- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
增强MongoDB默认安全性
在这个时代,在我们的电子通信中保持隐私是绝对必要的。创建用户帐户,而不是将MongoDB环境暴露在更广泛的互联网上,这是过去一直被忽略的基本概念。一旦解决了这一问题,有兴趣成为符合PCI标准的个人和组织必须转向通过加密保护其数据。对于MongoDB,我们有两个加密选项:静态(仅作为MongoDB的企业功能提供)和传输加密。
在本次会议中,我们将回顾
-MongoDB默认安全性
-附加安全层
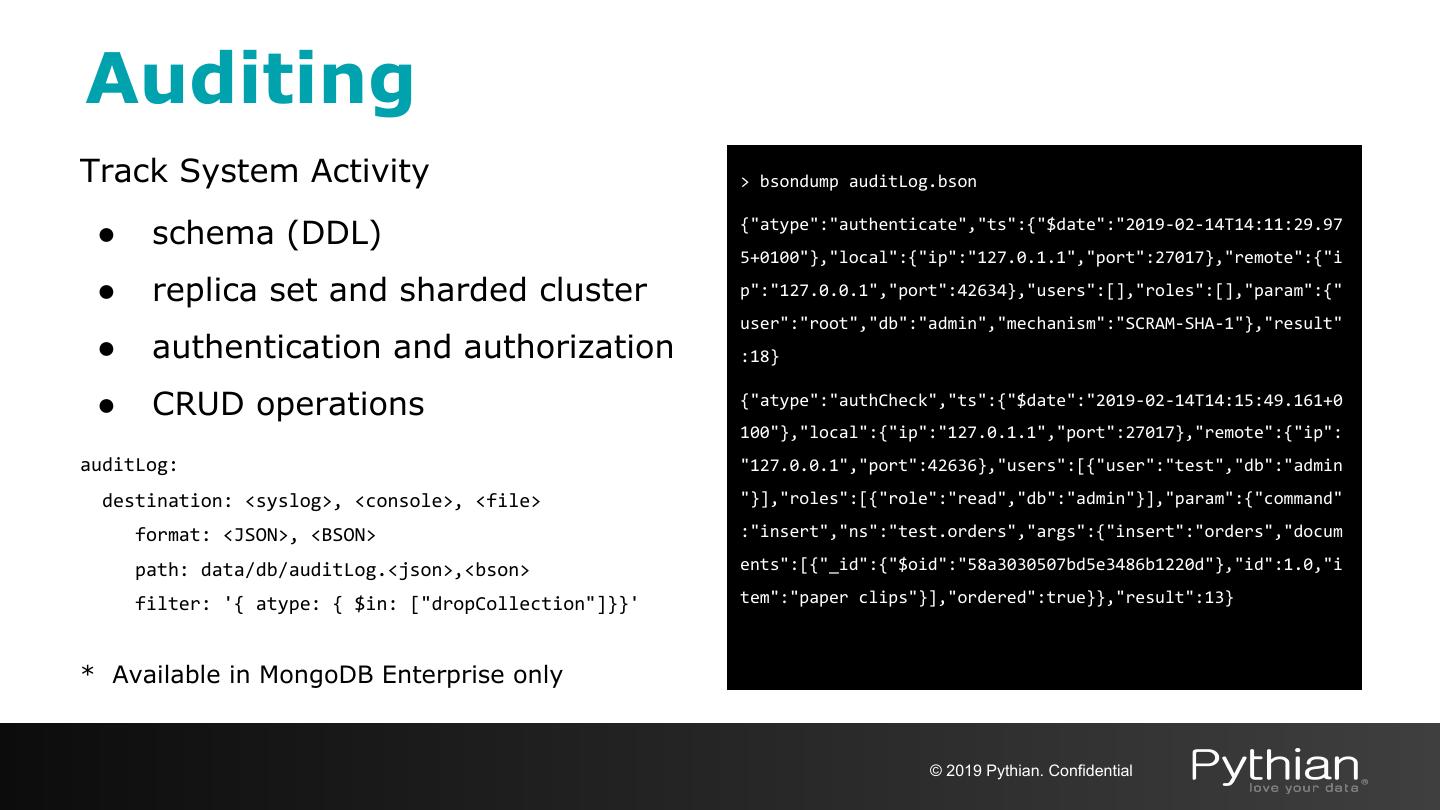
-审核和减少日志
-加密及其重要原因
-在静止和传输中逐步加密
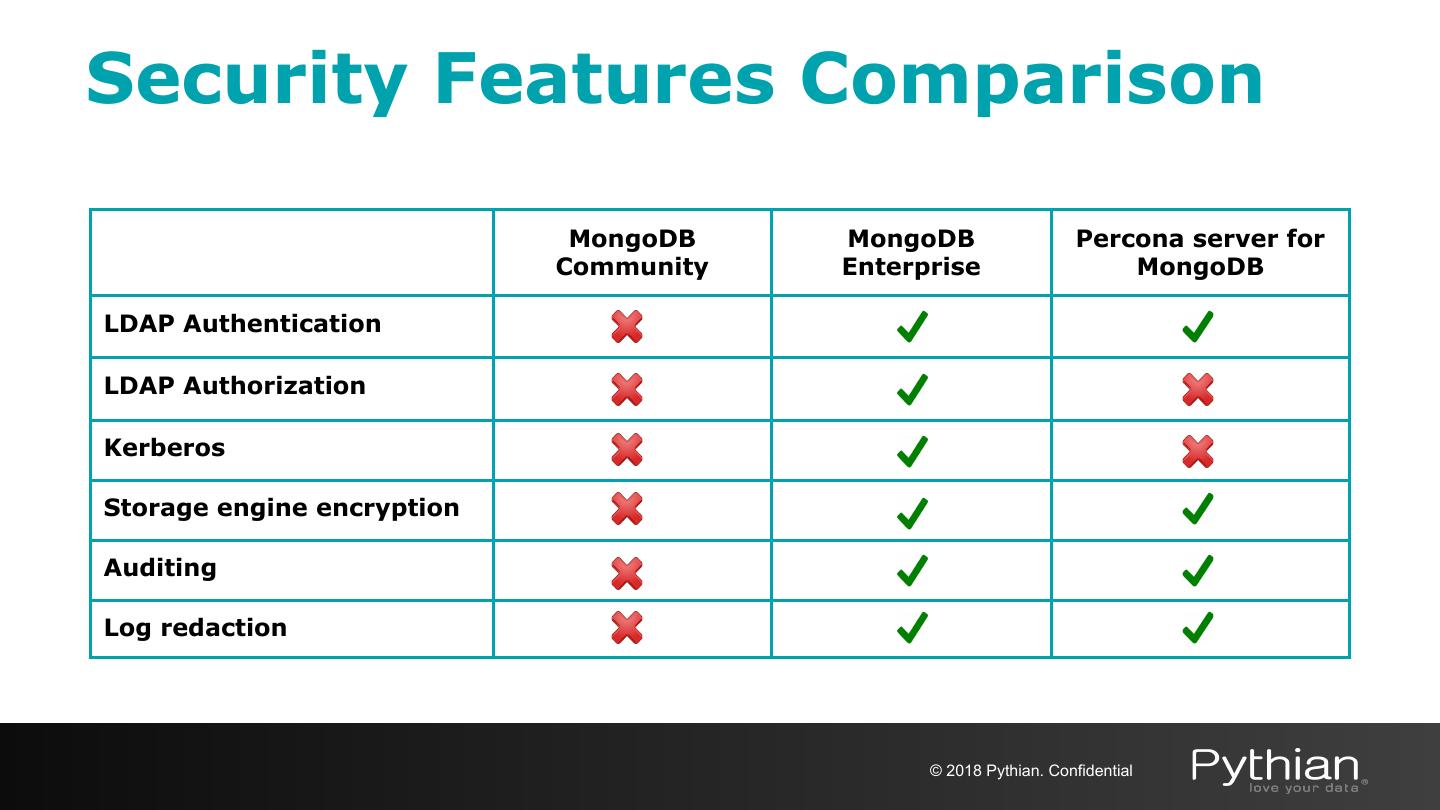
-Percona for MongoDB安全功能
展开查看详情
1 .Enhancing the Default MongoDB Security May-30-2019
2 . About Me {"name": "Igor Donchovski", "live_in": "Skopje", "email": "donchovski@pythian.com", "current_role": "Lead database consultant", "education": [{"type": "College", "name": "FEIT", "graduated": "2008", "university": "UKIM"}, {"type": "Master", "name": "FINKI", "graduated": "2013", "university": "UKIM"}], "work": [{"role": "Web developer", "start": "2007", "end": "2012", "company": "Gord Systems"}, {"role": "DBA", "start": "2012", "end": "2014", "company": "NOVP"}, {"role": "Database consultant", "start": "2014", "end": "2016", "company": "Pythian"}, {"role": "Lead database