- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
通过 Vault 进行 Istio 证书管理
展开查看详情
1 .Istio Certificate Management Through Vault Lei Tang, Yonggang Liu, Google LLC.
2 .Lei Tang Oliver (Yonggang) Liu Software Engineer Software Engineer Istio Istio leitang@google.com yonggangl@google.com wechat: LTANG2015 http://oliverliu.org
3 .Istio manages your microservices Relieve burden of service owners. Bring order to chaos. Photo credits
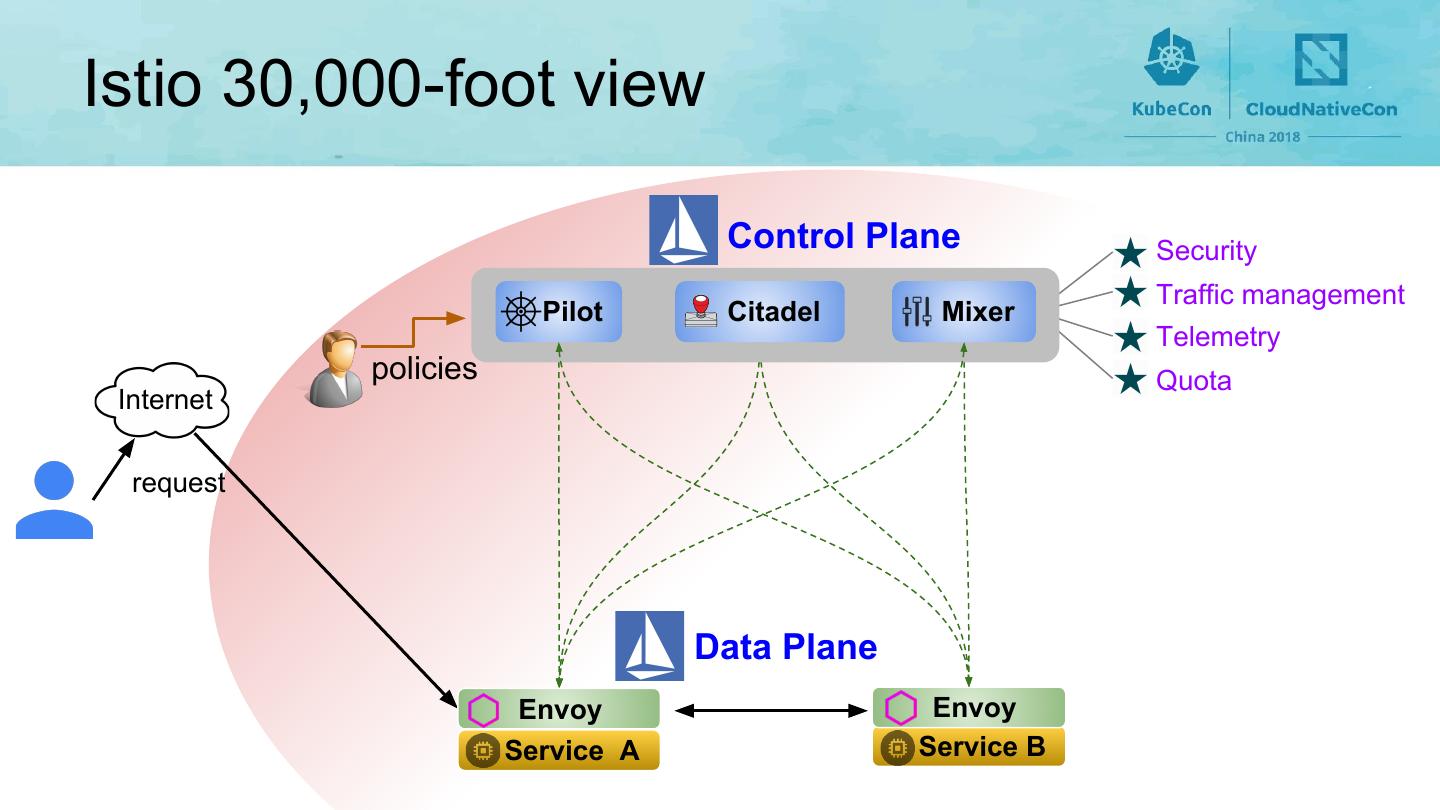
4 .Istio 30,000-foot view Control Plane Security Traffic management Pilot Citadel Mixer Telemetry policies Quota Internet request Data Plane Envoy Envoy Service A Service B
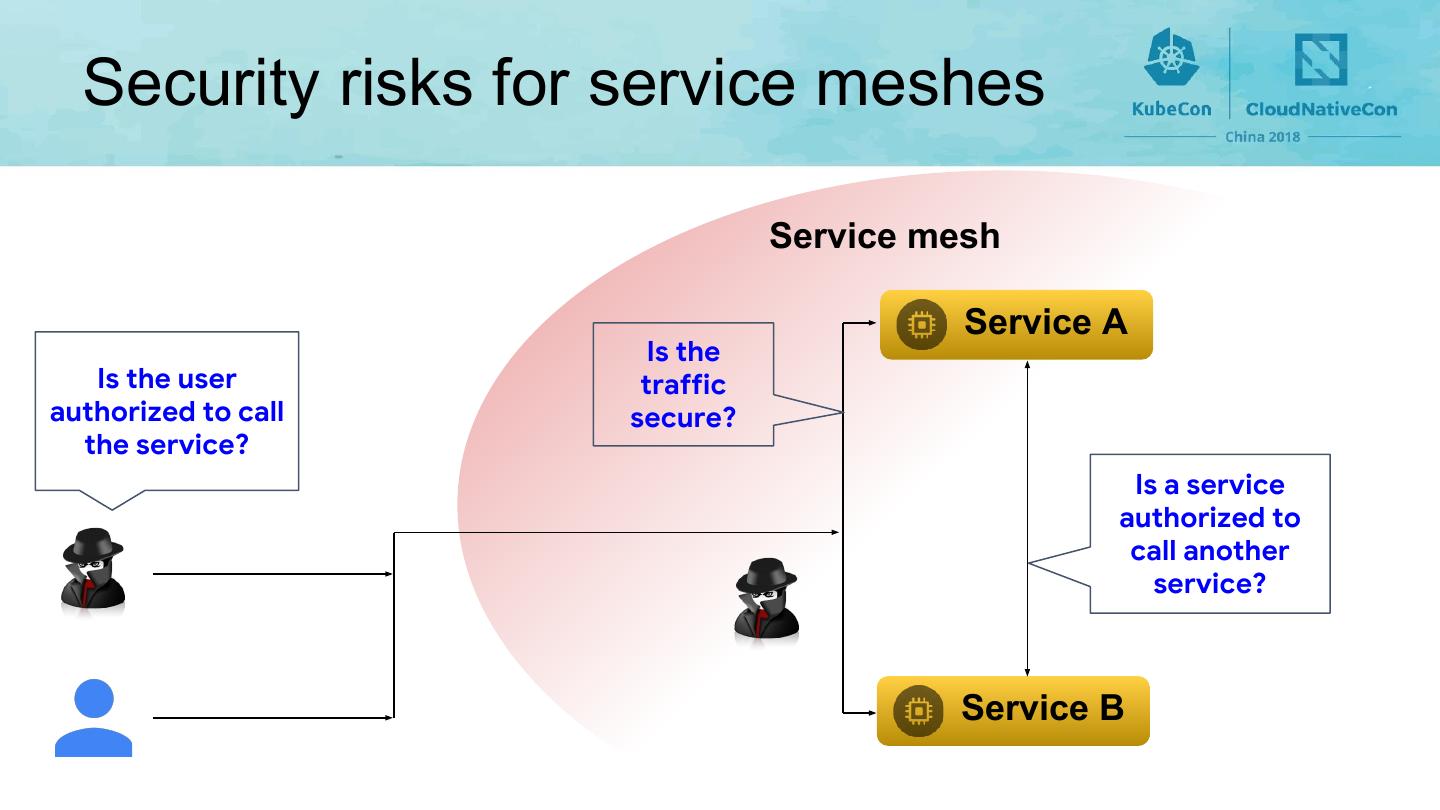
5 . Security risks for service meshes Service mesh Service A Is the Is the user traffic authorized to call secure? the service? Is a service authorized to call another service? Service B
