- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
Securing Your Serverless Endpoint with Webtask
展开查看详情
1 .
2 .Who am I? Md Shahbaz Alam Auth0 Ambassador, Auth0 Inc Mozilla Representative @mdsbzalam
3 .Serverless
4 .Quick History
5 .A typical Client-Server
6 .Why still C-S Architecture? • Technology evolution has changed its application • Improved Hardware • Lack of Trust “ We still need a trust boundary between client and server to control access to shared data or functionality. “
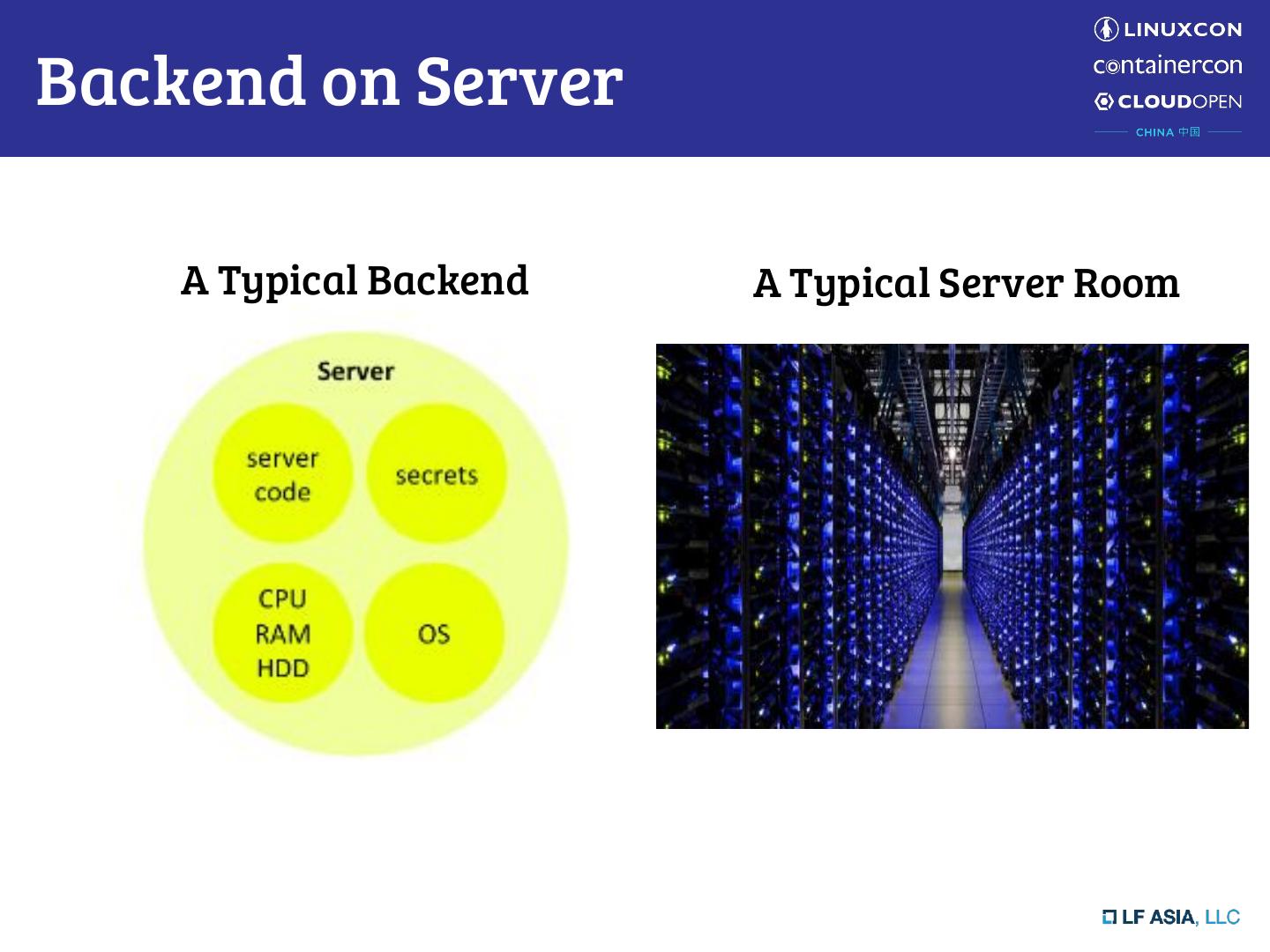
7 .Backend on Server A Typical Backend A Typical Server Room
8 .