consultant", "start": "2016", "company": "Pythian"}], "certificates": [{"name": "C100DBA", "year": "2016", "description": "MongoDB certified DBA"}], "social": [{"network": "LinkedIn", "url": "https://mk.linkedin.com/in/igorle"}, {"network": "Twitter", "url": "https://twitter.com/igorle"}], "interests": ["Hiking", "Biking", "Traveling"], "hobbies": ["Painting", "Photography", "Cooking"], "proud_of": ["Volunteering", "Helping the Community"]} © 2019 Pythian. Confidential
3 .Overview • Default security • Access control • Authentication and Authorization • Network hardening • Encryption in Transit • Encryption at REST • Auditing • QA © 2019 Pythian. Confidential
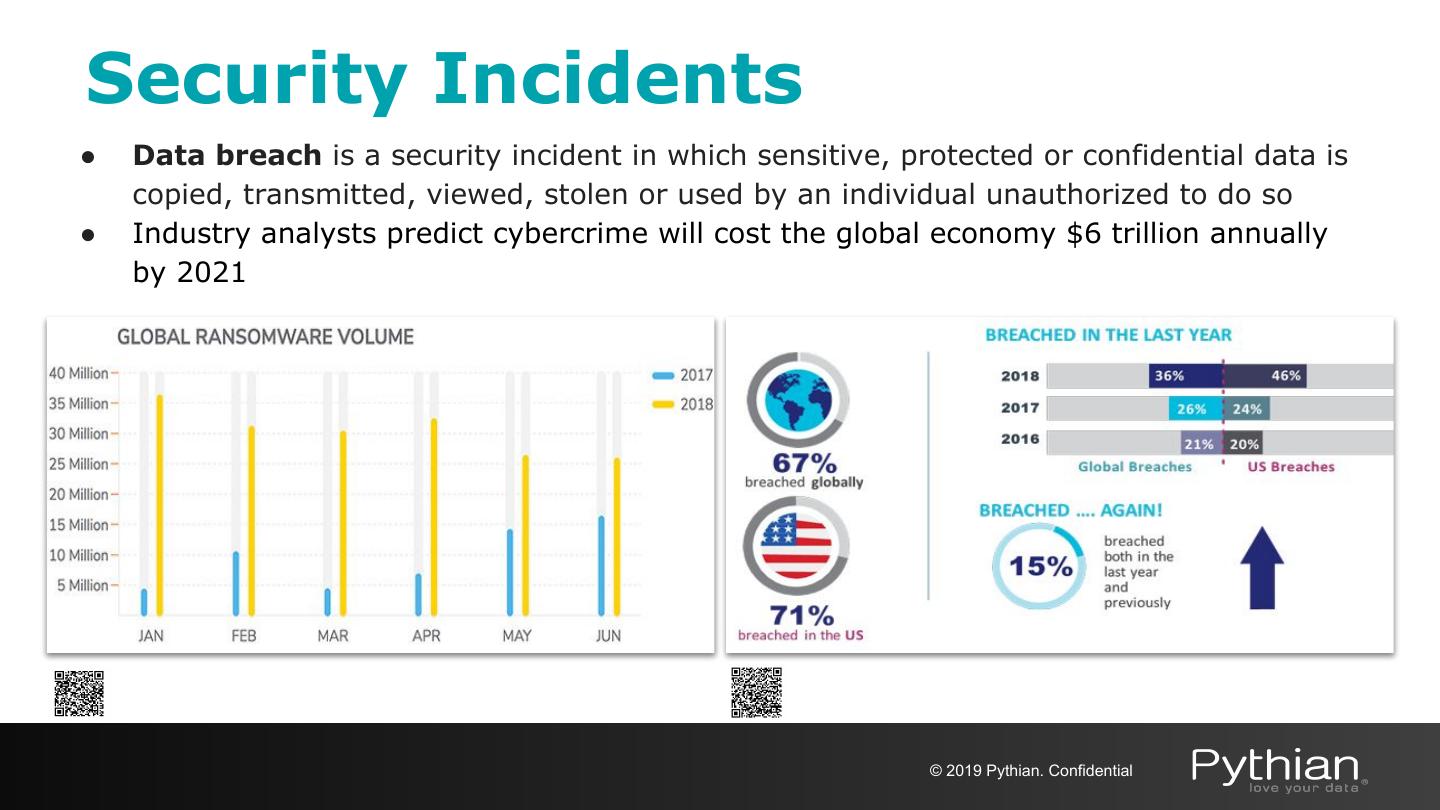
4 .Security Incidents ● Data breach is a security incident in which sensitive, protected or confidential data is copied, transmitted, viewed, stolen or used by an individual unauthorized to do so ● Industry analysts predict cybercrime will cost the global economy $6 trillion annually by 2021 © 2019 Pythian. Confidential
5 .Defaults © 2019 Pythian. Confidential
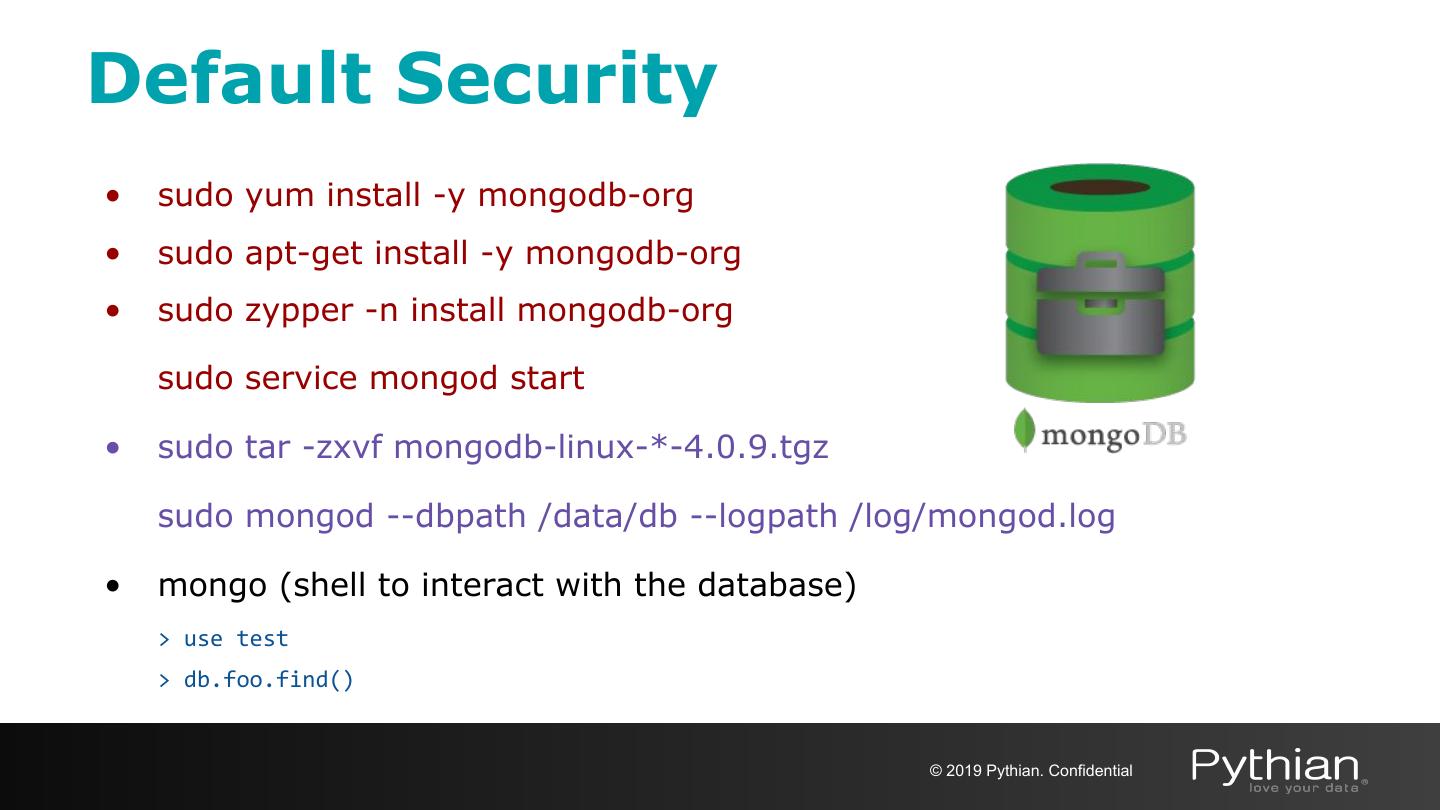
