- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
Securing your data
在这个时代,在我们的电子通信中保持隐私是绝对必要的。创建用户帐户,不要将MongoDB环境暴露在更广泛的互联网上,这是过去一直被忽略的基本概念。一旦解决了这一问题,有兴趣成为符合PCI标准的个人和组织必须转向通过加密保护其数据。对于MongoDB,我们有两个加密选项:静态(仅作为MongoDB的企业功能提供)和传输加密。在本次会议中,我们将回顾
-为什么加密很重要
-设置加密的先决条件是什么
-在静止和传输中逐步加密
-在云中使用卷加密加密加密数据
-Percona for MongoDB加密功能
展开查看详情
1 .Securing Your Data: All steps for encrypting your MongoDB Database Nov-7-2018
2 .About me ● Location: Skopje, Republic of Macedonia ● Education: MSc, Software Engineering ● Experience: ○ Lead Database Consultant (since 2016) ○ Database Consultant (2012 - 2016) ○ Web Developer, DBA (2007 - 2012) ● Certifications: C100DBA - MongoDB certified DBA (since 2016) ● Percona speaker since 2016 https://mk.linkedin.com/in/igorle @igorle © 2018 Pythian. Confidential
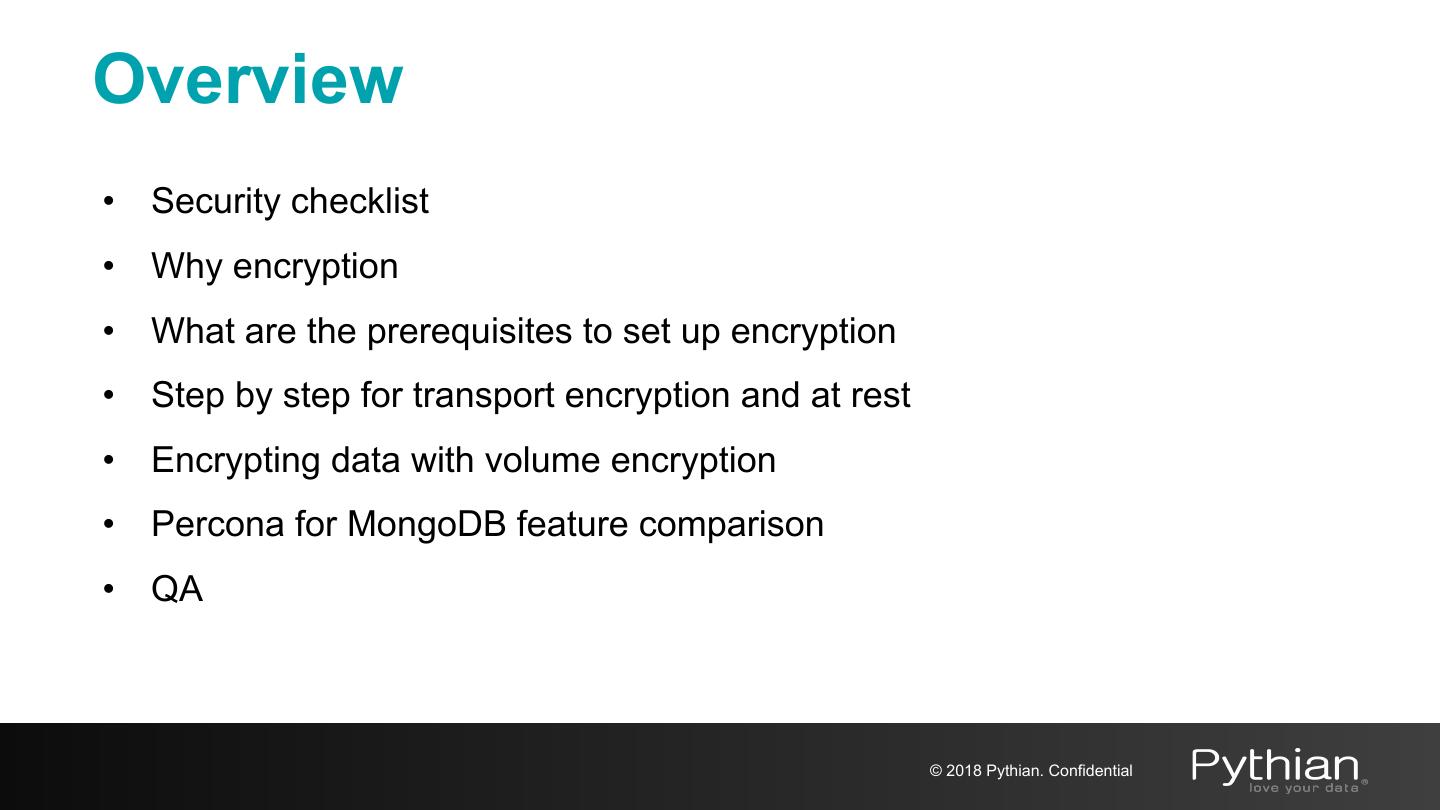
3 .Overview • Security checklist • Why encryption • What are the prerequisites to set up encryption • Step by step for transport encryption and at rest • Encrypting data with volume encryption • Percona for MongoDB feature comparison • QA © 2018 Pythian. Confidential