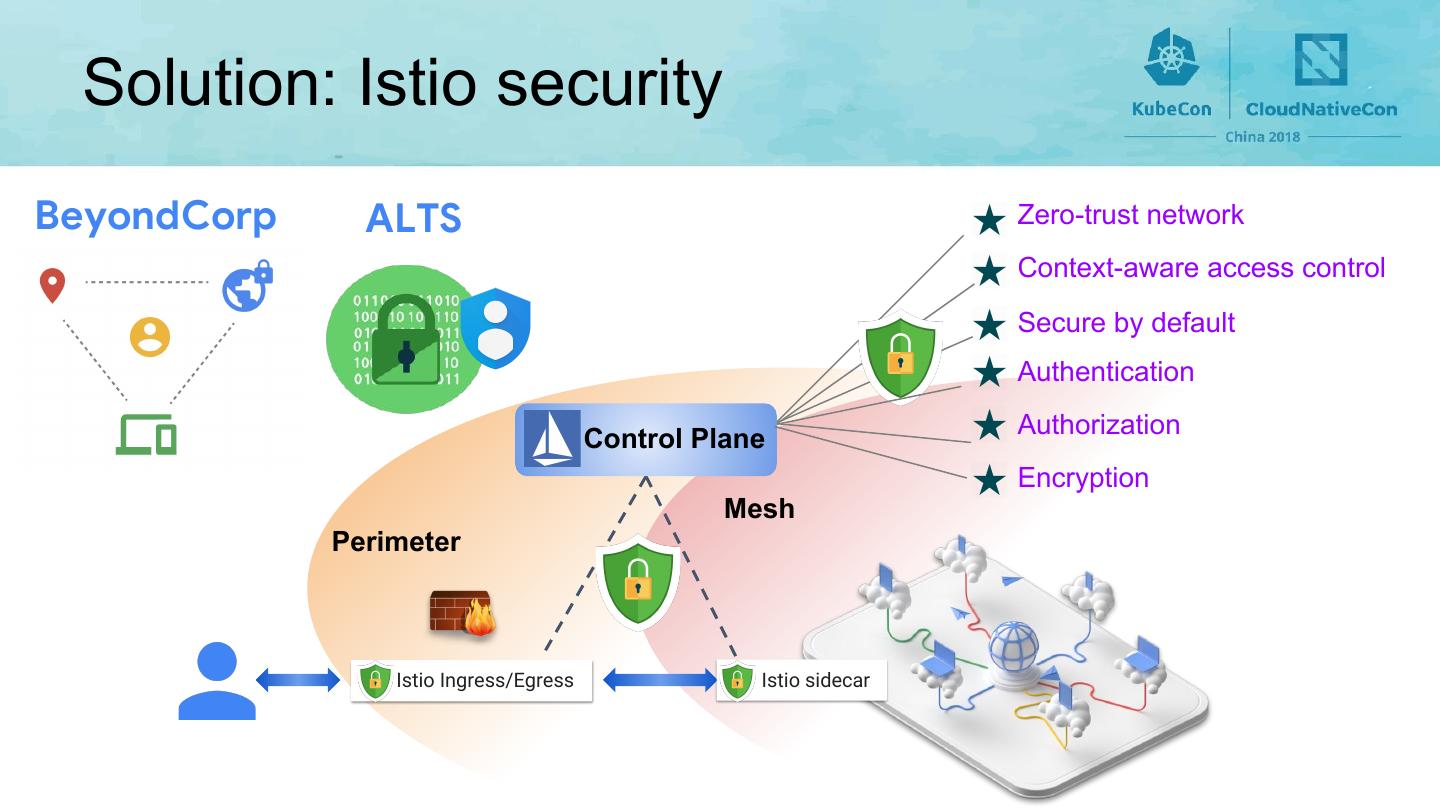
6 . Solution: Istio security BeyondCorp ALTS Zero-trust network Context-aware access control Secure by default Authentication Control Plane Authorization Encryption Mesh Perimeter Istio Ingress/Egress Istio sidecar
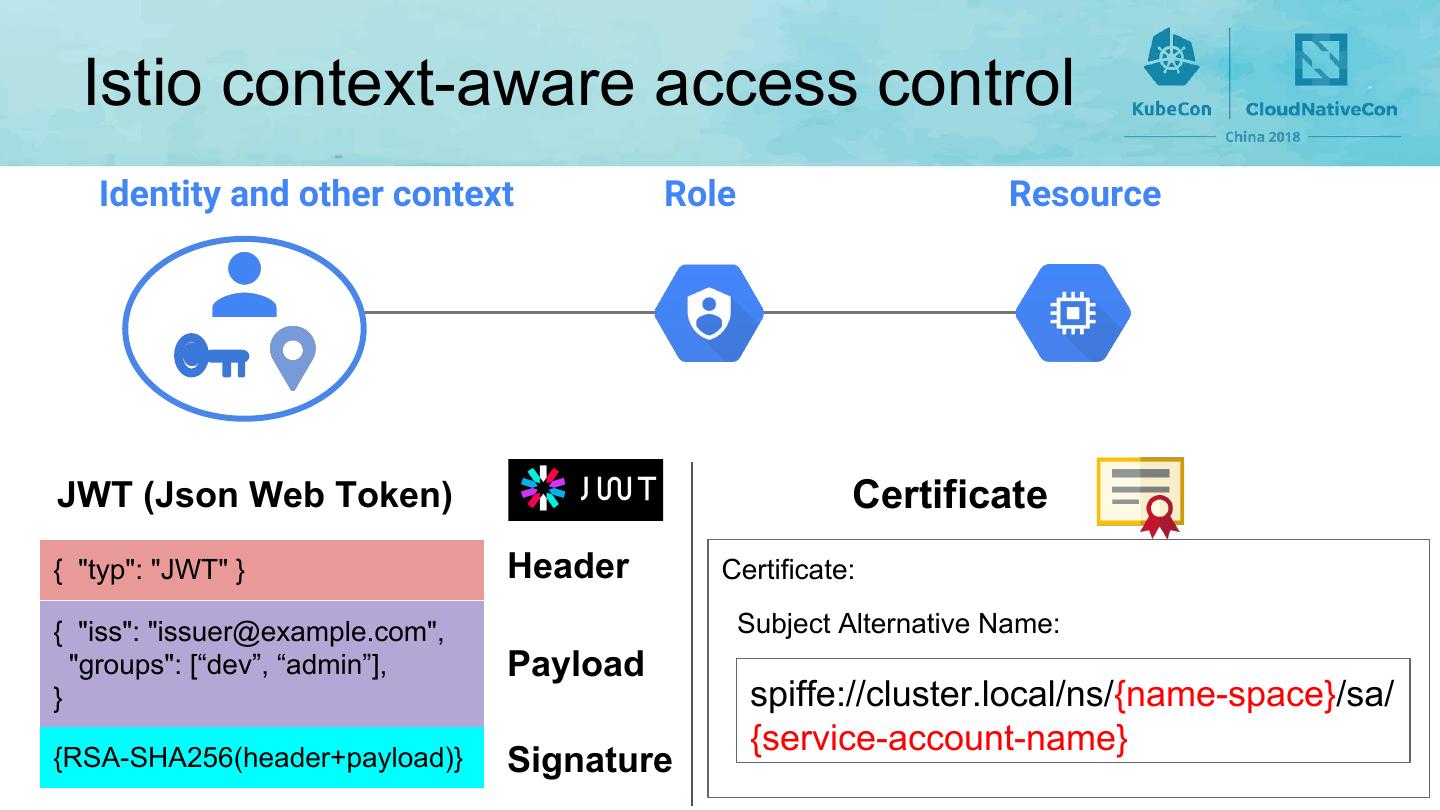
7 . Istio context-aware access control Identity and other context Role Resource JWT (Json Web Token) Certificate { "typ": "JWT" } Header Certificate: { "iss": "issuer@example.com", Subject Alternative Name: "groups": [“dev”, “admin”], Payload } spiffe://cluster.local/ns/{name-space}/sa/ {service-account-name} {RSA-SHA256(header+payload)} Signature
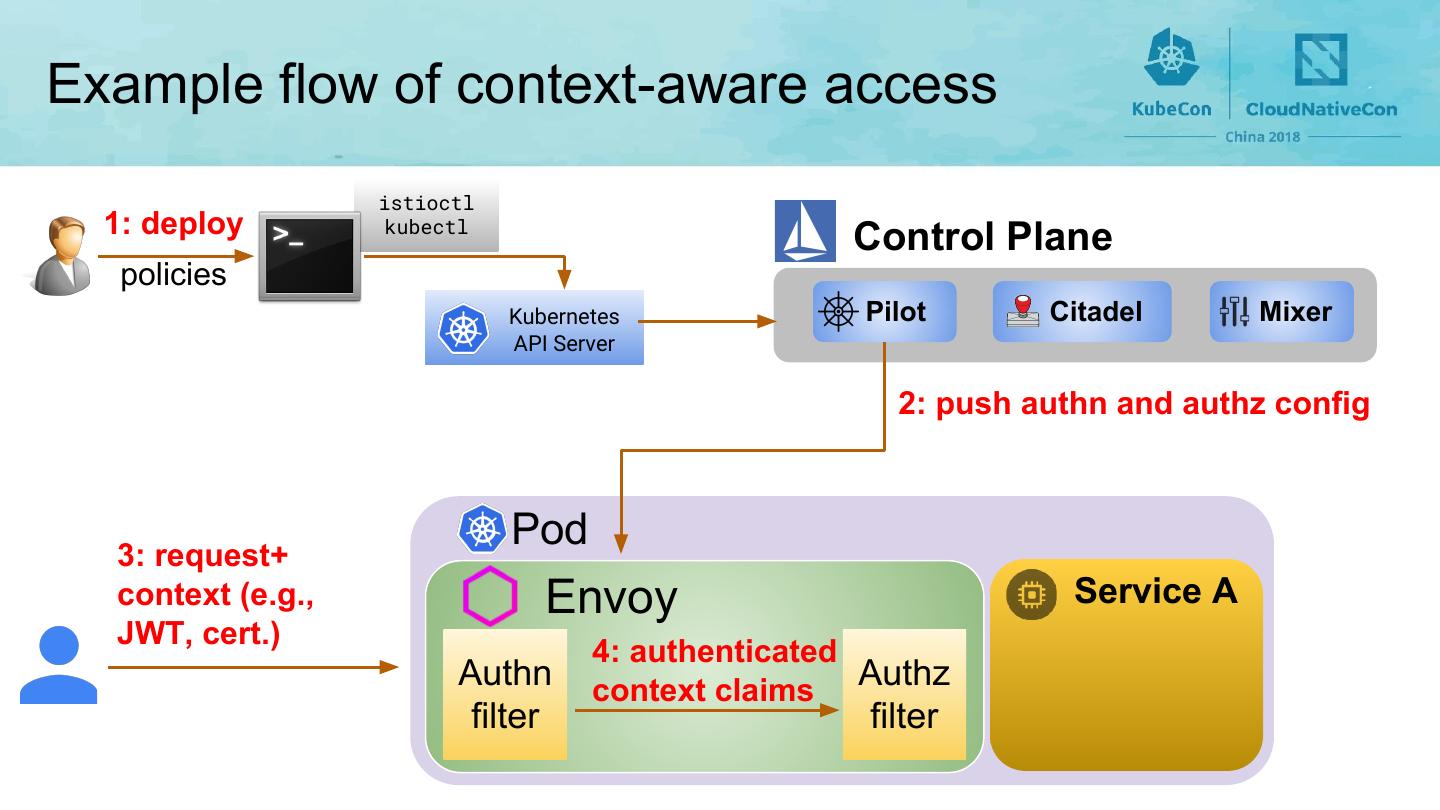
8 .Example flow of context-aware access istioctl 1: deploy kubectl Control Plane policies Kubernetes Pilot Citadel Mixer API Server 2: push authn and authz config Pod 3: request+ context (e.g., Envoy Service A JWT, cert.) 4: authenticated Authn context claims Authz filter filter
9 .Demo: Istio context-aware access control ● A user must be in a specific group to access a sensitive service. ● The access must be protected by mTLS. ● May also control the calling path. mTLS mTLS JWT JWT Sensitive Service RBAC RBAC
10 . Demo: authorization policies apiVersion: "rbac.istio.io/v1alpha1" apiVersion: "rbac.istio.io/v1alpha1" kind: ServiceRole kind: ServiceRoleBinding metadata: metadata: name: httpbin-viewer name: bind-httpbin-viewer spec: spec: rules: subjects: - services: - properties: ["httpbin.rbac-groups-test-ns.svc.cluster.local"] request.auth.claims[groups]: "group1" methods: ["GET"] roleRef: … kind: ServiceRole name: "httpbin-viewer" ...