6 .Default Security • sudo yum install -y mongodb-org • sudo apt-get install -y mongodb-org • sudo zypper -n install mongodb-org sudo service mongod start • sudo tar -zxvf mongodb-linux-*-4.0.9.tgz sudo mongod --dbpath /data/db --logpath /log/mongod.log • mongo (shell to interact with the database) > use test > db.foo.find() © 2019 Pythian. Confidential
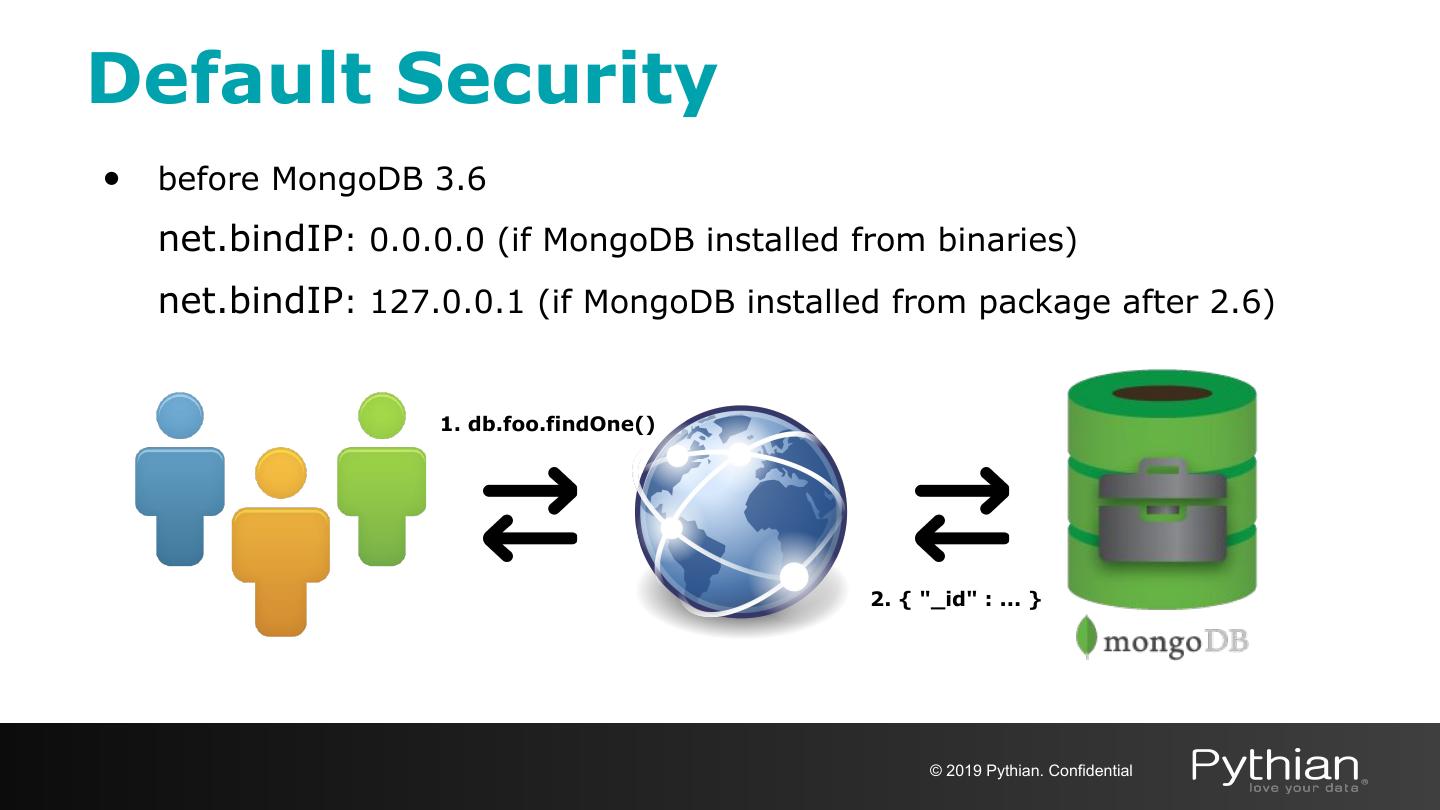
7 .Default Security • before MongoDB 3.6 net.bindIP: 0.0.0.0 (if MongoDB installed from binaries) net.bindIP: 127.0.0.1 (if MongoDB installed from package after 2.6) 1. db.foo.findOne() 2. { "_id" : ... } © 2019 Pythian. Confidential
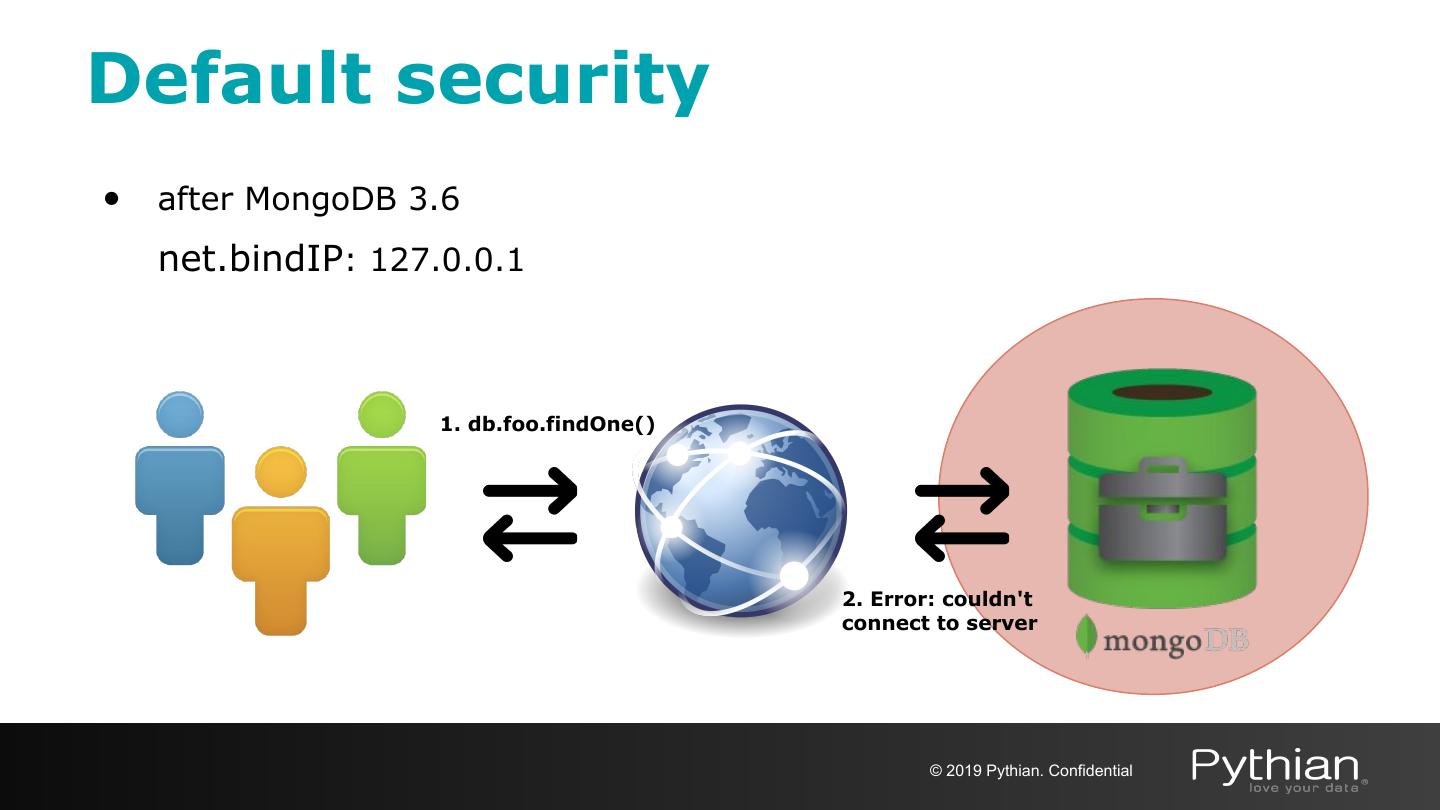
8 .Default security • after MongoDB 3.6 net.bindIP: 127.0.0.1 1. db.foo.findOne() 2. Error: couldn't connect to server © 2019 Pythian. Confidential
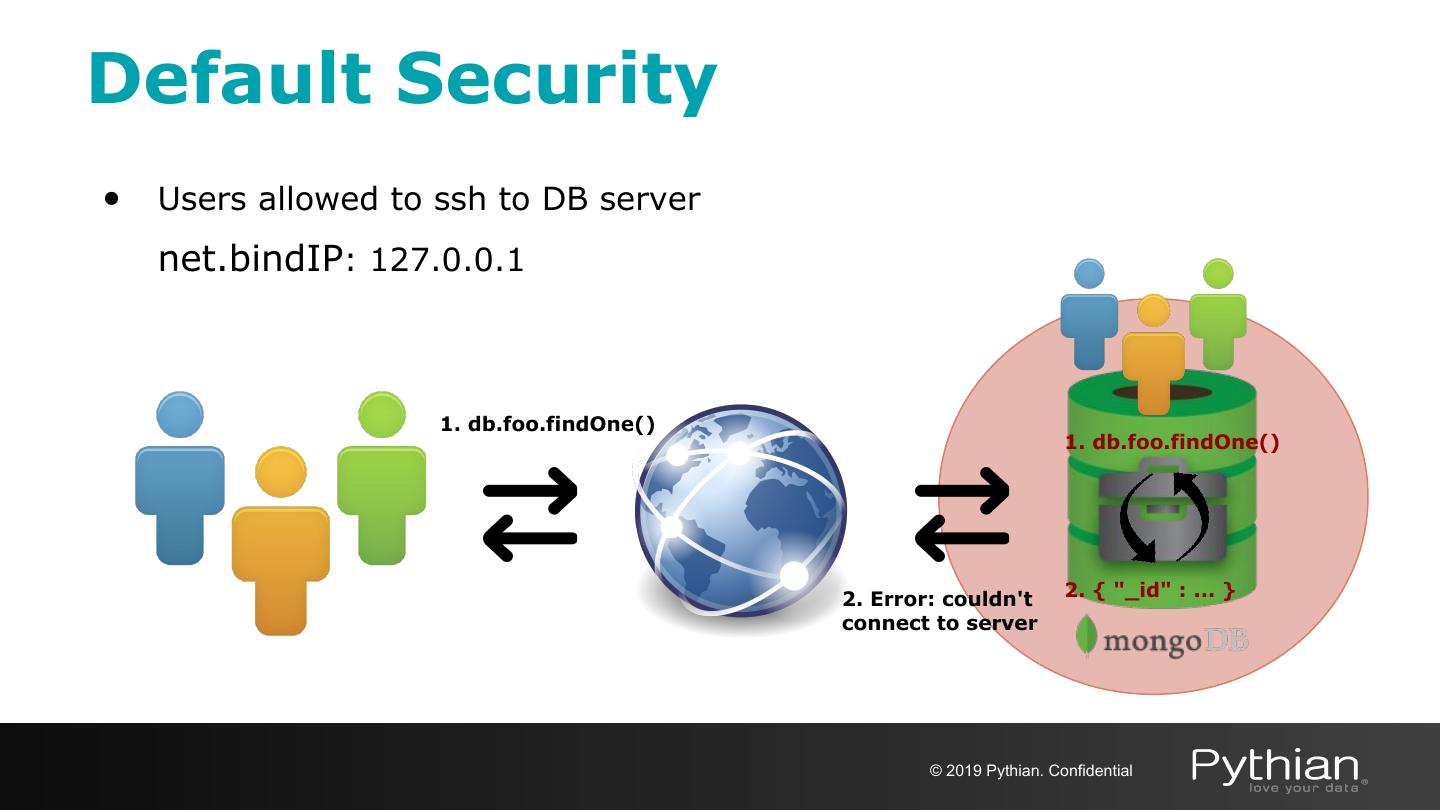
9 .Default Security • Users allowed to ssh to DB server net.bindIP: 127.0.0.1 1. db.foo.findOne() 1. db.foo.findOne() 2. Error: couldn't 2. { "_id" : ... } connect to server © 2019 Pythian. Confidential
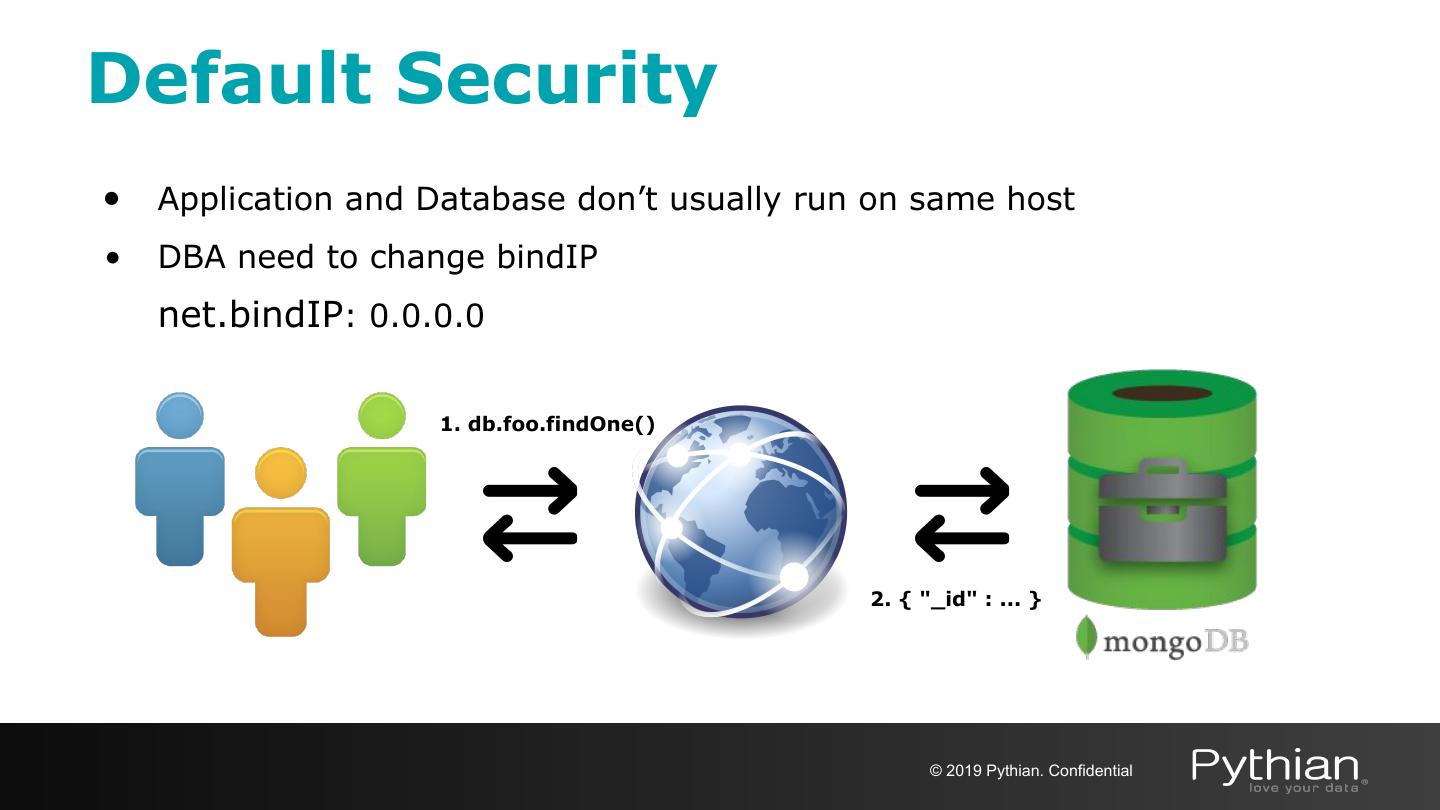
