- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
How Virtual Reality & Machine Learning Are Powering
展开查看详情
1 .How Virtual Reality & Machine Learning Are Powering The New Age of Network Monitoring DataStax Data & Drinks Denver April 25, 2017
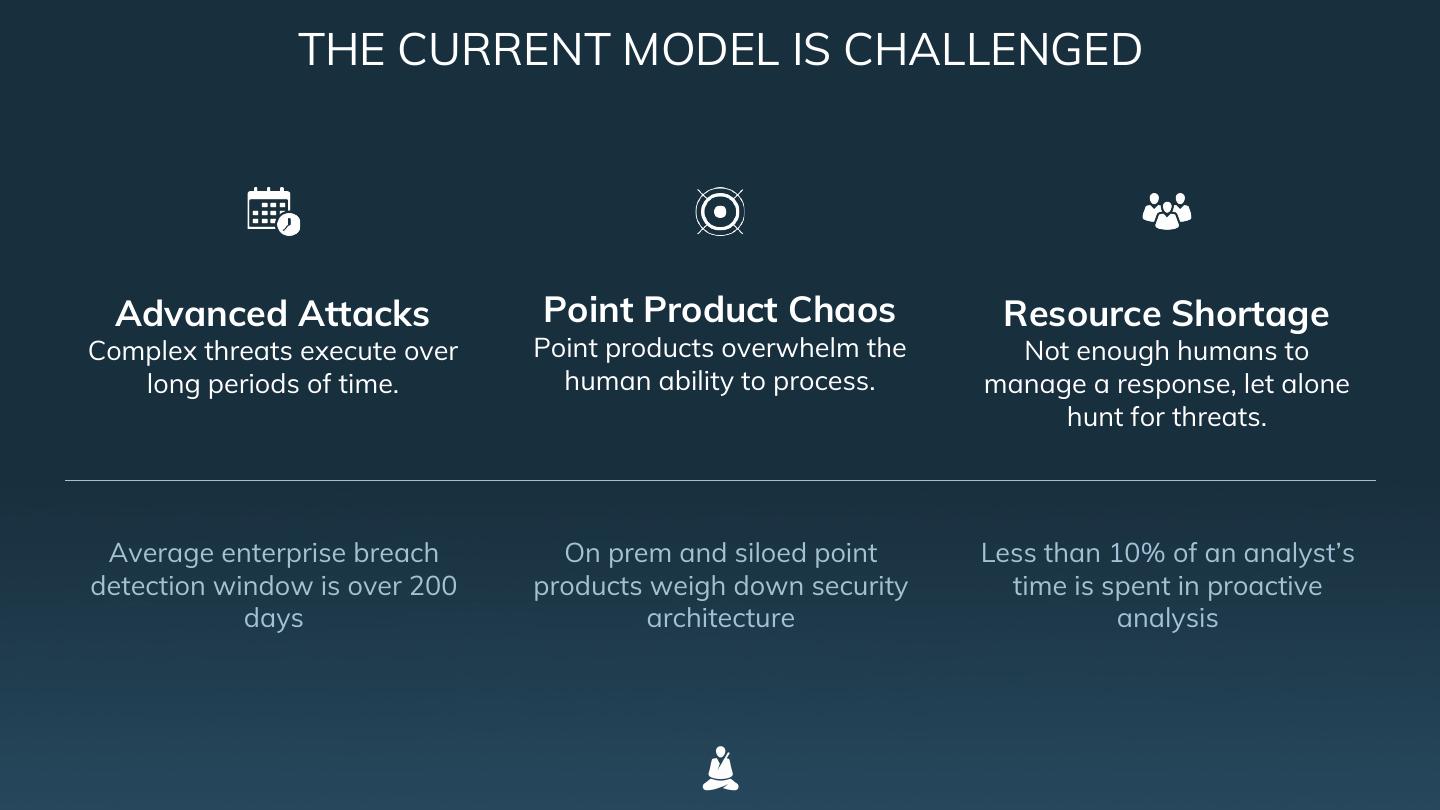
2 . THE CURRENT MODEL IS CHALLENGED Advanced Attacks Point Product Chaos Resource Shortage Complex threats execute over Point products overwhelm the Not enough humans to long periods of time. human ability to process. manage a response, let alone hunt for threats. Average enterprise breach On prem and siloed point Less than 10% of an analyst’s detection window is over 200 products weigh down security time is spent in proactive days architecture analysis