4 .Security incidents ● Data breach is a security incident in which sensitive, protected or confidential data is copied, transmitted, viewed, stolen or used by an individual unauthorized to do so ● Ransomware attacks © 2018 Pythian. Confidential
5 .Access hardening © 2018 Pythian. Confidential
6 .Security checklist • Network hardening • Authentication • Authorization (role based access control) © 2018 Pythian. Confidential
7 .Network hardening • Database servers exposed to the internet • No Firewall, VPN or VPC • net.bindIp: 0.0.0.0 Client Application Database Request © 2018 Pythian. Confidential
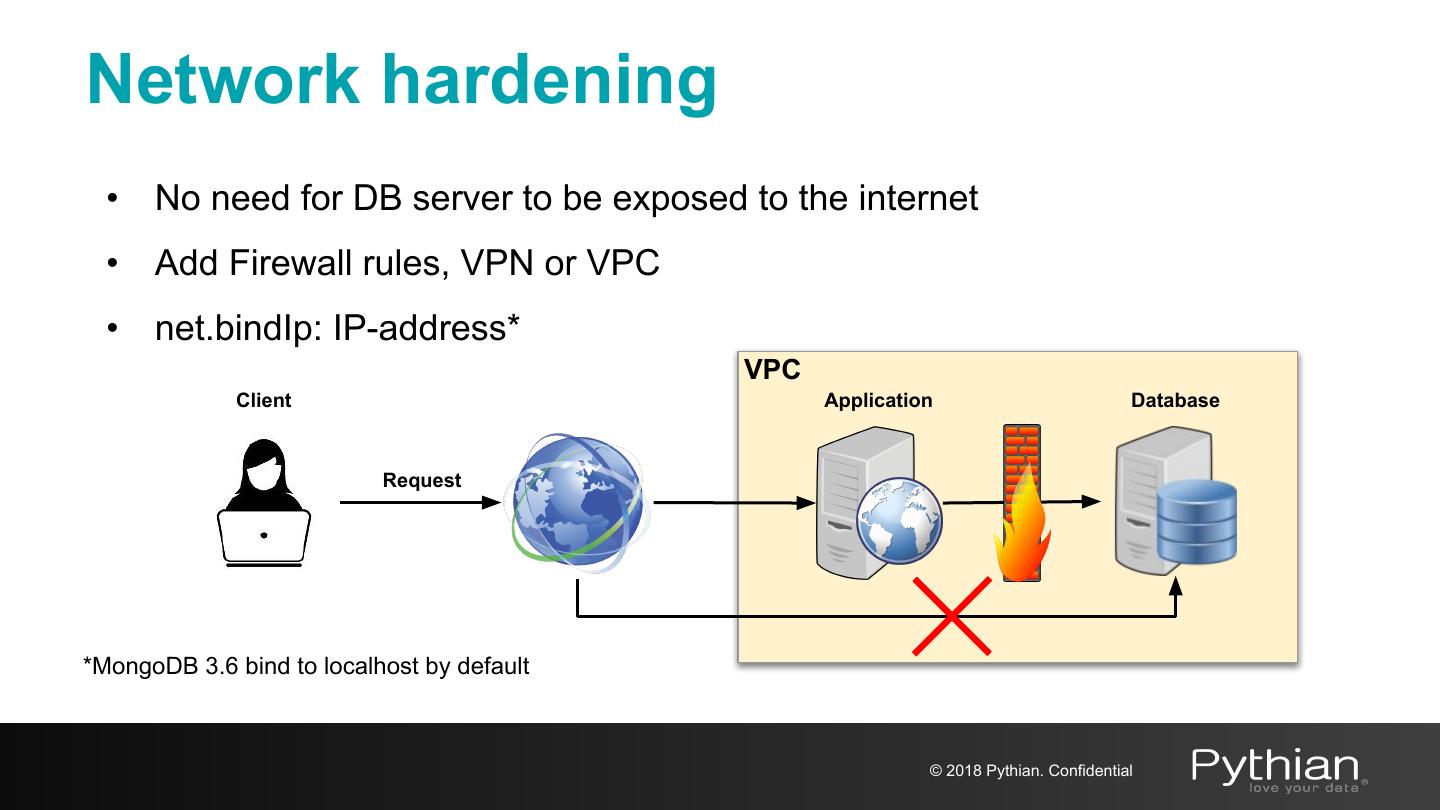
8 .Network hardening • No need for DB server to be exposed to the internet • Add Firewall rules, VPN or VPC • net.bindIp: IP-address* VPC Client Application Database Request *MongoDB 3.6 bind to localhost by default © 2018 Pythian. Confidential
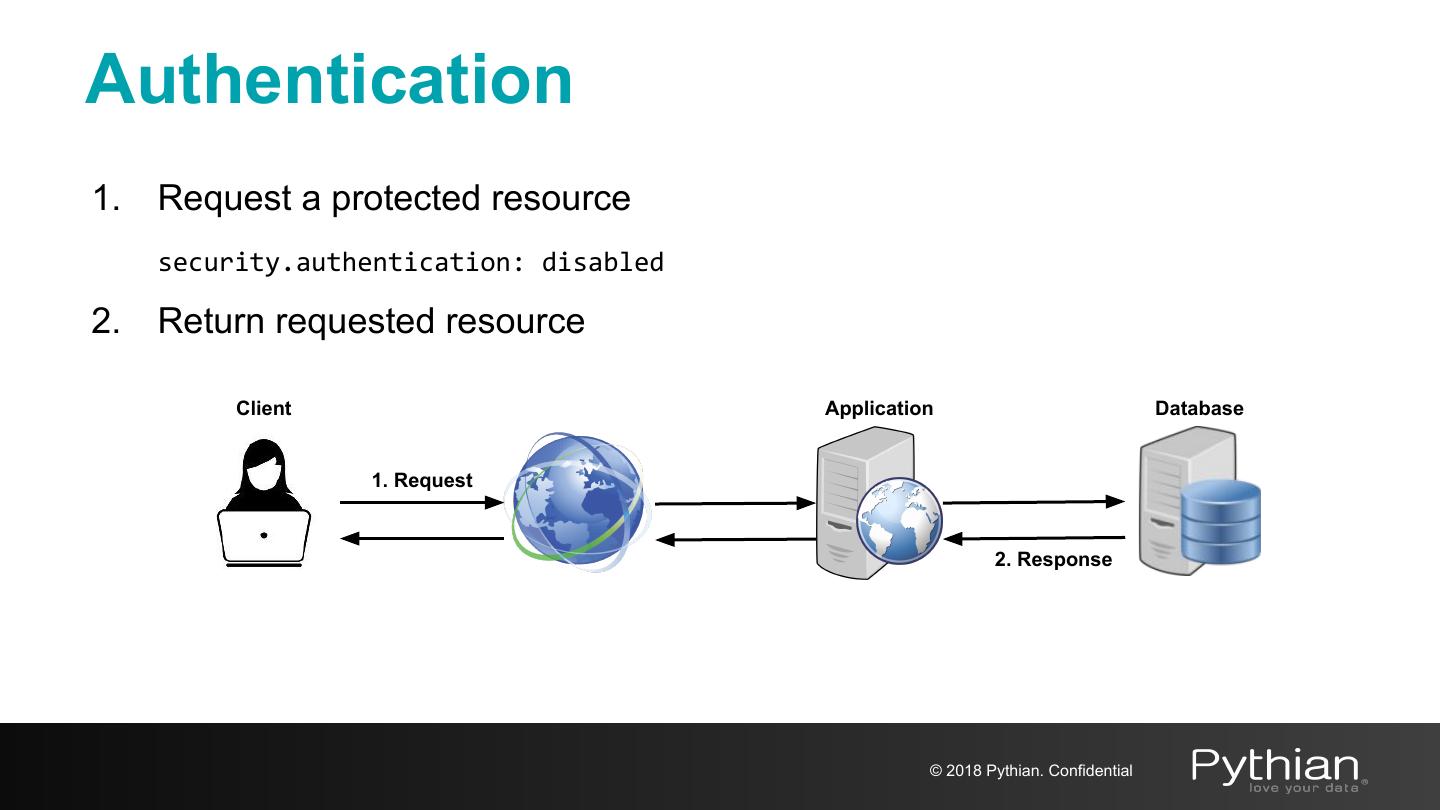
9 .Authentication 1. Request a protected resource security.authentication: disabled 2. Return requested resource Client Application Database 1. Request 2. Response © 2018 Pythian. Confidential
