- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
Database data security
基于密码工程的数据库数据安全
展开查看详情
1 .Database data security through the lens of cryptographic engineering Eugene Pilyankevich, Chief Technical officer, Cossack Labs
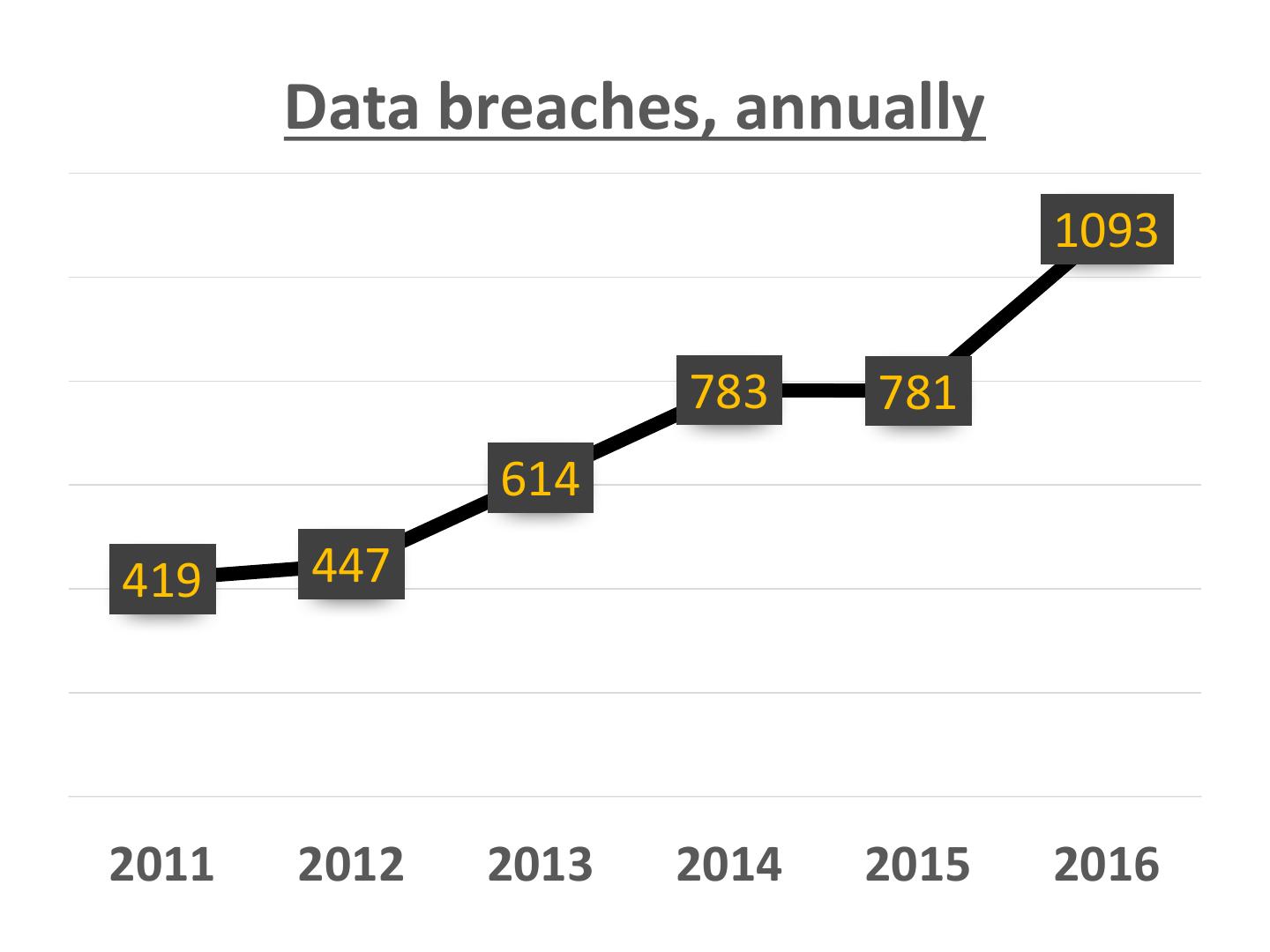
2 . Data breaches, annually 1093 783 781 614 419 447 2011 2012 2013 2014 2015 2016
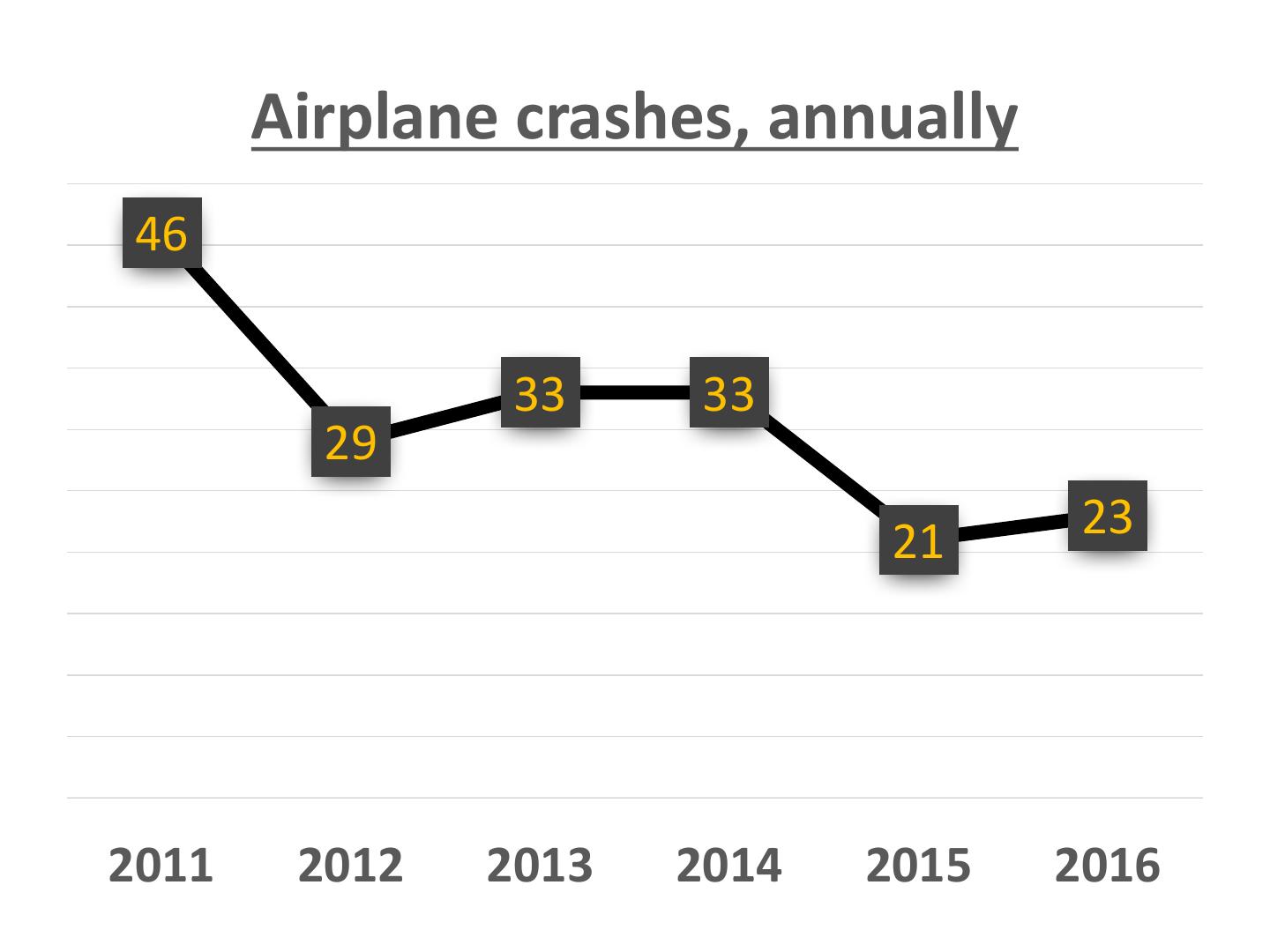