3 . THE PROTECTWISE GRID A new utility model for enterprise security, delivering pervasive visibility, automated threat detection and unlimited forensic exploration — on-demand and entirely from the cloud. “Never, in 52 years in this field, have I seen a collection of dashboards that even comes close to the collection you'll see in ProtectWise.” Peter Stephenson, Editor at Large SC Magazine 3
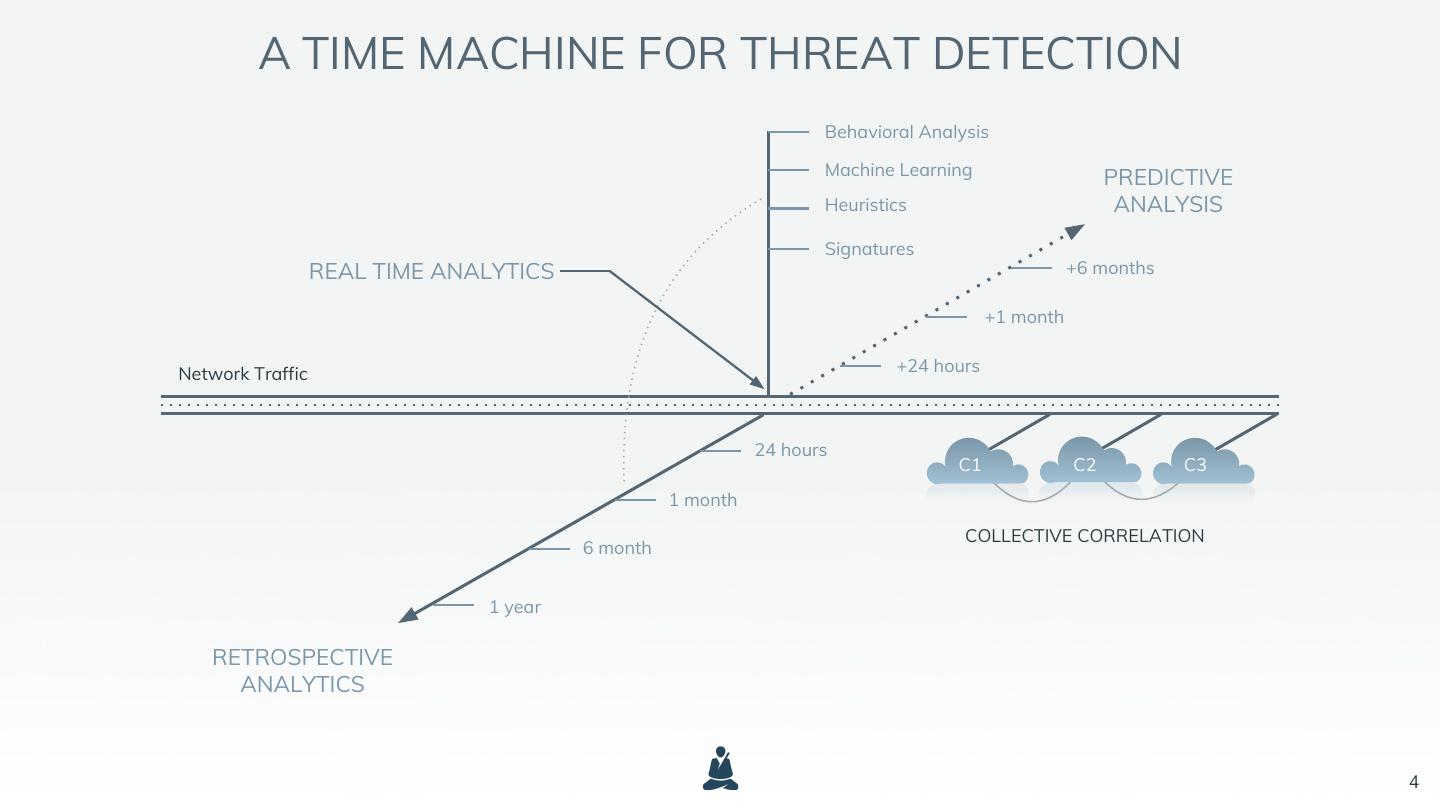
4 . A TIME MACHINE FOR THREAT DETECTION Behavioral Analysis Machine Learning PREDICTIVE Heuristics ANALYSIS Signatures REAL TIME ANALYTICS +6 months +1 month Network Traffic +24 hours 24 hours C1 C2 C3 1 month COLLECTIVE CORRELATION 6 month 1 year RETROSPECTIVE ANALYTICS 4
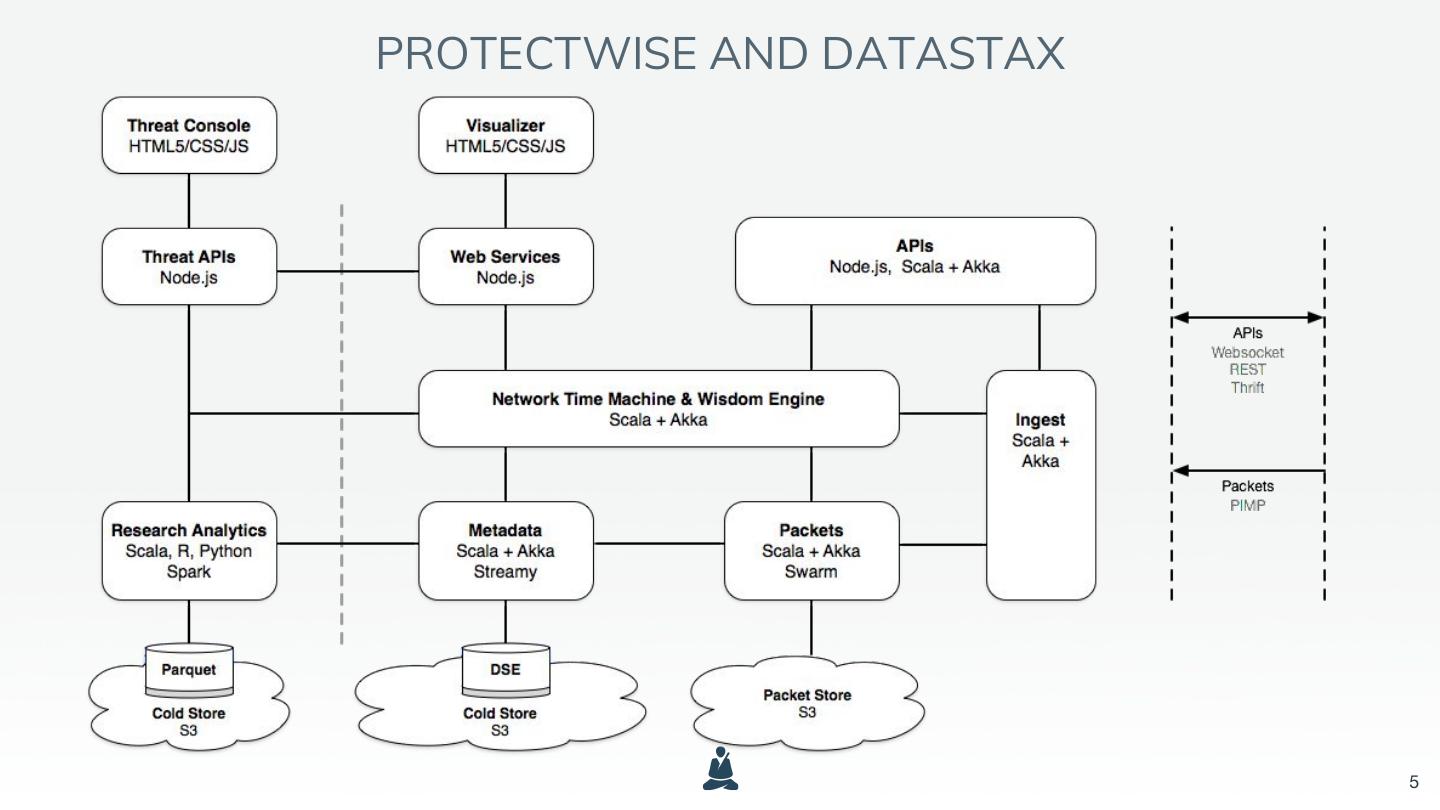
