- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
MongoDB Security
MongoDB安全漏洞经常出现在新闻中。然而,没有提到的是,这一切都是可以避免的。简单的错误会导致巨大的头痛,管理层和客户对您(DBA)的信心丧失。我们将消除市场宣传,并给你一本真实世界的剧本,告诉你在保护你的系统时应该做什么以及如何做。这包括启用身份验证、理解和构建自定义角色和用户、了解如何加密数据、使用LDAP/AD等。
展开查看详情
1 . MongoDB Security: Making Things Secure by Default Wed, Aug 9, 2017 11:00 AM - 12:00 PM PDT Adamo Tonete, Senior Technical Services Engineer 1 © 2017 Percona
2 .Recent Security Problems 2 © 2017 Percona
3 .{ me : 'twitter.com/adamotonete' } Adamo Tonete I've been working for Percona since late 2015 as a Senior Technical Services Engineer. Based on São Paulo Brazil 3 © 2017 Percona
4 .Agenda ● Installing MongoDB; ● Enabling authentication and creating a root and a standard user; ● Default roles; ● Starting a replica-set and a sharded environment with authentication; ● SSL; ● LDAP; ● Audit plugin; ● Store backups safely. 4 © 2017 Percona
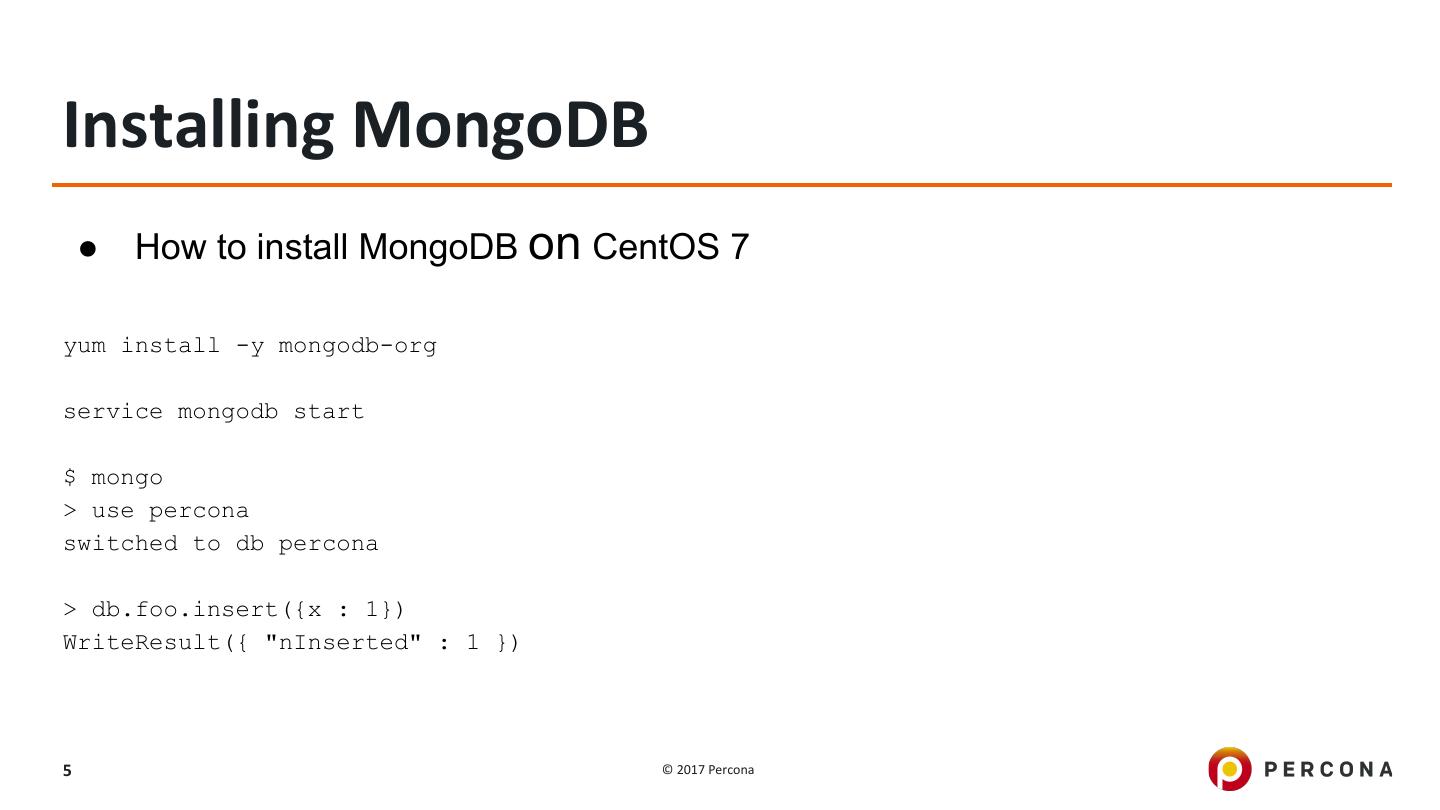