10 .Default Security • Application and Database don’t usually run on same host • DBA need to change bindIP net.bindIP: 0.0.0.0 1. db.foo.findOne() 2. { "_id" : ... } © 2019 Pythian. Confidential
11 .Access Control © 2019 Pythian. Confidential
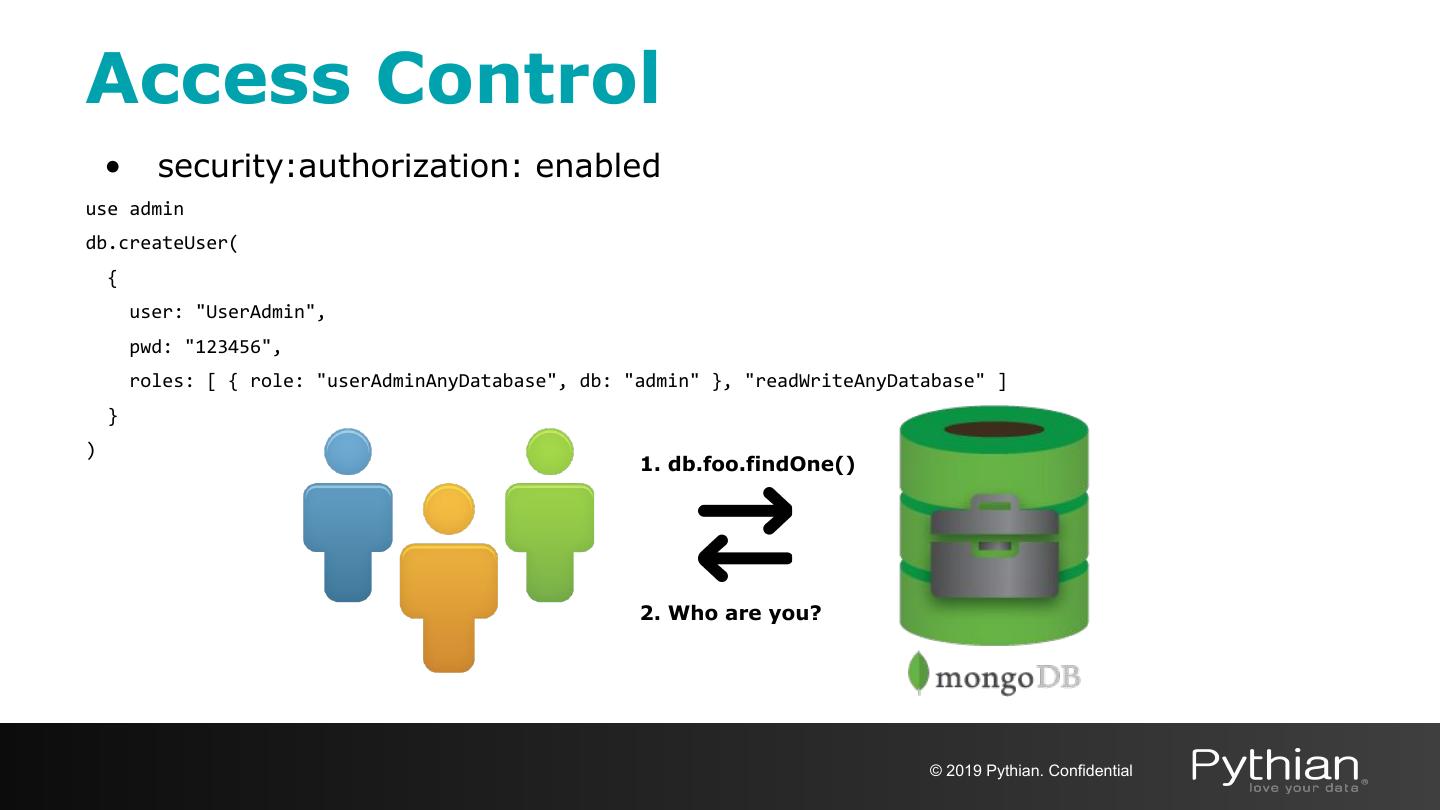
12 .Access Control • security:authorization: enabled use admin db.createUser( { user: "UserAdmin", pwd: "123456", roles: [ { role: "userAdminAnyDatabase", db: "admin" }, "readWriteAnyDatabase" ] } ) 1. db.foo.findOne() 2. Who are you? © 2019 Pythian. Confidential
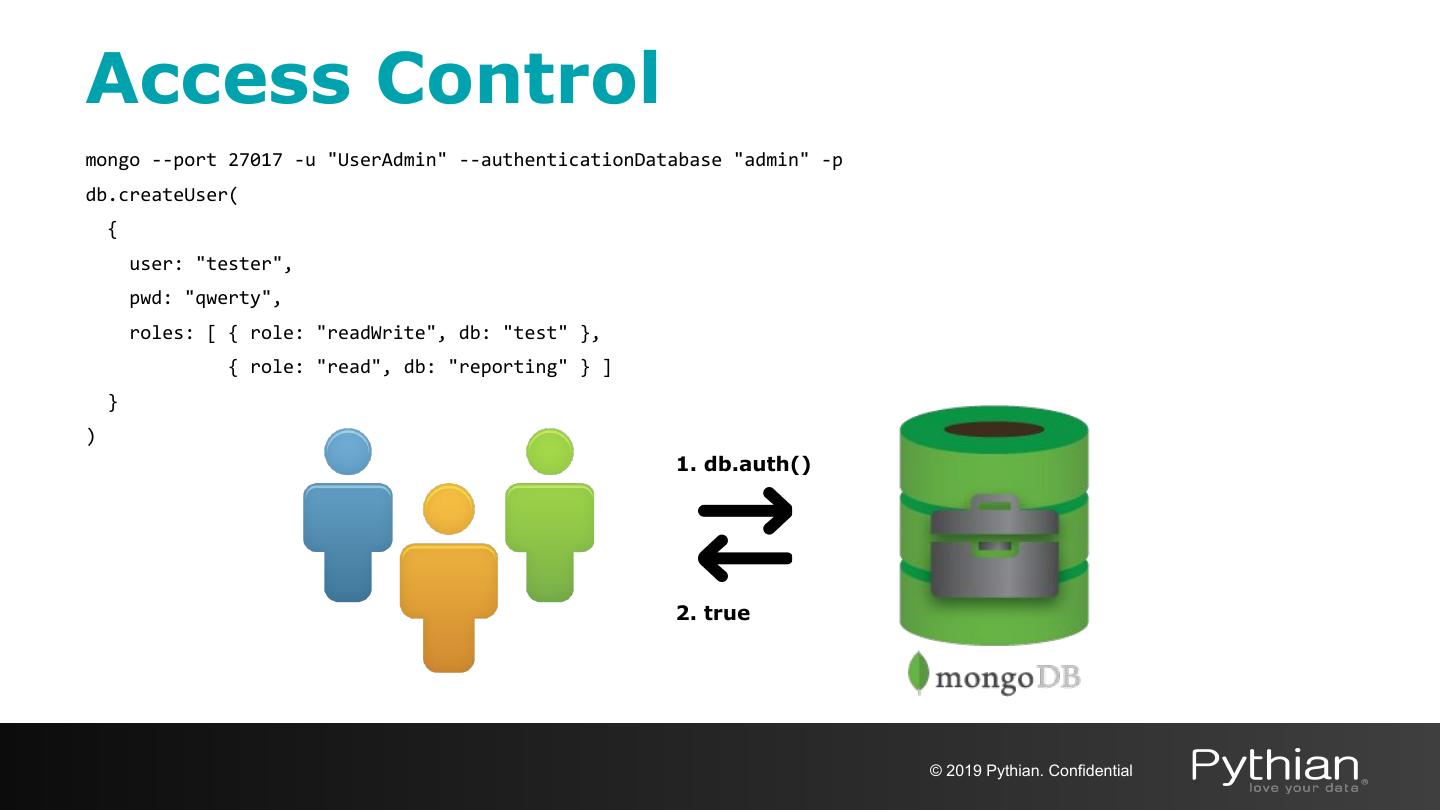
13 .Access Control mongo --port 27017 -u "UserAdmin" --authenticationDatabase "admin" -p db.createUser( { user: "tester", pwd: "qwerty", roles: [ { role: "readWrite", db: "test" }, { role: "read", db: "reporting" } ] } ) 1. db.auth() 2. true © 2019 Pythian. Confidential
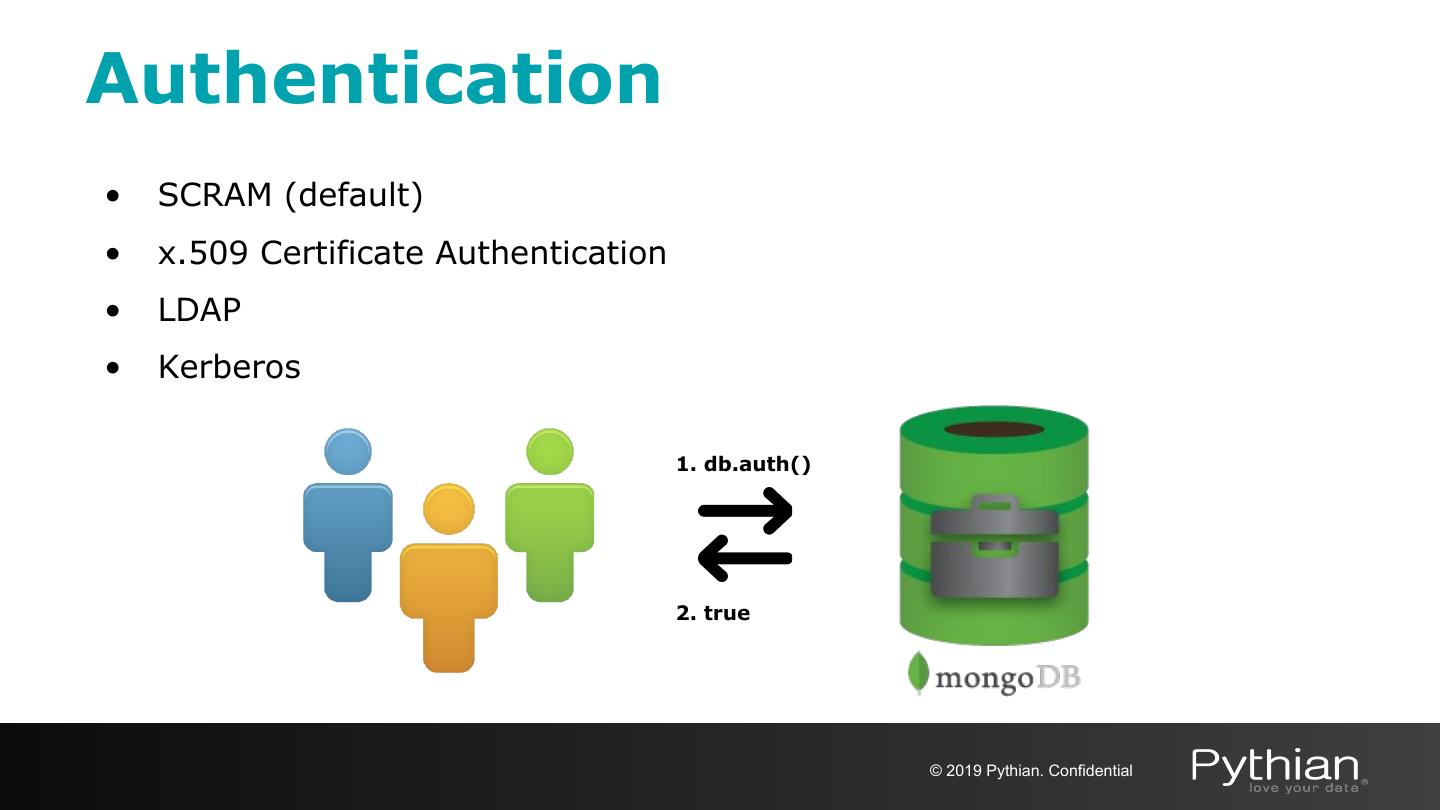
14 .Authentication • SCRAM (default) • x.509 Certificate Authentication • LDAP • Kerberos 1. db.auth() 2. true © 2019 Pythian. Confidential
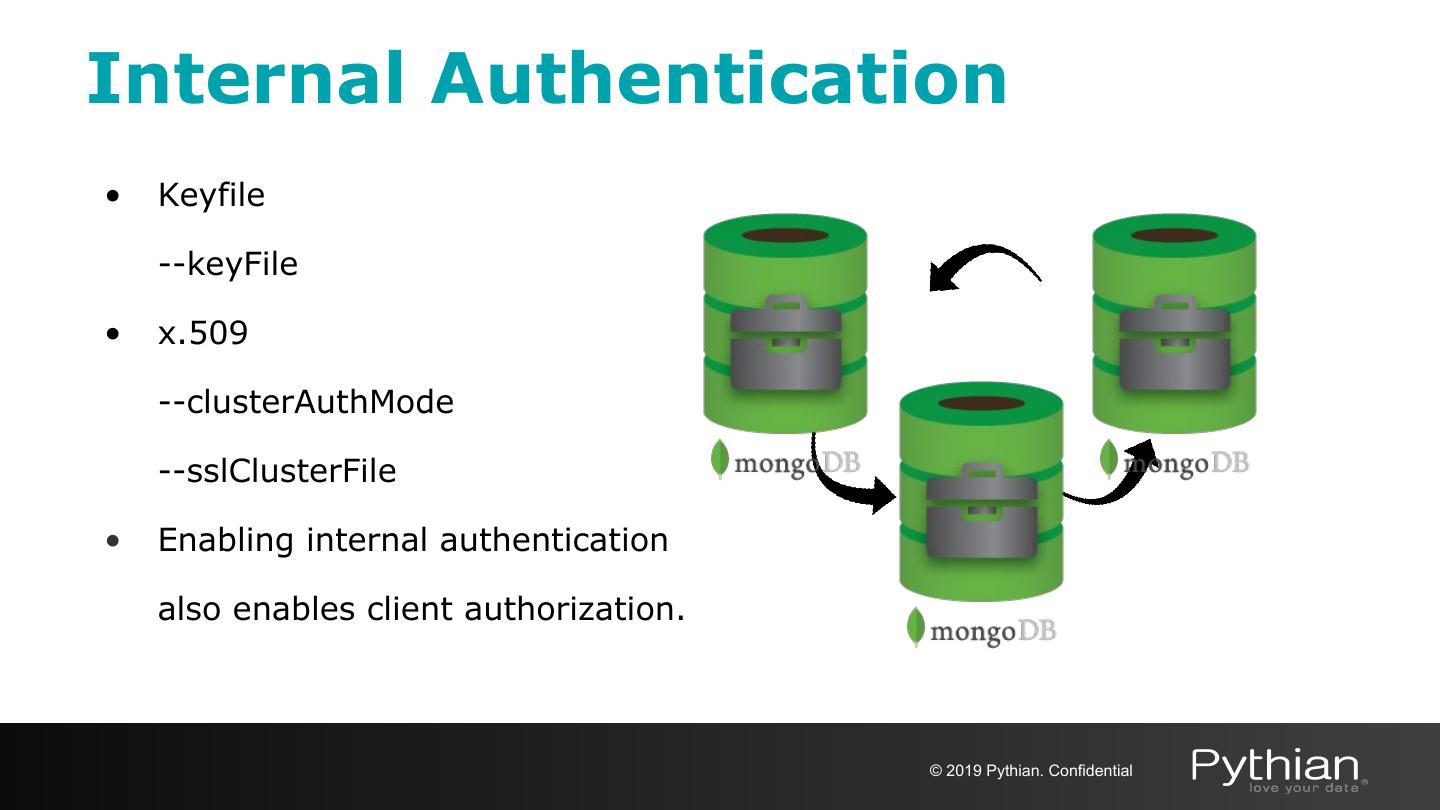