5 .PROTECTWISE AND DATASTAX 5
6 . WHY DATASTAX ● Needed Cassandra and Search combined ● Large distributed systems are hard ● Synchronizing them is crazy hard ● Access to support was crucial ● Time to market was imperative ● They are good people 6
7 . COVERAGE MODEL What’s missing from big data is data
8 .BIG DATA - Log Files - Metadata - Threat Intelligence - Context …all of these are not enough
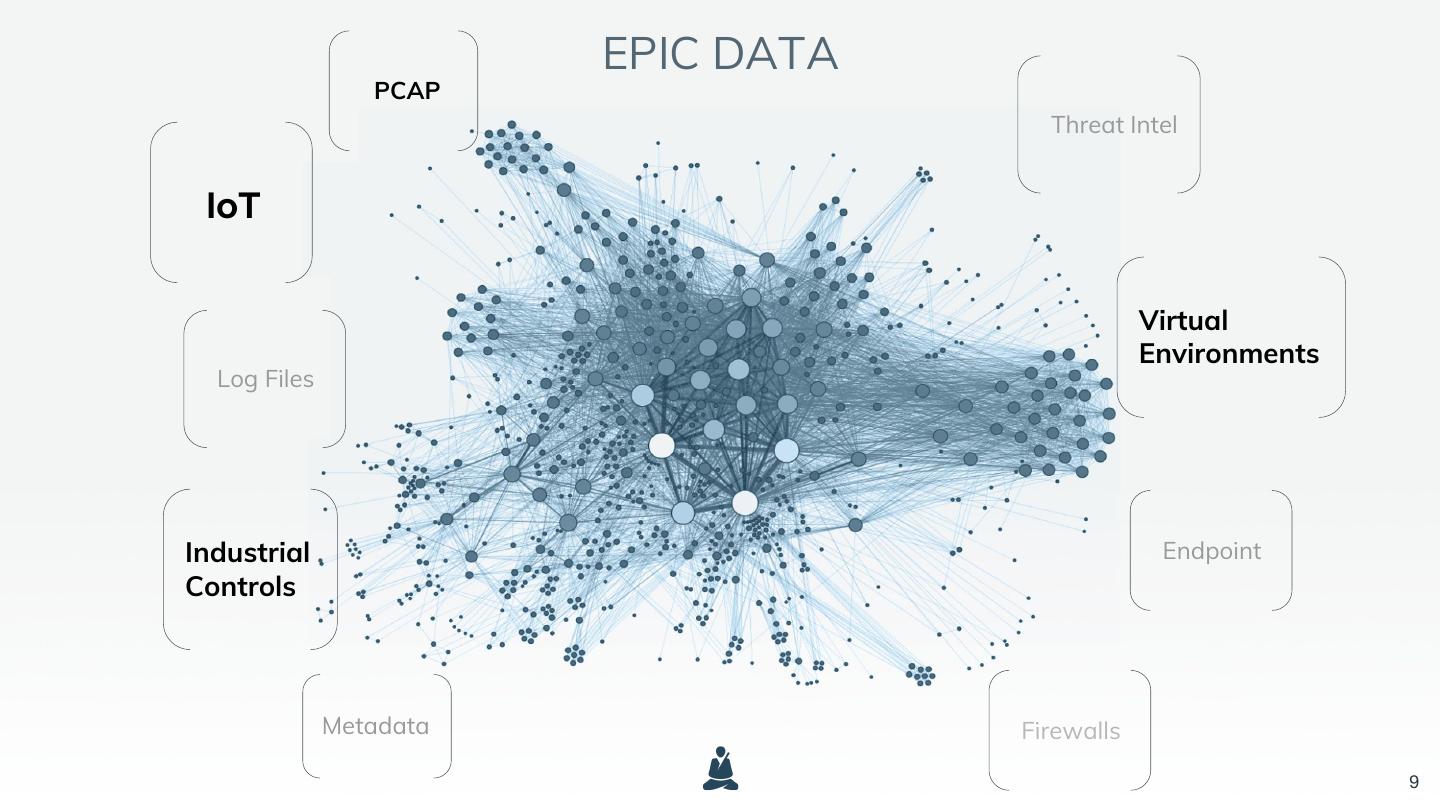
9 . EPIC DATA PCAP Threat Intel IoT Virtual Environments Log Files Industrial Endpoint Controls Metadata Firewalls 9
10 . DATA ANALYSIS Intelligent data reasoning based on first principles
11 . SECURITY FROM FIRST PRINCIPLES Comprehensive Contextual Correlated Consensus Full packet capture across Cross-reference of Pattern recognition to Numerous classifiers and traditional, virtual (cloud), multiple indicators detect security events statistical analysis industrial control, IoT included in analysis from a plethora of modeled to form a observations consensus of experts
12 .THE UTILITY OF THE CLOUD Security at scale
13 .Security should be … A Utility ● A fundamentally basic service ● Continuous and unbroken ● Provided like other basic utilities (e.g. electricity and water) ● An operations expense ● Deeply automated ● Accessed via a myriad of surfaces A technology truly matures when it disappears and becomes beautiful
14 .IMMERSIVE SECURITY
15 . 15 To fundamentally change human experience in security
16 .THANK YOU