3 . Airplane crashes, annually 46 33 33 29 21 23 2011 2012 2013 2014 2015 2016
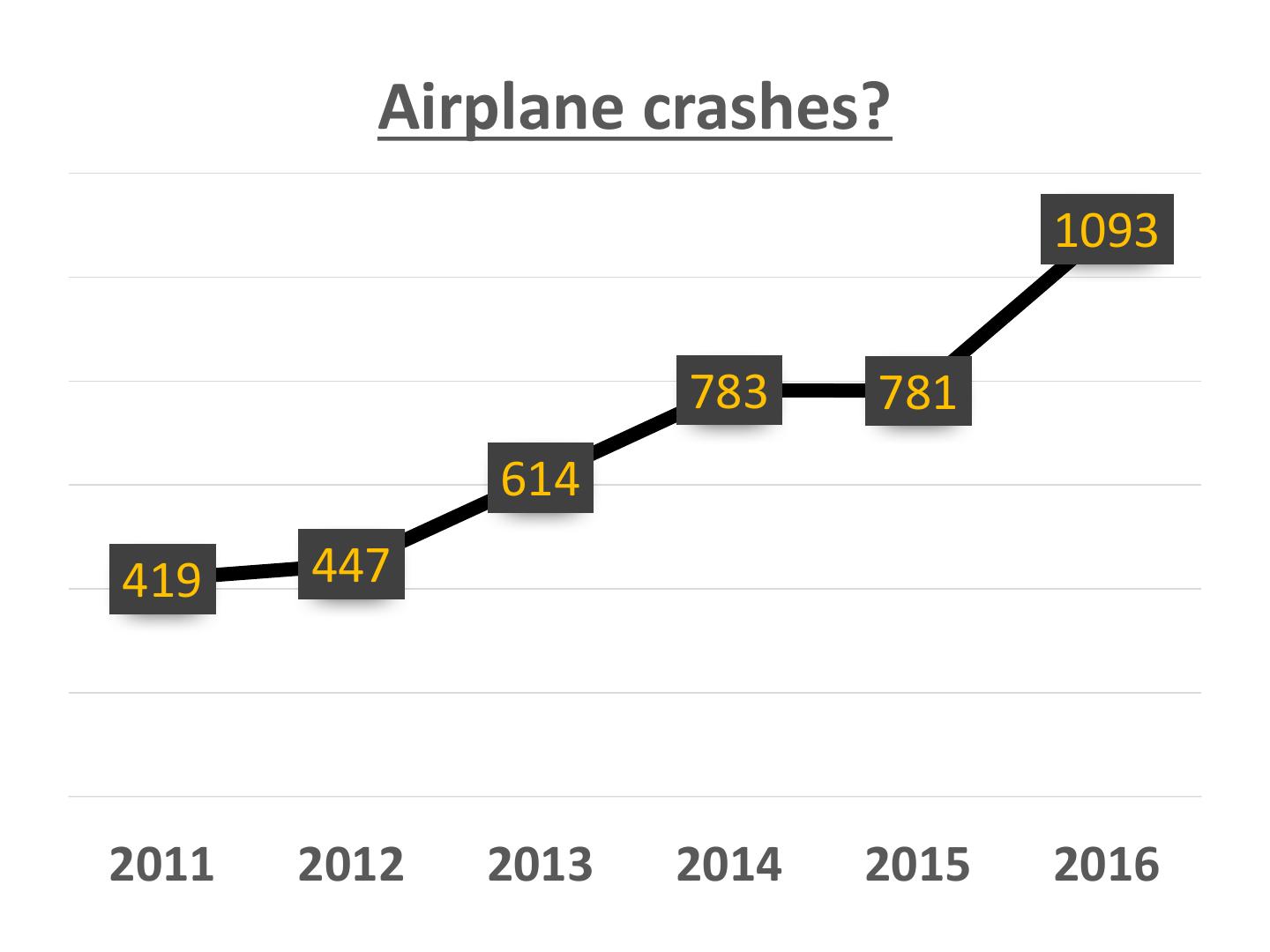
4 . Airplane crashes? 1093 783 781 614 419 447 2011 2012 2013 2014 2015 2016
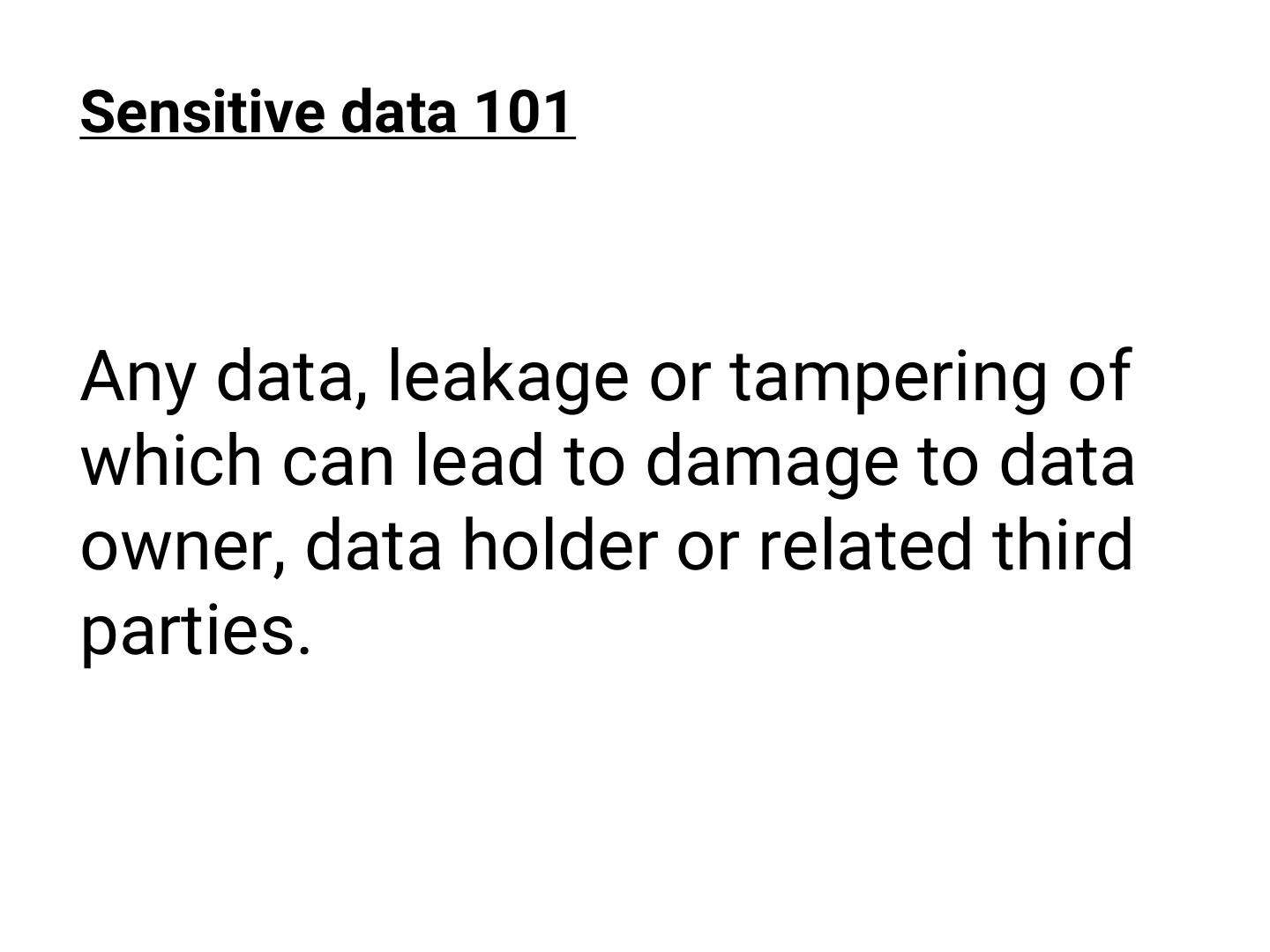
5 .Sensitive data 101 Any data, leakage or tampering of which can lead to damage to data owner, data holder or related third parties.
6 .Naïve security model
7 .Naïve security model Focused on Ops-driven components
8 .Naïve security model Few generic vectors Passive attacks Smash’n’grab
9 .Securing the naïve security model § encryption-at-rest § encryption-in-transit § access distribution & control § event monitoring
10 .Pragmatic security model
11 .Real attackers are: § Smart and resourceful … targeting an old § Multi-skilled vulnerability that § Many vectors of attack you forgot to patch.
12 .Pragmatic security model Poor perimeter
13 .Pragmatic security model Poor perimeter Active and/or persistent attacks
14 .Pragmatic security model Poor perimeter Active and/or persistent attacks Data-specific attacks
15 .Pragmatic security model Poor perimeter Active and/or persistent attacks Data-specific attacks Systematic approach
16 .… anything else?