15 .Internal Authentication • Keyfile --keyFile • x.509 --clusterAuthMode --sslClusterFile • Enabling internal authentication also enables client authorization. © 2019 Pythian. Confidential
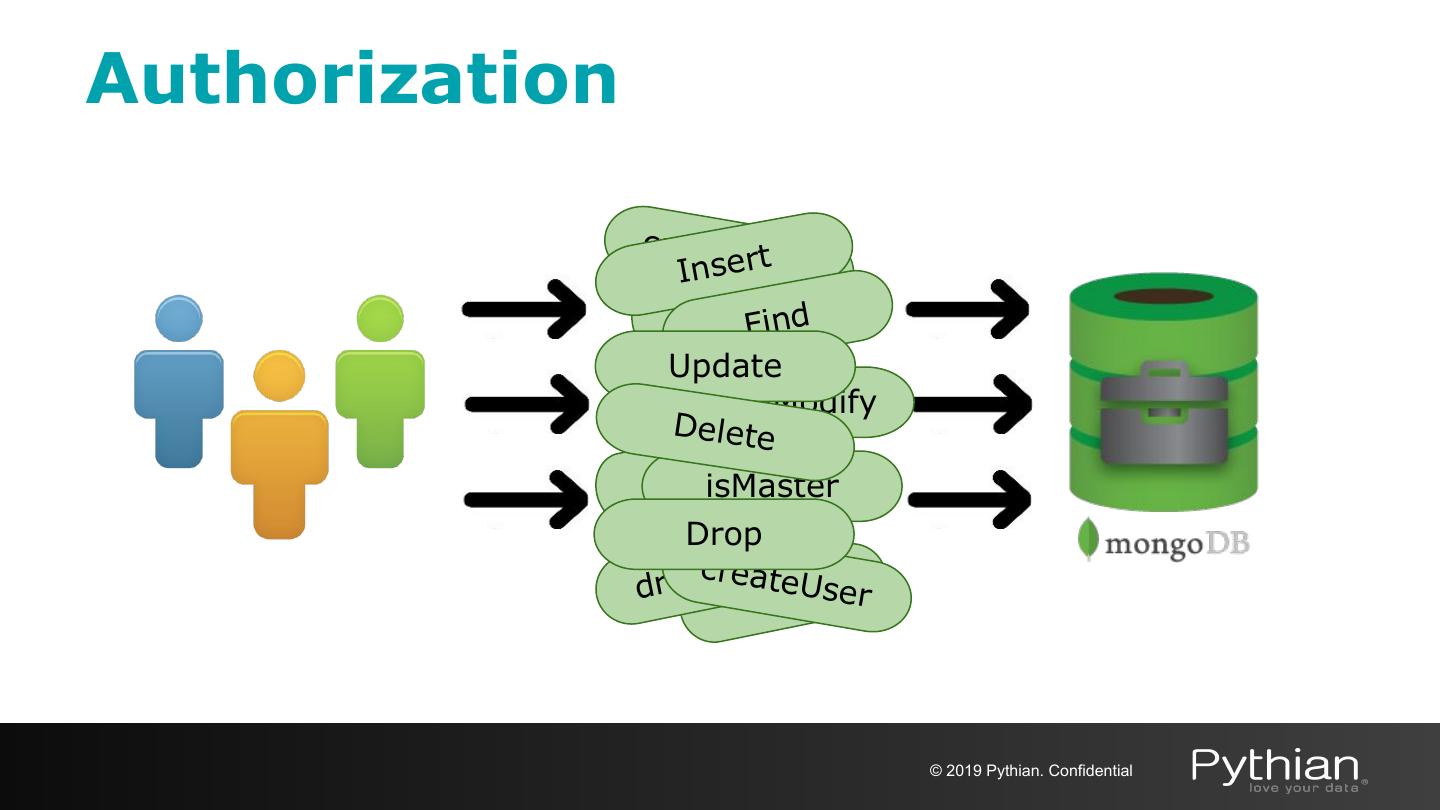
16 .Authorization create InseUrtser DropFind Update findAndModify Delete DropisMaster Drop arteU cr se dropUeD ropser © 2019 Pythian. Confidential
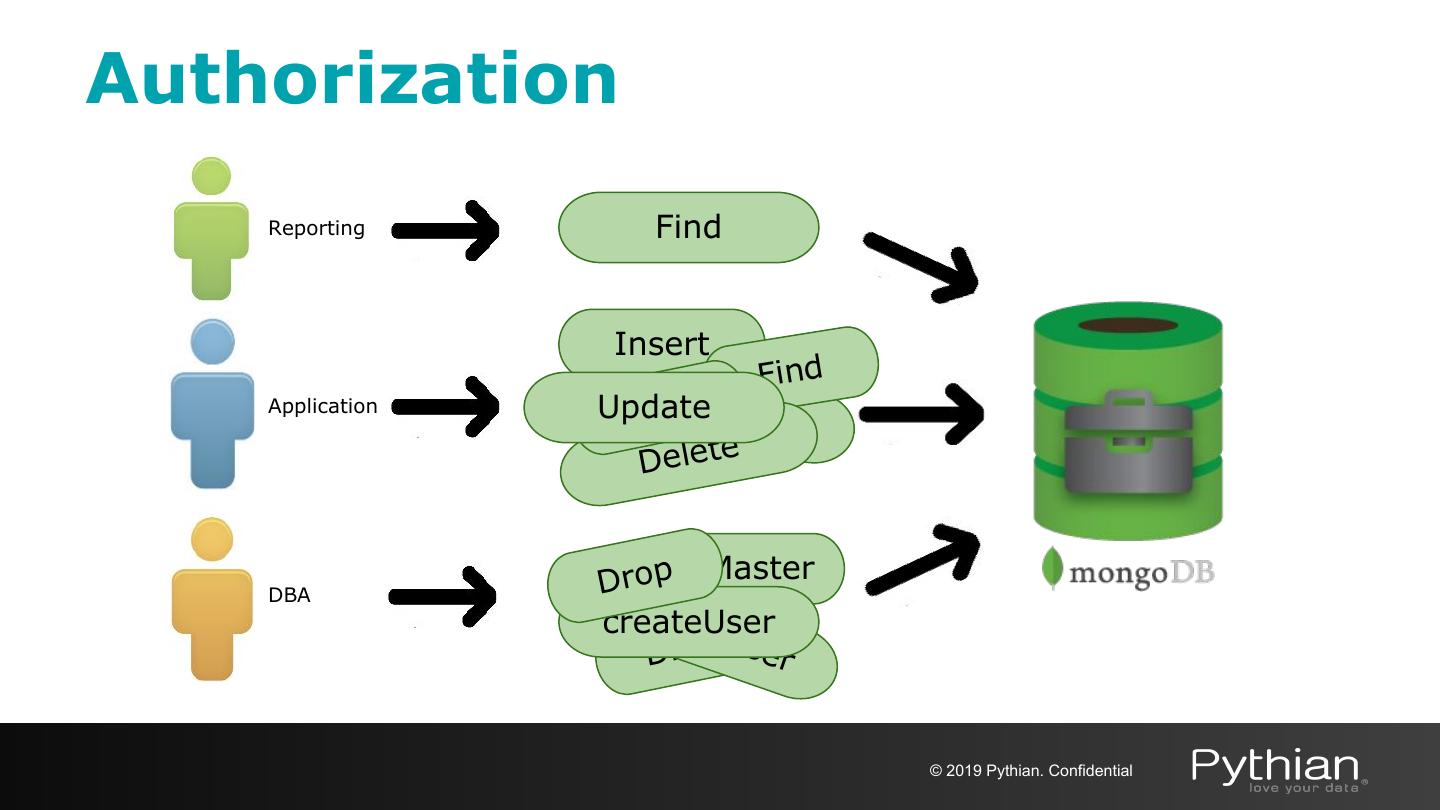
17 .Authorization Reporting Find Insert Find Application DcrroepateUser Update Delete DBA Drop isMaster cre ate createUserU D op ser r © 2019 Pythian. Confidential
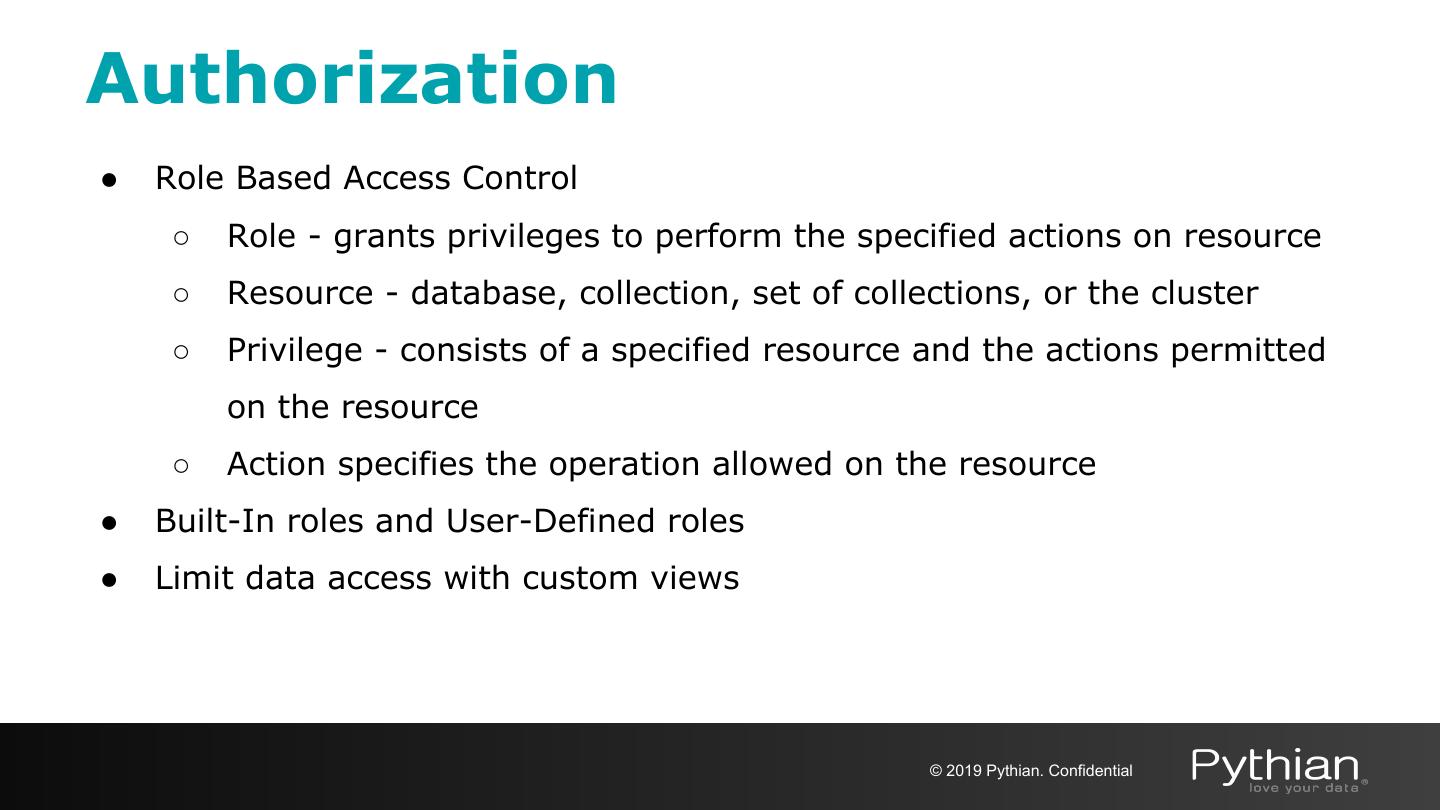
18 .Authorization ● Role Based Access Control ○ Role - grants privileges to perform the specified actions on resource ○ Resource - database, collection, set of collections, or the cluster ○ Privilege - consists of a specified resource and the actions permitted on the resource ○ Action specifies the operation allowed on the resource ● Built-In roles and User-Defined roles ● Limit data access with custom views © 2019 Pythian. Confidential