5 .Installing MongoDB ● How to install MongoDB on CentOS 7 yum install -y mongodb-org service mongodb start $ mongo > use percona switched to db percona > db.foo.insert({x : 1}) WriteResult({ "nInserted" : 1 }) 5 © 2017 Percona
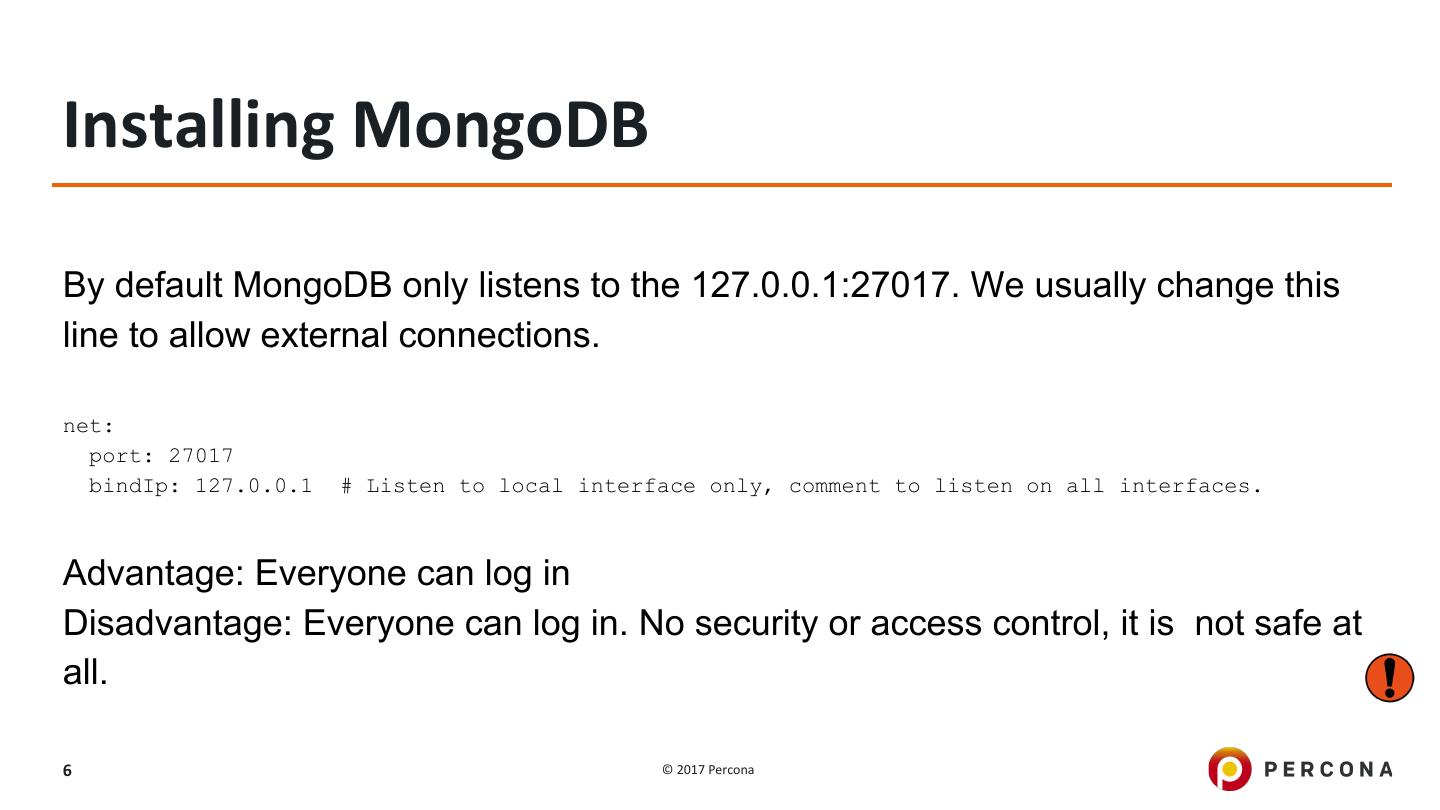
6 .Installing MongoDB By default MongoDB only listens to the 127.0.0.1:27017. We usually change this line to allow external connections. net: port: 27017 bindIp: 127.0.0.1 # Listen to local interface only, comment to listen on all interfaces. Advantage: Everyone can log in Disadvantage: Everyone can log in. No security or access control, it is not safe at all. 6 © 2017 Percona
7 .Installing MongoDB ● If it is not a local development with fake data, please make sure that authentication is enabled. ● Try to isolate the access as much as possible, several administrator users is almost the same as no user control. 7 © 2017 Percona