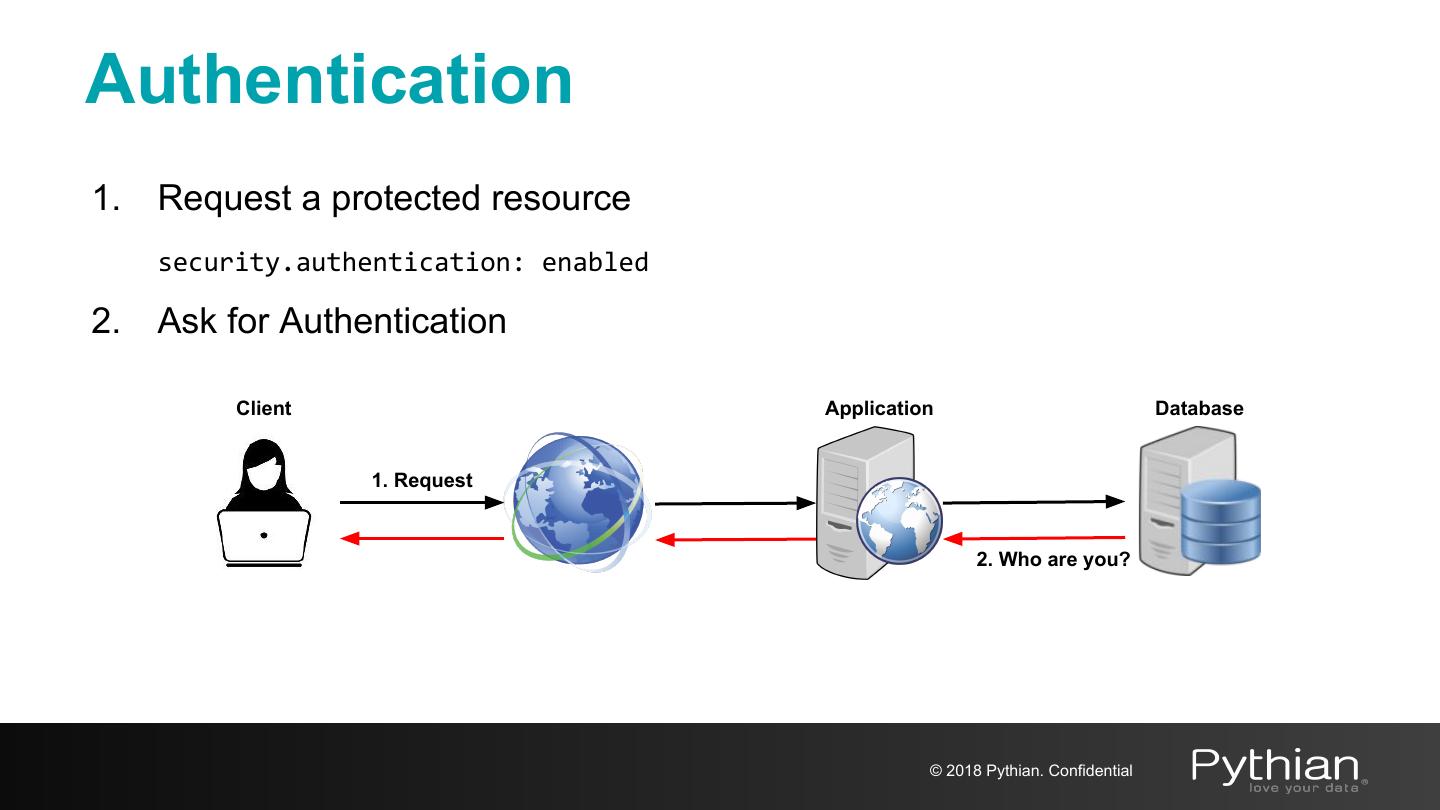
10 .Authentication 1. Request a protected resource security.authentication: enabled 2. Ask for Authentication Client Application Database 1. Request 2. Who are you? © 2018 Pythian. Confidential
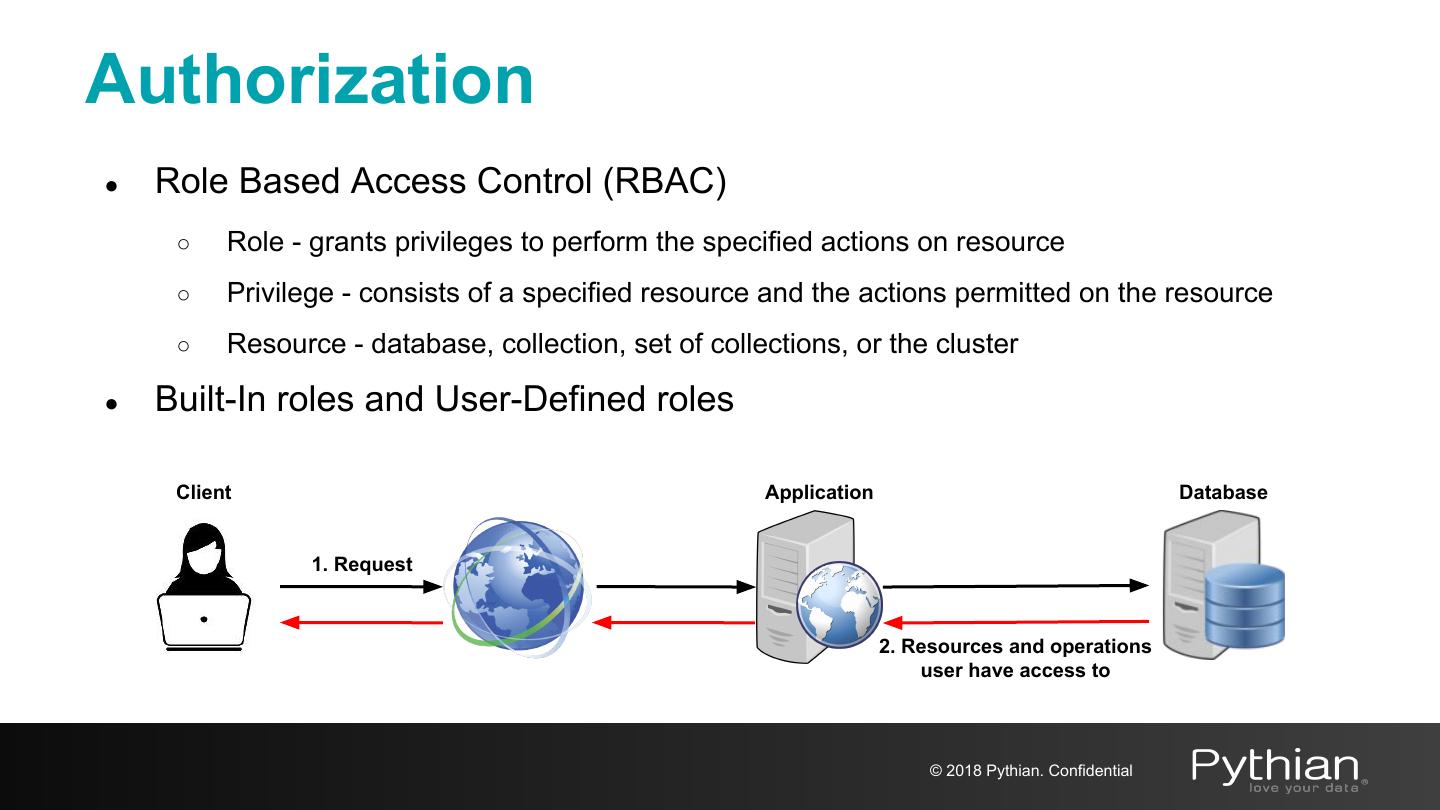
11 .Authorization ● Role Based Access Control (RBAC) ○ Role - grants privileges to perform the specified actions on resource ○ Privilege - consists of a specified resource and the actions permitted on the resource ○ Resource - database, collection, set of collections, or the cluster ● Built-In roles and User-Defined roles Client Application Database 1. Request 2. Resources and operations user have access to © 2018 Pythian. Confidential
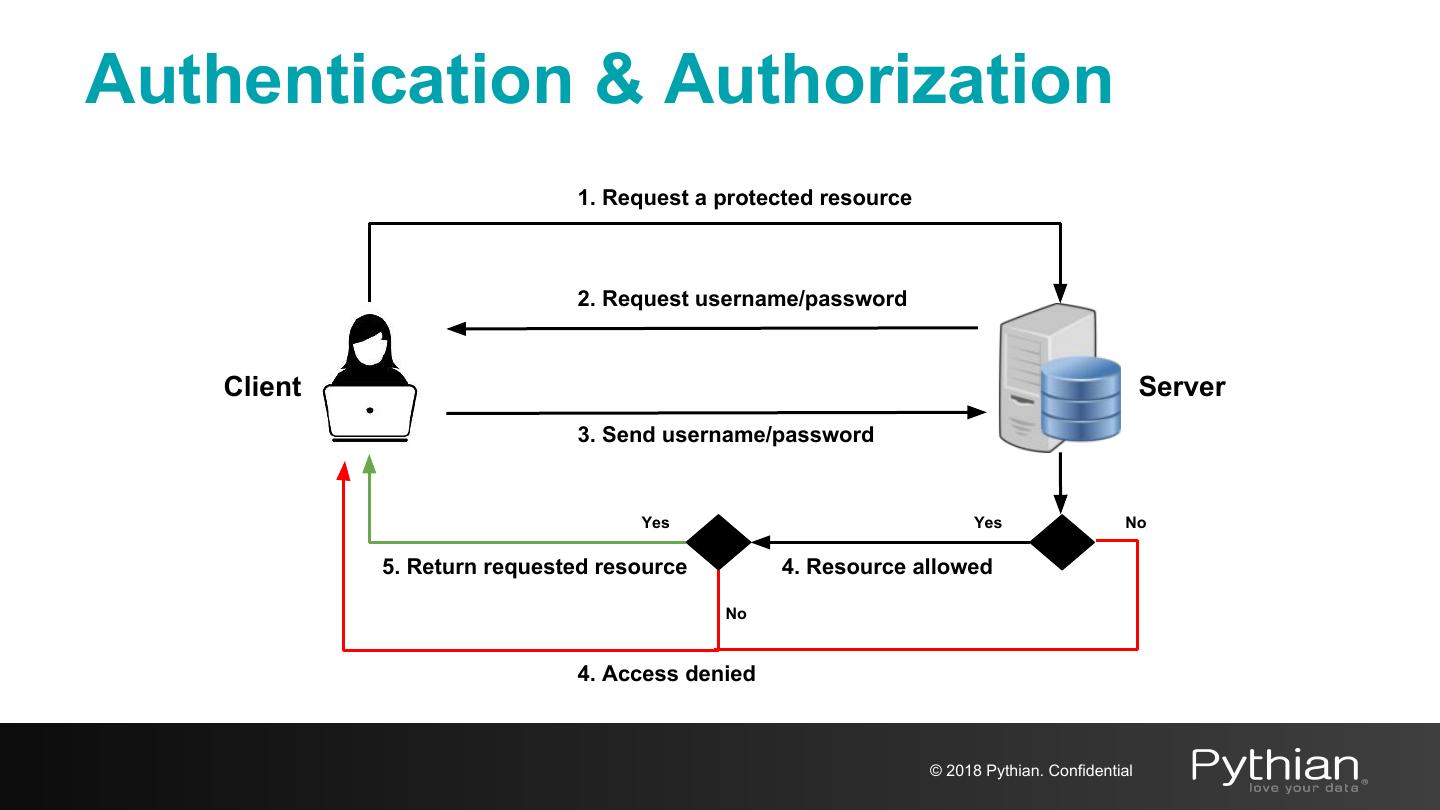
12 .Authentication & Authorization 1. Request a protected resource 2. Request username/password Client Server 3. Send username/password Yes Yes No 5. Return requested resource 4. Resource allowed No 4. Access denied © 2018 Pythian. Confidential