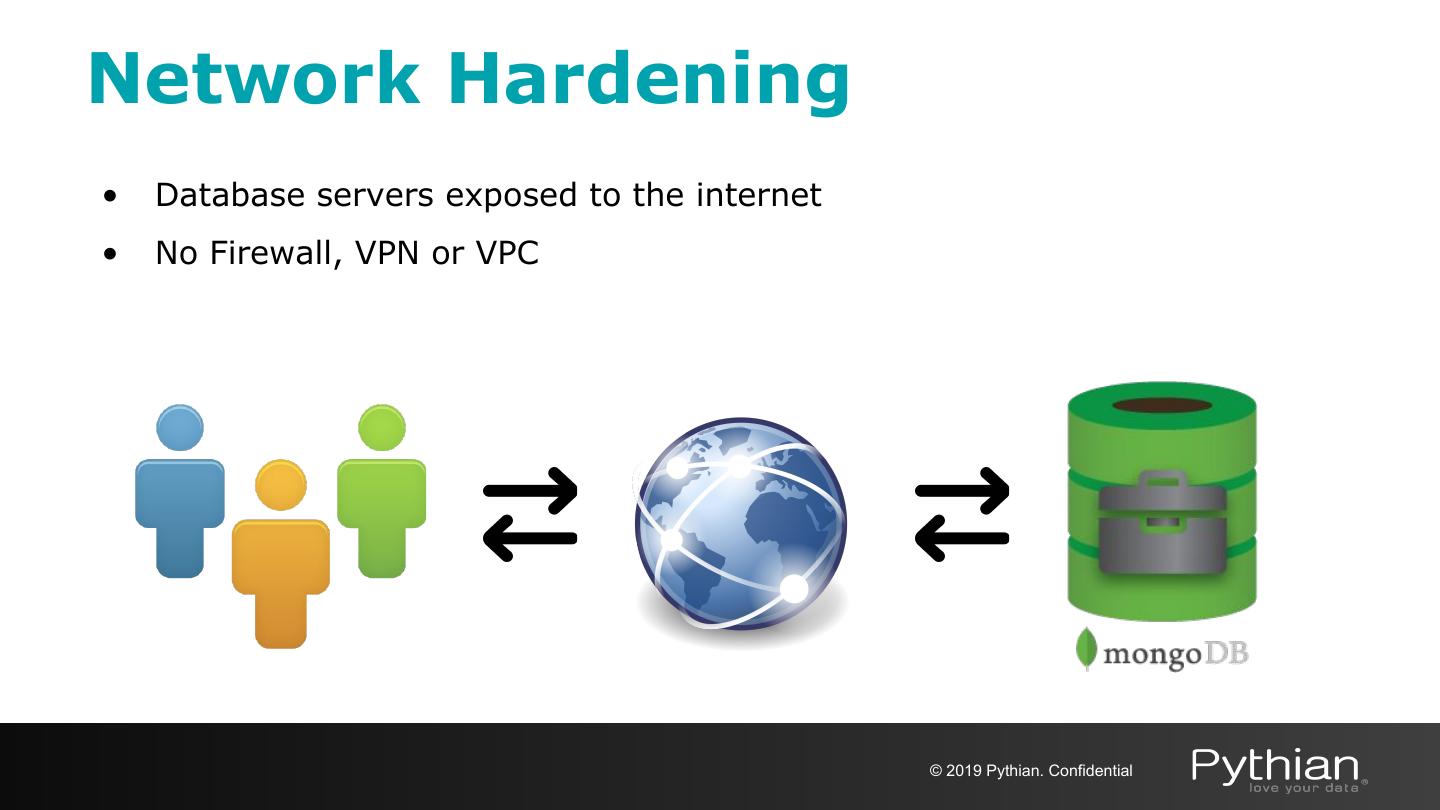
19 .Network Hardening • Database servers exposed to the internet • No Firewall, VPN or VPC © 2019 Pythian. Confidential
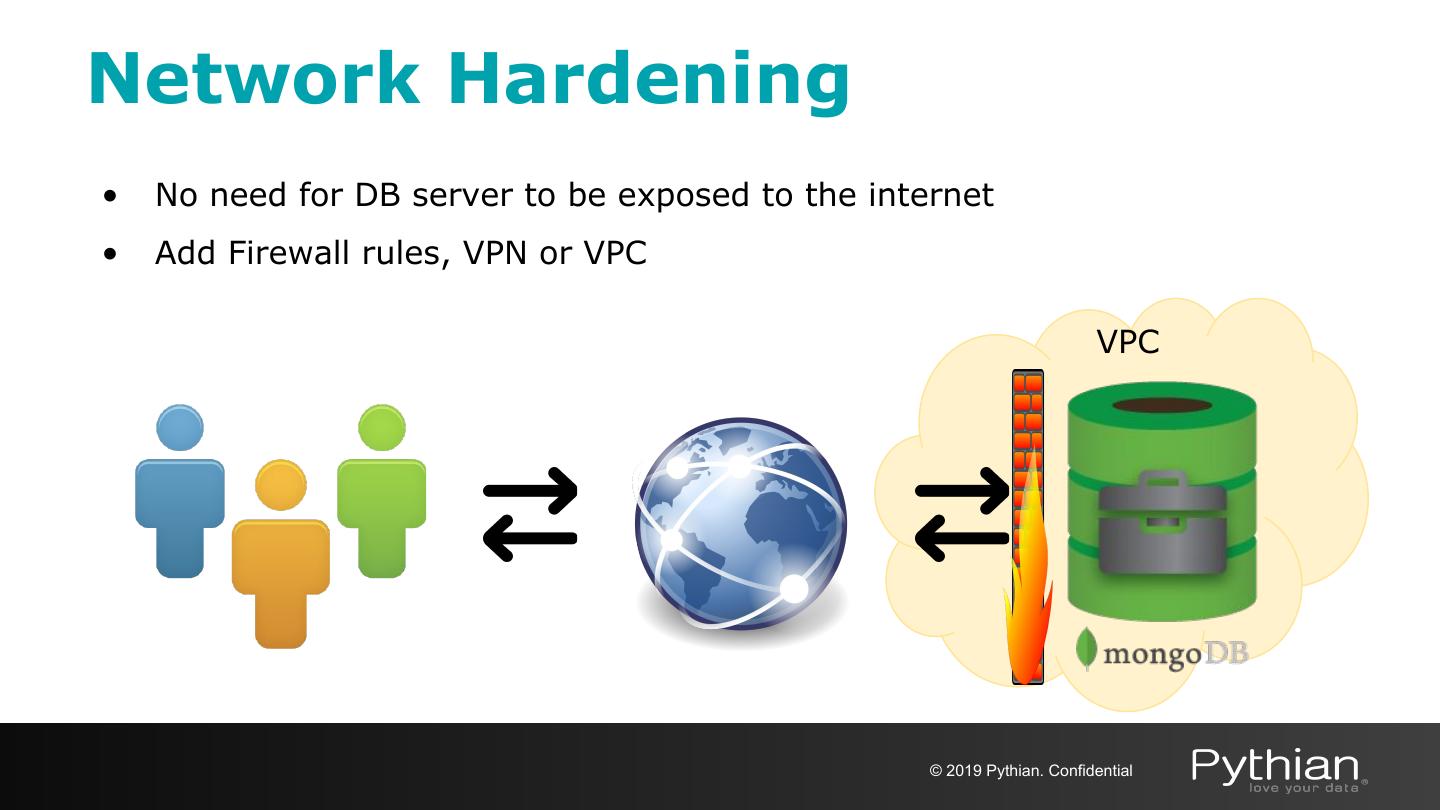
20 .Network Hardening • No need for DB server to be exposed to the internet • Add Firewall rules, VPN or VPC VPC © 2019 Pythian. Confidential
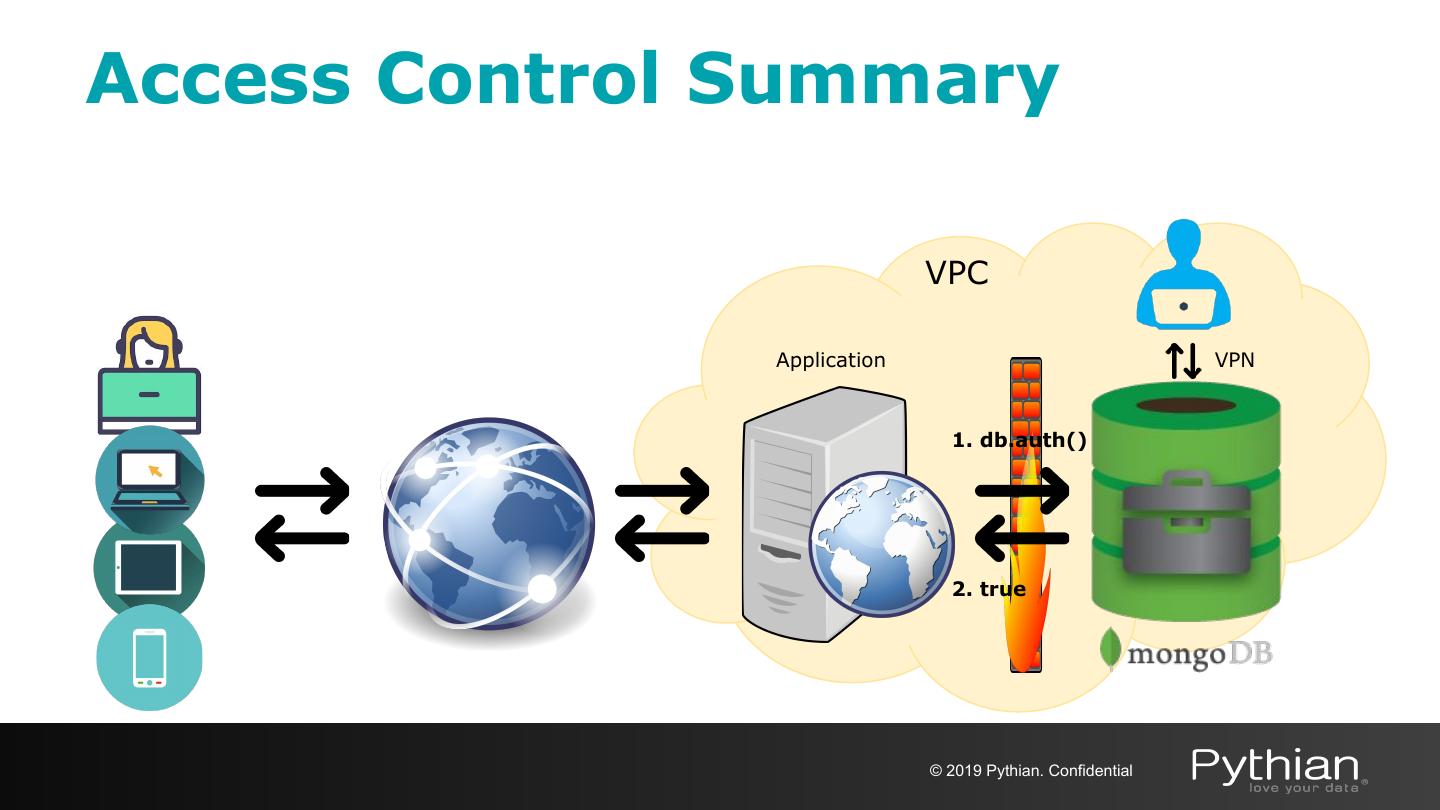
21 .Access Control Summary VPC Application VPN 1. db.auth() 2. true © 2019 Pythian. Confidential
22 .Encryption © 2019 Pythian. Confidential
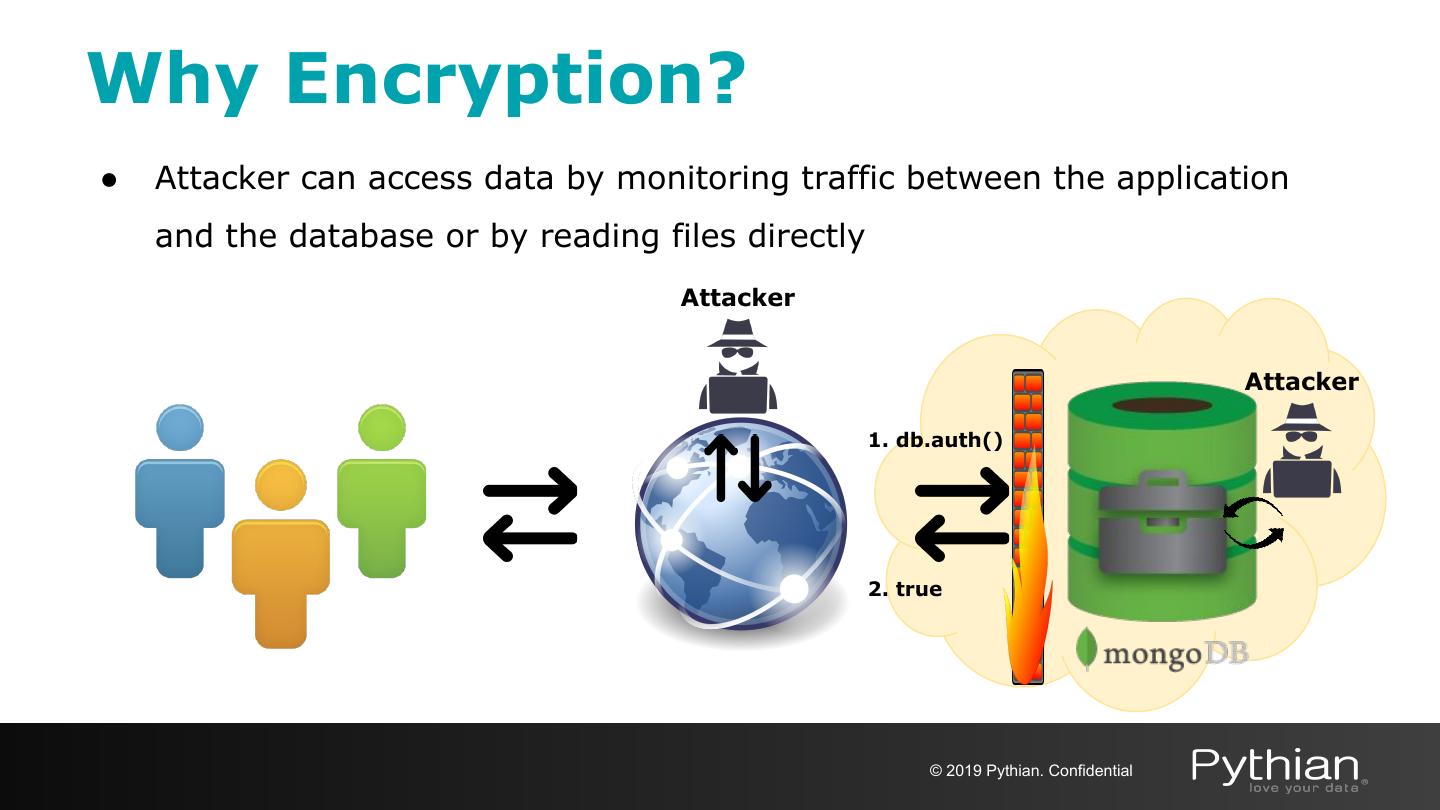
23 .Why Encryption? ● Attacker can access data by monitoring traffic between the application and the database or by reading files directly Attacker Attacker 1. db.auth() 2. true © 2019 Pythian. Confidential
24 .Why Encryption? ● Protect Personally Identifiable Information (PII) ○ PCI DSS for managing cardholder information ○ HIPAA standards for managing healthcare information ○ GDPR for the protection of EU citizen data privacy (May 2018) ○ FISMA to ensure the security of data in the federal government ○ FERPA to protect the privacy of student education records ○ The Asia Pacific Cross-border Privacy Enforcement Arrangement (CPEA) ○ Others © 2019 Pythian. Confidential
