- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
确保部署管道的安全
展开查看详情
1 .Securing the Deploy Pipeline Felix Glaser Production Security Engineer
2 .curl | sudo bash
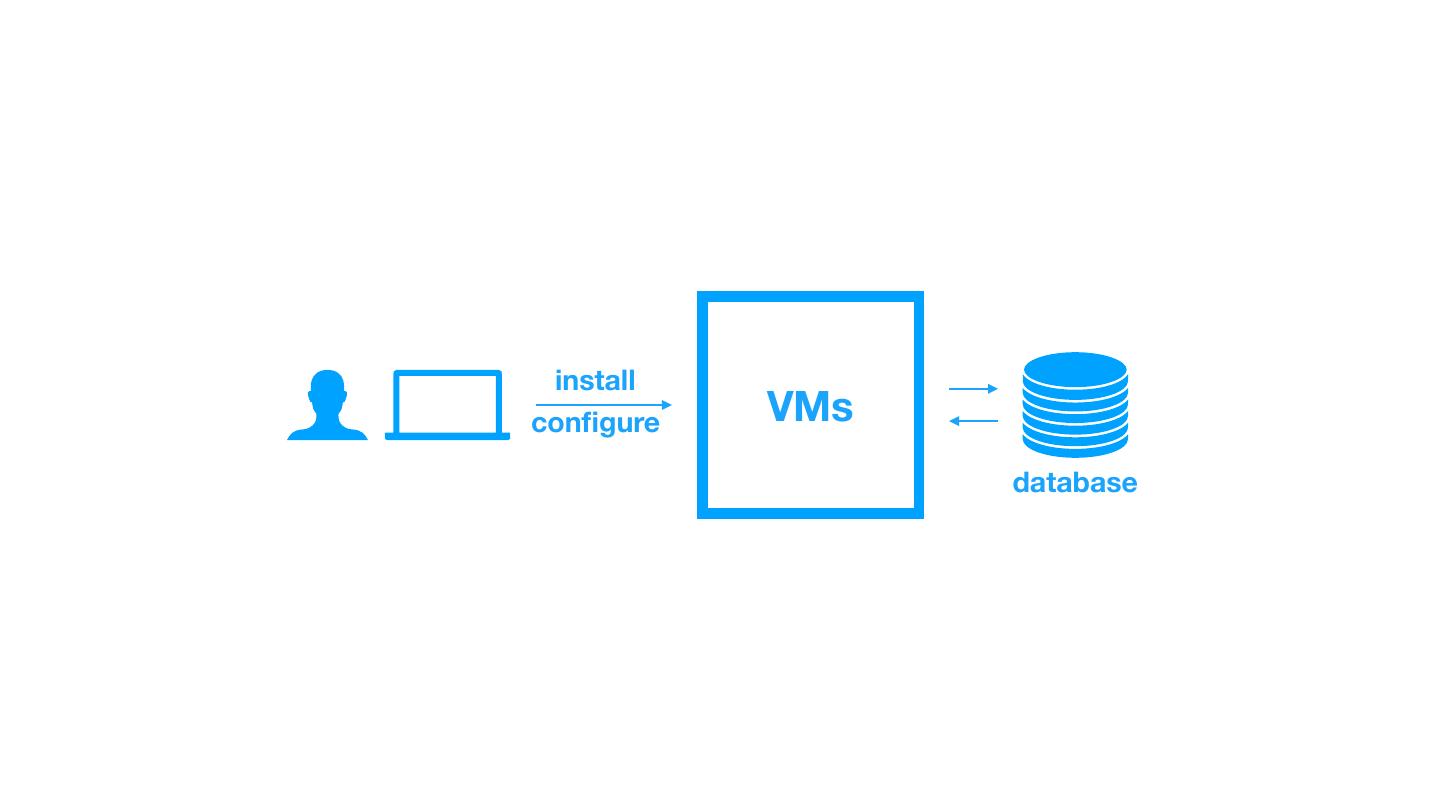
3 . install configure VMs database
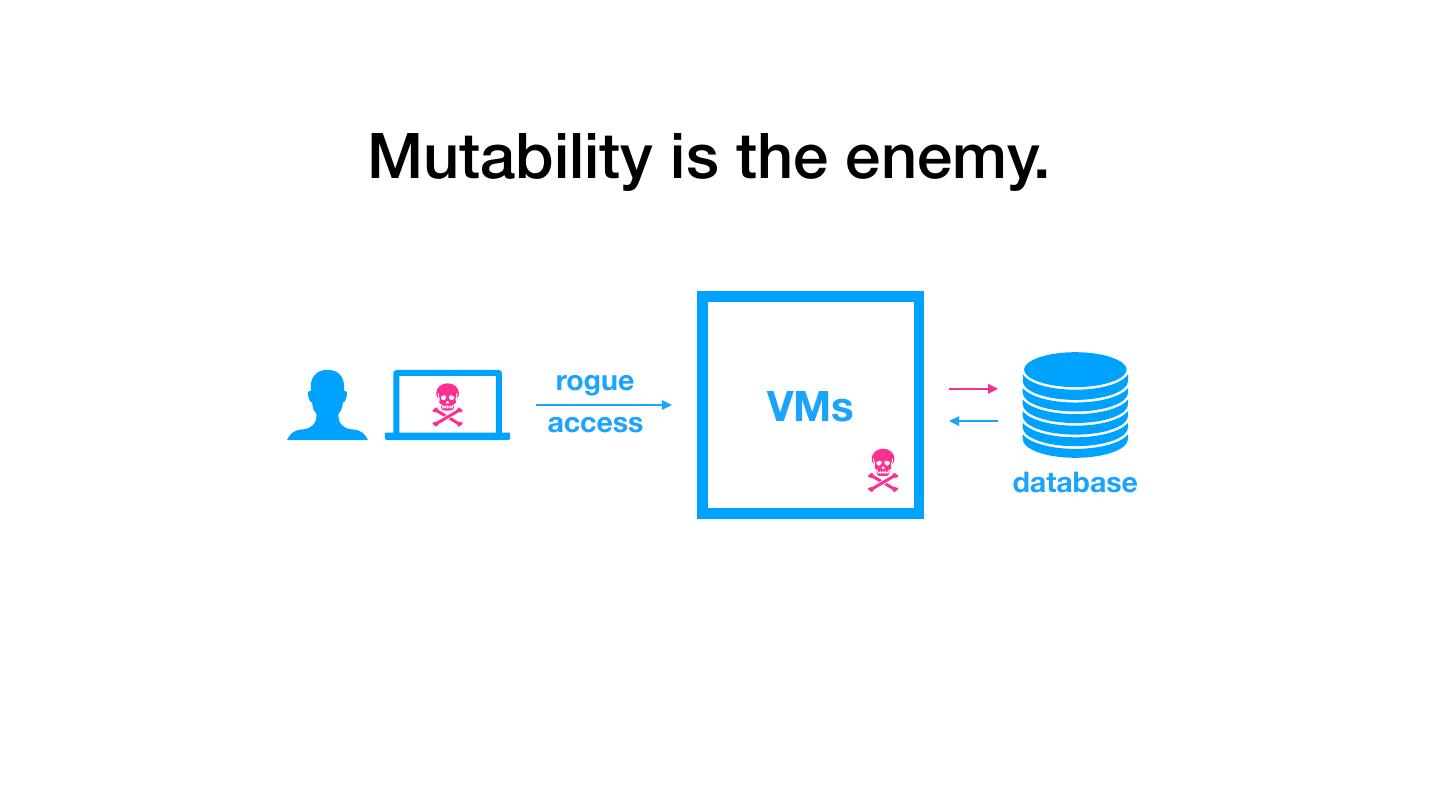
4 .Mutability is the enemy. rogue access VMs database
5 .Mutability is no more!