17 .Idealistic security model
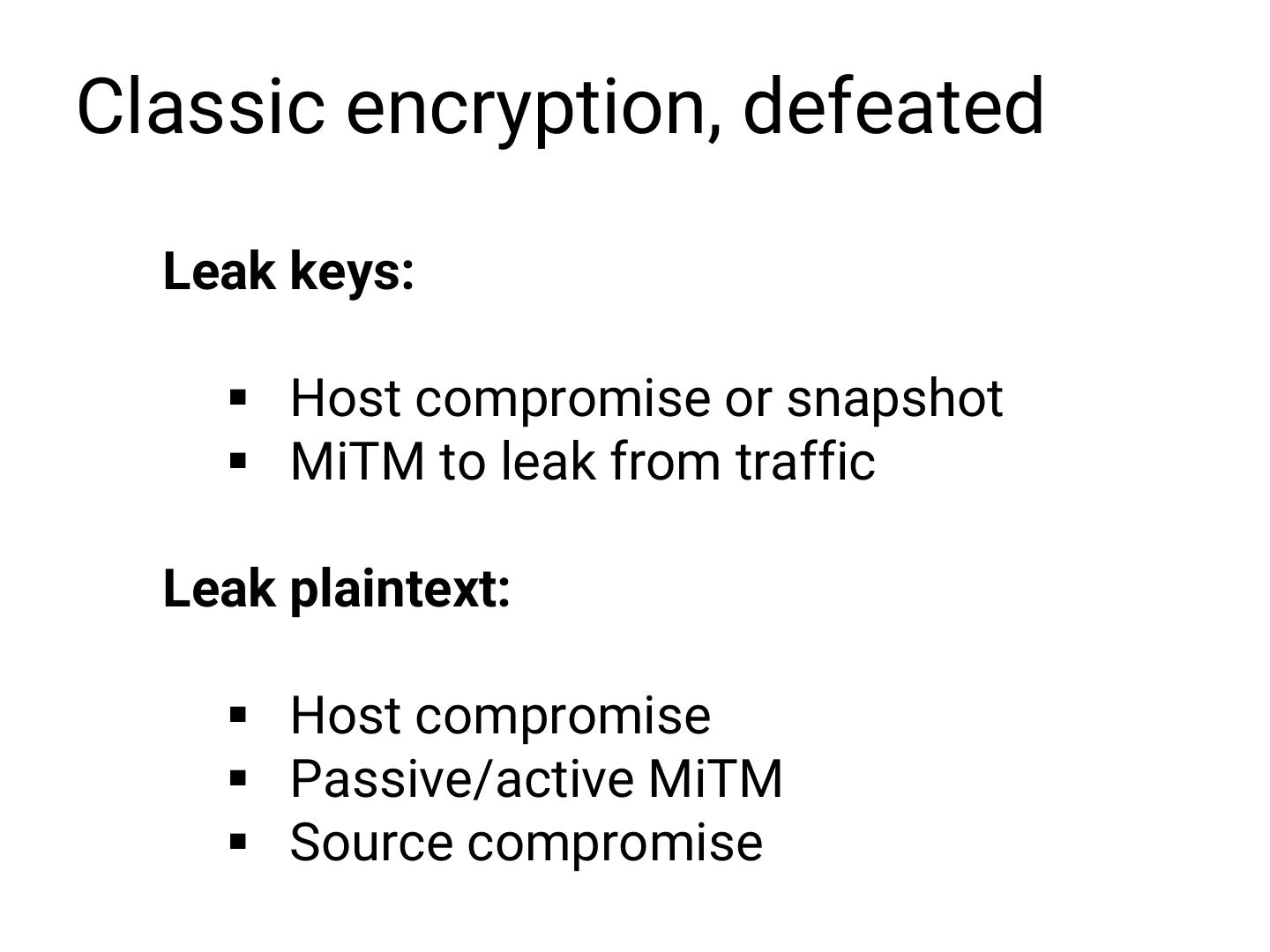
18 .Idealistic security model: Future is now Future is reliable Working as guinea pig is a great idea
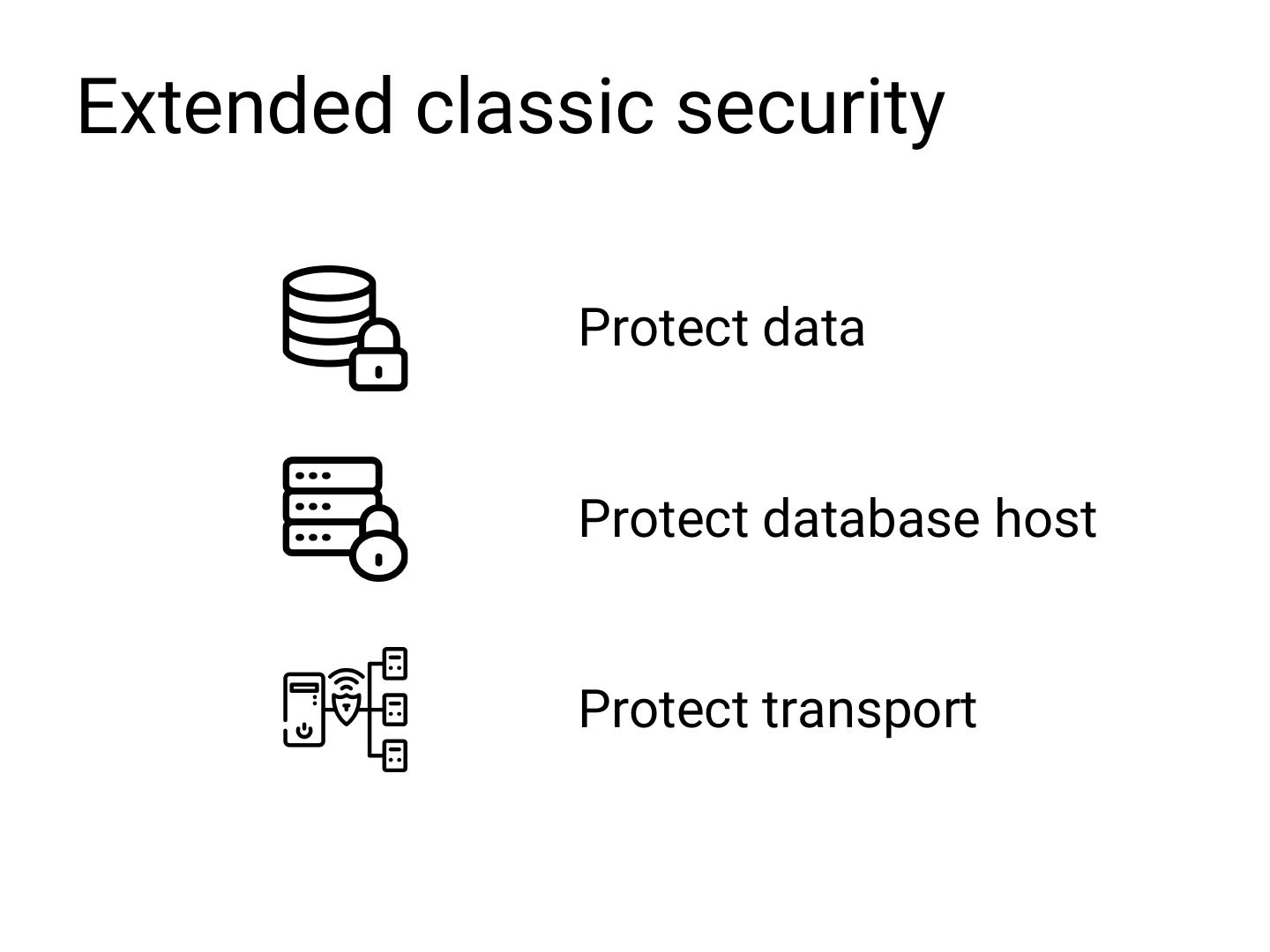
19 .Idealistic security model: Less than 10 years in public Assumptions assumptions Not tested in production
20 .Database encryption
21 .What does encryption do? Encryption narrows attack surface from data to keys
22 .Database encryption Classic Modern
23 .Classic attacks § Smash ‘n’ grab § Snapshot attacker § Persistent passive attacker
24 .Сlassic encryption? Row/column/table Database files Full disk encryption
25 .Сlassic encryption? Row/column/table NO DIFFERENCE Database files Full disk encryption
26 .Сlassic encryption, defeated Leak keys: § Host compromise or snapshot § MiTM to leak from traffic Leak plaintext: § Host compromise § Passive/active MiTM § Source compromise
27 .Extended classic security Protect data Protect database host Protect transport
28 .Typical modern attacks § Flow alternation (SQL Injection) § VM image leak § Full compromise (temporary or persistent)
29 .