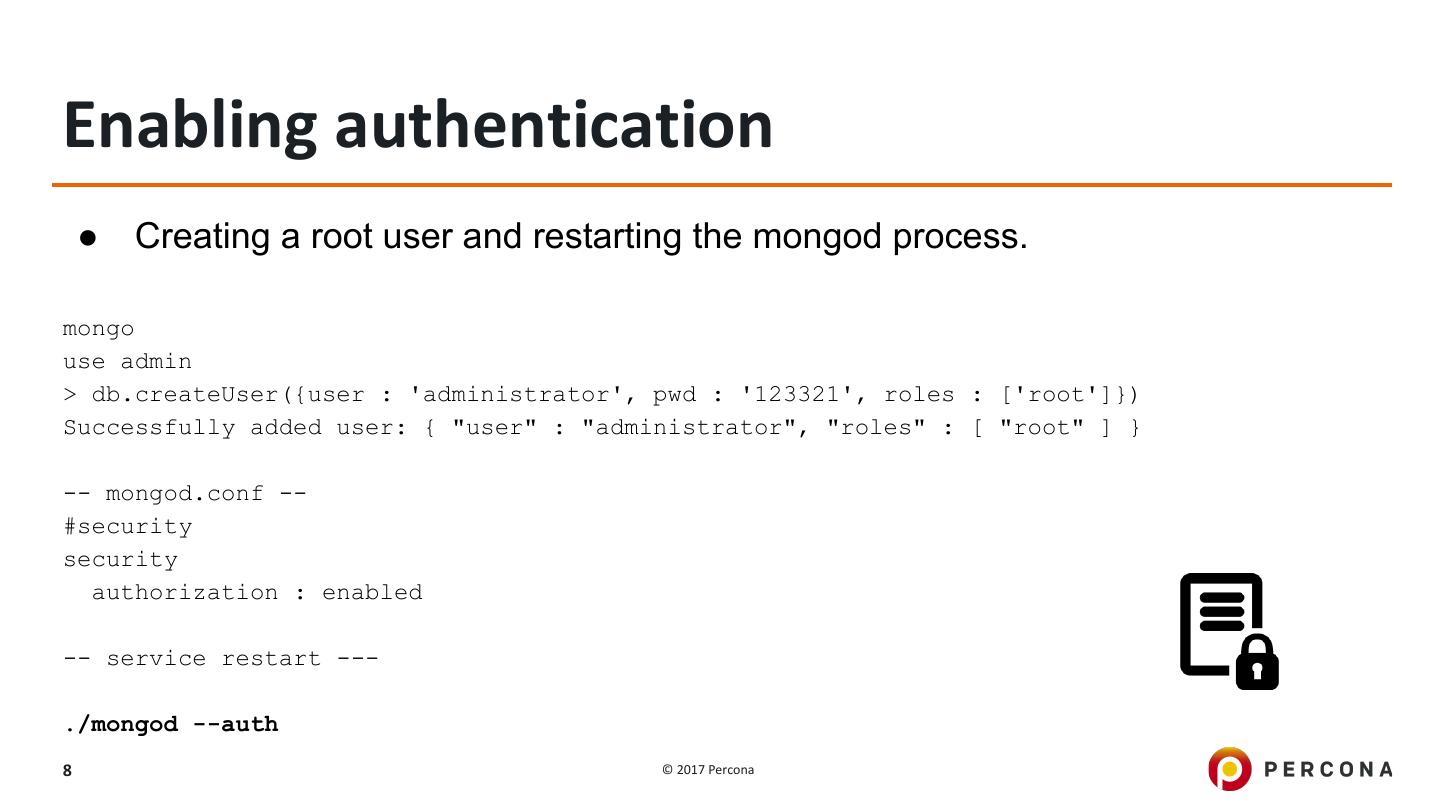
8 .Enabling authentication ● Creating a root user and restarting the mongod process. mongo use admin > db.createUser({user : 'administrator', pwd : '123321', roles : ['root']}) Successfully added user: { "user" : "administrator", "roles" : [ "root" ] } -- mongod.conf -- #security security authorization : enabled -- service restart --- ./mongod --auth 8 © 2017 Percona
9 .Enabling authentication ● Checking access: Mongo > show dbs 2017-04-05T13:39:30.040-0400 E QUERY [thread1] Error: listDatabases failed:{ "ok" : 0, "errmsg" : "not authorized on admin to execute command { listDatabases: 1.0 }", "code" : 13, "codeName" : "Unauthorized" } : 9 © 2017 Percona
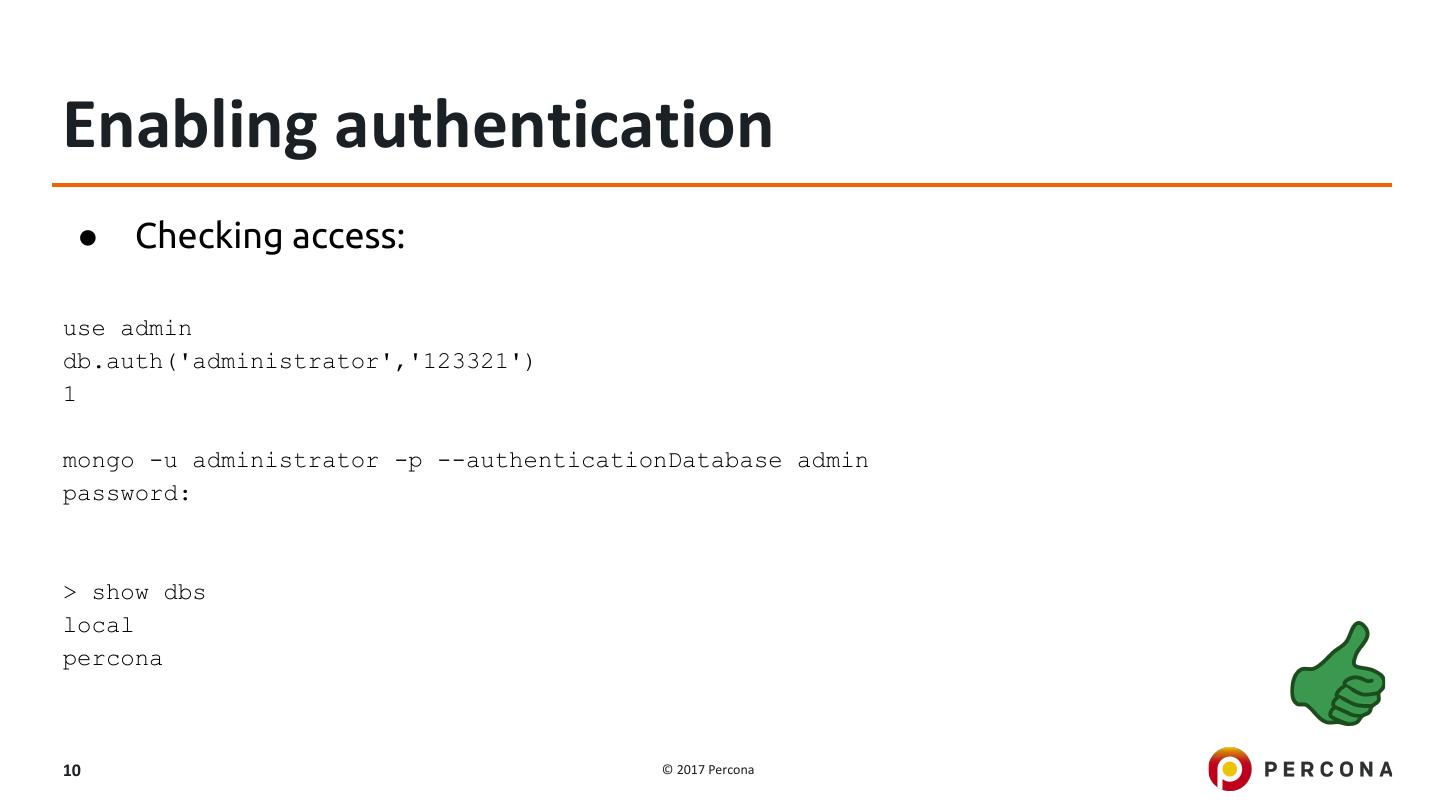
10 .Enabling authentication ● Checking access: use admin db.auth('administrator','123321') 1 mongo -u administrator -p --authenticationDatabase admin password: > show dbs local percona 10 © 2017 Percona
