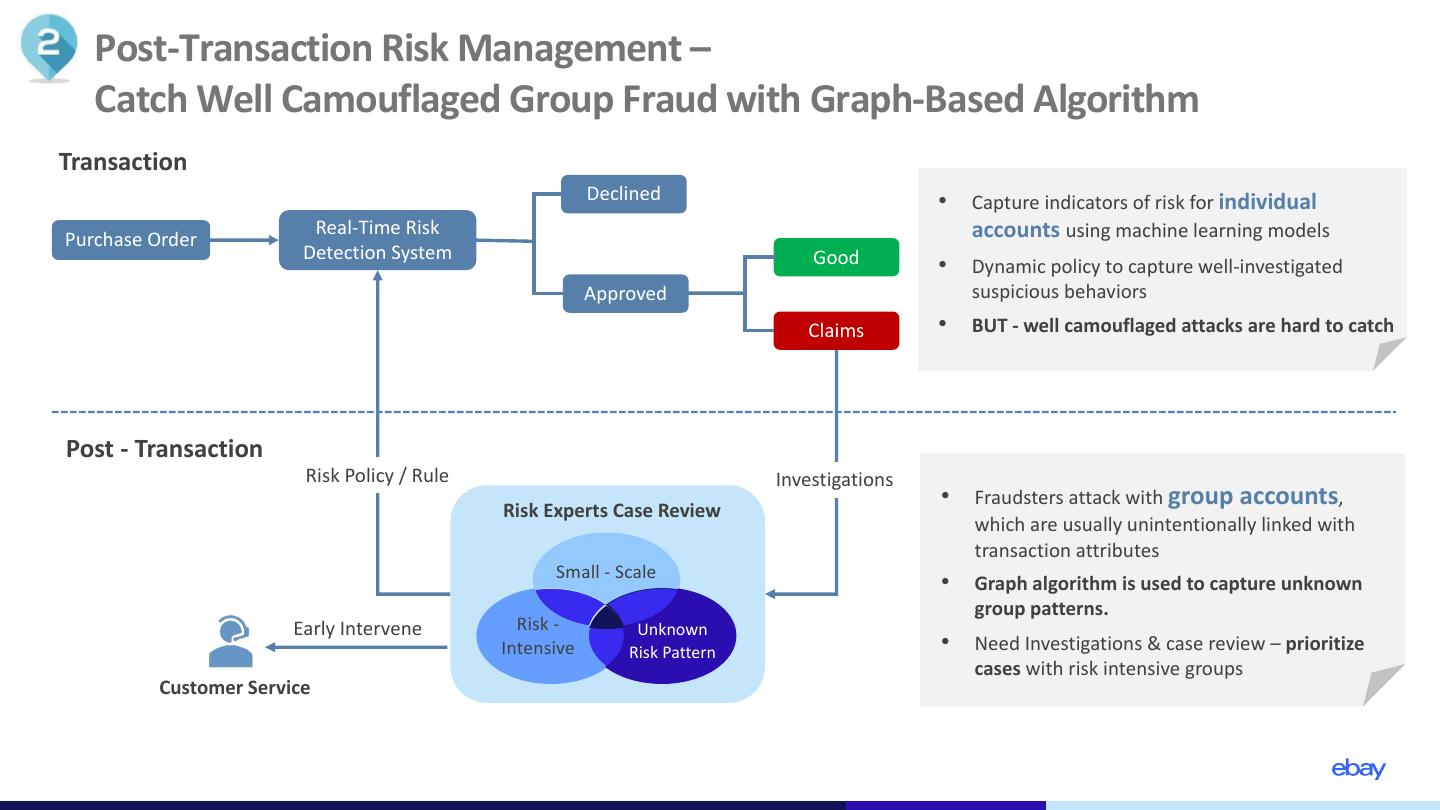
7 . Post-Transaction Risk Management – Catch Well Camouflaged Group Fraud with Graph-Based Algorithm Transaction Declined • Capture indicators of risk for individual Real-Time Risk accounts using machine learning models Purchase Order Detection System Good • Dynamic policy to capture well-investigated Approved suspicious behaviors Claims • BUT - well camouflaged attacks are hard to catch Post - Transaction Risk Policy / Rule Investigations • Fraudsters attack with group accounts, Risk Experts Case Review which are usually unintentionally