- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
确保周边安全——使用 CI/CD 管道的 CFCR/CFAR 监管链
展开查看详情
1 .Securing the Perimeter CFCR/CFAR Chain Of Custody With CI/CD Pipelines
2 . Who We Are... Keith Strini ... …. Shaozhen Ding ■ Provide operational assistance and guidance ■ Build balanced customer product teams delivering “Platform” as a capability within their organization ■ Establish and maintain continuous delivery pipelines for deployme nt of Pivotal Cloud Foundry and related products in a customer’s infrastructure ■ Design and implement continuous integration and continuous deli very processes to deliver customer applications to production, fostering a culture of continu ous process improvement
3 . Shift the Mindset ”Assume The Continuous Threat of Compromise and Then Continuously Move The Target ” From Reactive Courses of Action into Proactive Security Policy ◆ Recovery Point Objective • The recovery point objective (RPO) is the point in time that you wish to recover to. ◆ Recovery Time Objective • The recovery time objective (RTO) is how long it takes to recover, taken irrespective of the RPO. That is, after the disaster, how long until you have recovered to the point determined by the RPO.
4 . A Standard Delivery Pipeline Artifactory binary/containers DVCS Build Deploy To Test Deploy To QA Deploy To Prod Platform As A service
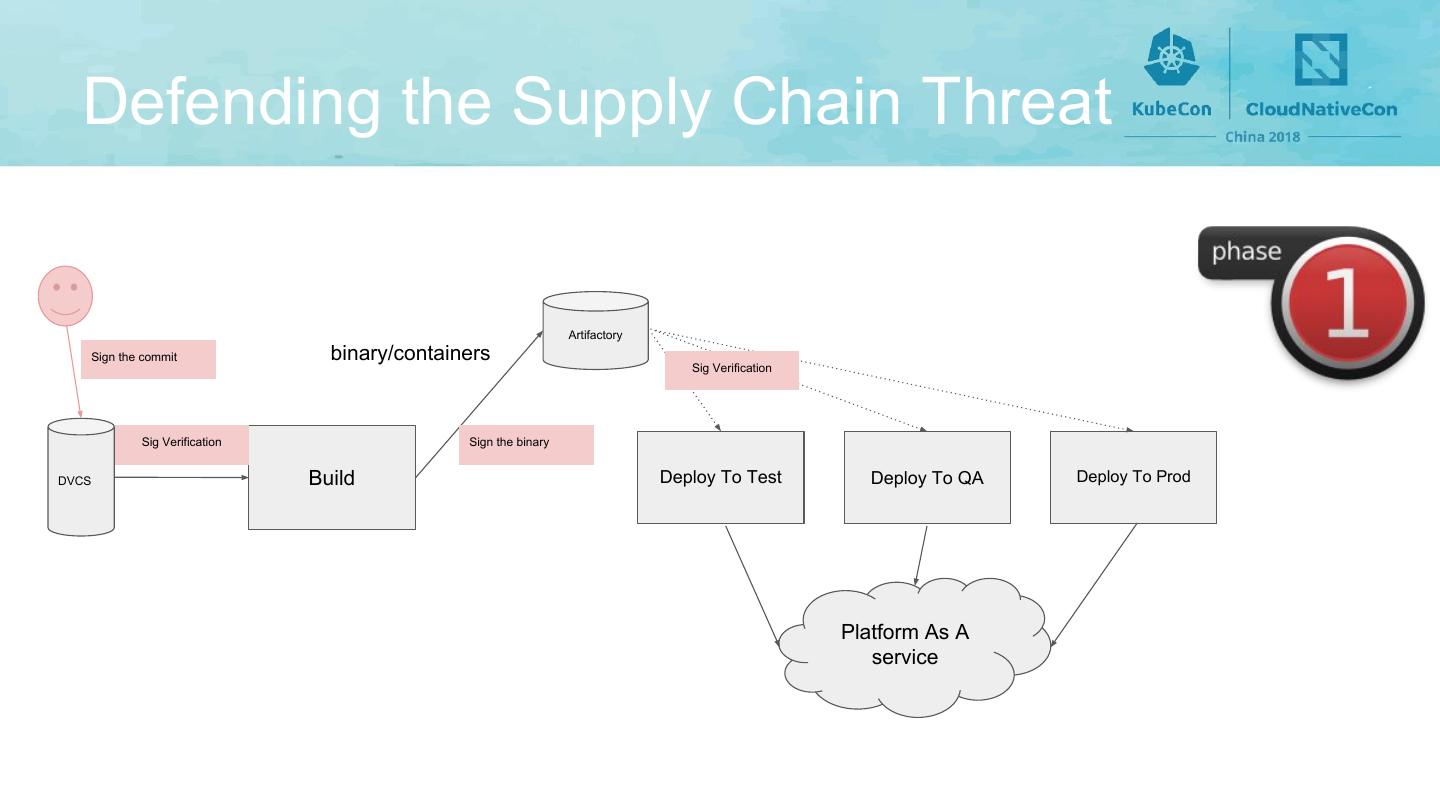
5 . Defending the Supply Chain Threat Artifactory Sign the commit binary/containers Sig Verification Sig Verification Sign the binary DVCS Build Deploy To Test Deploy To QA Deploy To Prod Platform As A service
6 .Limiting CI/CD Breakout Exposure Artifactory binary/containers DVCS Build Deploy To Test Deploy To QA Deploy To Prod Platform As A service