6 .Containerized infrastructure push code build deploy
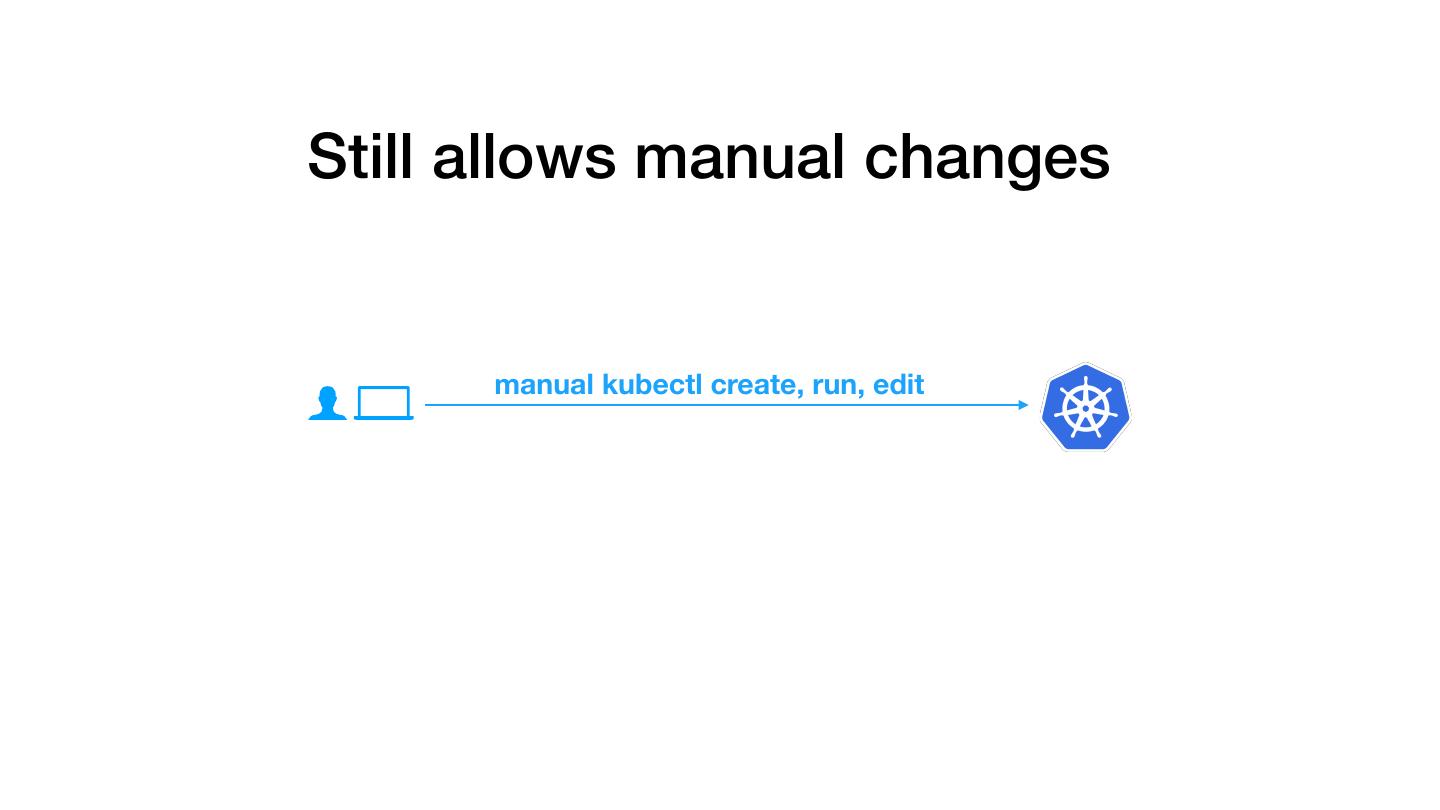
7 .Still allows manual changes manual kubectl create, run, edit
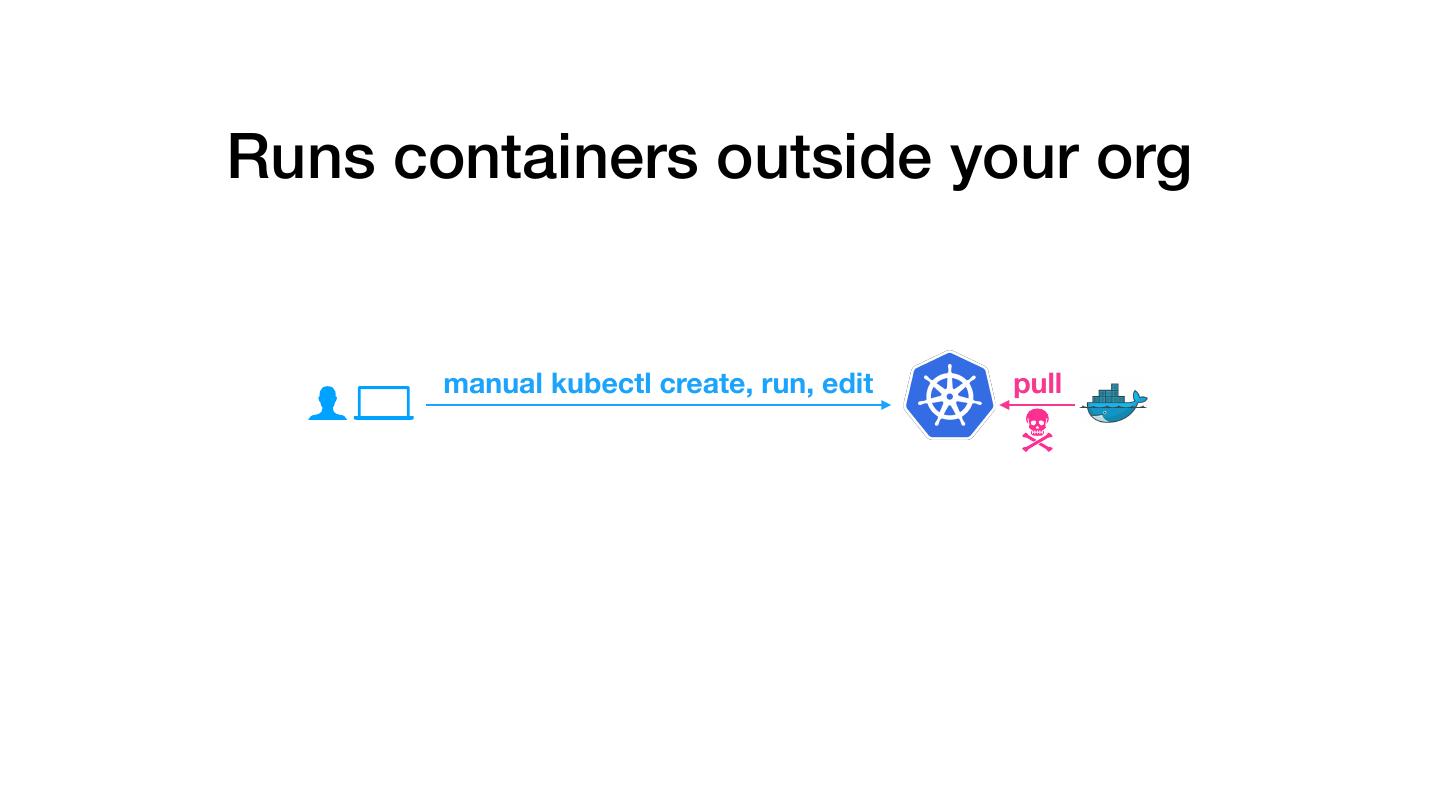
8 .Runs containers outside your org manual kubectl create, run, edit pull