linked with transaction attributes Small - Scale • Graph algorithm is used to capture unknown group patterns. Early Intervene Risk - Unknown Intensive Risk Pattern • Need Investigations & case review – prioritize cases with risk intensive groups Customer Service
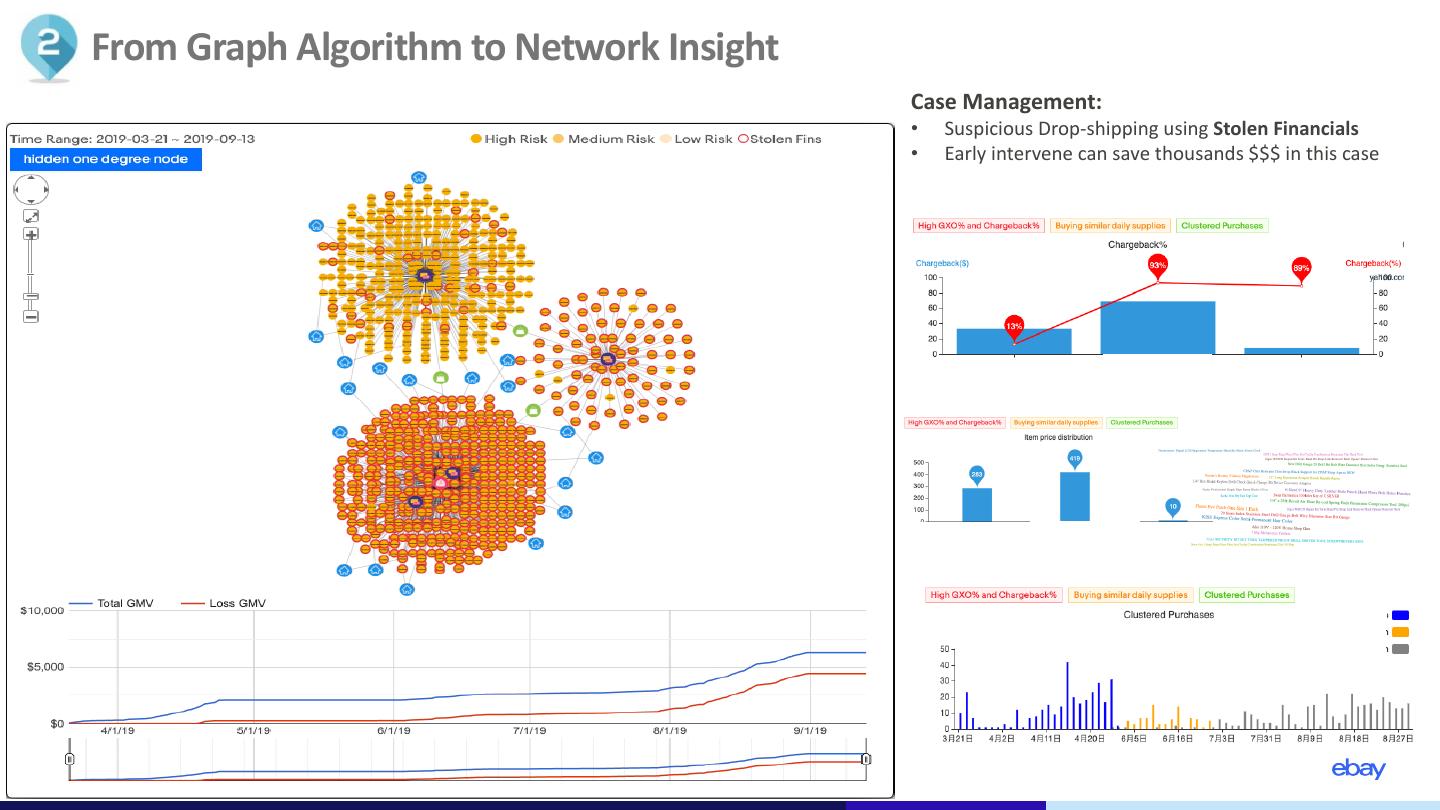
8 .From Graph Algorithm to Network Insight Case Management: • Suspicious Drop-shipping using Stolen Financials • Early intervene can save thousands $$$ in this case
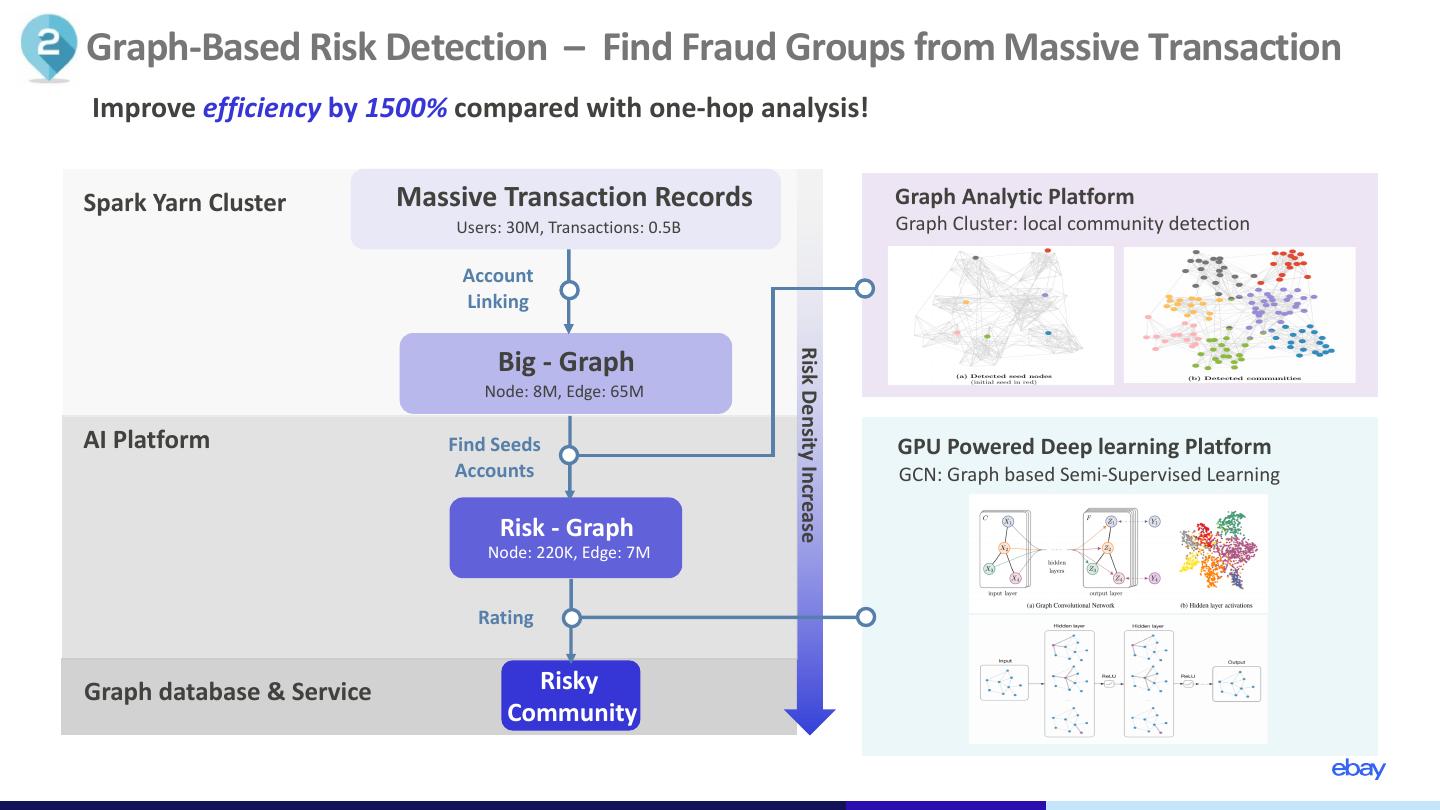