13 .Encryption © 2018 Pythian. Confidential
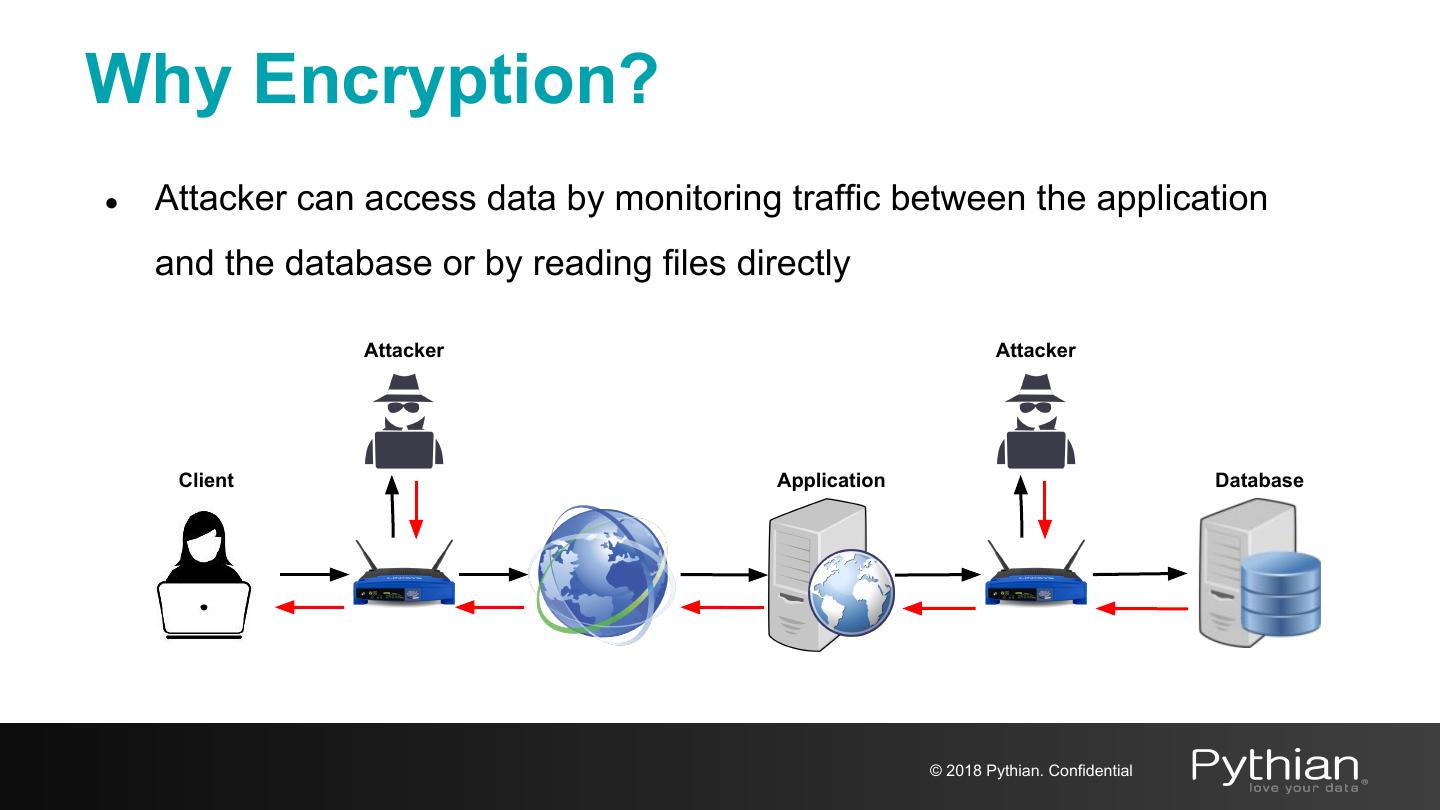
14 .Why Encryption? ● Attacker can access data by monitoring traffic between the application and the database or by reading files directly Attacker Attacker Client Application Database © 2018 Pythian. Confidential
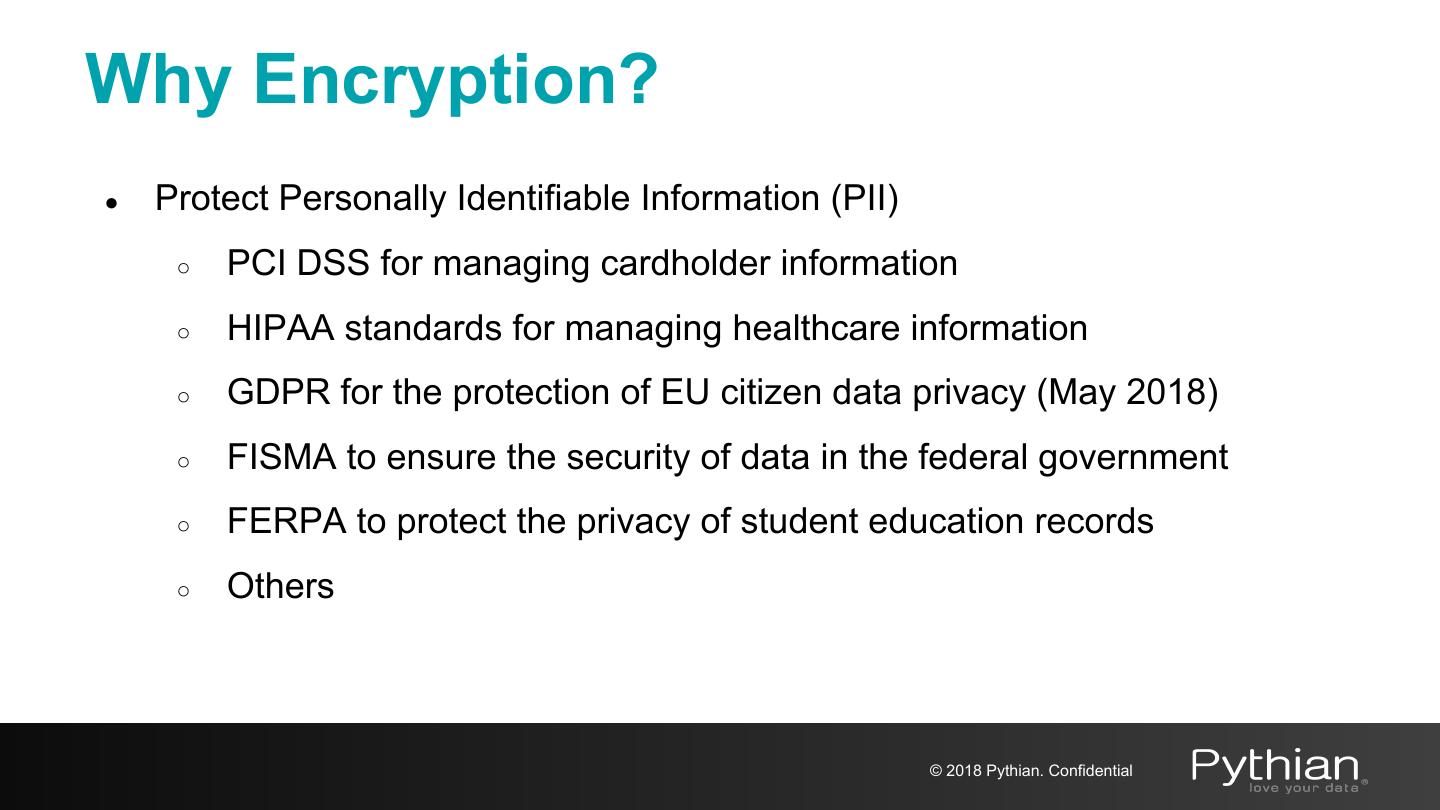
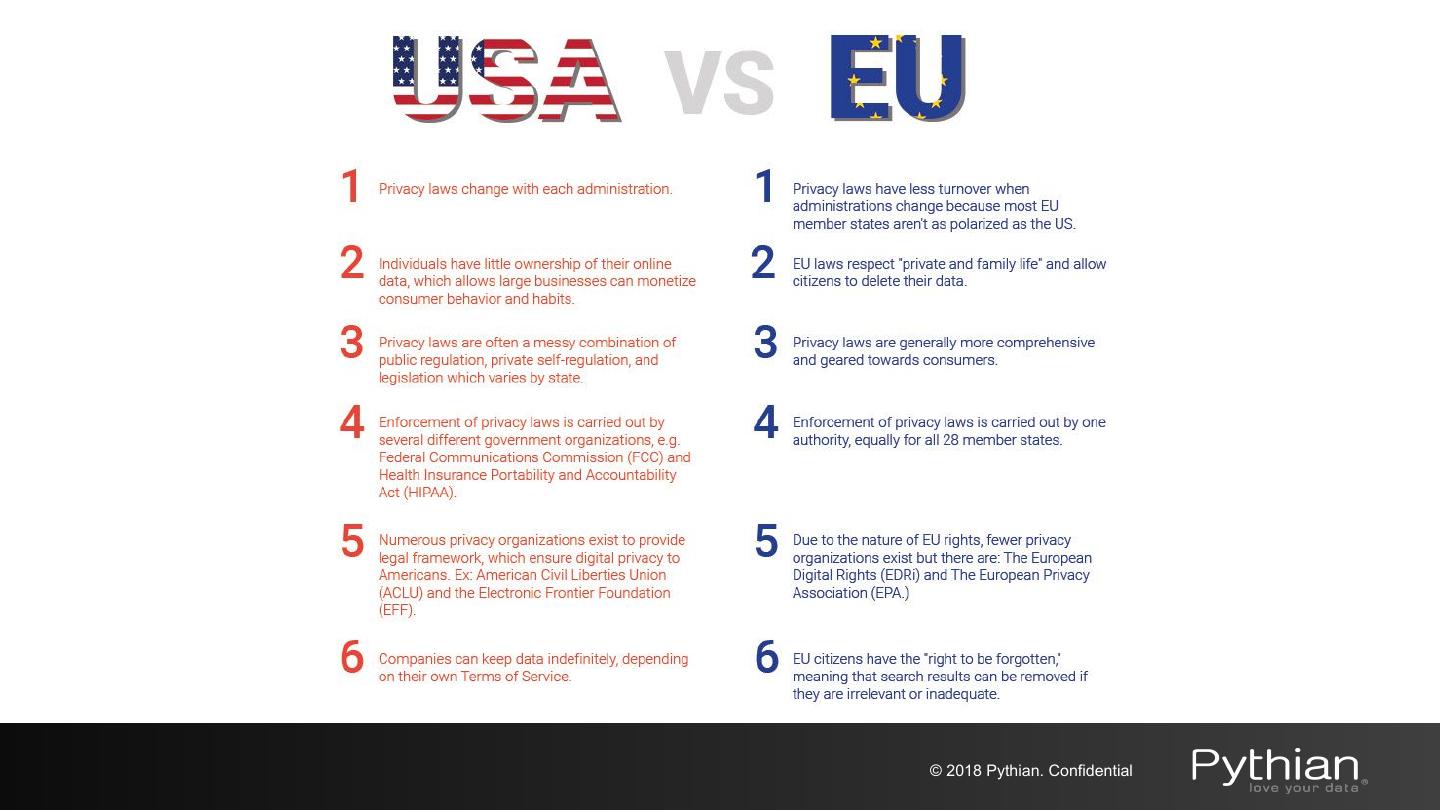
15 .Why Encryption? ● Protect Personally Identifiable Information (PII) ○ PCI DSS for managing cardholder information ○ HIPAA standards for managing healthcare information ○ GDPR for the protection of EU citizen data privacy (May 2018) ○ FISMA to ensure the security of data in the federal government ○ FERPA to protect the privacy of student education records ○ Others © 2018 Pythian. Confidential
16 .© 2018 Pythian. Confidential
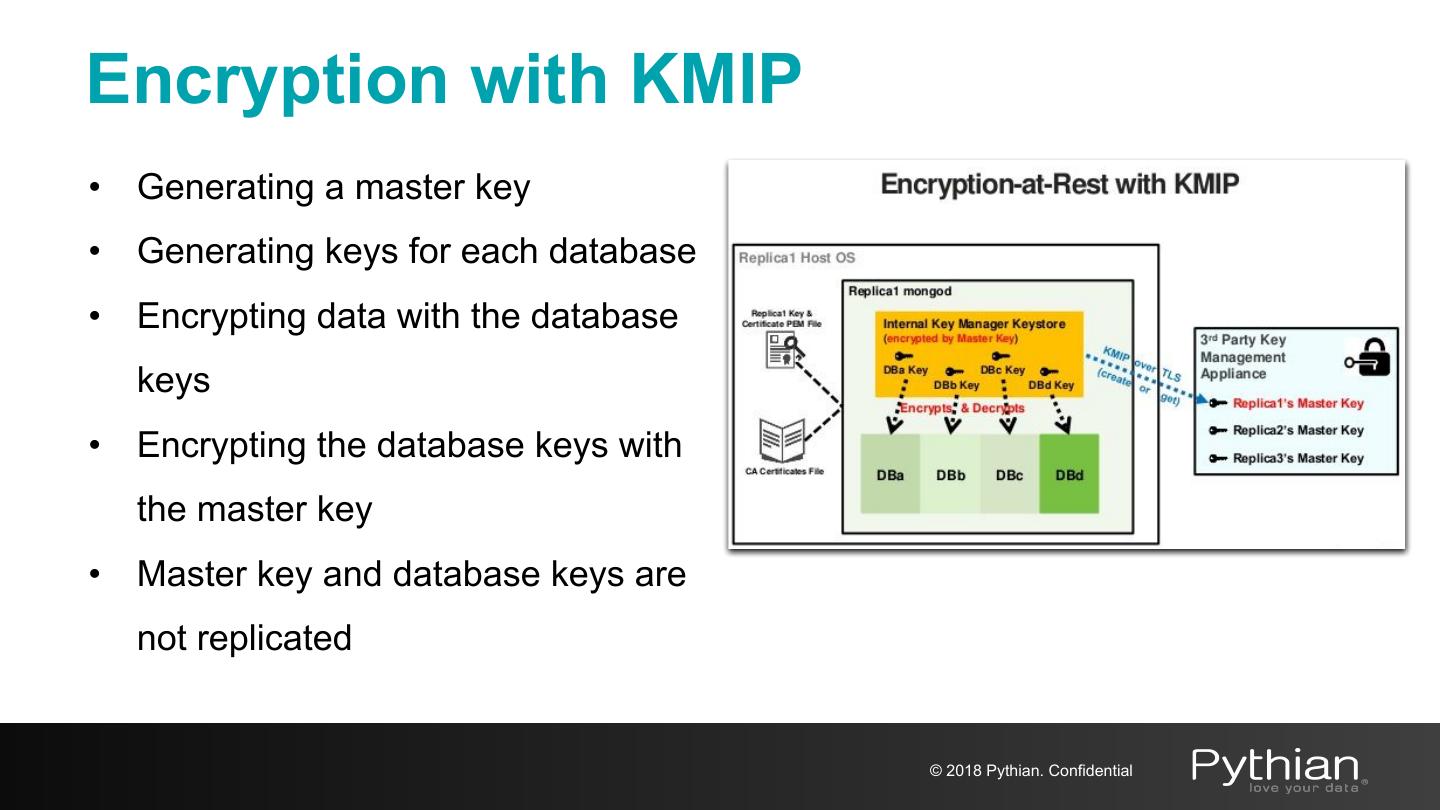
17 .Encryption with MongoDB ● Transport encryption ○ MongoDB network traffic is only readable by the intended client ● Encryption at REST ○ Application Level Encryption and Storage Encryption ○ Native encryption option for the WiredTiger storage engine* * Available in MongoDB Enterprise only © 2018 Pythian. Confidential