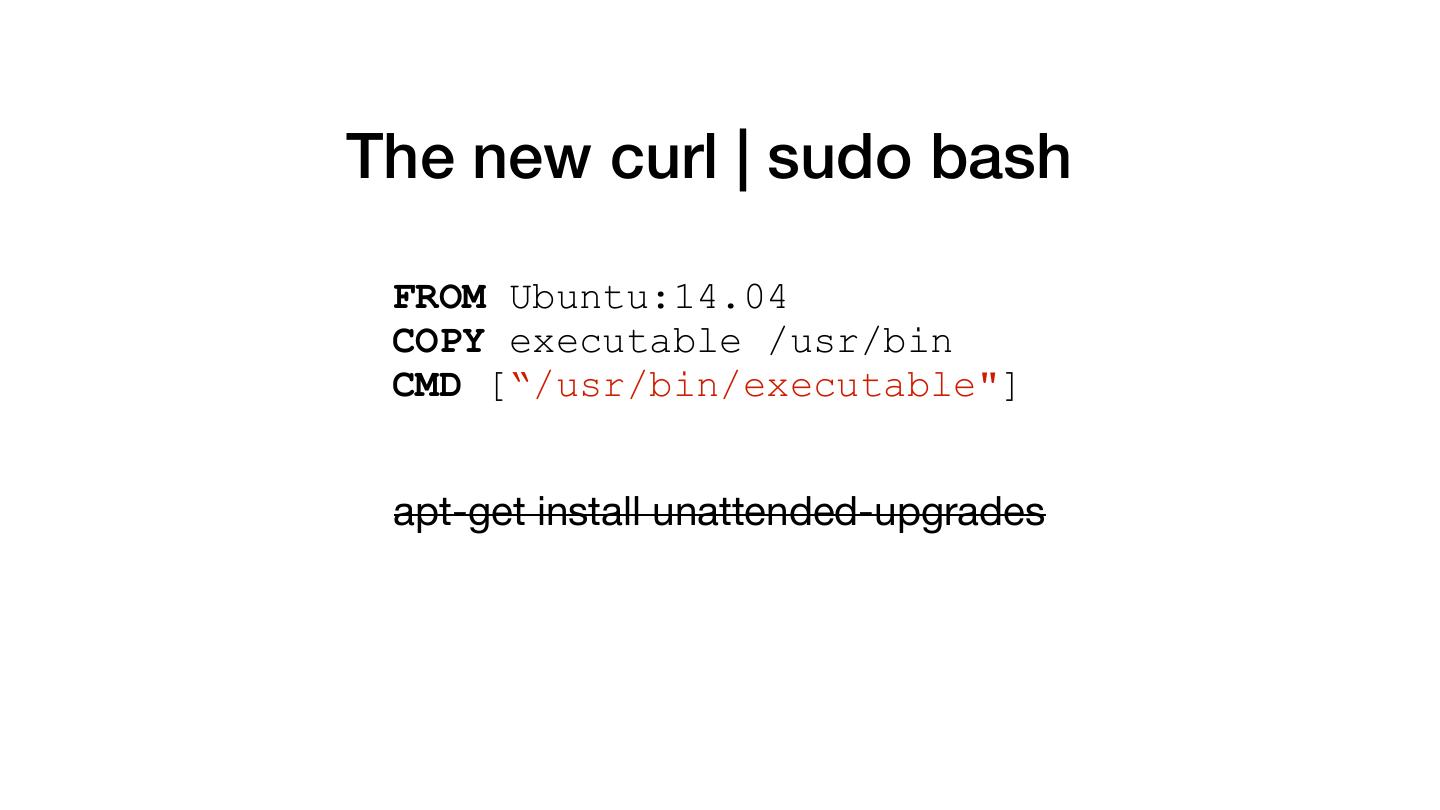
9 .The new curl | sudo bash FROM Ubuntu:14.04 COPY executable /usr/bin CMD [“/usr/bin/executable"]
10 .The new curl | sudo bash FROM Ubuntu:14.04 COPY executable /usr/bin CMD [“/usr/bin/executable"] apt-get install unattended-upgrades
11 .How do we fix this?