9 .Graph-Based Risk Detection – Find Fraud Groups from Massive Transaction Improve efficiency by 1500% compared with one-hop analysis! Spark Yarn Cluster Massive Transaction Records Graph Analytic Platform Users: 30M, Transactions: 0.5B Graph Cluster: local community detection Account Linking Big - Graph Risk Density Increase Node: 8M, Edge: 65M AI Platform Find Seeds GPU Powered Deep learning Platform Accounts GCN: Graph based Semi-Supervised Learning Risk - Graph Node: 220K, Edge: 7M Rating Graph database & Service Risky Community
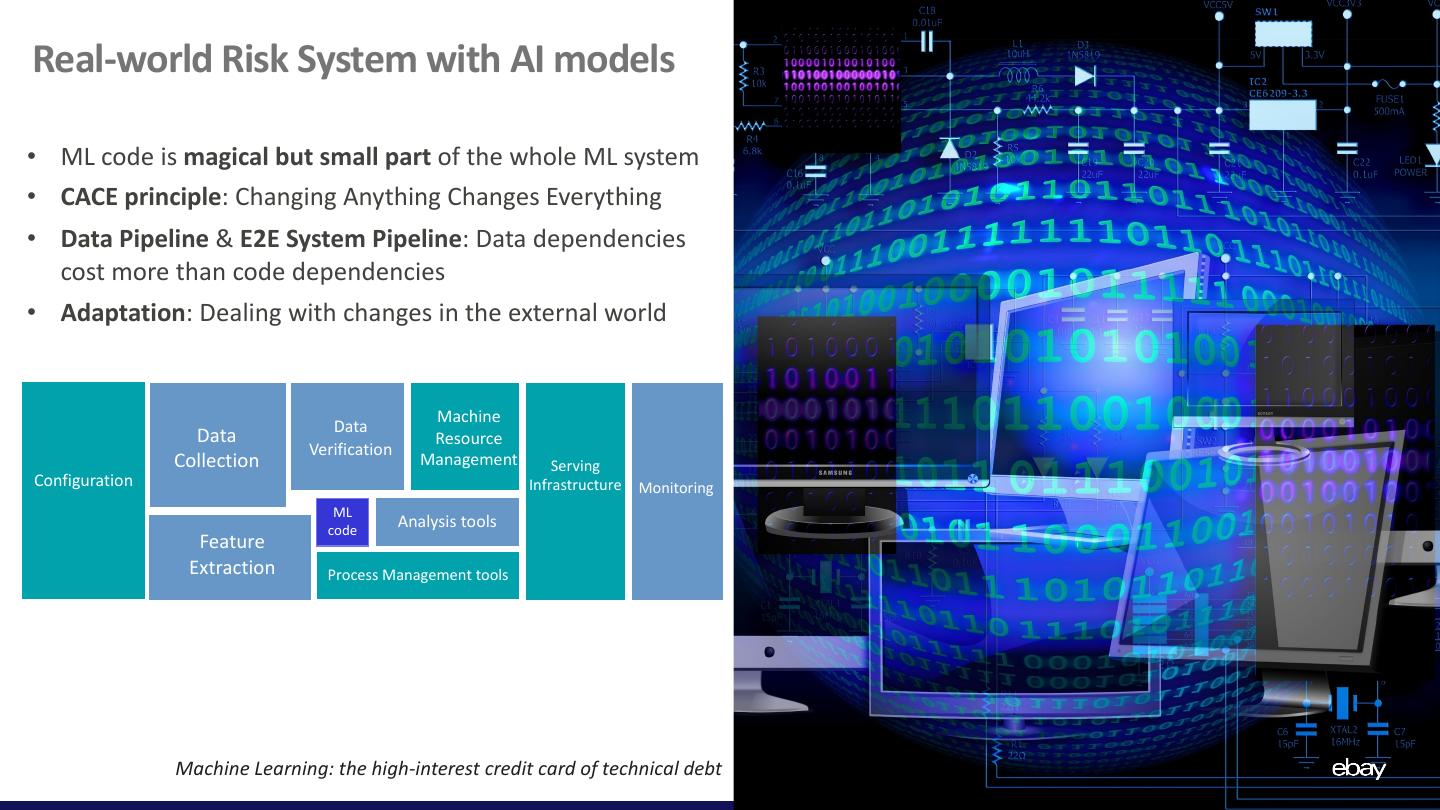