18 .Transport Encryption © 2018 Pythian. Confidential
19 .Transport encryption ● TLS/SSL (Transport Layer Security/Secure Sockets Layer) to encrypt all of MongoDB’s network traffic ● Certificate Authorities - valid certificates generated and signed by a single certificate authority ○ PEMKeyfile with the name of the .pem file that contains the signed TLS/SSL certificate and key ○ CAFile with the name of the .pem file that contains the root certificate chain from the Certificate Authority © 2018 Pythian. Confidential
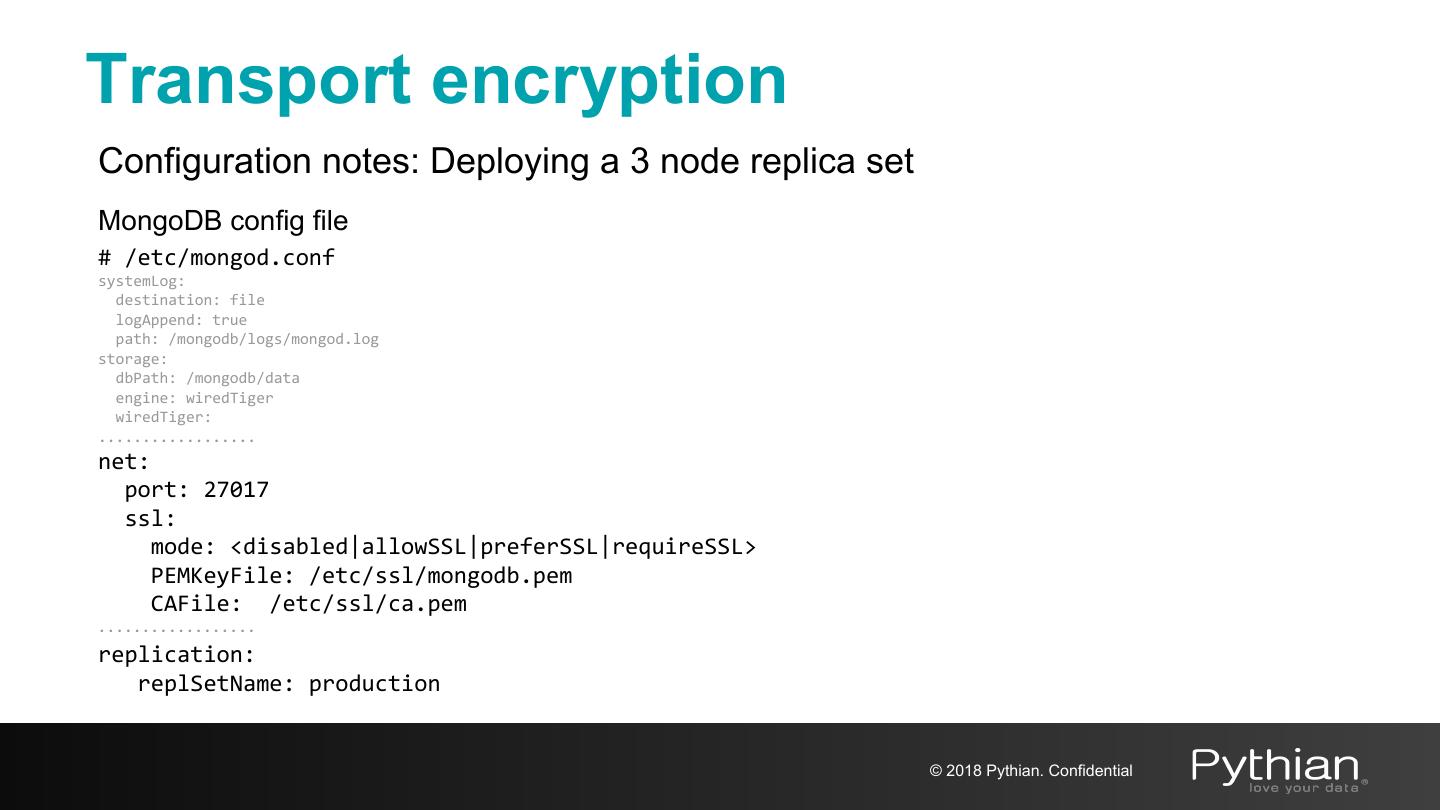
20 .Transport encryption Configuration notes: Deploying a 3 node replica set MongoDB config file # /etc/mongod.conf systemLog: destination: file logAppend: true path: /mongodb/logs/mongod.log storage: dbPath: /mongodb/data engine: wiredTiger wiredTiger: .................. net: port: 27017 ssl: mode: <disabled|allowSSL|preferSSL|requireSSL> PEMKeyFile: /etc/ssl/mongodb.pem CAFile: /etc/ssl/ca.pem .................. replication: replSetName: production © 2018 Pythian. Confidential