12 .Gate which images can run run ok?
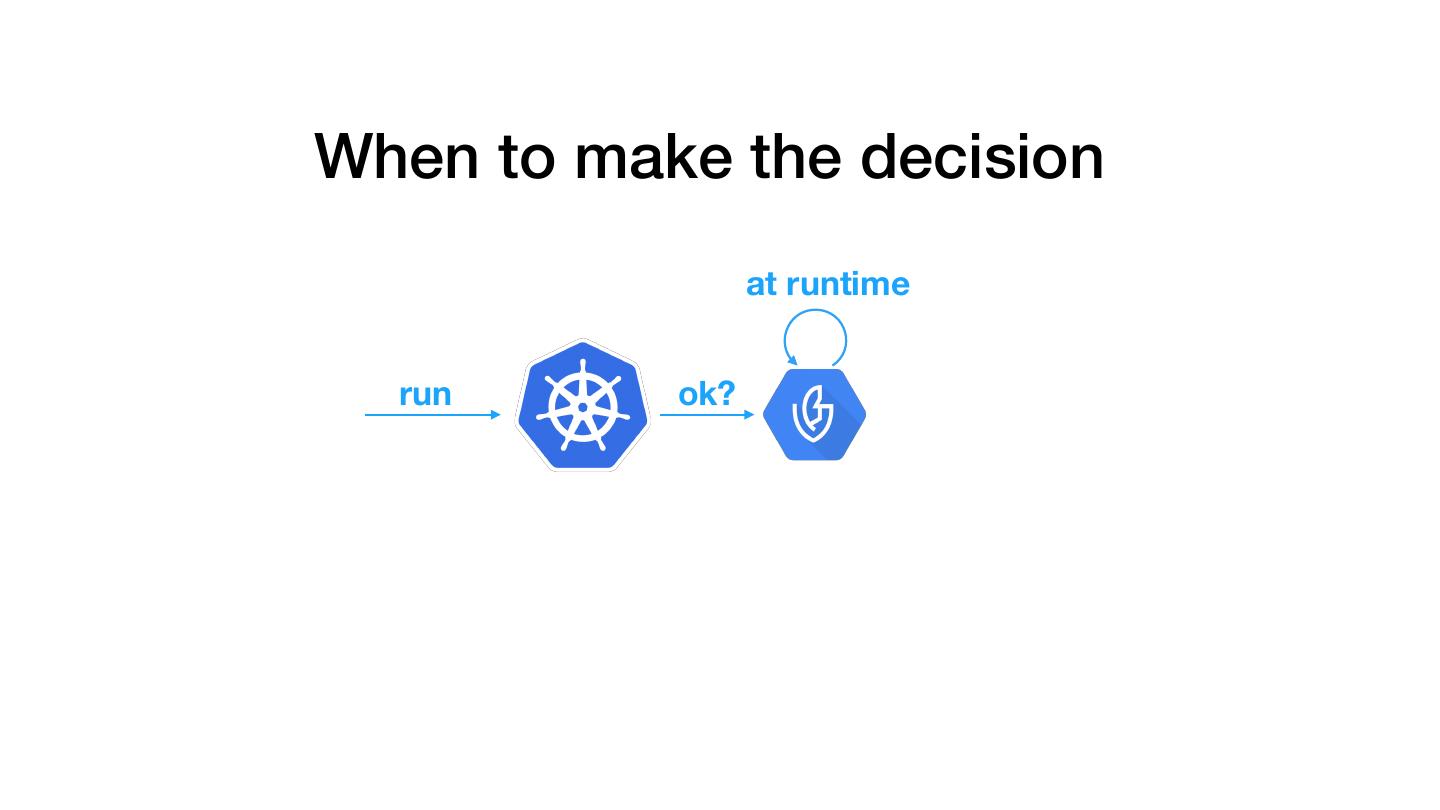
13 .When to make the decision at runtime run ok?
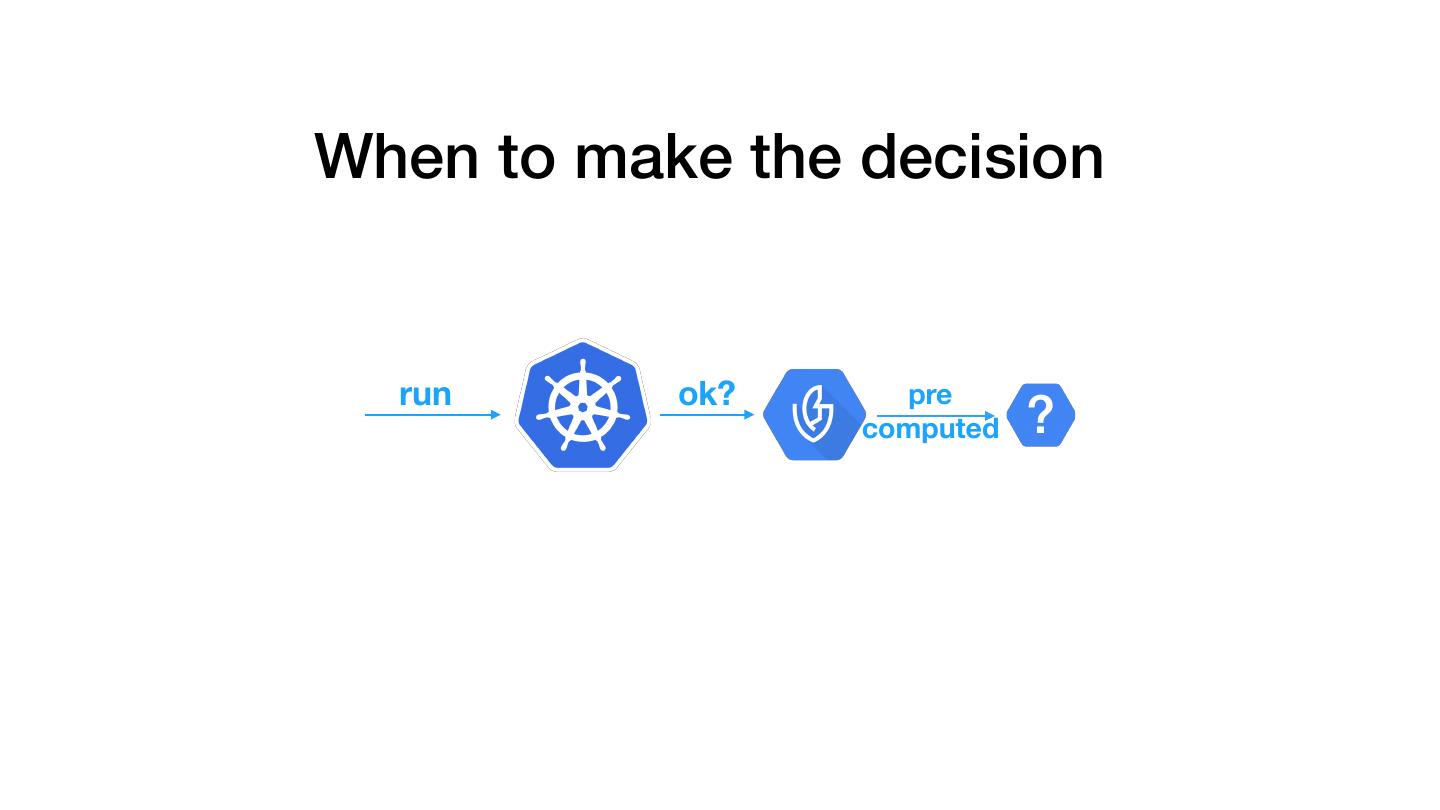
14 .When to make the decision run ok? pre computed ?