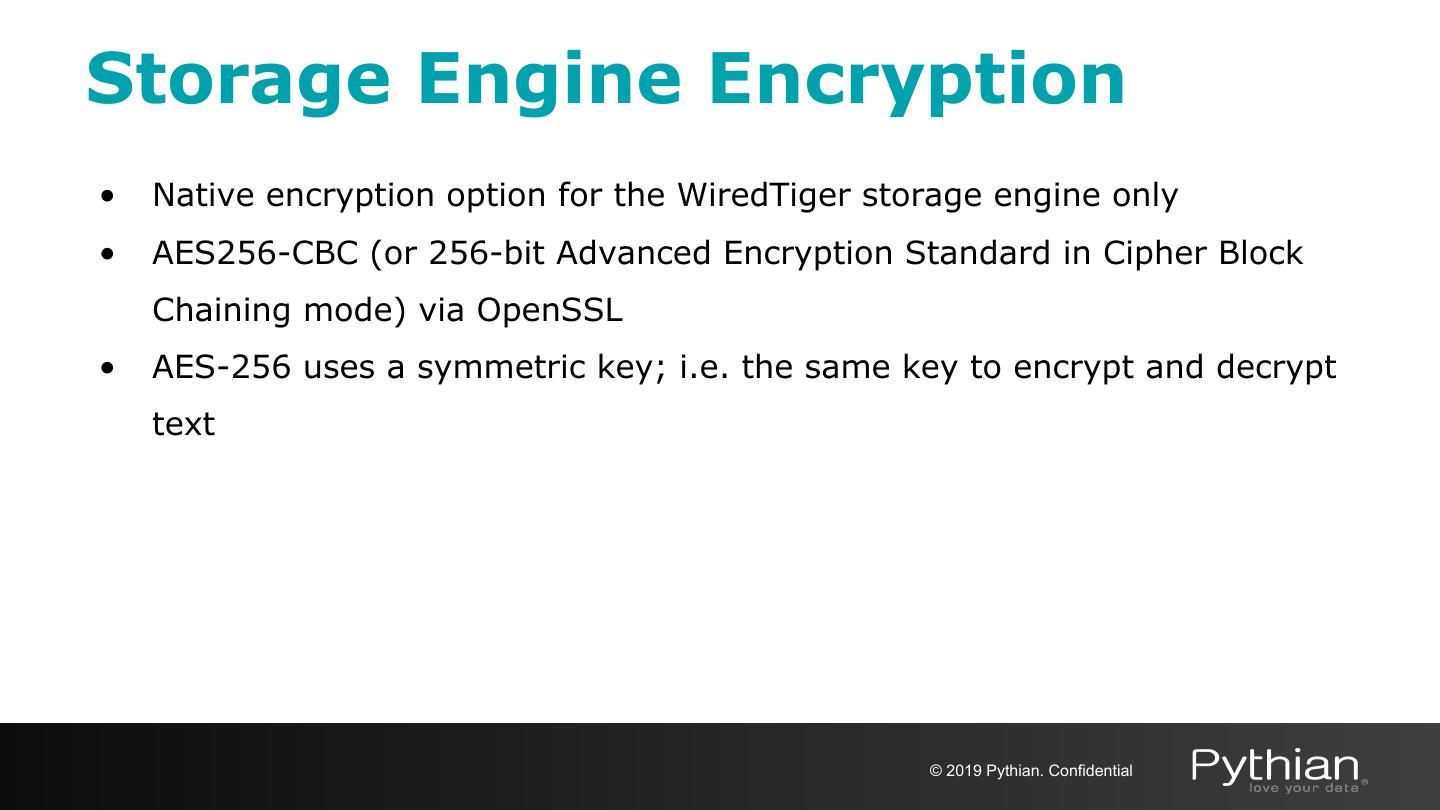
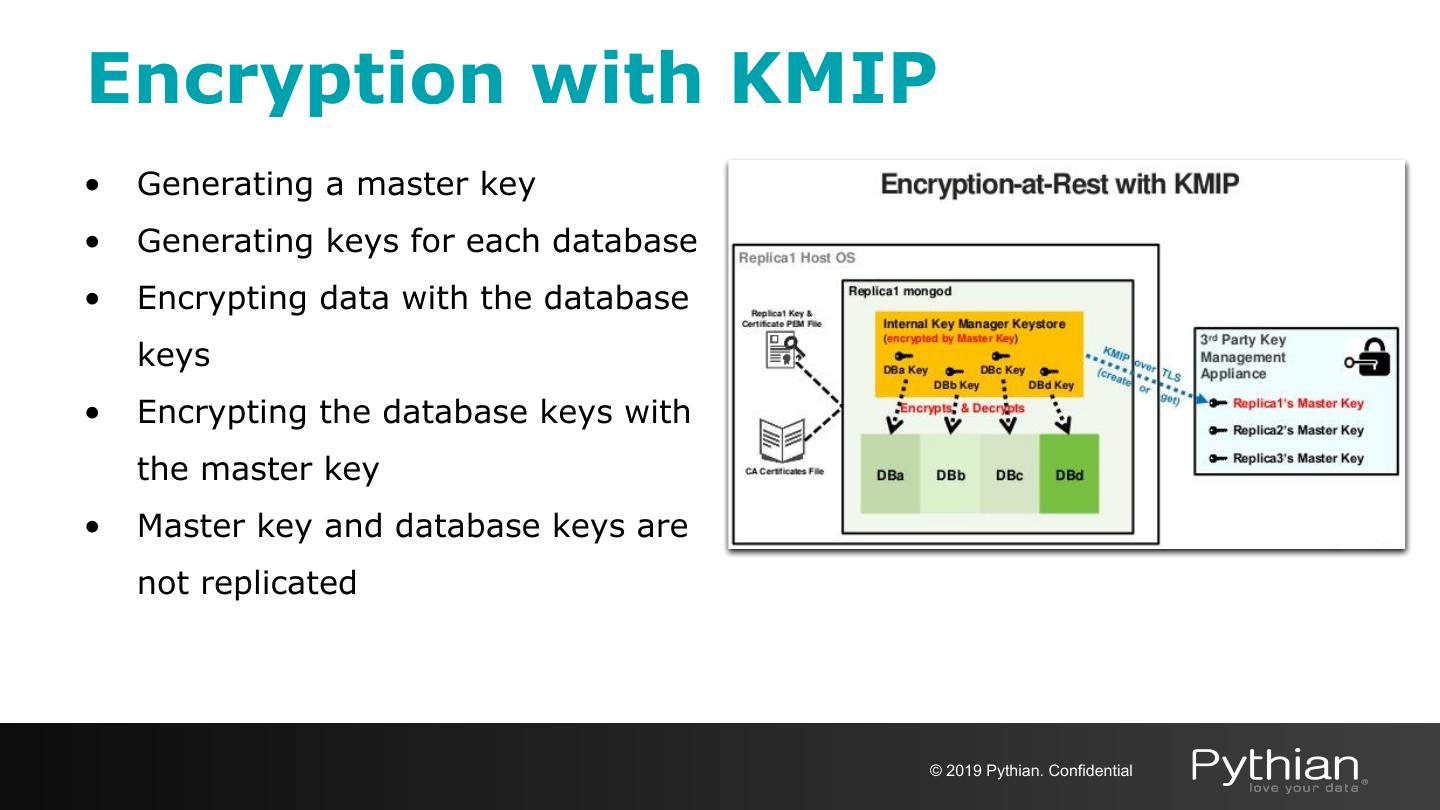
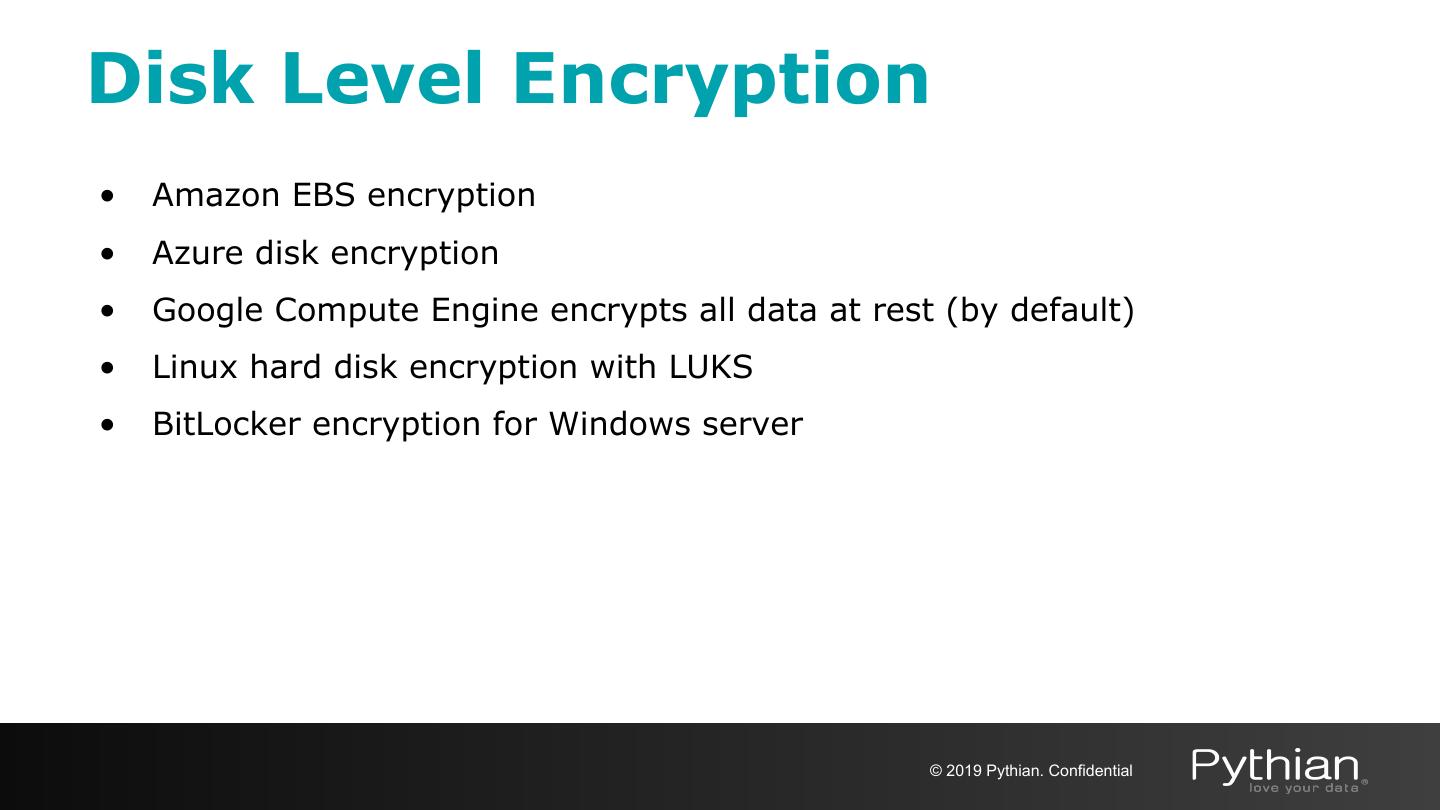
25 .Encryption with MongoDB ● Transport encryption ○ MongoDB network traffic is only readable by the intended client ● Encryption at REST ○ Application Level Encryption and Storage Encryption ○ Native encryption option for the WiredTiger storage engine* * Available in MongoDB Enterprise only © 2019 Pythian. Confidential
26 .Transport Encryption © 2019 Pythian. Confidential
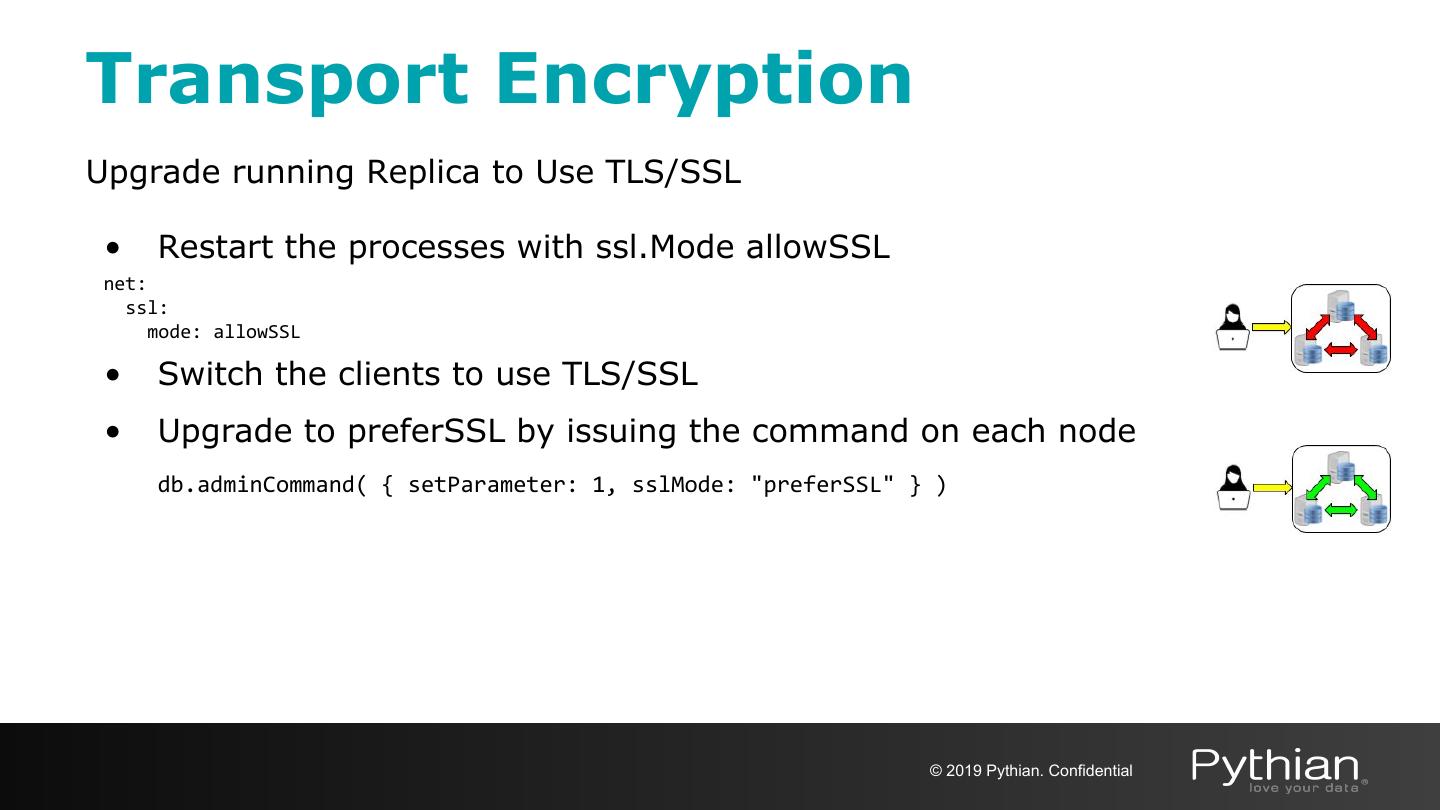
27 .Transport Encryption ● TLS/SSL (Transport Layer Security/Secure Sockets Layer) to encrypt all of MongoDB’s network traffic ● Certificate Authorities - valid certificates generated and signed by a single certificate authority ○ PEMKeyfile with the name of the .pem file that contains the signed TLS/SSL certificate and key ○ CAFile with the name of the .pem file that contains the root certificate chain from the Certificate Authority © 2019 Pythian. Confidential