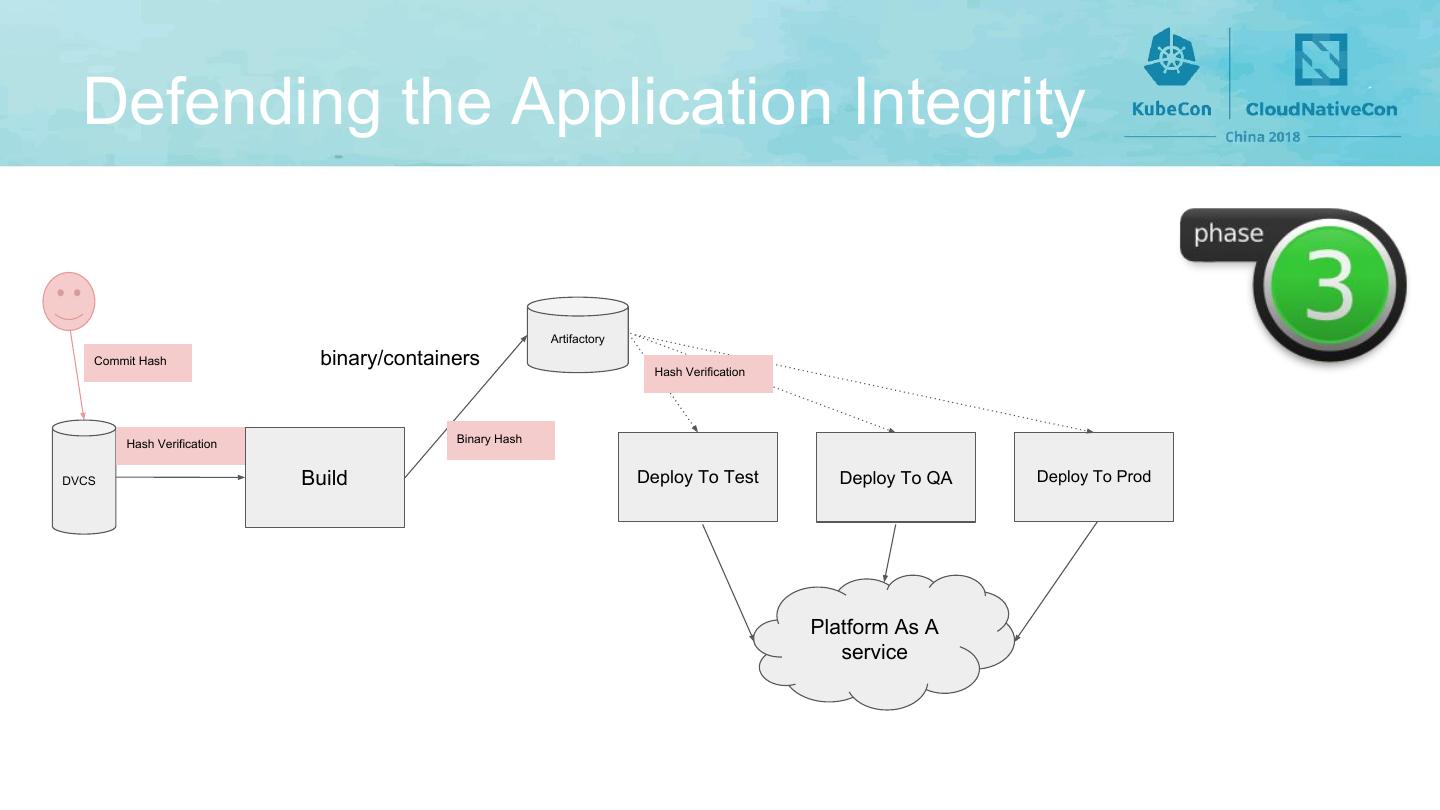
7 . Defending the Application Integrity Artifactory Commit Hash binary/containers Hash Verification Hash Verification Binary Hash DVCS Build Deploy To Test Deploy To QA Deploy To Prod Platform As A service
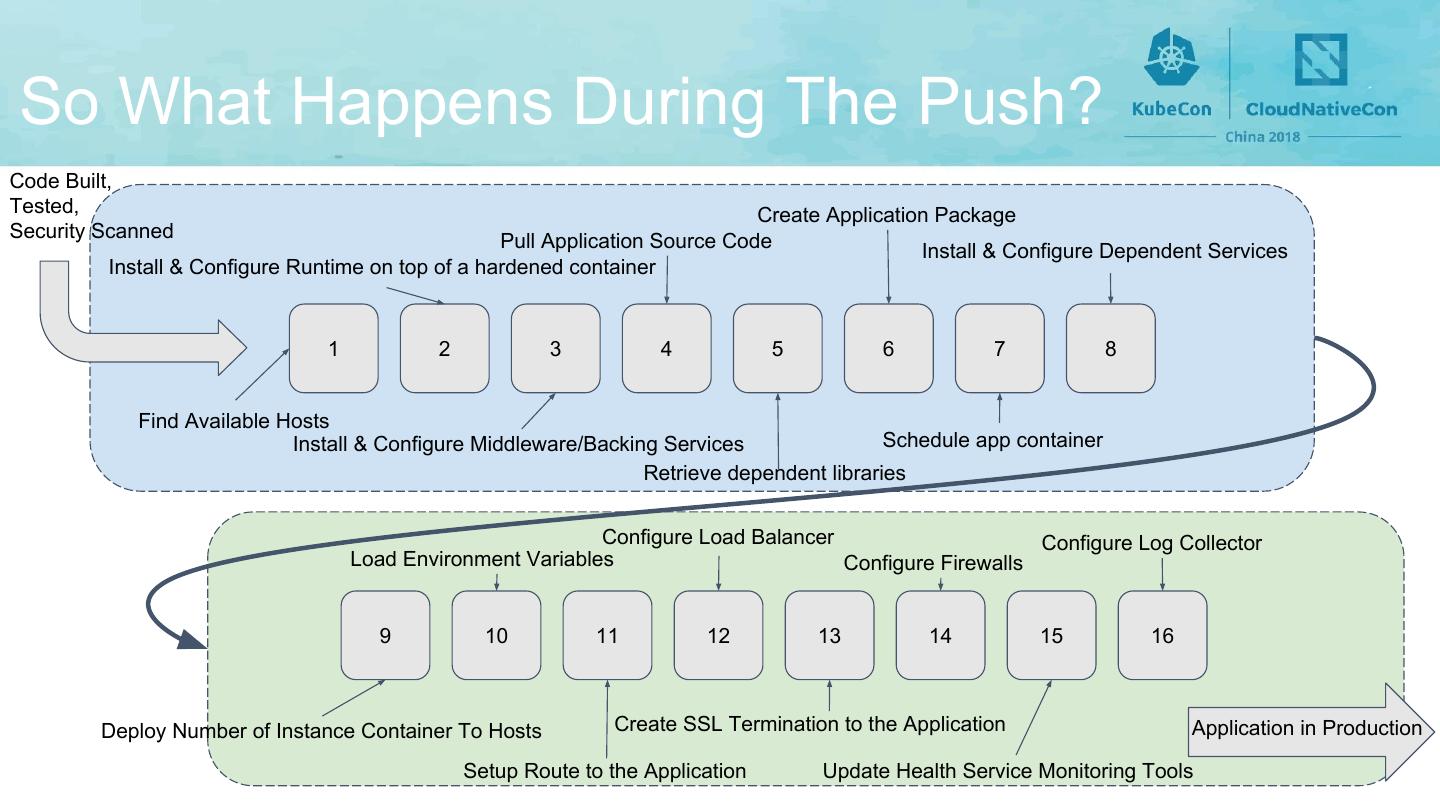
8 .So What Happens During The Push? Code Built, Tested, Create Application Package Security Scanned Pull Application Source Code Install & Configure Dependent Services Install & Configure Runtime on top of a hardened container 1 2 3 4 5 6 7 8 Find Available Hosts Install & Configure Middleware/Backing Services Schedule app container Retrieve dependent libraries Configure Load Balancer Configure Log Collector Load Environment Variables Configure Firewalls 9 10 11 12 13 14 15 16 Deploy Number of Instance Container