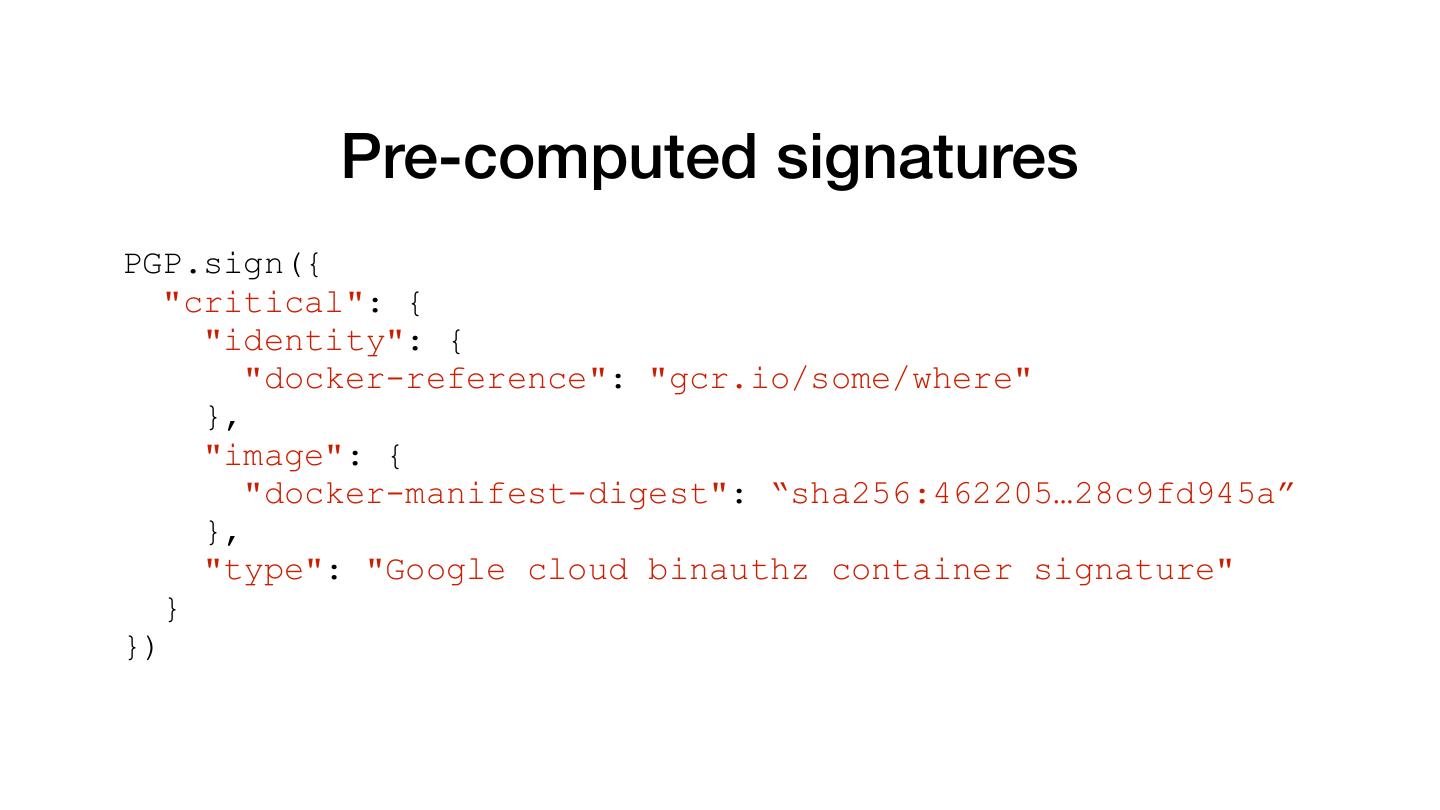
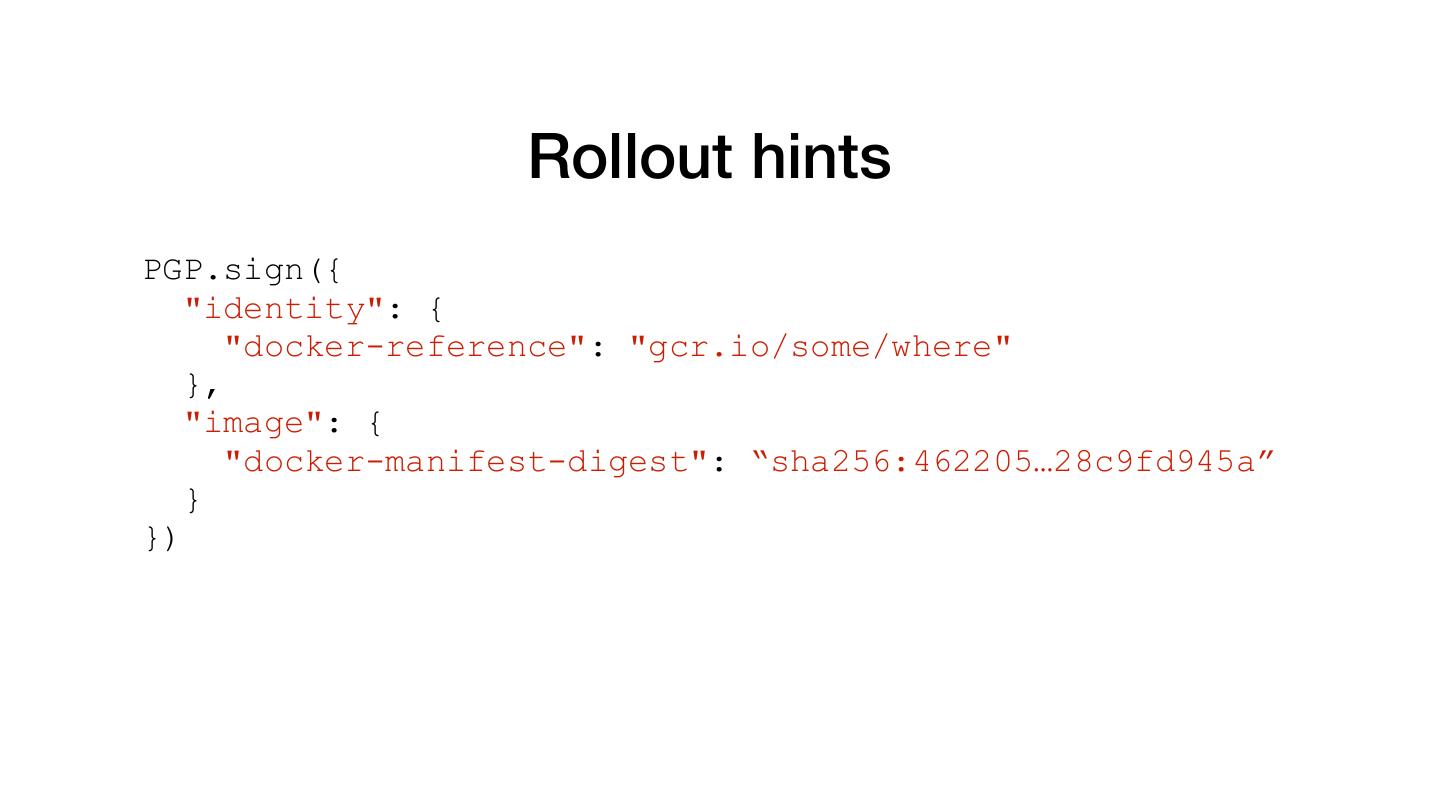
15 . Pre-computed signatures PGP.sign({ "critical": { "identity": { "docker-reference": "gcr.io/some/where" }, "image": { "docker-manifest-digest": “sha256:462205…28c9fd945a” }, "type": "Google cloud binauthz container signature" } })
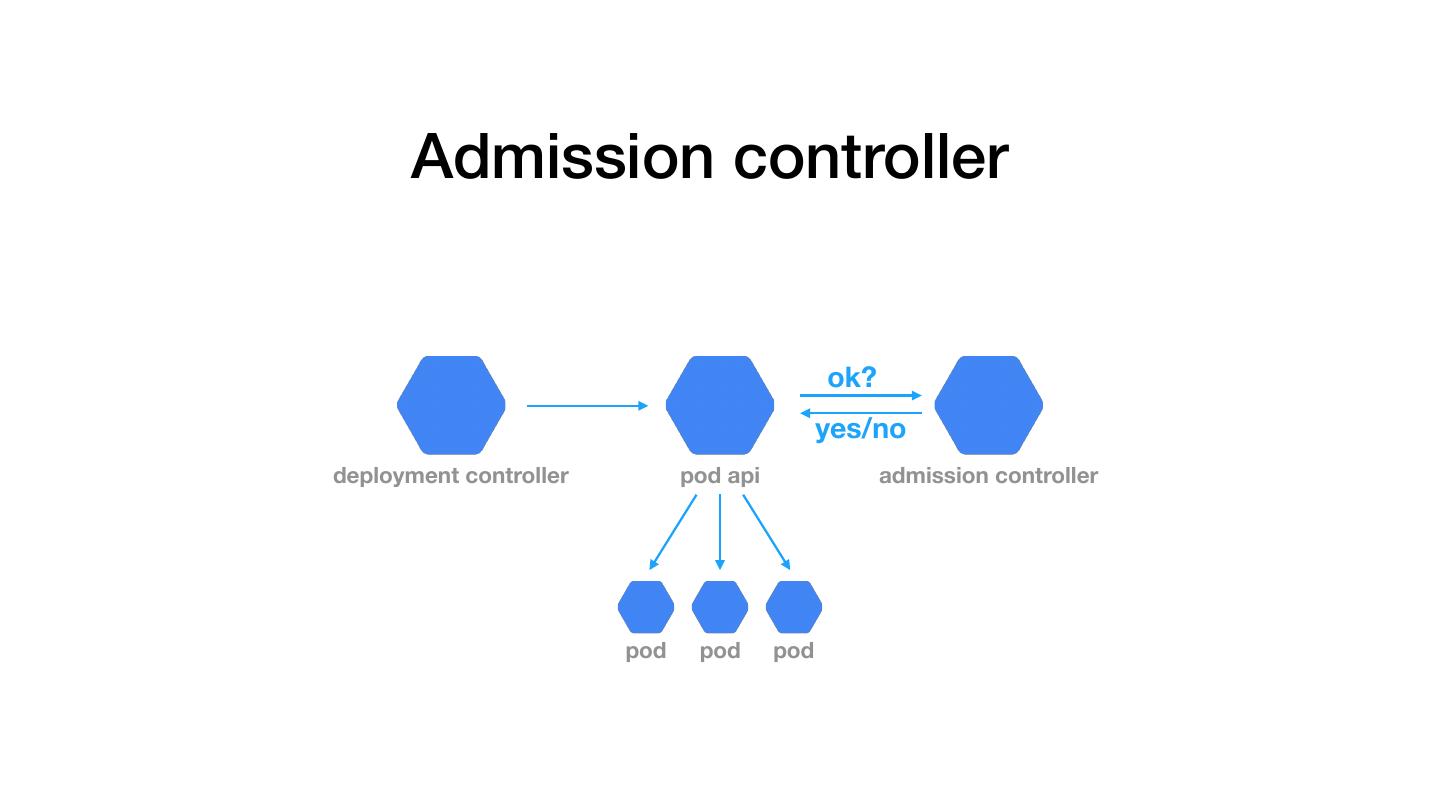
16 . Admission controller ok? yes/no deployment controller pod api admission controller pod pod pod