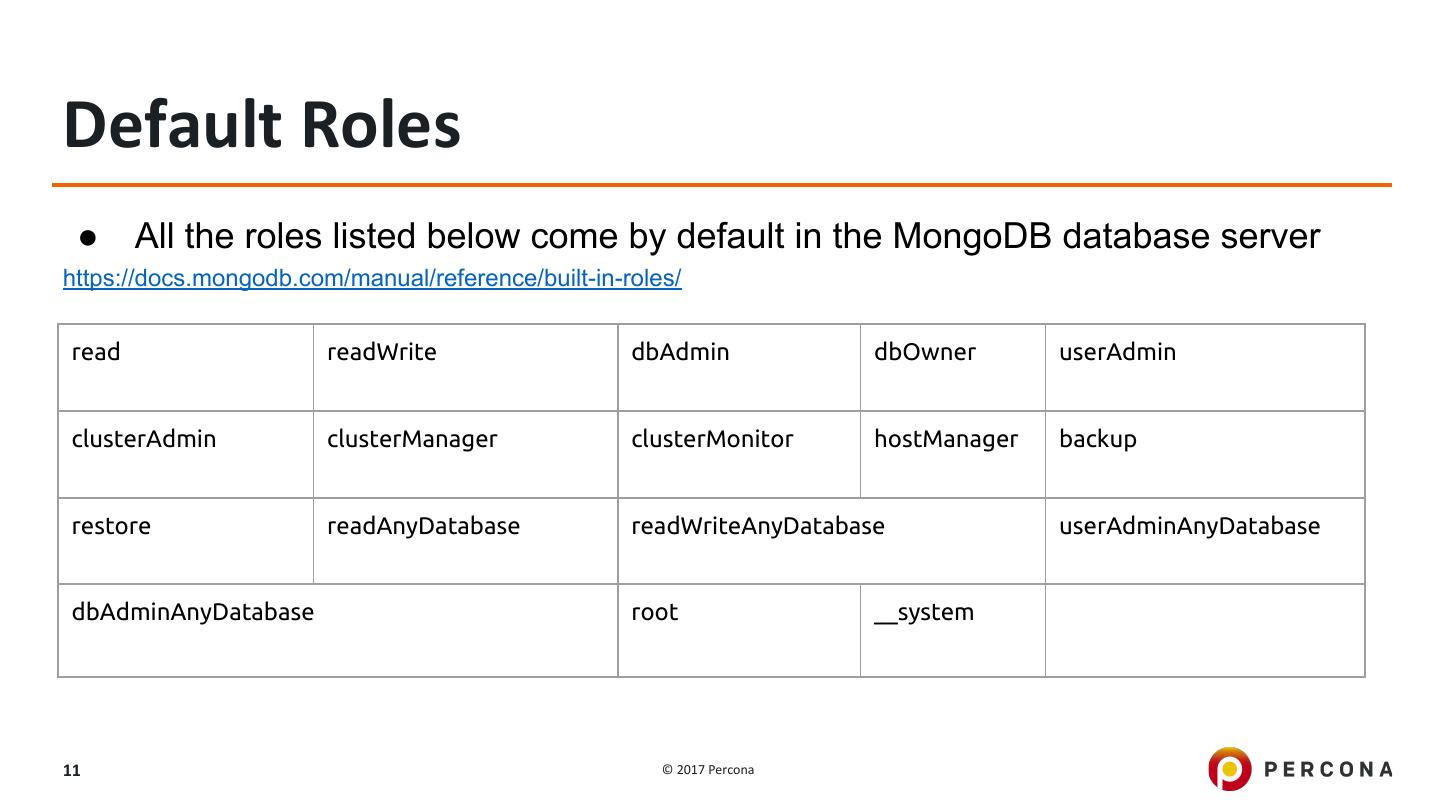
11 .Default Roles ● All the roles listed below come by default in the MongoDB database server https://docs.mongodb.com/manual/reference/built-in-roles/ read readWrite dbAdmin dbOwner userAdmin clusterAdmin clusterManager clusterMonitor hostManager backup restore readAnyDatabase readWriteAnyDatabase userAdminAnyDatabase dbAdminAnyDatabase root __system 11 © 2017 Percona
12 .User Defined Roles ● Users can create their own roles based on the default roles or from scratch to give access to specific collections or commands. ● https://www.percona.com/blog/2017/05/17/mongodb-authentication-and-roles- creating-your-first-personalized-role/ 12 © 2017 Percona
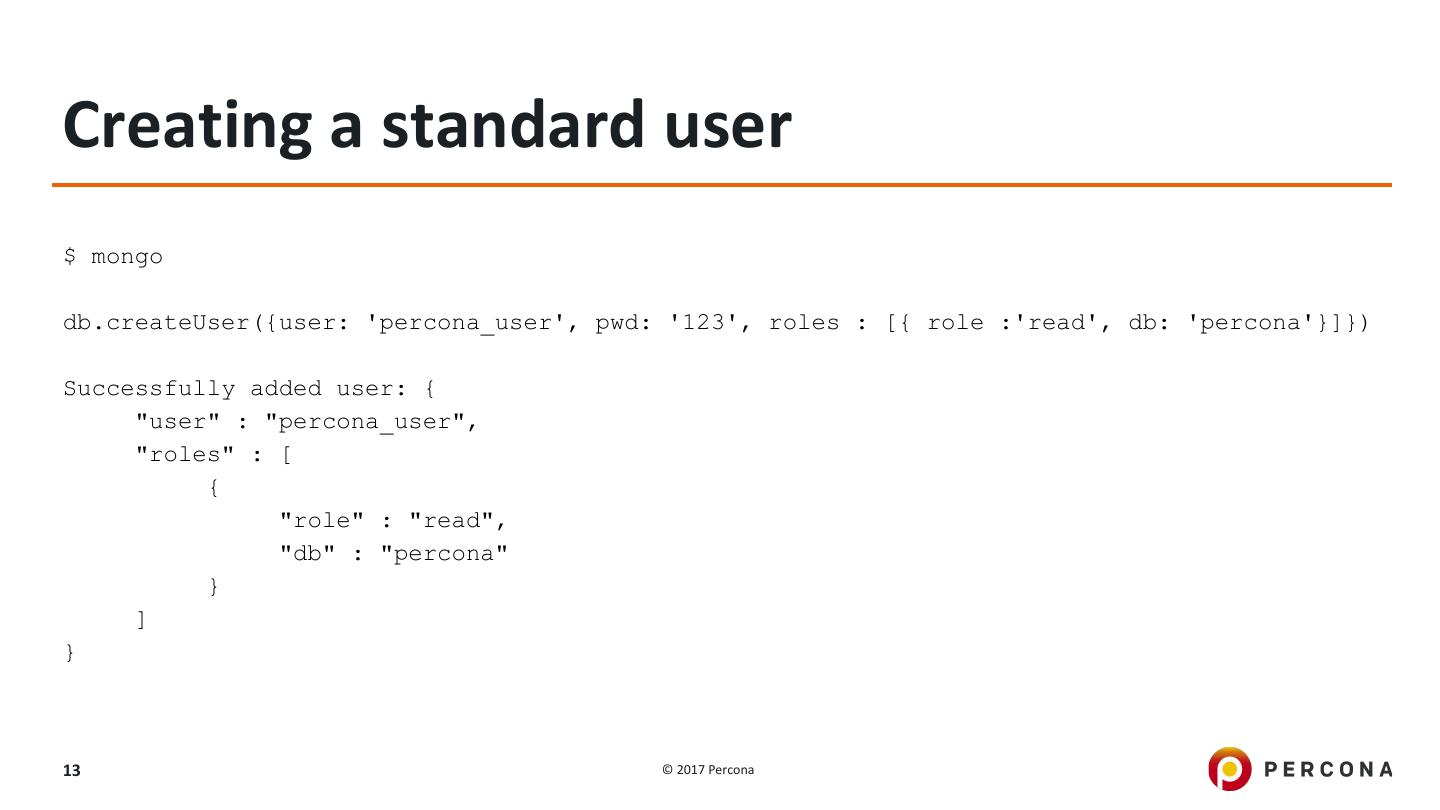
13 .Creating a standard user $ mongo db.createUser({user: 'percona_user', pwd: '123', roles : [{ role :'read', db: 'percona'}]}) Successfully added user: { "user" : "percona_user", "roles" : [ { "role" : "read", "db" : "percona" } ] } 13 © 2017 Percona