To Hosts Create SSL Termination to the Application Application in Production Setup Route to the Application Update Health Service Monitoring Tools
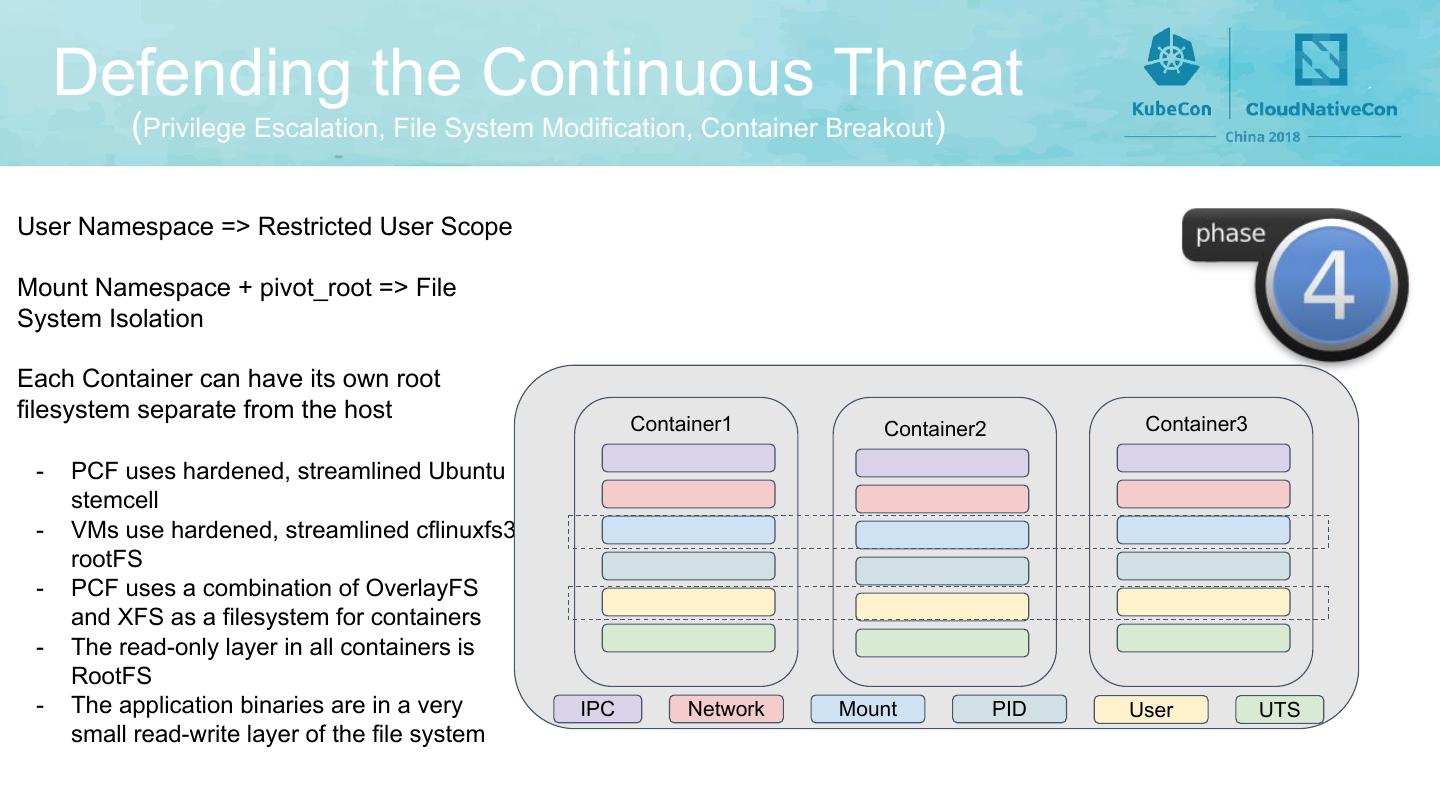
9 . Defending the Continuous Threat (Privilege Escalation, File System Modification, Container Breakout) User Namespace => Restricted User Scope Mount Namespace + pivot_root => File System Isolation Each Container can have its own root filesystem separate from the host Container1 Container2 Container3 - PCF uses hardened, streamlined Ubuntu stemcell - VMs use hardened, streamlined cflinuxfs3 rootFS - PCF uses a combination of OverlayFS and XFS as a filesystem for containers - The read-only layer in all containers is RootFS - The application binaries are in a very IPC Network Mount PID User UTS small read-write layer of the file system