17 . Kritis github.com/grafeas/kritis
18 .Kritis gating deploys ll pu pu ll apply ok? rogue access
19 . Grafeas github.com/grafeas/grafeas
20 . Kind, note and occurrence Kind Note Summary Occurrence Summary A logical attestation role or An attestation by an authority for a specific property ATTESTATION authority, used as an anchor for and resource specific attestations Filesystem locations detailing where the package is PACKAGE Package descriptions installed in a specific resource CVE or vulnerability description VULNERABILITY and details including severity, Affected packages/versions in a specific resource versions
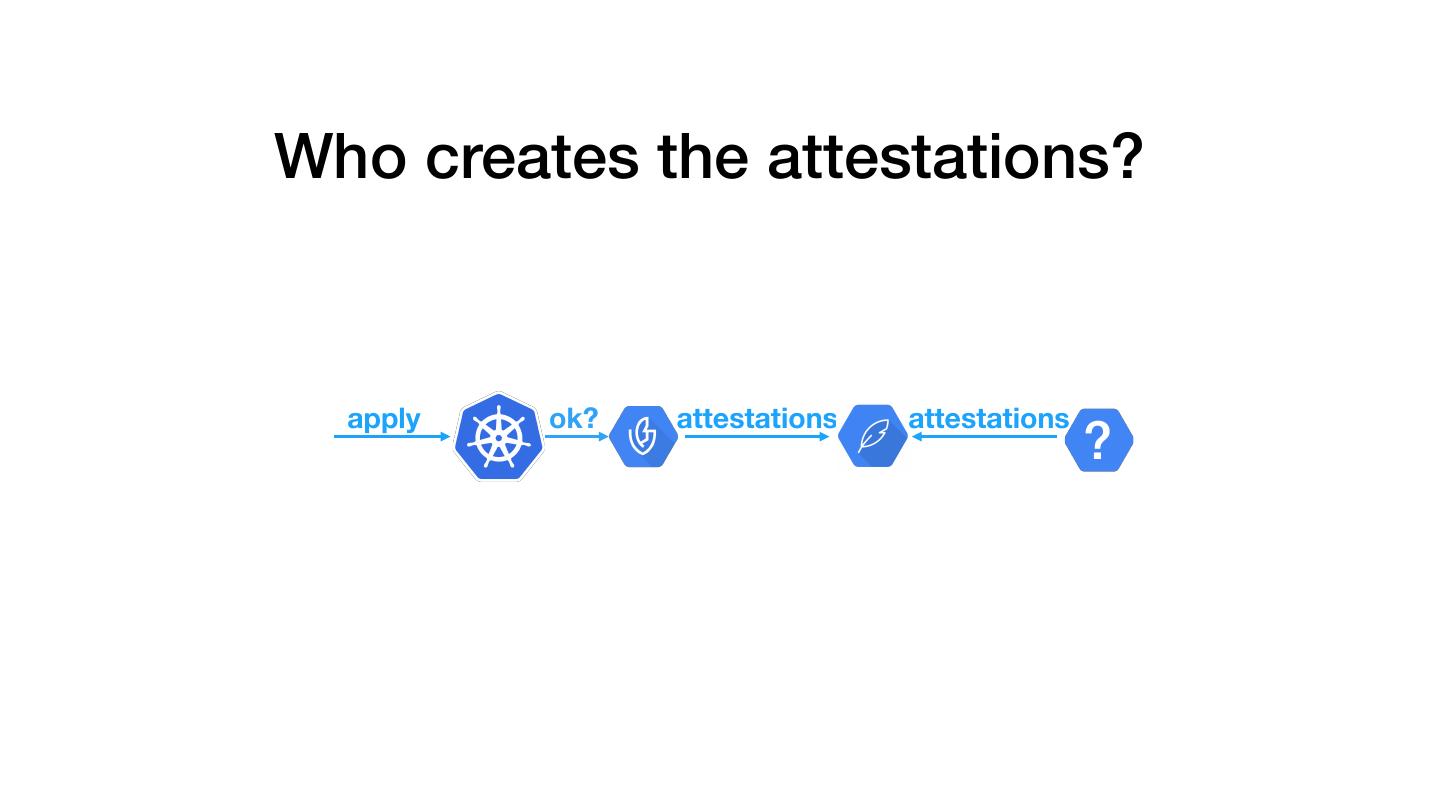
21 .Who creates the attestations? apply ok? attestations attestations ?
22 . 🎟 Voucher github.com/shopify/voucher
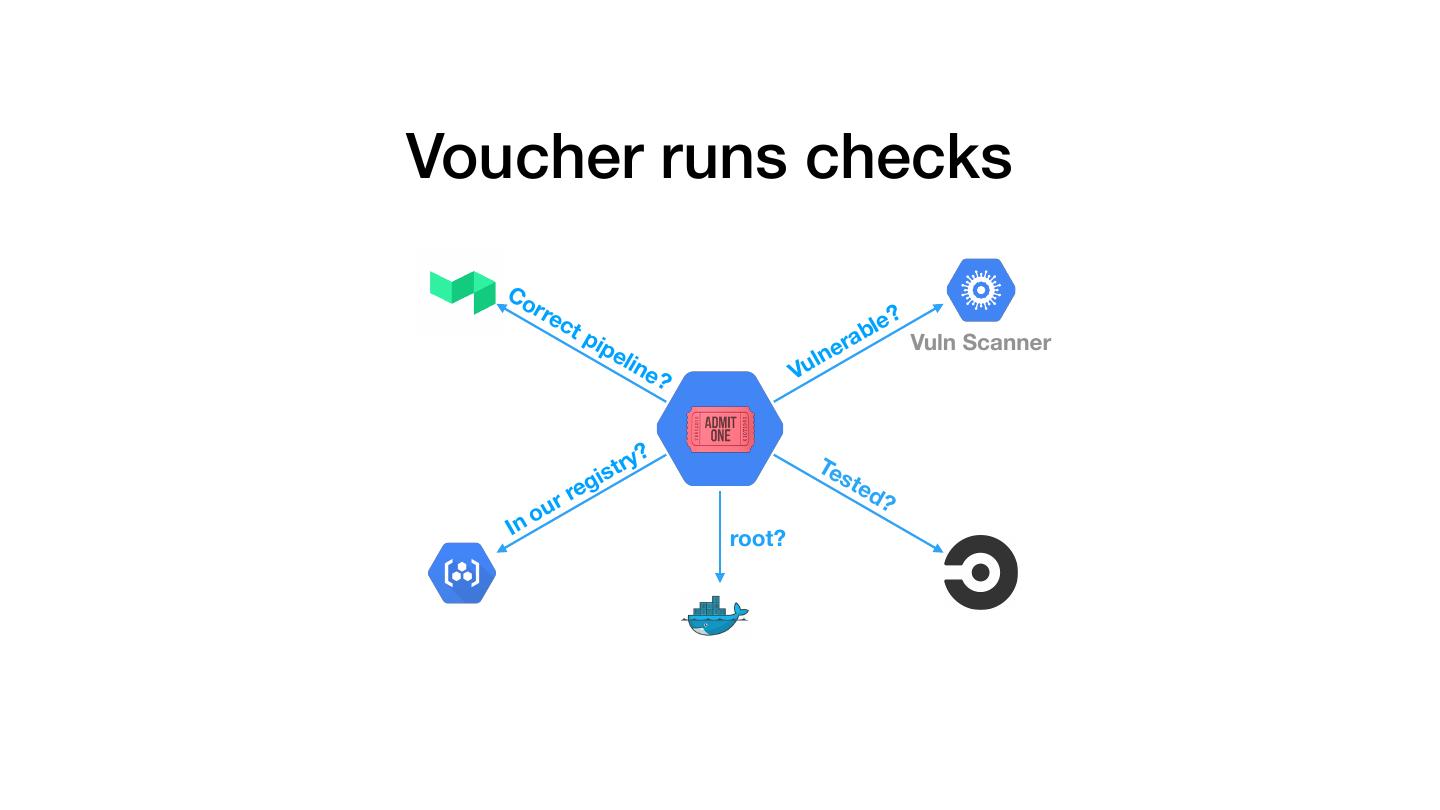
23 .Voucher runs checks Co rre ? ct bl e pip r a Vuln Scanner eli lne ne Vu ? gis tr y ? 🎟 Te s ted re ? r ou In root?