10 .Real-world Risk System with AI models • ML code is magical but small part of the whole ML system • CACE principle: Changing Anything Changes Everything • Data Pipeline & E2E System Pipeline: Data dependencies cost more than code dependencies • Adaptation: Dealing with changes in the external world Machine Data Data Resource Verification Collection Management Serving Configuration Infrastructure Monitoring ML code Analysis tools Feature Extraction Process Management tools Machine Learning: the high-interest credit card of technical debt
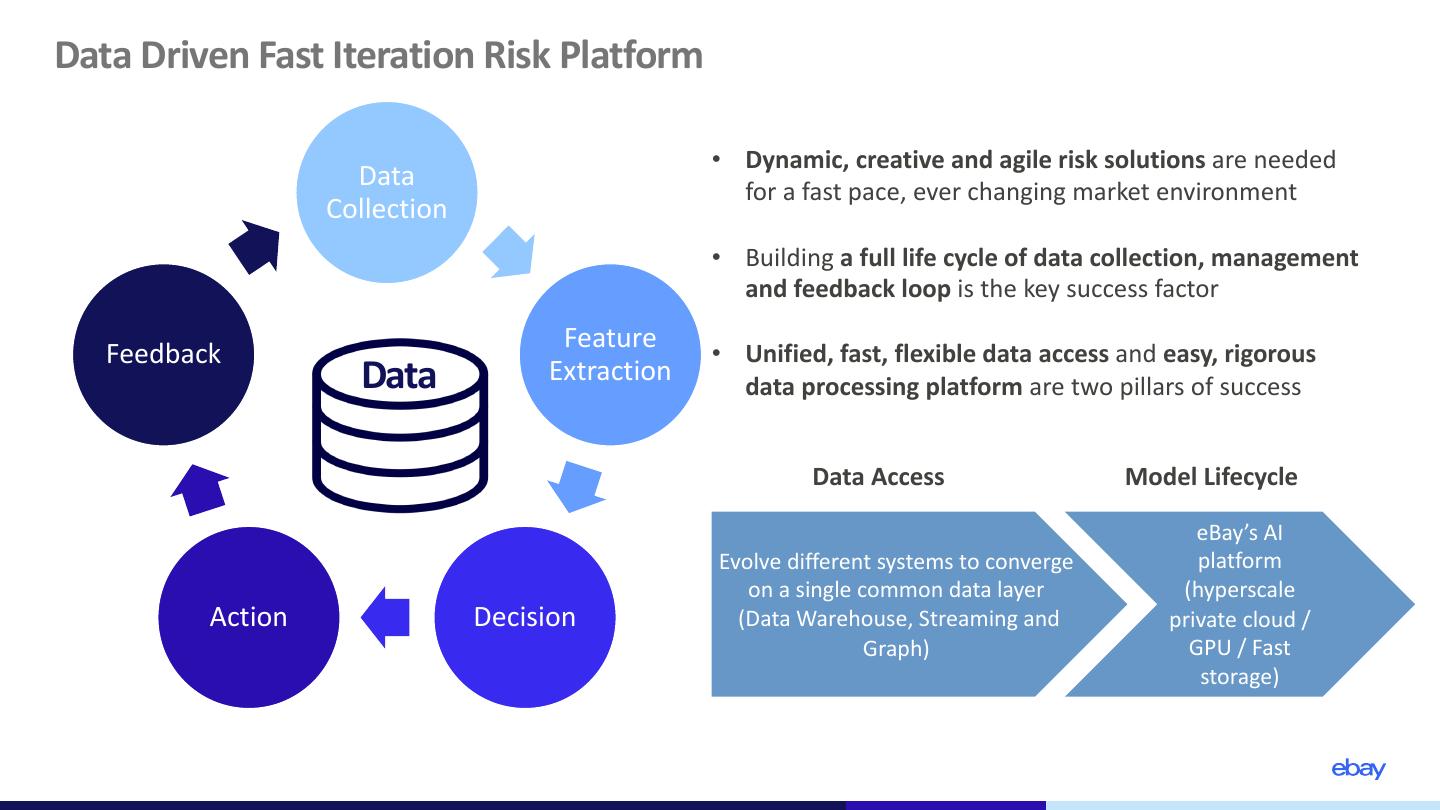
11 .Data Driven Fast Iteration Risk Platform • Dynamic, creative and agile risk solutions are needed Data for a fast pace, ever changing market environment Collection • Building a full life cycle of data collection, management and feedback loop is the key success factor Feature Feedback • Unified, fast, flexible data access and easy, rigorous Data Extraction data processing platform are two pillars of success Data Access Model Lifecycle eBay’s AI Evolve different systems to converge platform on a single common data layer (hyperscale Action Decision (Data Warehouse, Streaming and private cloud / Graph) GPU / Fast storage)
12 .