9 .
10 .
11 .Serverless: someone else’s servers
12 . Examples ➔ WebTask ➔ AWS Lambda ➔ Azure Functions
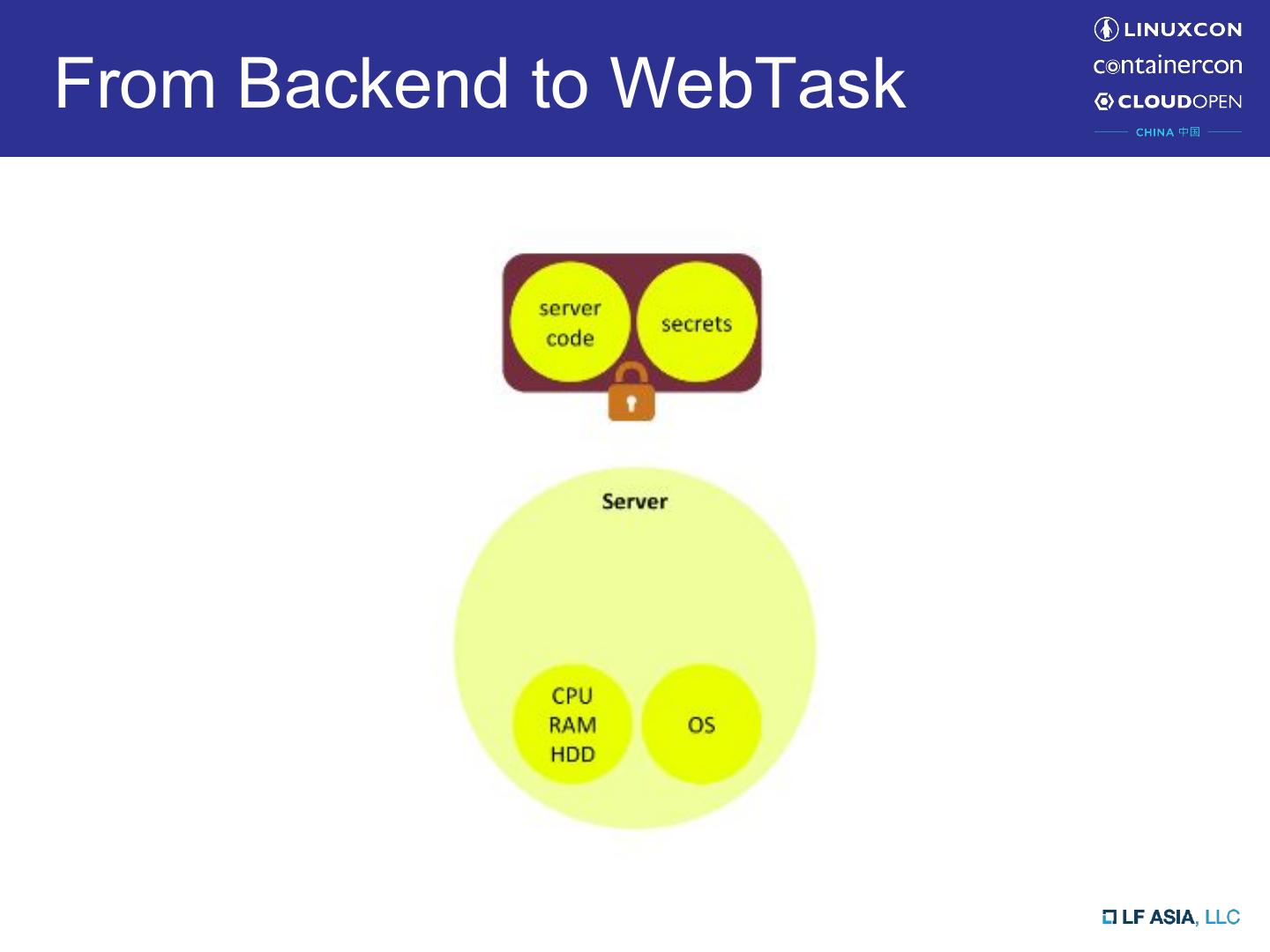
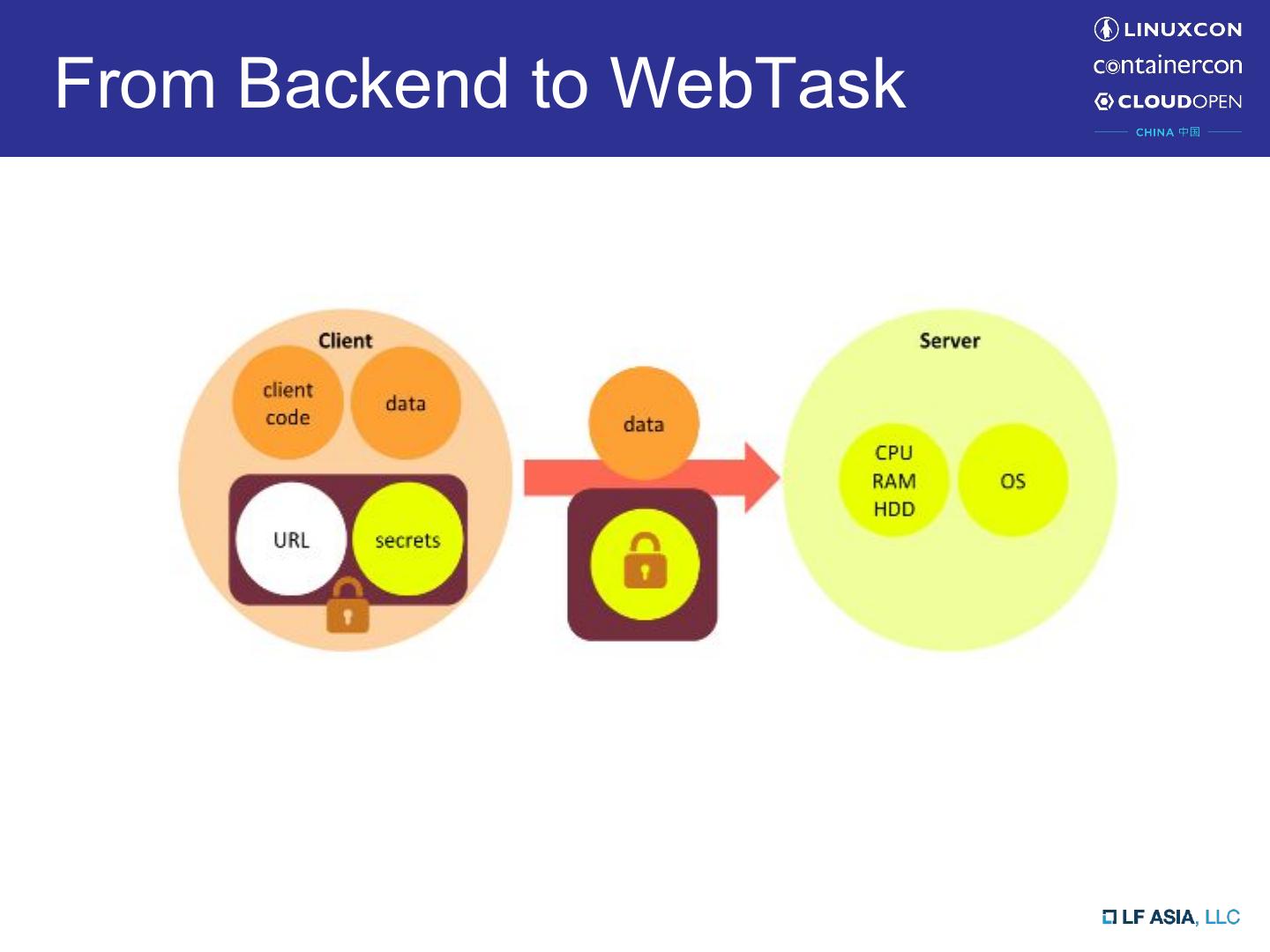
13 .From Backend to WebTask
14 .From Backend to WebTask
15 .From Backend to WebTask
16 .From Backend to WebTask
17 .WebTask
18 .WebTask: Scenario ● WebTask as a Code Sandbox ● WebTask as a Webhook
19 .How to start with WebTask?
20 .Getting Started 1. Install WebTask CLI 2. Init WebTask 3. Create hello.js and Deploy
21 .Success WebTask and WebTask Editor
22 .Thank you!