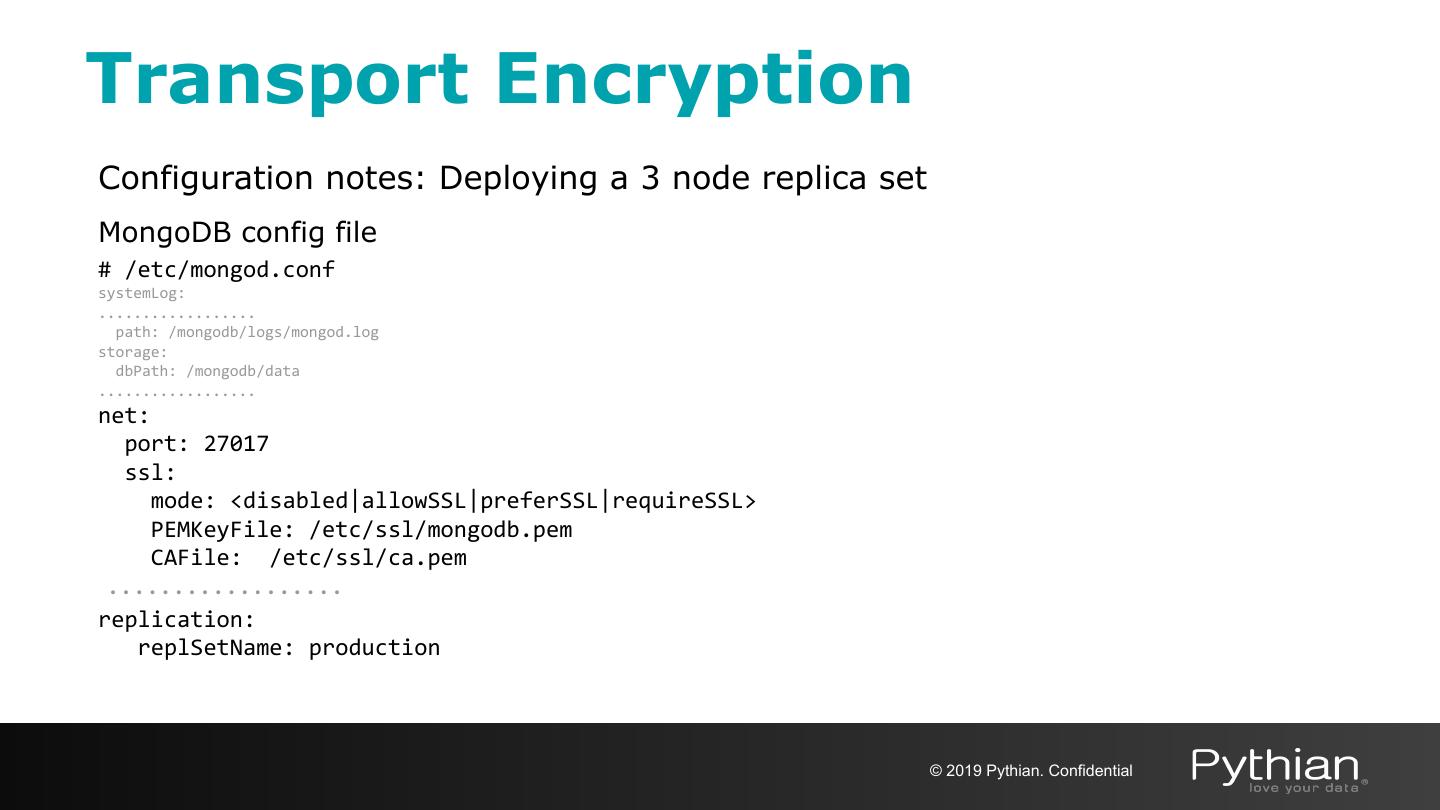
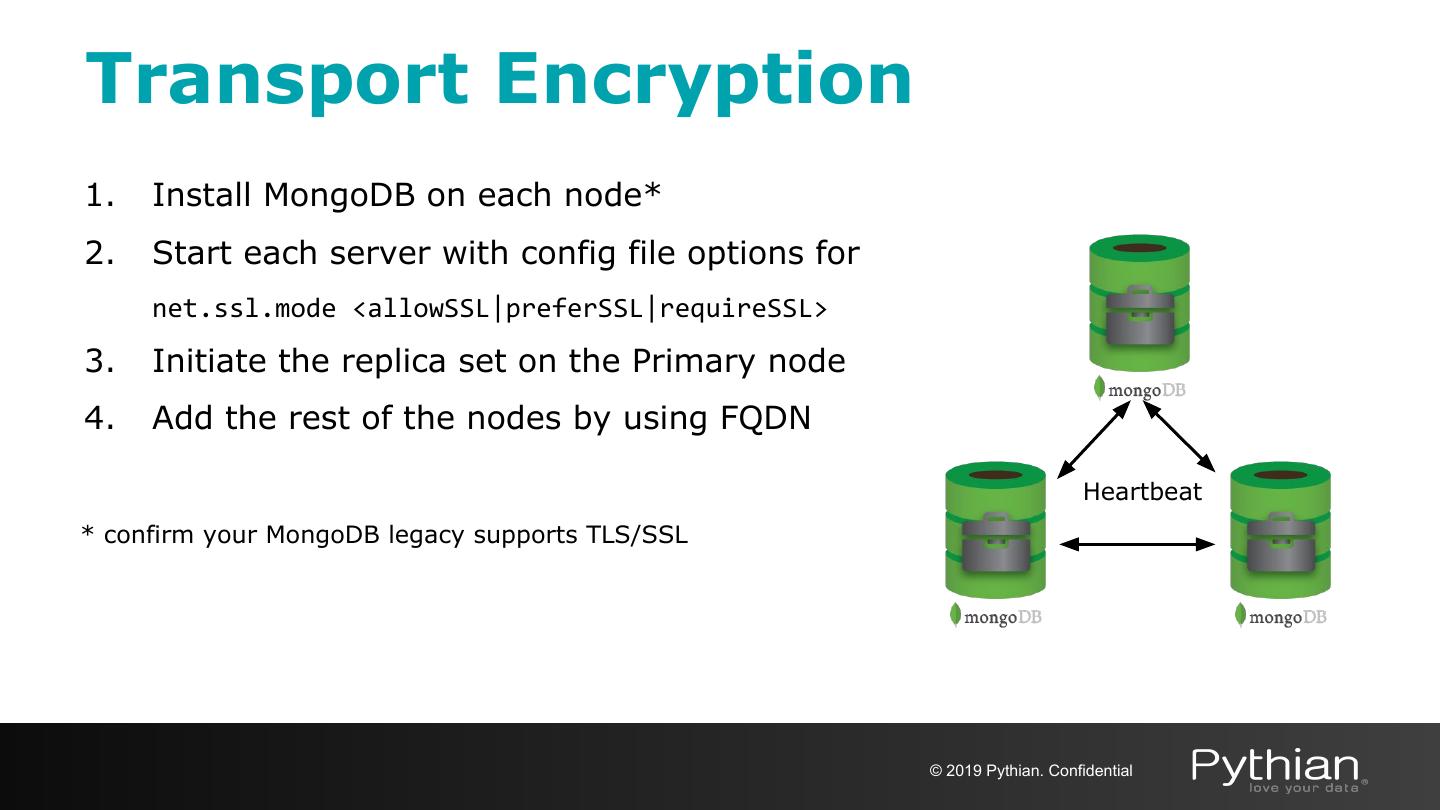
28 .Transport Encryption Configuration notes: Deploying a 3 node replica set MongoDB config file # /etc/mongod.conf systemLog: .................. path: /mongodb/logs/mongod.log storage: dbPath: /mongodb/data .................. net: port: 27017 ssl: mode: <disabled|allowSSL|preferSSL|requireSSL> PEMKeyFile: /etc/ssl/mongodb.pem CAFile: /etc/ssl/ca.pem .................. replication: replSetName: production © 2019 Pythian. Confidential
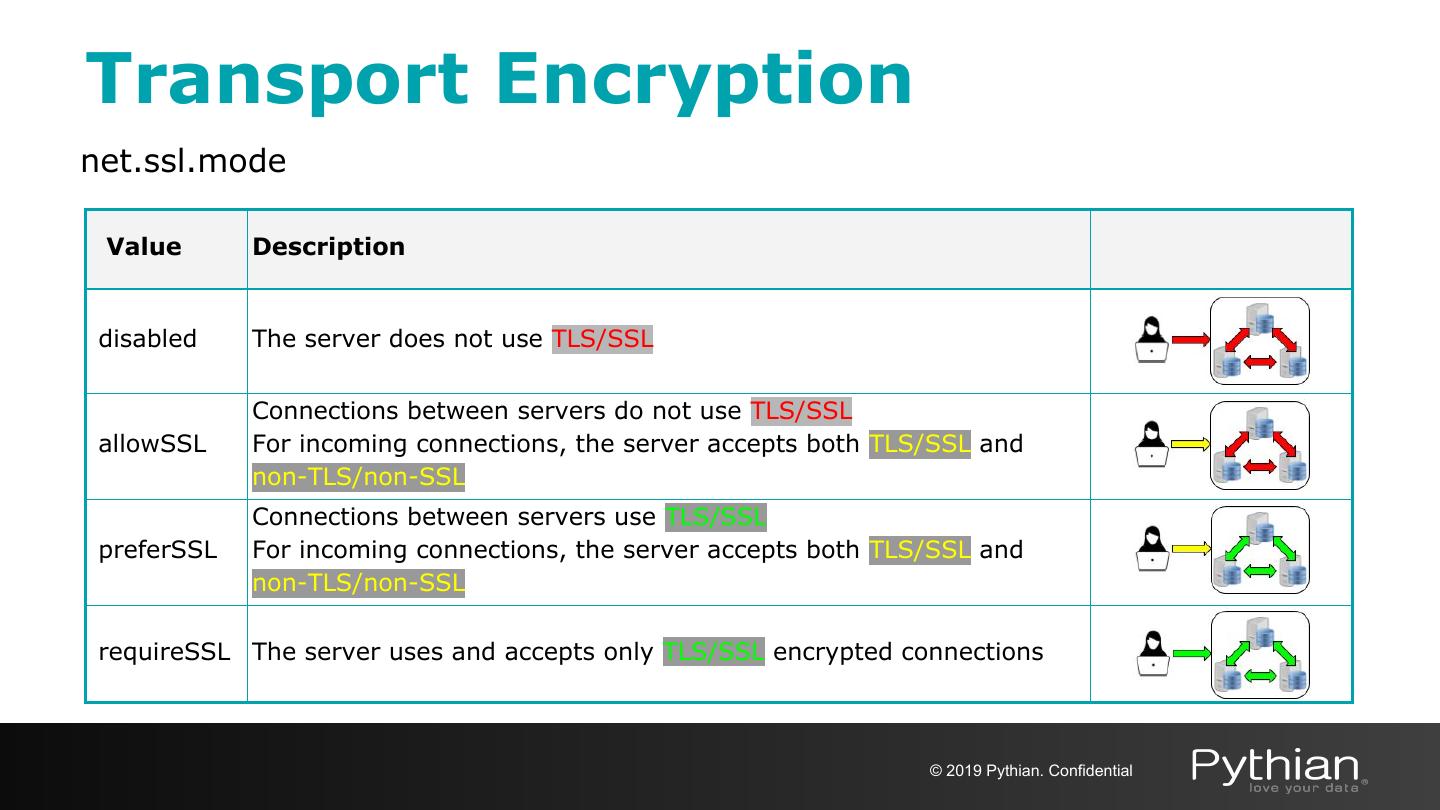
29 .Transport Encryption net.ssl.mode Value Description disabled The server does not use TLS/SSL Connections between servers do not use TLS/SSL allowSSL For incoming connections, the server accepts both TLS/SSL and non-TLS/non-SSL Connections between servers use TLS/SSL preferSSL For incoming connections, the server accepts both TLS/SSL and non-TLS/non-SSL requireSSL The server uses and accepts only TLS/SSL encrypted connections © 2019 Pythian. Confidential