21 .Transport encryption net.ssl.mode Value Description disabled The server does not use TLS/SSL Connections between servers do not use TLS/SSL allowSSL For incoming connections, the server accepts both TLS/SSL and non-TLS/non-SSL Connections between servers use TLS/SSL preferSSL For incoming connections, the server accepts both TLS/SSL and non-TLS/non-SSL requireSSL The server uses and accepts only TLS/SSL encrypted connections © 2018 Pythian. Confidential
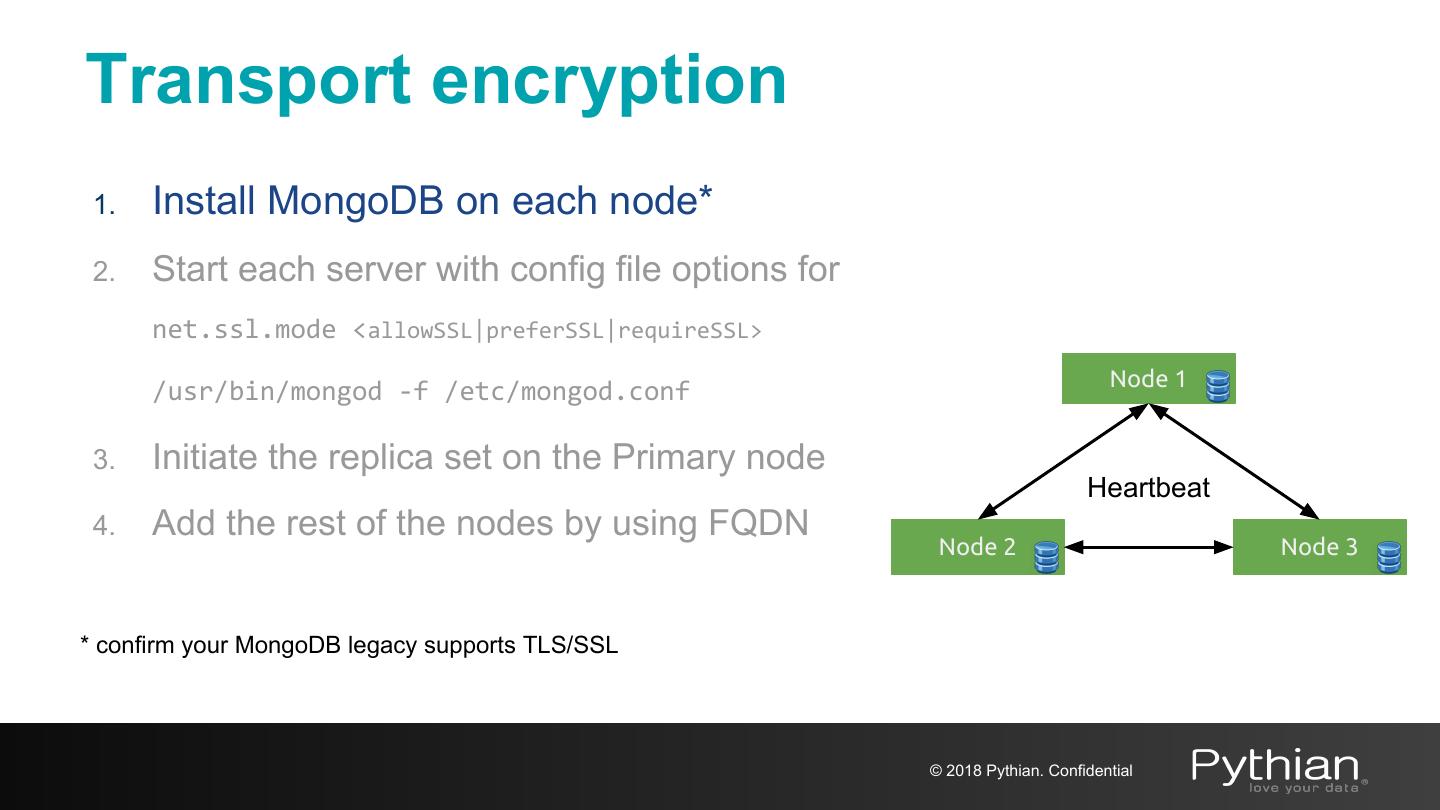
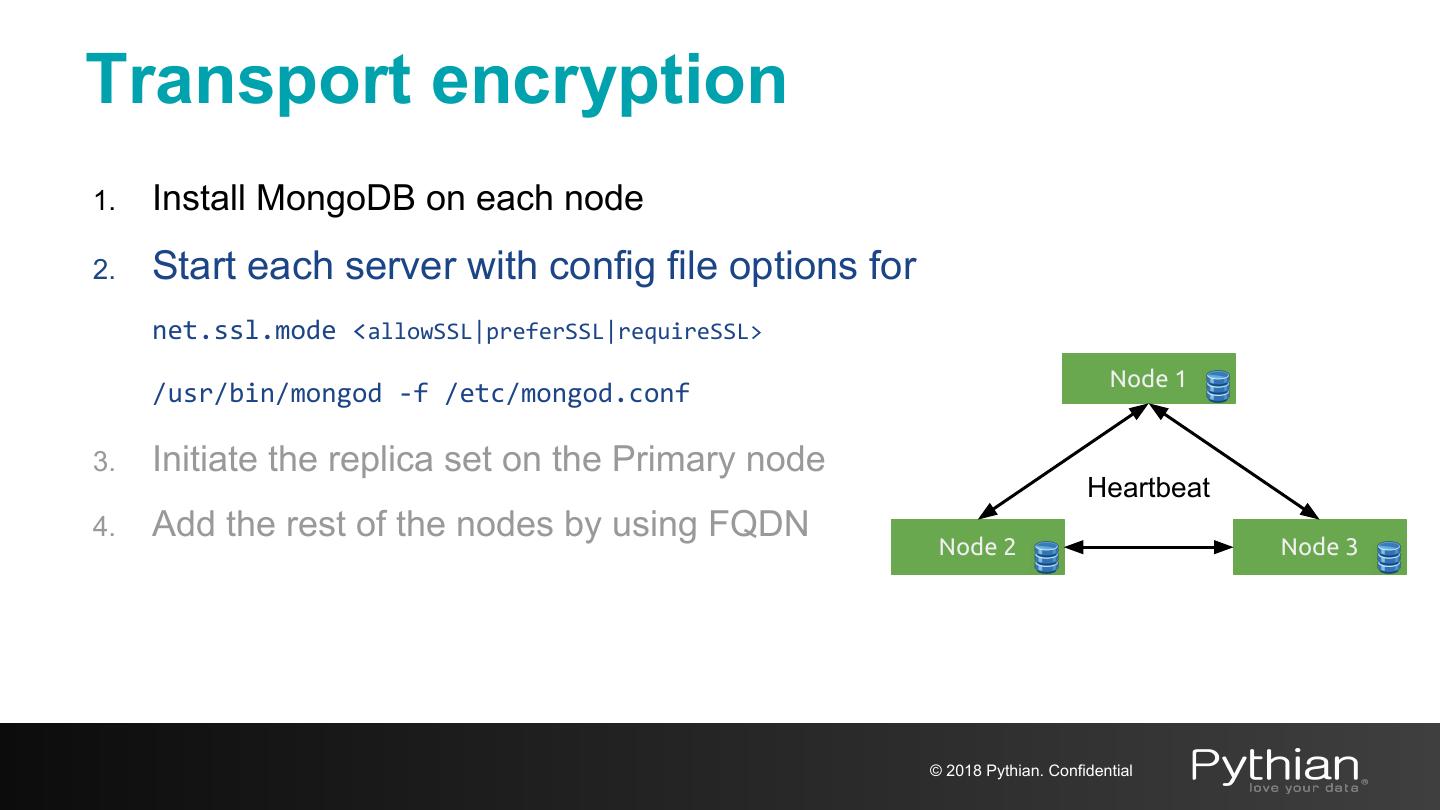
22 .Transport encryption 1. Install MongoDB on each node* 2. Start each server with config file options for net.ssl.mode <allowSSL|preferSSL|requireSSL> Node 1 /usr/bin/mongod -f /etc/mongod.conf 3. Initiate the replica set on the Primary node Heartbeat 4. Add the rest of the nodes by using FQDN Node 2 Node 3 * confirm your MongoDB legacy supports TLS/SSL © 2018 Pythian. Confidential