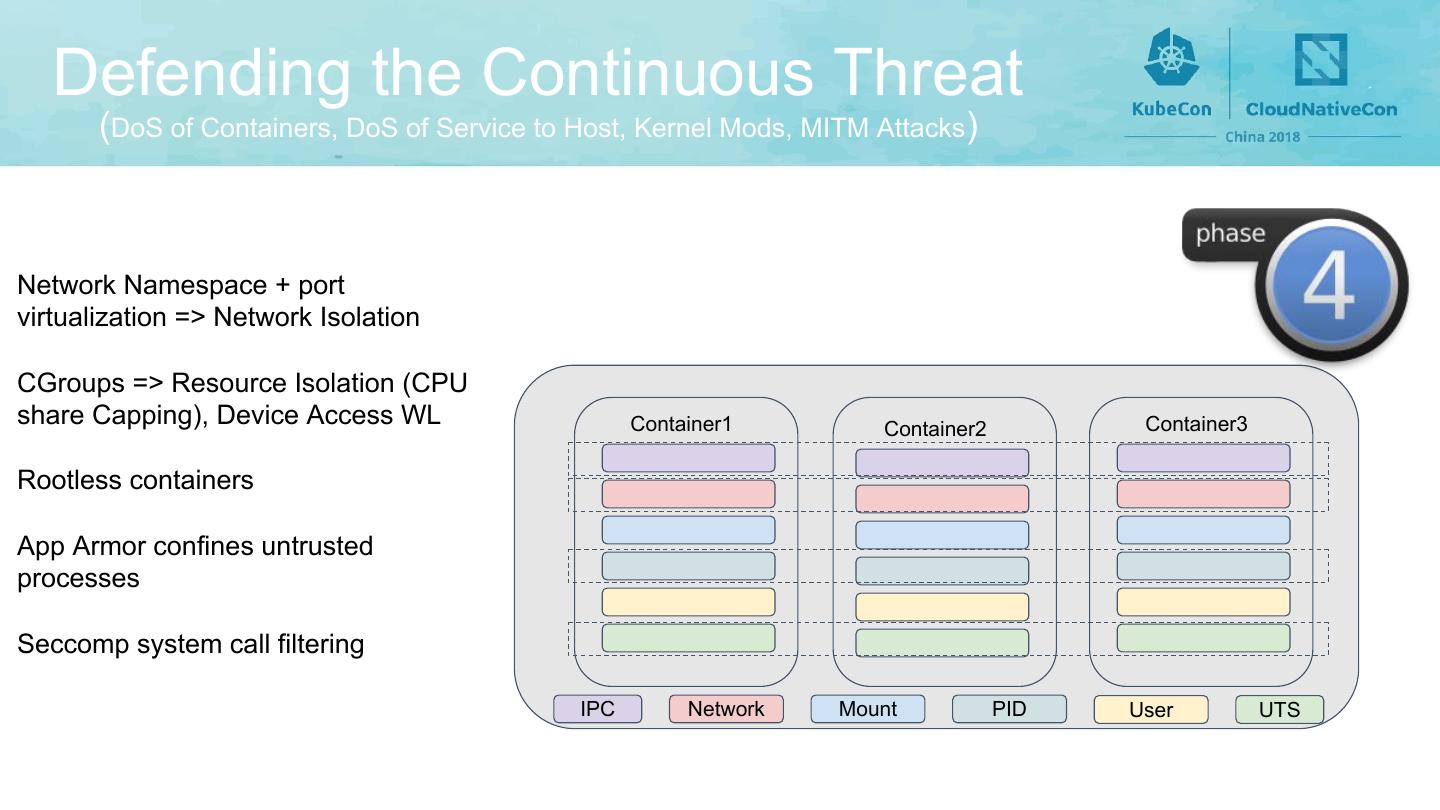
10 . Defending the Continuous Threat (DoS of Containers, DoS of Service to Host, Kernel Mods, MITM Attacks) Network Namespace + port virtualization => Network Isolation CGroups => Resource Isolation (CPU share Capping), Device Access WL Container1 Container2 Container3 Rootless containers App Armor confines untrusted processes Seccomp system call filtering IPC Network Mount PID User UTS
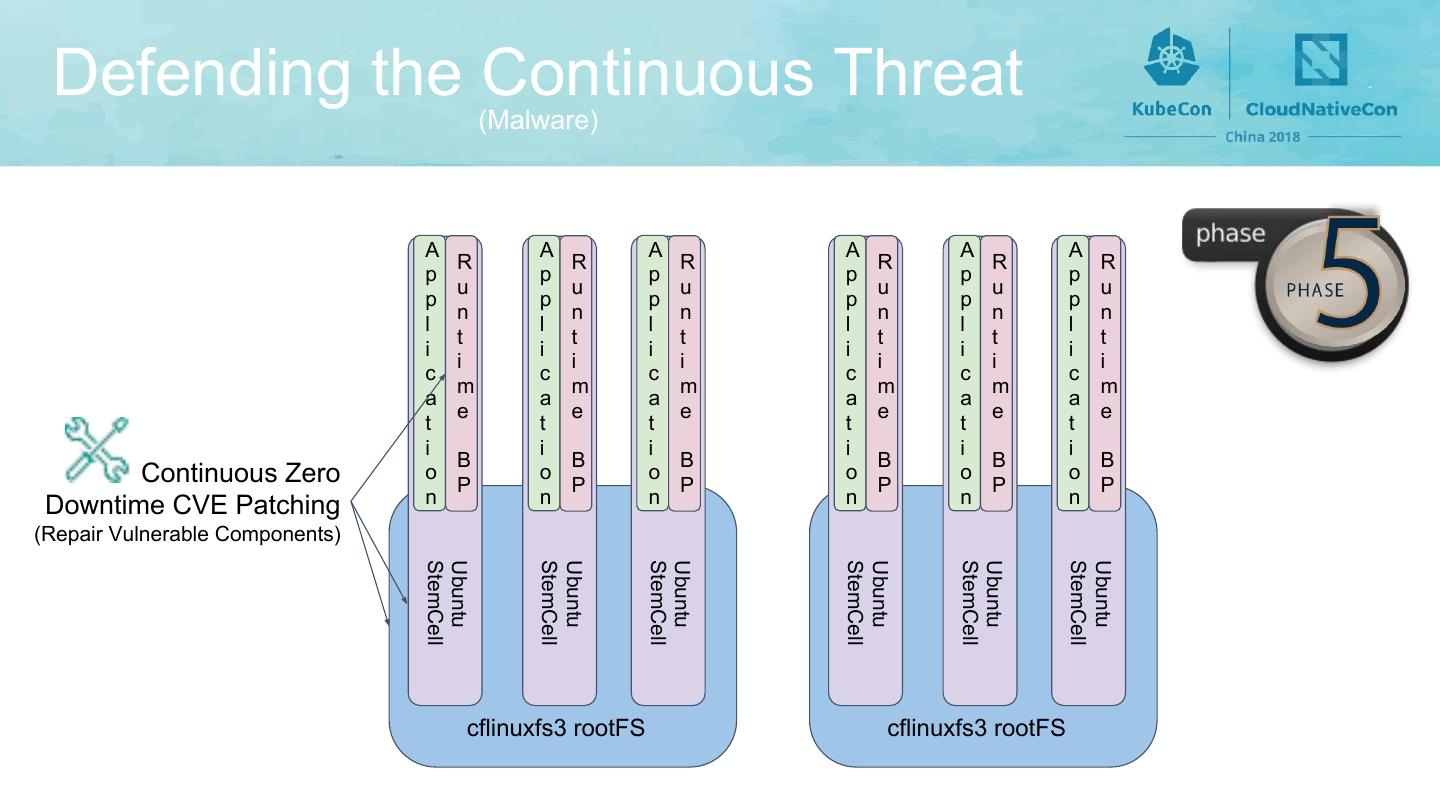
11 . Defending the Continuous Threat (Malware) A A A A A A R R R R R R p p p p p p u u u u u u p p p p p p n n n n n n l l l l l l t t t t t t i i i i i i i i i i i i c c c c c c m m m m m m a a a a a a e e e e e e t t t t t t i i i i i i B B B B B B Continuous Zero o P o P o P o P o P o P Downtime CVE Patching n n n n n n (Repair Vulnerable Components) StemCell Ubuntu StemCell Ubuntu StemCell Ubuntu StemCell Ubuntu StemCell Ubuntu StemCell Ubuntu cflinuxfs3 rootFS cflinuxfs3 rootFS