11 .Demo: authentication policy apiVersion: "authentication.istio.io/v1alpha1" kind: "Policy" metadata: name: "require-mtls-jwt" spec: targets: - name: httpbin peers: - mtls: {} origins: - jwt: issuer: "testing@secure.istio.io"
12 .Demo Demo of Istio context-aware access control
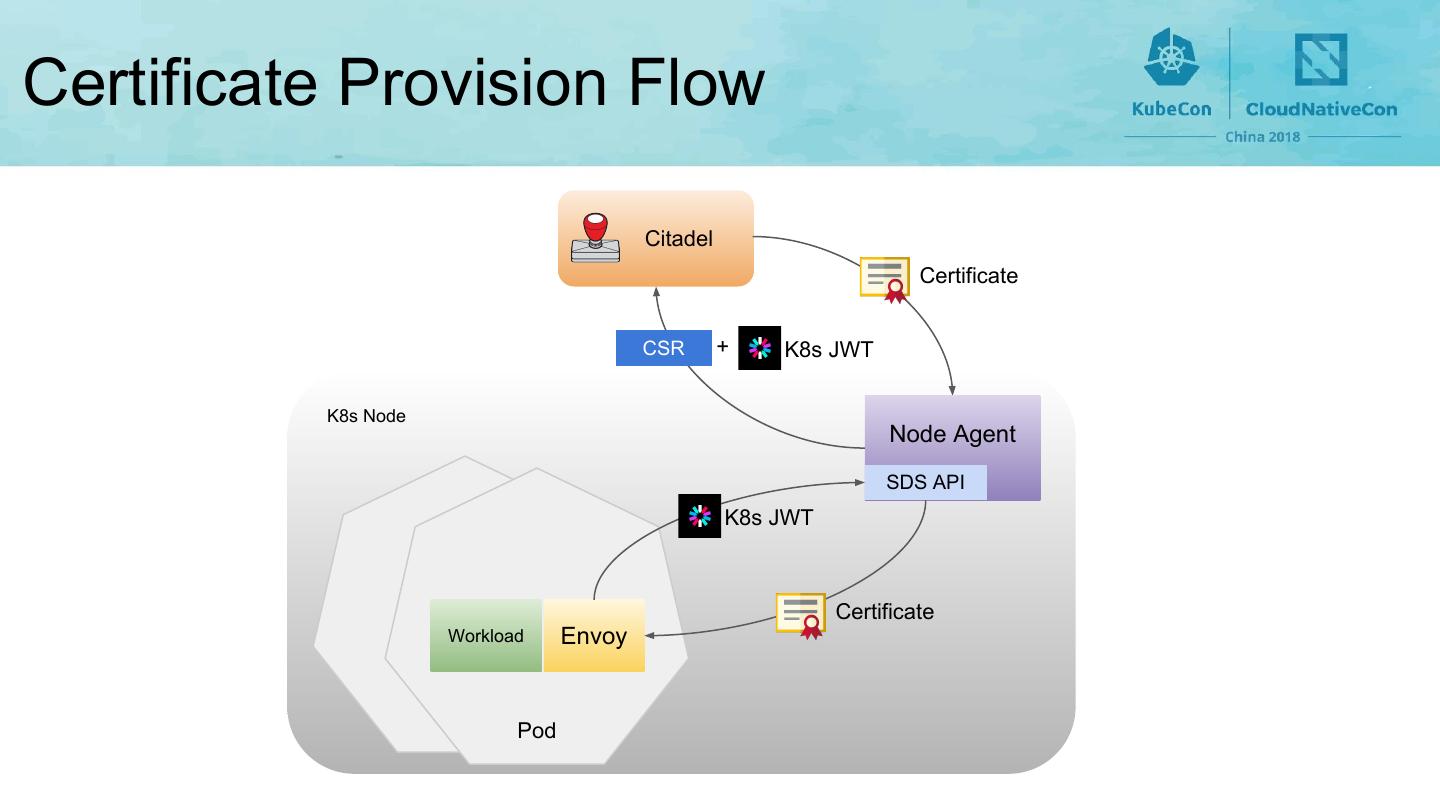
13 .Certificate Provision Flow Citadel Certificate CSR + K8s JWT K8s Node Node Agent SDS API K8s JWT Certificate Workload Envoy Pod
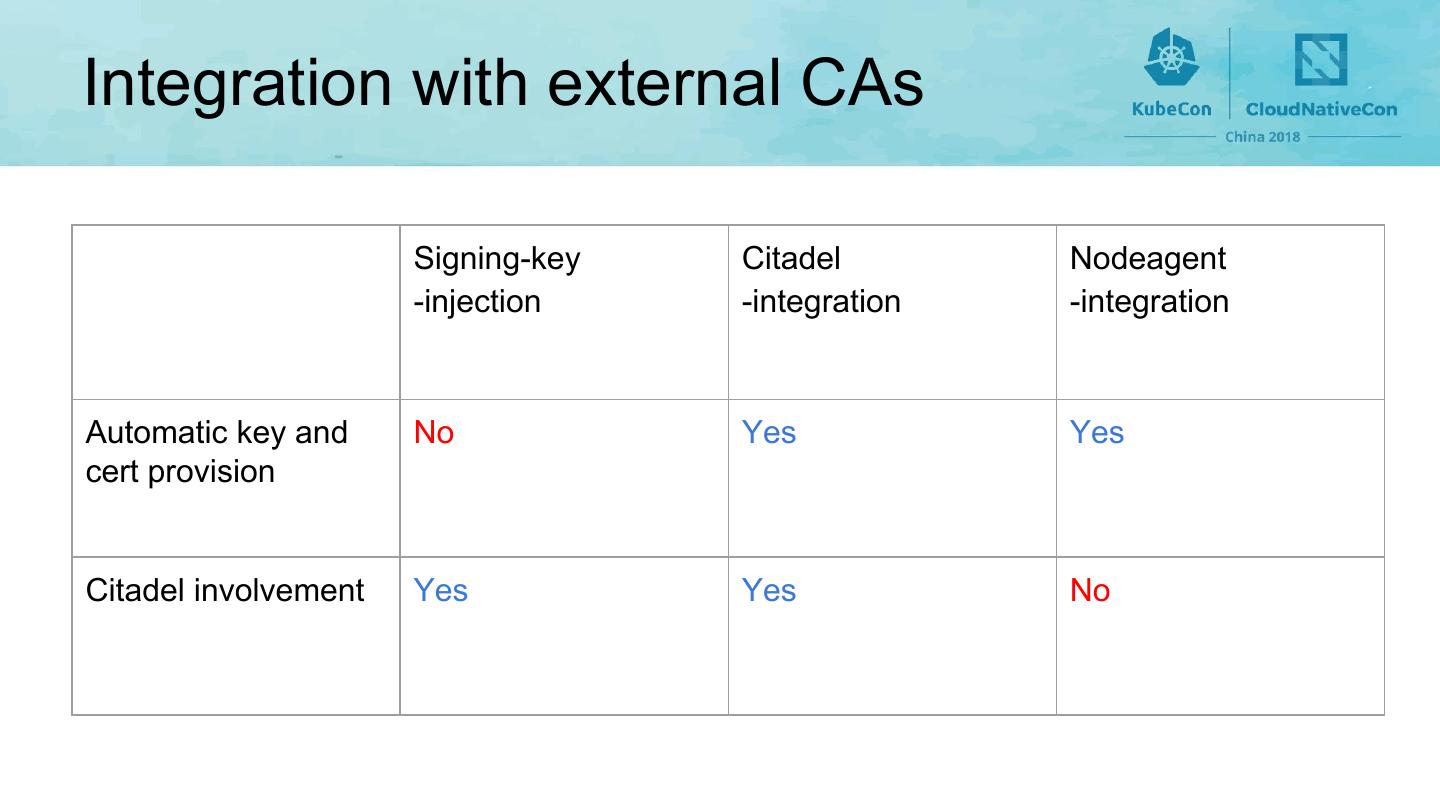