23 .Transport encryption 1. Install MongoDB on each node 2. Start each server with config file options for net.ssl.mode <allowSSL|preferSSL|requireSSL> Node 1 /usr/bin/mongod -f /etc/mongod.conf 3. Initiate the replica set on the Primary node Heartbeat 4. Add the rest of the nodes by using FQDN Node 2 Node 3 © 2018 Pythian. Confidential
24 .Transport encryption 1. Install MongoDB on each node 2. Start each server with config file options for net.ssl.mode <allowSSL|preferSSL|requireSSL> /usr/bin/mongod -f /etc/mongod.conf Primary 3. Initiate the replica set on the Primary node Heartbeat 4. Add the rest of the nodes by using FQDN Node 2 Node 3 © 2018 Pythian. Confidential
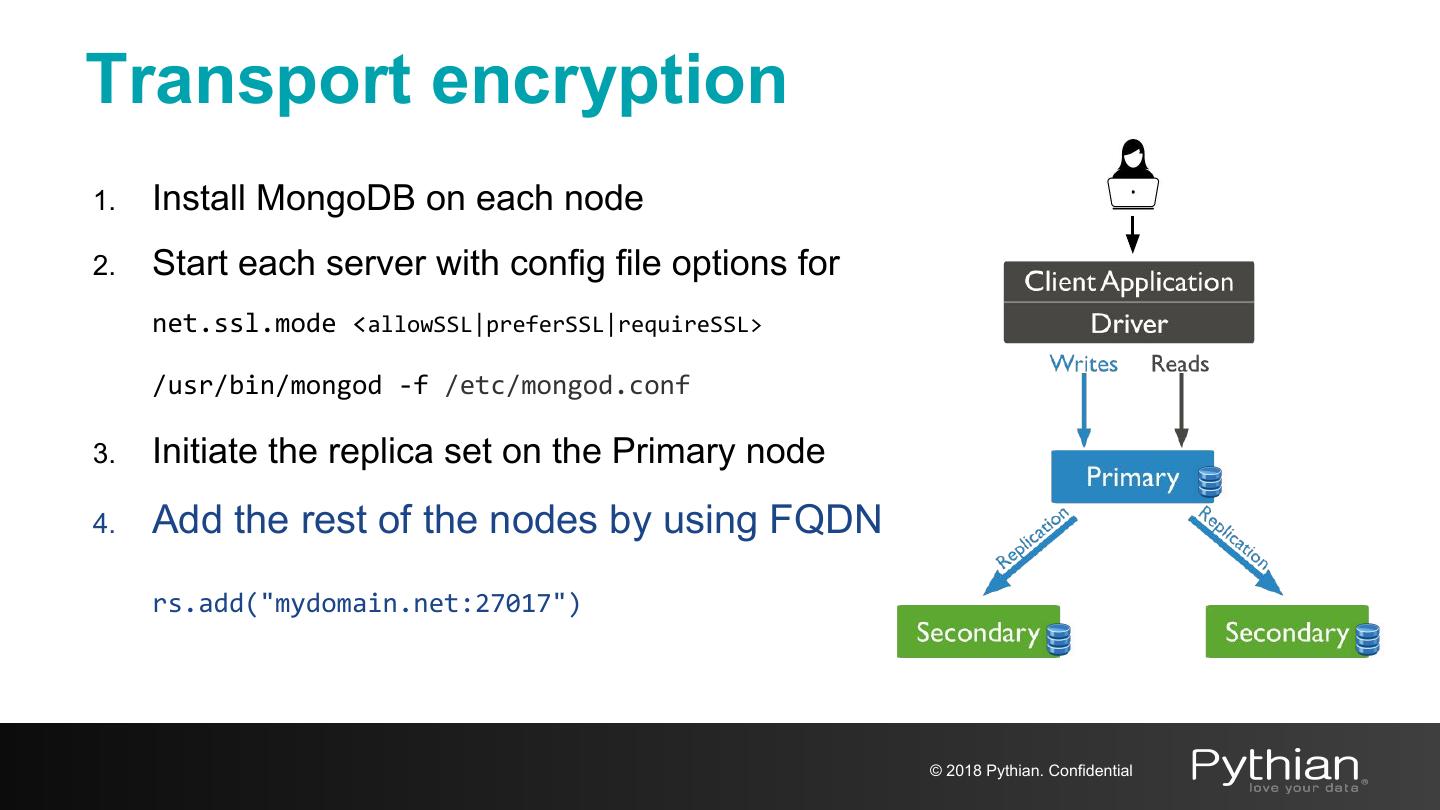
25 .Transport encryption 1. Install MongoDB on each node 2. Start each server with config file options for net.ssl.mode <allowSSL|preferSSL|requireSSL> /usr/bin/mongod -f /etc/mongod.conf 3. Initiate the replica set on the Primary node 4. Add the rest of the nodes by using FQDN rs.add("mydomain.net:27017") © 2018 Pythian. Confidential
26 .Transport encryption Upgrade running Replica to Use TLS/SSL • Restart the processes with ssl.Mode allowSSL net: ssl: mode: allowSSL • Switch the clients to use TLS/SSL © 2018 Pythian. Confidential
27 .Transport encryption Upgrade running Cluster to Use TLS/SSL • Restart the processes with ssl.Mode allowSSL net: ssl: mode: allowSSL • Switch the clients to use TLS/SSL • Upgrade to preferSSL by issuing the command on each node db.adminCommand( { setParameter: 1, sslMode: "preferSSL" } ) © 2018 Pythian. Confidential
28 .Transport encryption Upgrade running Cluster to Use TLS/SSL • Restart the processes with ssl.Mode allowSSL net: ssl: mode: allowSSL • Switch the clients to use TLS/SSL • Upgrade to preferSSL by issuing the command on each node db.adminCommand( { setParameter: 1, sslMode: "preferSSL" } ) • Upgrade to requireSSL by issuing the command on each node db.adminCommand( { setParameter: 1, sslMode: "requireSSL" } ) • Update the config file to persist the settings net.ssl.mode: requireSSL © 2018 Pythian. Confidential
29 .Encryption at REST © 2018 Pythian. Confidential