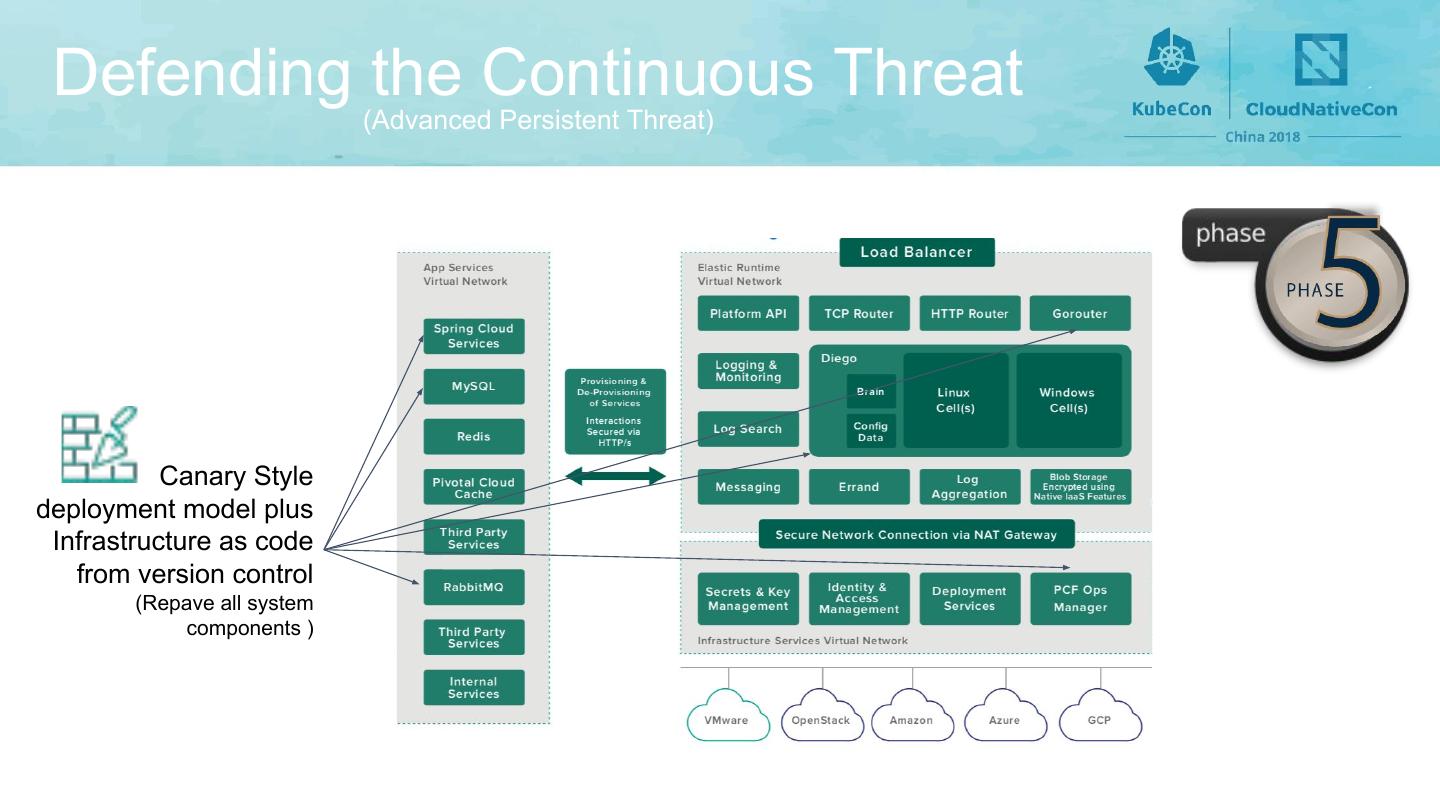
12 . Defending the Continuous Threat (Advanced Persistent Threat) Canary Style deployment model plus Infrastructure as code from version control (Repave all system components )
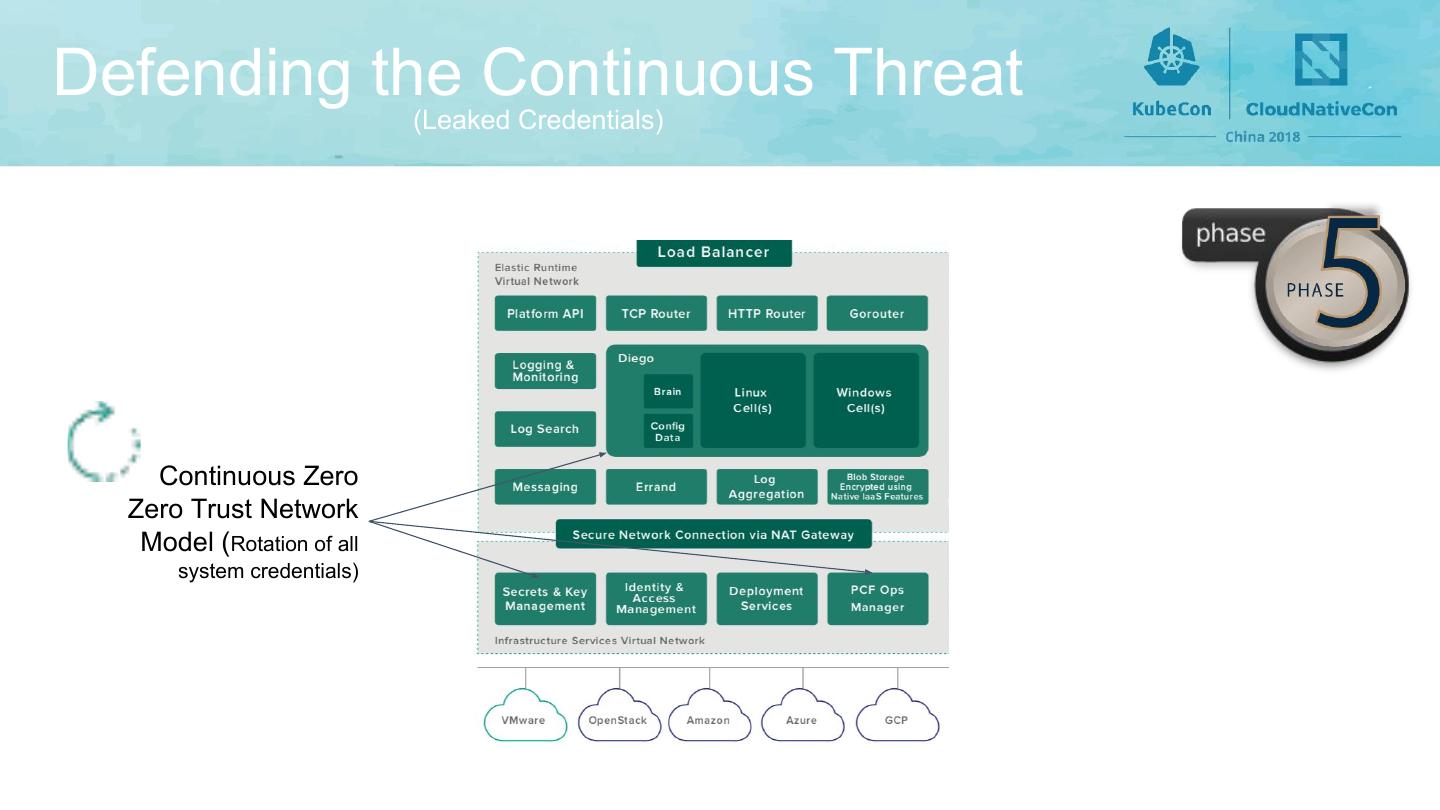
13 .Defending the Continuous Threat (Leaked Credentials) Continuous Zero Zero Trust Network Model (Rotation of all system credentials)
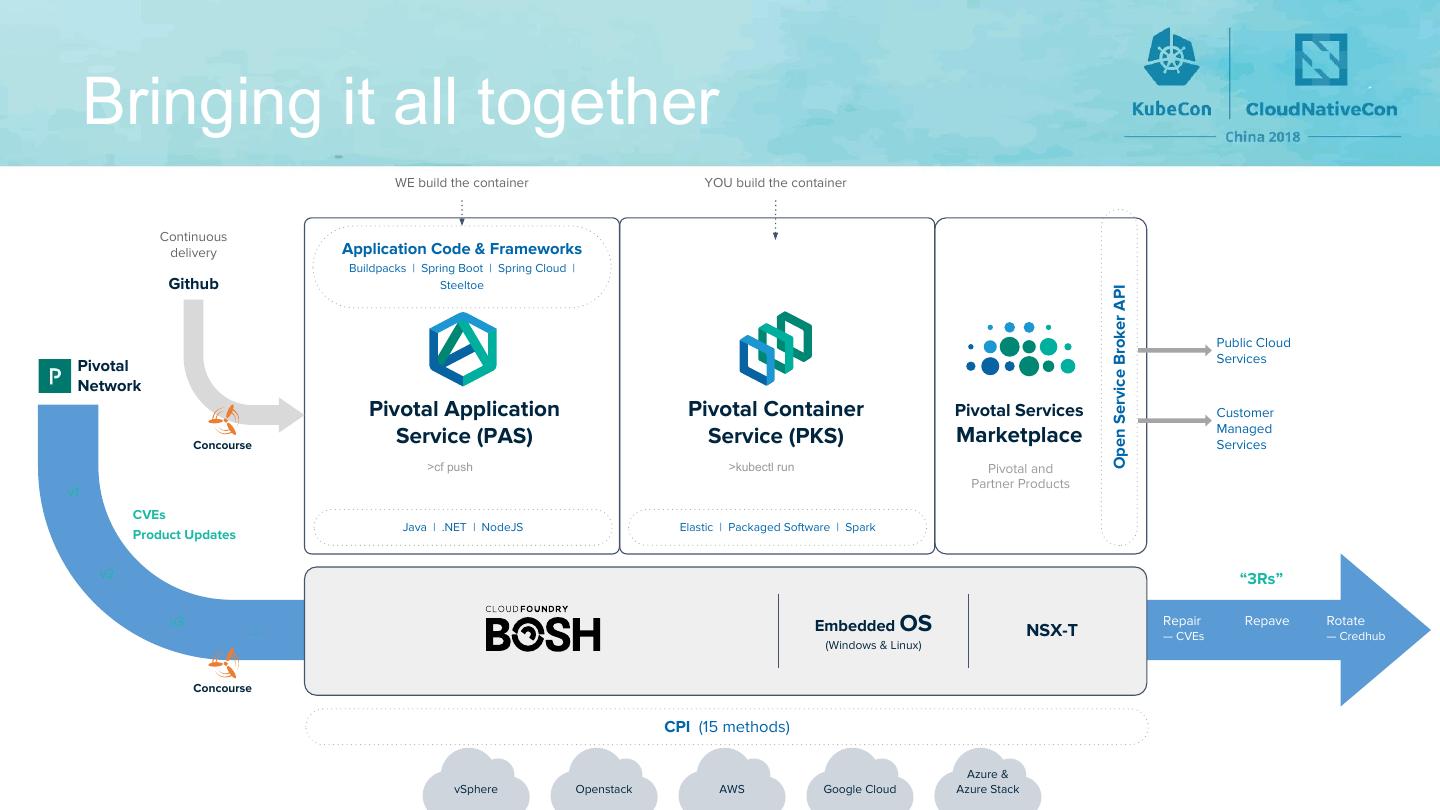
14 . Bringing it all together WE build the container YOU build the container Continuous delivery Application Code & Frameworks Buildpacks | Spring Boot | Spring Cloud | Github Steeltoe Open Service Broker API Public Cloud Services Pivotal Network Pivotal Application Pivotal Container Pivotal Services Customer Managed Concourse Service (PAS) Service (PKS) Marketplace Services >cf push >kubectl run Pivotal and Partner Products v1 CVEs Java | .NET | NodeJS Elastic | Packaged Software | Spark Product Updates v2 “3Rs” v3 ... Embedded OS NSX-T Repair Repave Rotate — CVEs — Credhub (Windows & Linux) Concourse CPI (15 methods) Azure & vSphere Openstack AWS Google Cloud Azure Stack
15 . Conclusion - Move The Target Proactive Security Policy Phase I - Aggressive Rotation of the issued Developer Keys Phase II – Rotation of Environment Credentials, End Point IPs, and Dynamic Management of IP WL/ACLs Phase III - Continuous Verification of the Application Integrity Phase IV – Continuous Authorization for Runtime Validation Phase V – Continuous Paving of the Environment, Rotation of the Keys, Renewal of Authorizing Credentials plus Least Privilege Container Authority
16 .