14 .Integration with external CAs Signing-key Citadel Nodeagent -injection -integration -integration Automatic key and No Yes Yes cert provision Citadel involvement Yes Yes No
15 .Approach 1: Signing-key-injection External CA ● Operator involved for signing key and Secret volume mount cert rotation Citadel K8s node Node Agent pod pod
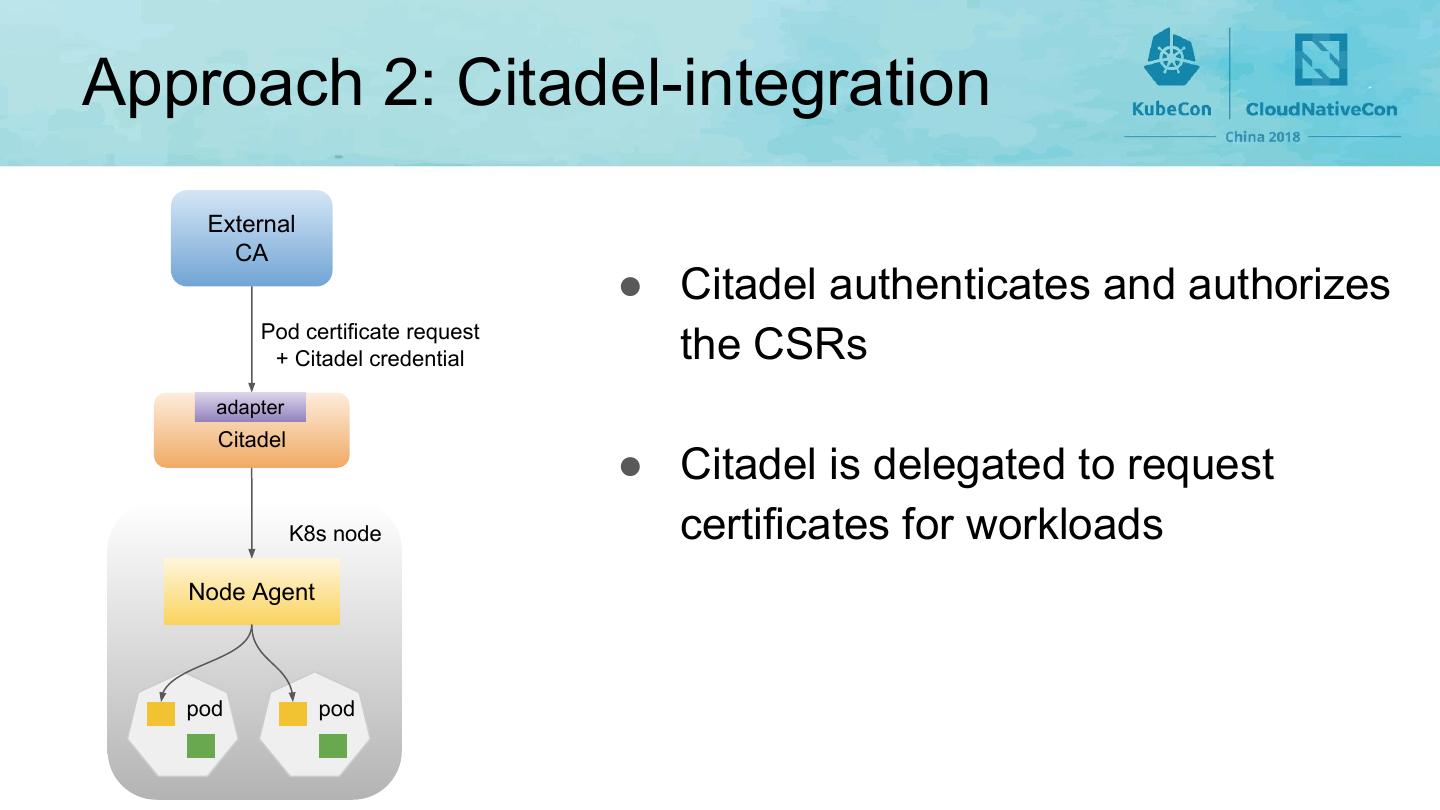
16 .Approach 2: Citadel-integration External CA ● Citadel authenticates and authorizes Pod certificate request + Citadel credential the CSRs adapter Citadel ● Citadel is delegated to request K8s node certificates for workloads Node Agent pod pod