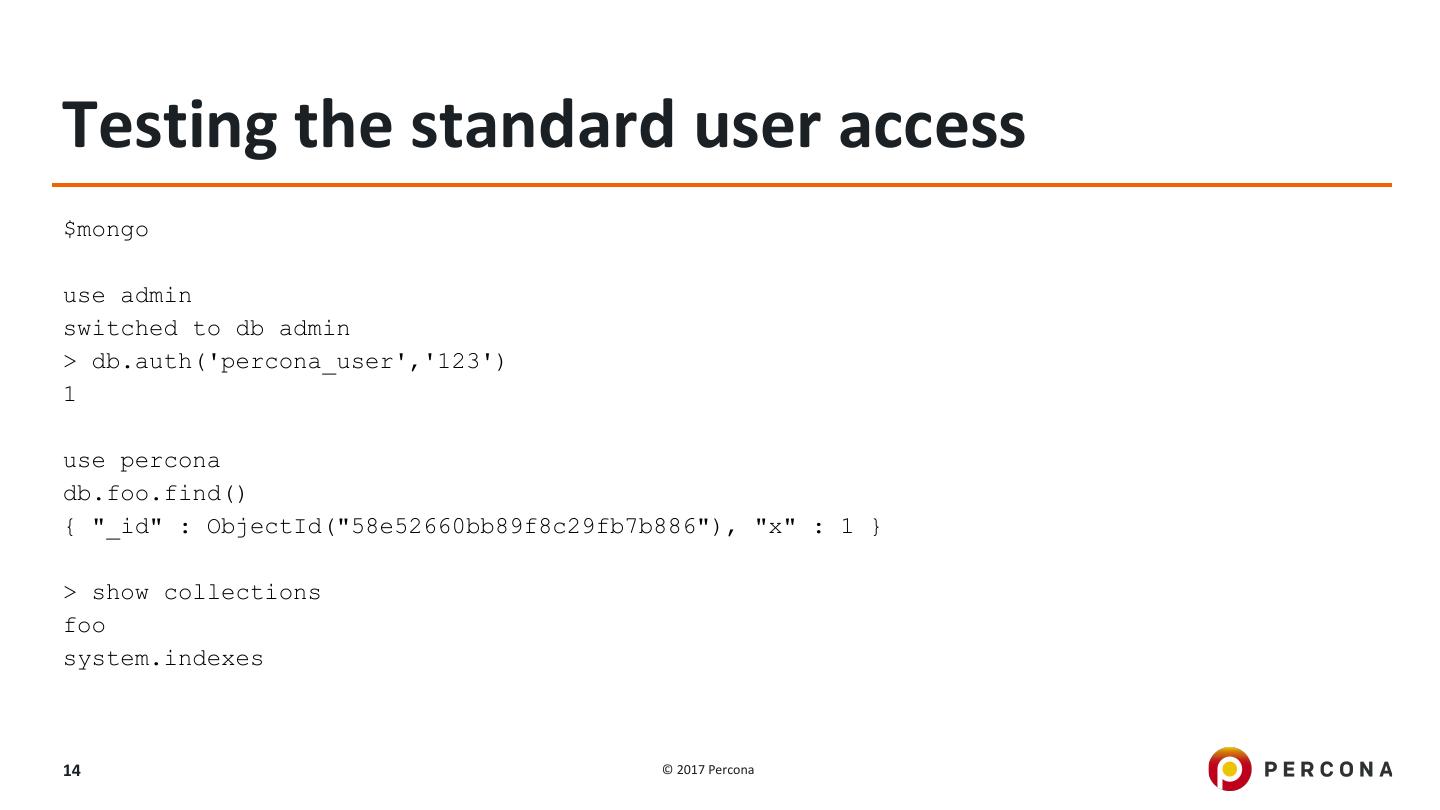
14 .Testing the standard user access $mongo use admin switched to db admin > db.auth('percona_user','123') 1 use percona db.foo.find() { "_id" : ObjectId("58e52660bb89f8c29fb7b886"), "x" : 1 } > show collections foo system.indexes 14 © 2017 Percona
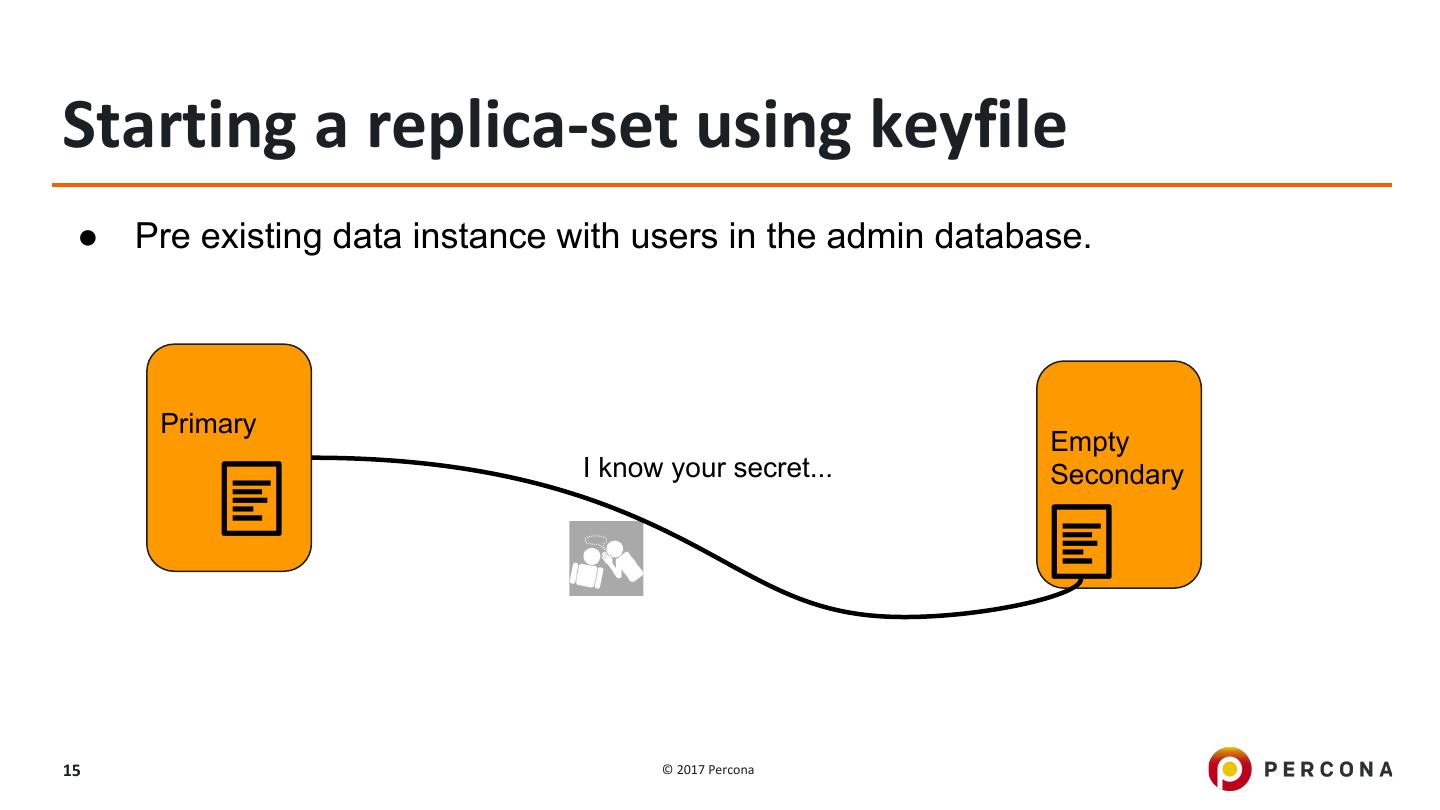
15 .Starting a replica-set using keyfile ● Pre existing data instance with users in the admin database. Primary Empty I know your secret... Secondary 15 © 2017 Percona
16 .Starting a replica-set with key file client Primary __system sync'ed Data... Ok, i can trust you. 16 © 2017 Percona
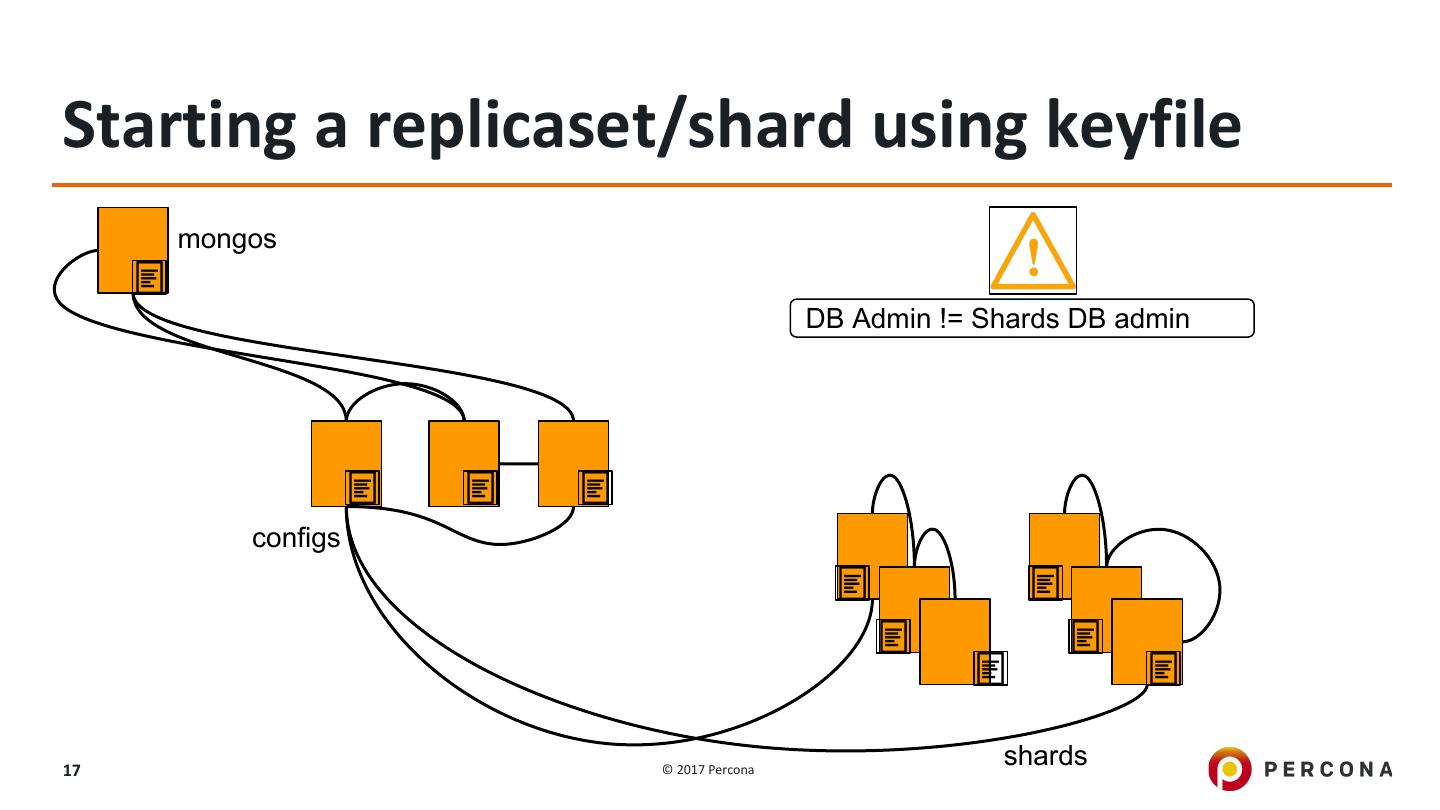
17 .Starting a replicaset/shard using keyfile mongos DB Admin != Shards DB admin configs 17 © 2017 Percona shards