24 .Which attestations are required? apply ok? attestations attestations 🎟 requires which attestation ?
25 . Policies admissionWhitelistPatterns: - namePattern: nginx/image:sha256… defaultAdmissionRule: enforcementMode: ENFORCED_BLOCK_AND_AUDIT_LOG evaluationMode: REQUIRE_ATTESTATION requireAttestationsBy: - projects/binauthz/attestors/name name: projects/shopify-security/policy
26 . Policies per cluster admissionWhitelistPatterns: -namePattern: nginx/image:sha256… clusterAdmissionRules: us-east1-a.cluster: evaluationMode: REQUIRE_ATTESTATION enforcementMode: ENFORCED_BLOCK_AND_AUDIT_LOG requireAttestationsBy: - projects/name/attestors/name defaultAdmissionRule: …
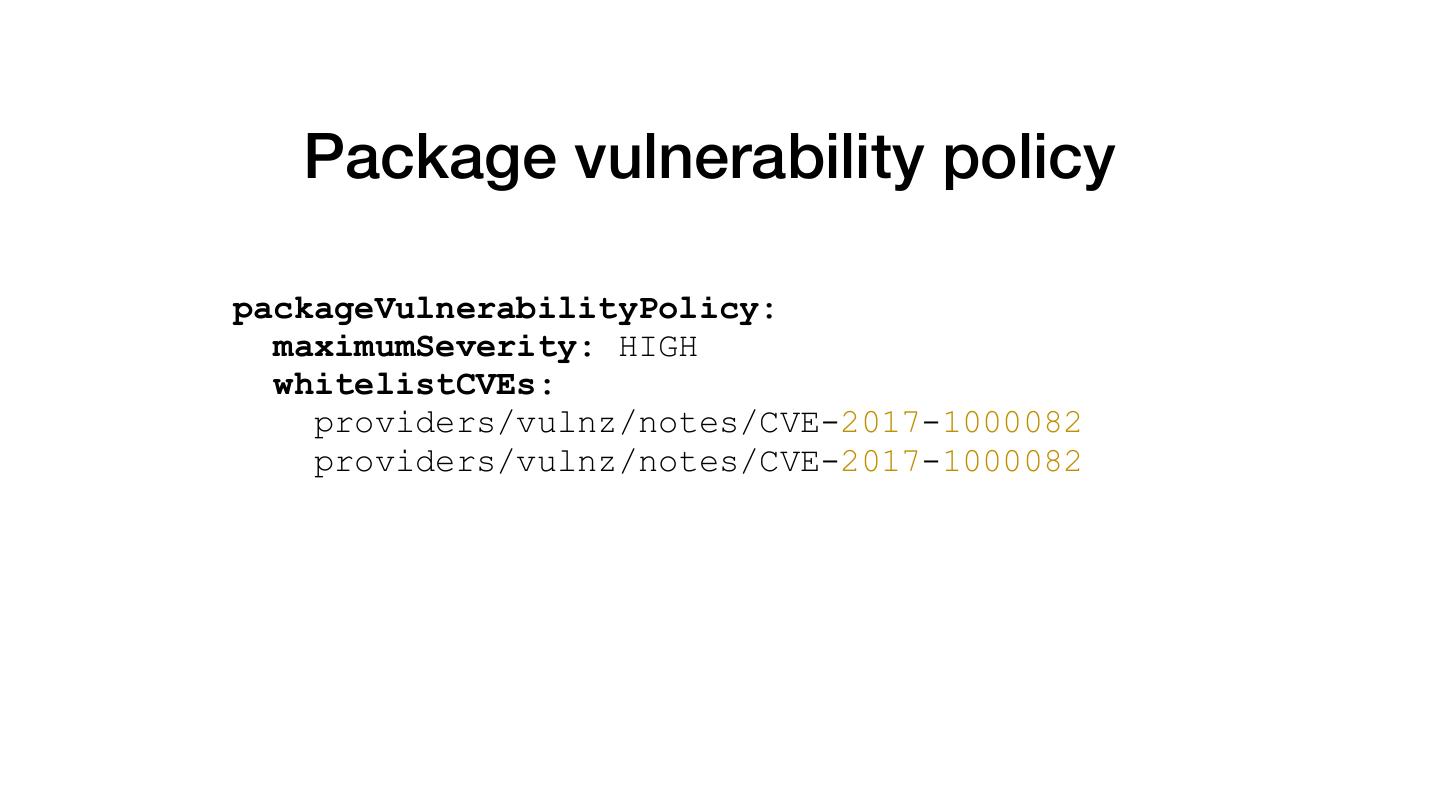
27 . Package vulnerability policy packageVulnerabilityPolicy: maximumSeverity: HIGH whitelistCVEs: providers/vulnz/notes/CVE-2017-1000082 providers/vulnz/notes/CVE-2017-1000082
28 .Policies per project/cluster apply ok? attestations attestations 🎟 requires which attestation P1 P2
29 .But what about emergencies? That require changes right now!