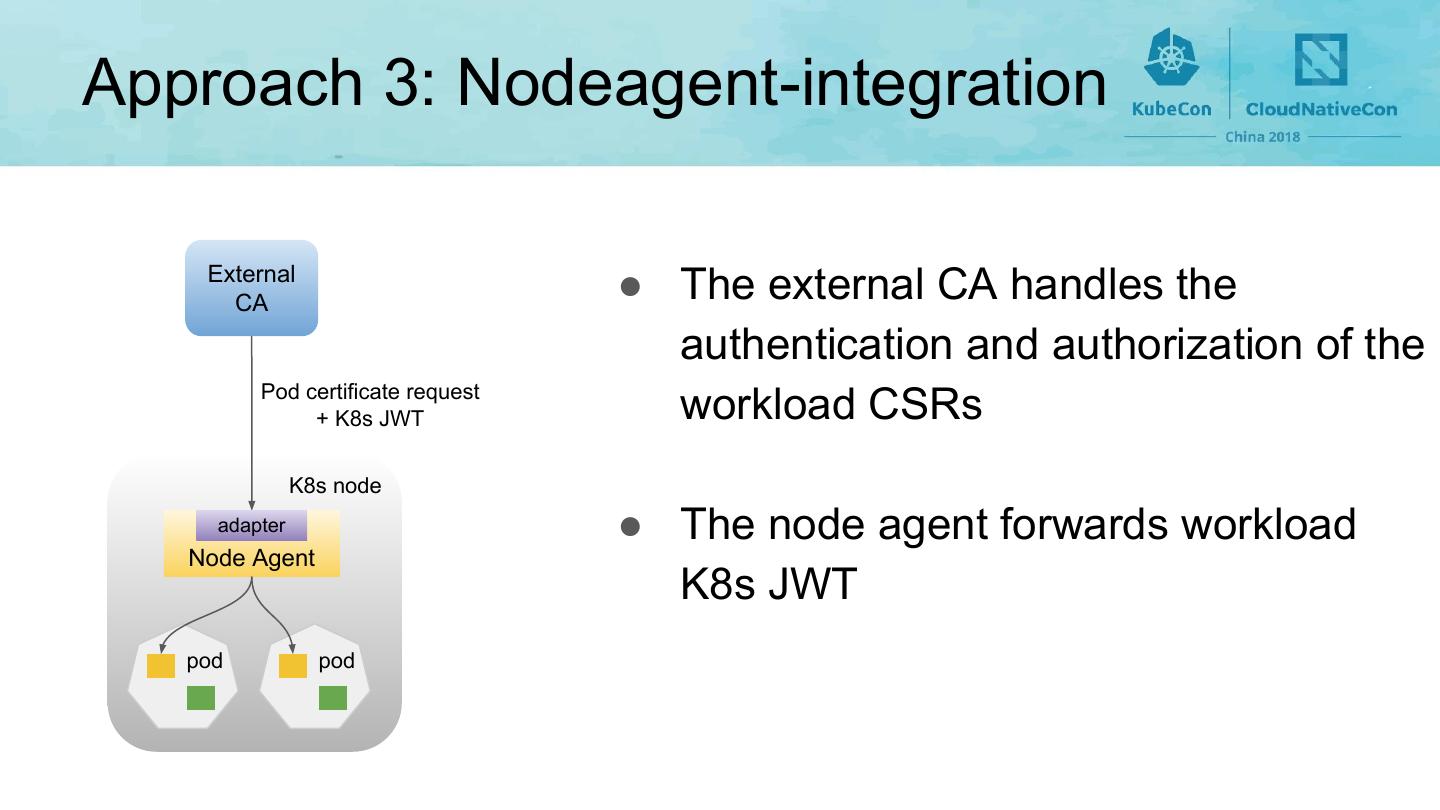
17 .Approach 3: Nodeagent-integration External CA ● The external CA handles the authentication and authorization of the Pod certificate request + K8s JWT workload CSRs K8s node adapter ● The node agent forwards workload Node Agent K8s JWT pod pod
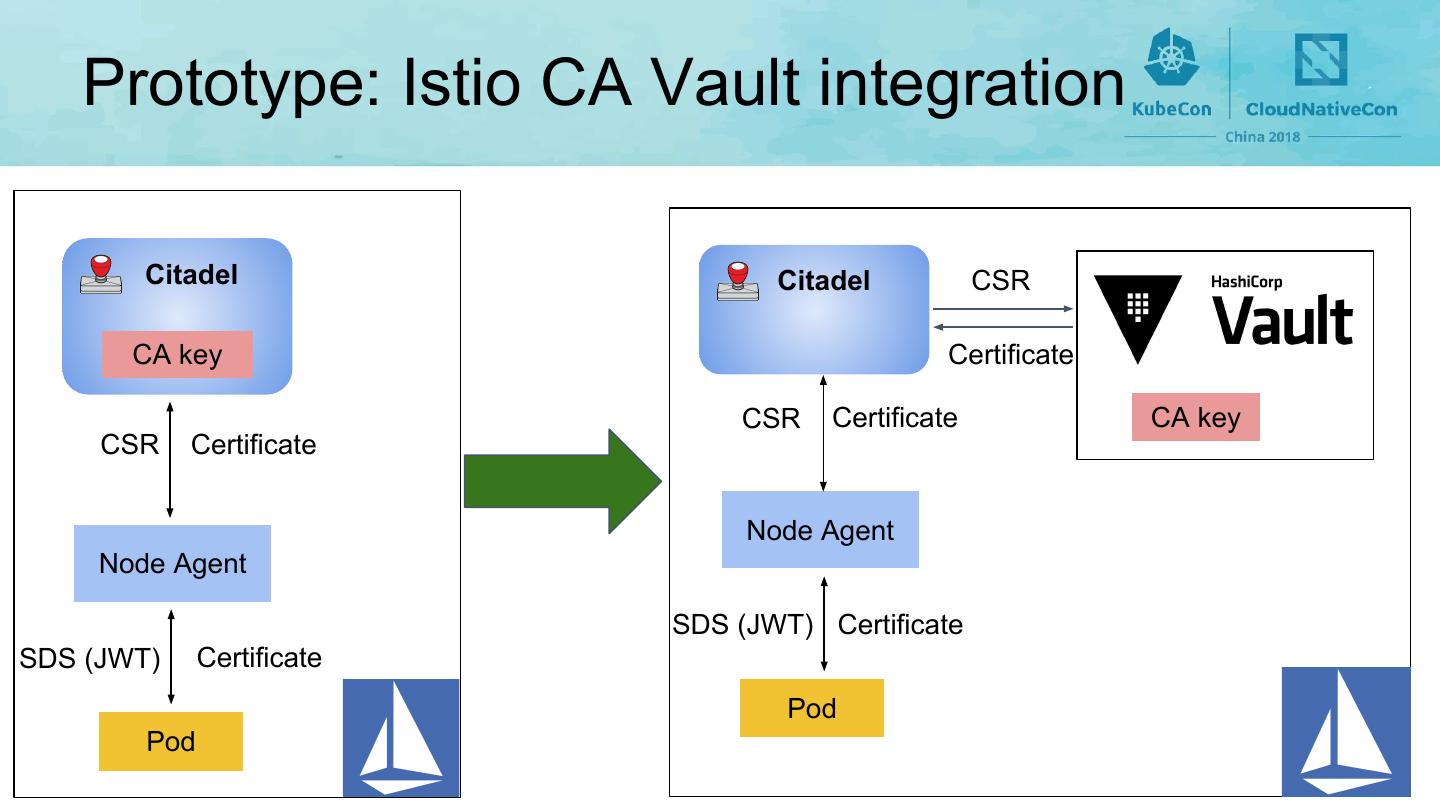
18 . Prototype: Istio CA Vault integration Citadel Citadel CSR CA key Certificate CSR Certificate CA key CSR Certificate Node Agent Node Agent SDS (JWT) Certificate SDS (JWT) Certificate Pod Pod