18 .Enhanced security SSL (security socket layer) ● When using keyfiles, the information travels through the wire without any encryption. ● The SSL will encrypt both the communication among the mongod instances and the communication with clients. ● It does requires a CA and valid certificates. 18 © 2017 Percona
19 .Enhanced security LDAP (Lightweight Directory Access Protocol) ● LDAP authentication is a free feature in the Percona Server for MongoDB and it allows companies to use a single password server to authenticate the users. ● This is very useful for big companies whose employee users and passwords are already managed by LDAP or Microsoft Active Directory. 19 © 2017 Percona
20 .Enhanced security LDAP (Lightweight Directory Access Protocol) ● Instead of keeping the user/pass on the database only the user exists on the database using an external tool to authenticate. ● https://www.percona.com/blog/2017/03/16/percona-server-for-mongodb-dashi ng-new-ldap-authentication-plugin/ 20 © 2017 Percona
21 .Enhanced security Audit ● Percona server for mongodb comes with the audit plugin, this plugin is also free on our version it allows you to generate logs from a specific filter. ● https://www.percona.com/doc/percona-server-for-mongodb/LATEST/audit-log ging.html 21 © 2017 Percona
22 .Enhanced security Backups ● How do you store your backups? ● Do you use at least a password or encryption? ● Have you ever tested your backup? 22 © 2017 Percona
23 . Live Demo and Questions DEMO db.createUser({user: 'percona_user', pwd: '123', roles : [{ role :'read', db: 'percona'}]}) wget https://fastdl.mongodb.org/osx/mongodb-osx-ssl-x86_64-3.4.7.tgz tar -xvzf mongodb-osx-ssl-x86_64-3.4.7.tgz Test; mv mongodb-osx-x86_64-3.4.7/ mongo34 cd mongo34/ db.createRole({ cd bin/ role : 'read_perconaAndListDBs', ./mongod --dbpath data --logpath data/log.log --fork --auth privileges : [ {resource : {cluster : true}, actions : ["listDatabases"] }], ./mongo roles : [{ role: "read", db: "percona"}] use admin }) db.createUser({user : 'administrator', pwd : '123321', roles : ['root']}) db.auth('administrator','123321') db.revokeRolesFromUser('percona_user', [{ role :'read', db: 'percona'}]) db.grantRolesToUser('percona_user', ["read_perconaAndListDBs"]) use percona db.foo.insert({x : 1}); ./mongo -u administrator -p --authenticationDatabase admin use percona1 db.foo.insert({y : 1}) use percona2 db.foo.insert({z : 1}) use admin 23 © 2017 Percona
24 .Get Your Tickets for Percona Live Europe! Championing Open Source Databases ● MySQL, MongoDB, Open Source Databases ● Time Series Databases, PostgreSQL, RocksDB ● Developers, Business/Case Studies, Operations ● September 25-27th, 2017 ● Radisson Blu Royal Hotel, Dublin, Ireland Advanced Reg Tickets Available Until Sep 5th! 24 © 2017 Percona
25 . DATABASE PERFORMANCE Database Performance Matters MATTERS