17 . What Does Bosh Do Packaging w/ embedded OS Server provisioning on any IaaS ● Cloud Native Security Software deployment across availability zones ○ Repair BOSH is an open source tool Health monitoring (server AND processes) ○ Repave for release engineering, ○ Rotate Self-healing w/ Resurrector deployment, lifecycle management, and monitoring Storage management of distributed systems such Rolling upgrades via canaries as Kubernetes. Easy scaling of clusters Backup and Restore Rotating Server Credentials
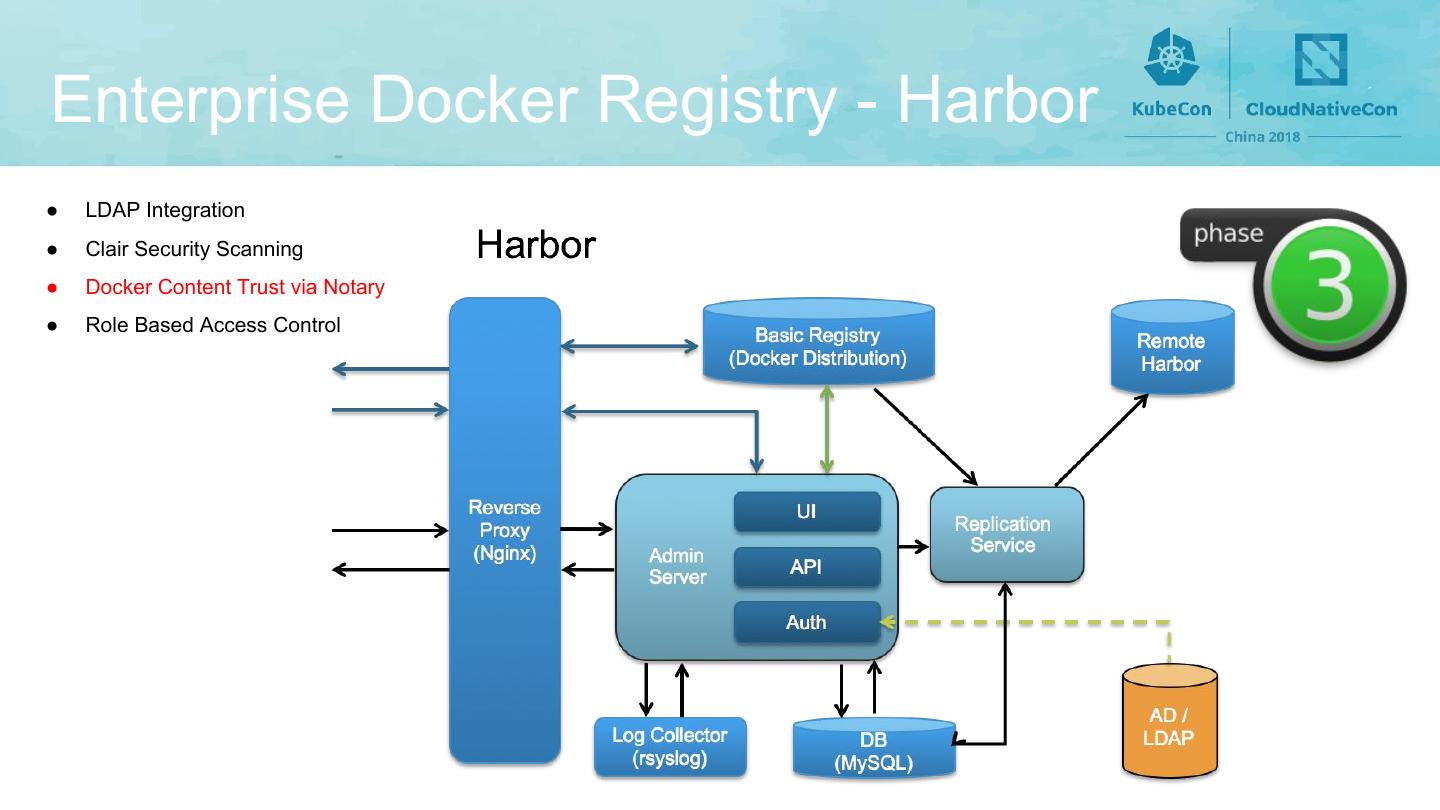
18 .Enterprise Docker Registry - Harbor ● LDAP Integration ● Clair Security Scanning ● Docker Content Trust via Notary ● Role Based Access Control