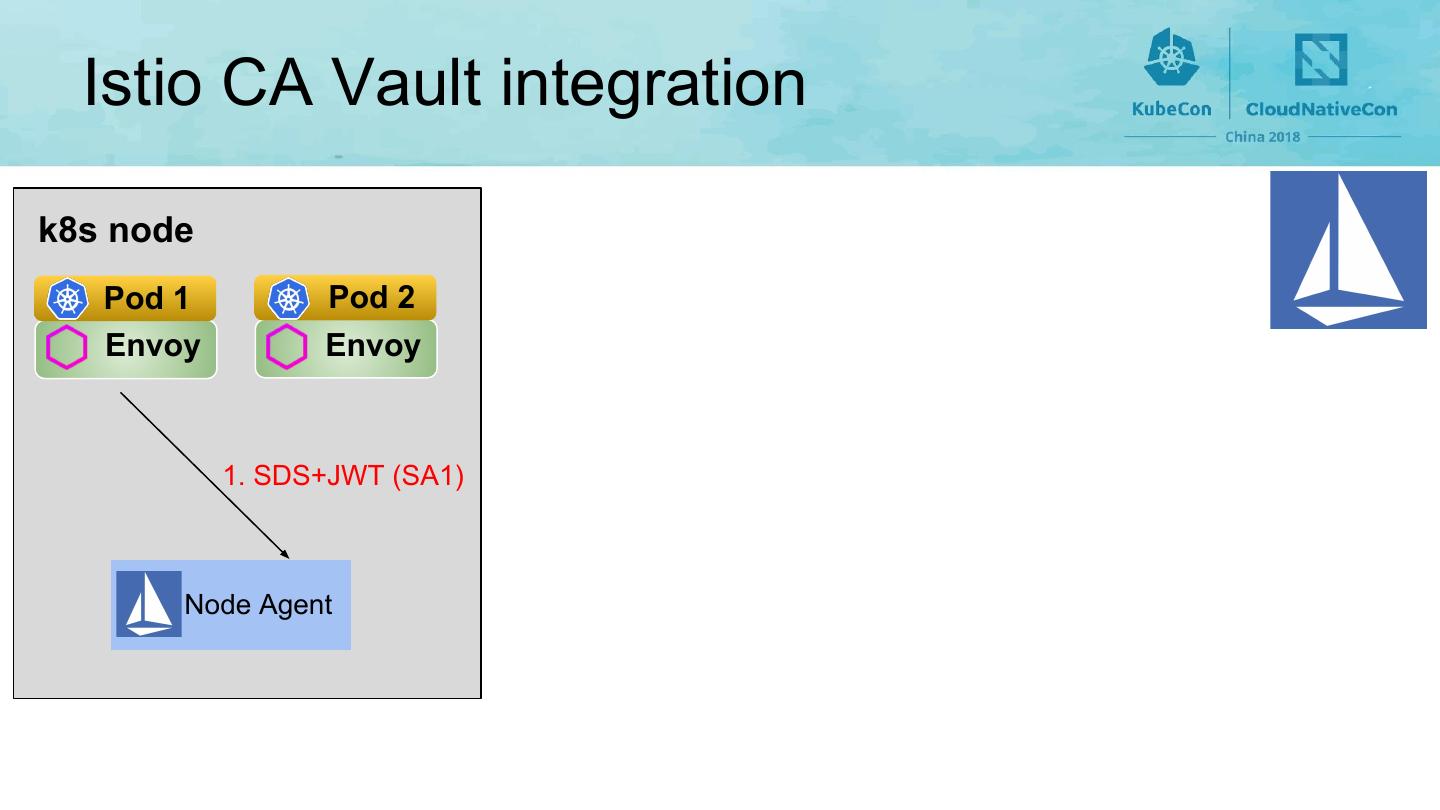
19 . Istio CA Vault integration k8s node Pod 1 Pod 2 Envoy Envoy 1. SDS+JWT (SA1) Node Agent
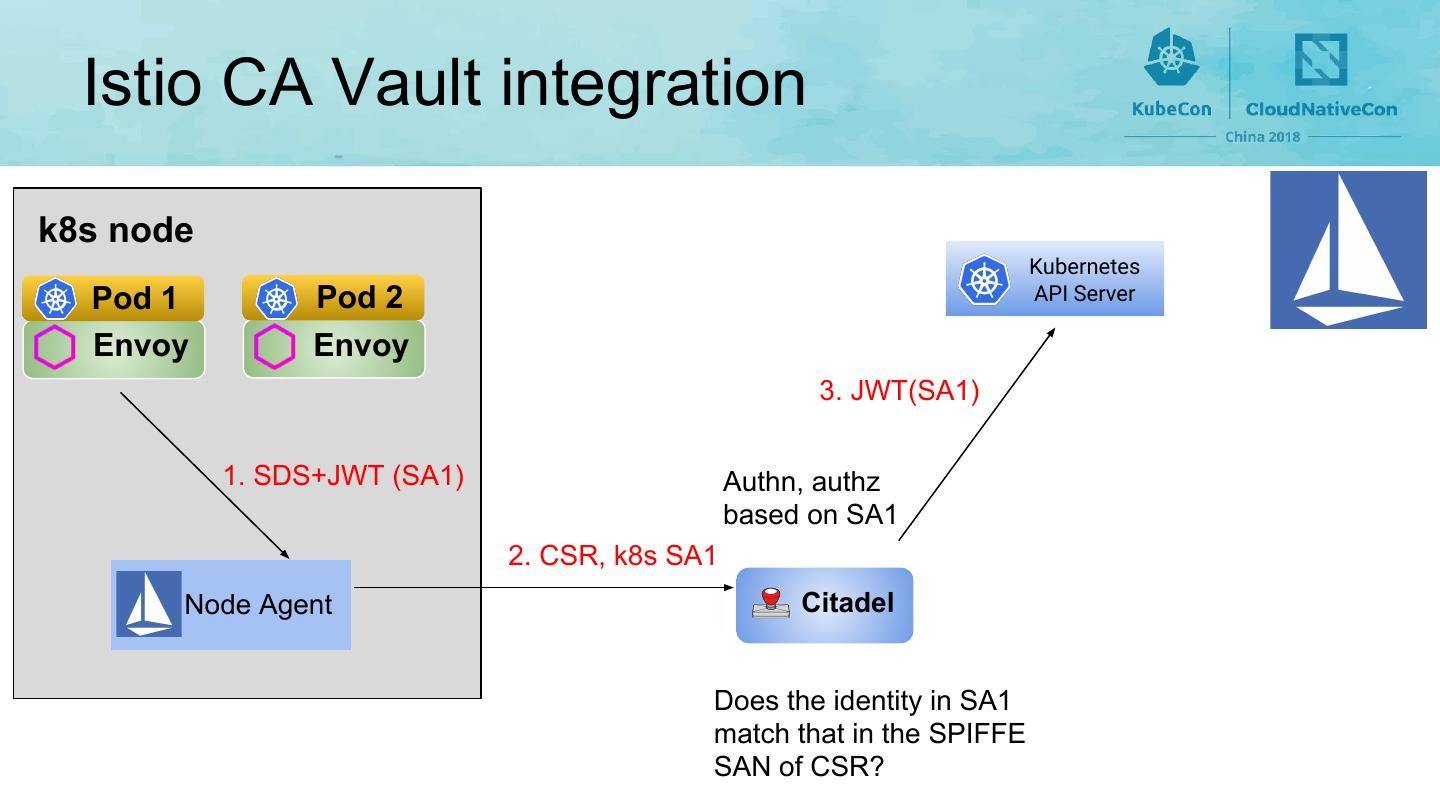
20 . Istio CA Vault integration k8s node Kubernetes Pod 1 Pod 2 API Server Envoy Envoy 3. JWT(SA1) 1. SDS+JWT (SA1) Authn, authz based on SA1 2. CSR, k8s SA1 Node Agent Citadel Does the identity in SA1 match that in the SPIFFE SAN of CSR?
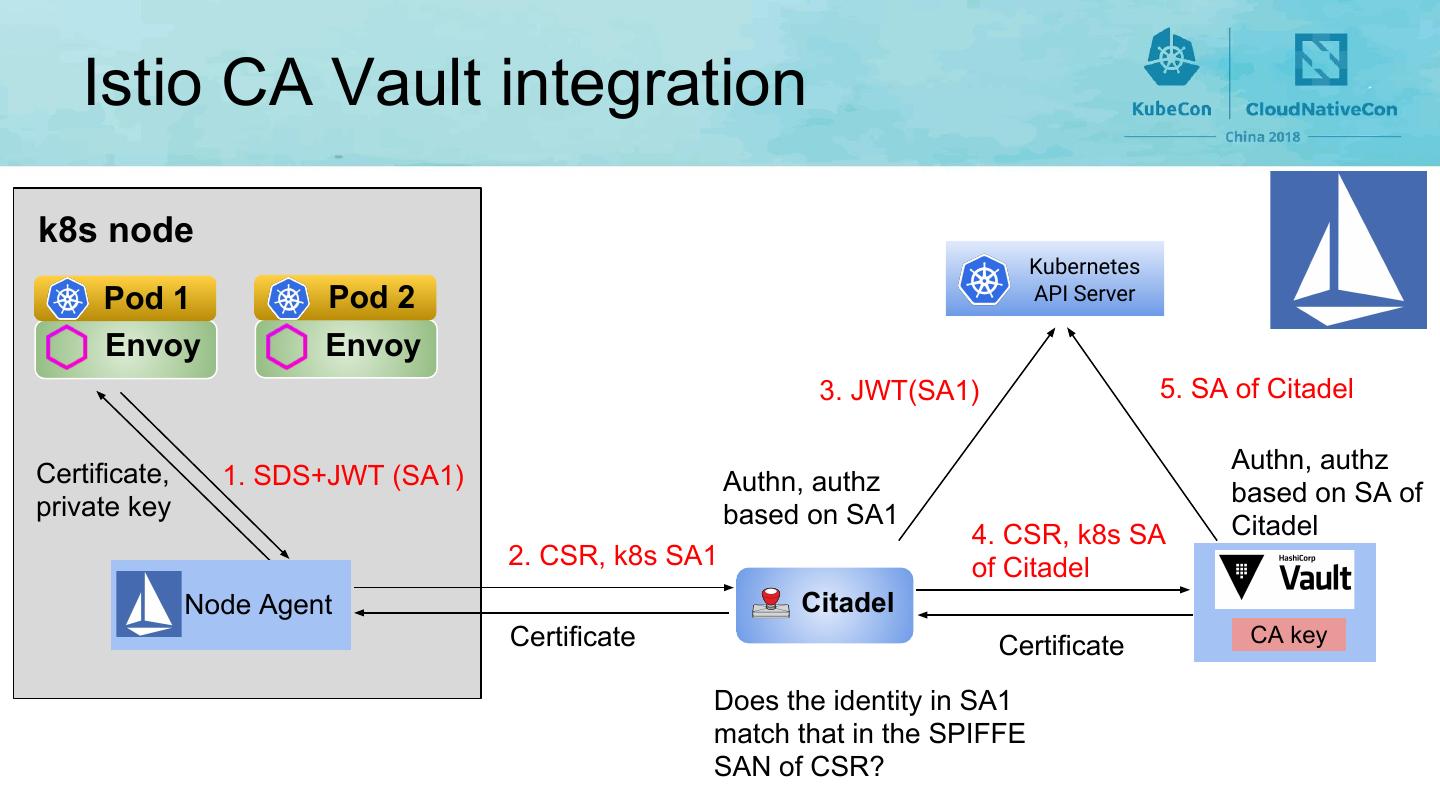
21 . Istio CA Vault integration k8s node Kubernetes Pod 1 Pod 2 API Server Envoy Envoy 3. JWT(SA1) 5. SA of Citadel Certificate, Authn, authz 1. SDS+JWT (SA1) Authn, authz private key based on SA of based on SA1 Citadel 4. CSR, k8s SA 2. CSR, k8s SA1 of Citadel Node Agent Citadel Certificate Certificate CA key Does the identity in SA1 match that in the SPIFFE SAN of CSR?
22 .Demo Demo of Istio CA Vault integration
23 .Istio survey We would love to hear your feedbacks on Istio. Please fill the survey on the survey website; we have rewards waiting for you :)
24 .