- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
实施授权——Torin Sandall,Styra
展开查看详情
1 .Implementing Authorization @sometorin
2 . Torin Sandall ● Engineer @ Styra ● Co-founder @ Open Policy Agent @sometorin
3 ."Undifferentiated Heavy Lifting" - Jeff Bezos (Amazon CEO, 2006) @sometorin
4 .Authorization is heavy lifting. @sometorin
5 ....but every app needs authorization. @sometorin
6 .Rethink how you implement authorization. @sometorin
7 .Ship secure projects faster. @sometorin
8 .Authentication != Authorization Verify identity Verify permission @sometorin
9 .Authentication != Authorization Am I talking to Bob? Is Bob allowed to talk to me? @sometorin
10 .Authentication standards SAML OpenID Connect SPIFFE <saml:Assertion> <saml:Subject> { <saml:NameID abcdef> "iss": https://example.com </saml:NameID> "sub": bob <saml:SubjectConfirmation "aud": retail Method="urn:...:bearer"> "nbf": 123456789, spiffe://acmecorp/a/b/c <saml:SubjectConfirmation "exp": 123456789, Data NotOnOrAfter=../> "amr": ["password", "otp"] </saml:SubjectConfirmation> } <saml:Conditions>... Enterprise Consumer Infrastructure @sometorin
11 .Authentication verifies identity & produces attributes. Human { iss: acmecorp sub: bob aud: retail nbf: 123456789 credentials Authentication Verified Identity exp: 123456789 amr: [ password otp ] } Machine @sometorin
12 . ### 2.2. Path The path component of a SPIFFE ID allows for the unique identification of a given workload. The Attribute meaning behind the path is left open ended and the responsibility of the administrator to define. Paths MAY be hierarchical - similar to filesystem semantics are paths. The specific meaning of paths is reserved as an exercise to the implementer and are outside the SVID specification. However some examples and conventions are expressed below. beyond the 2. ID Token [...] scope of the The definition of particular values to be used in the amr Claim is beyond the scope of this specification. Parties using this claim will need to agree upon the meanings of specification. the values used, which may be context-specific. [...] ID Tokens MAY contain other Claims. @sometorin
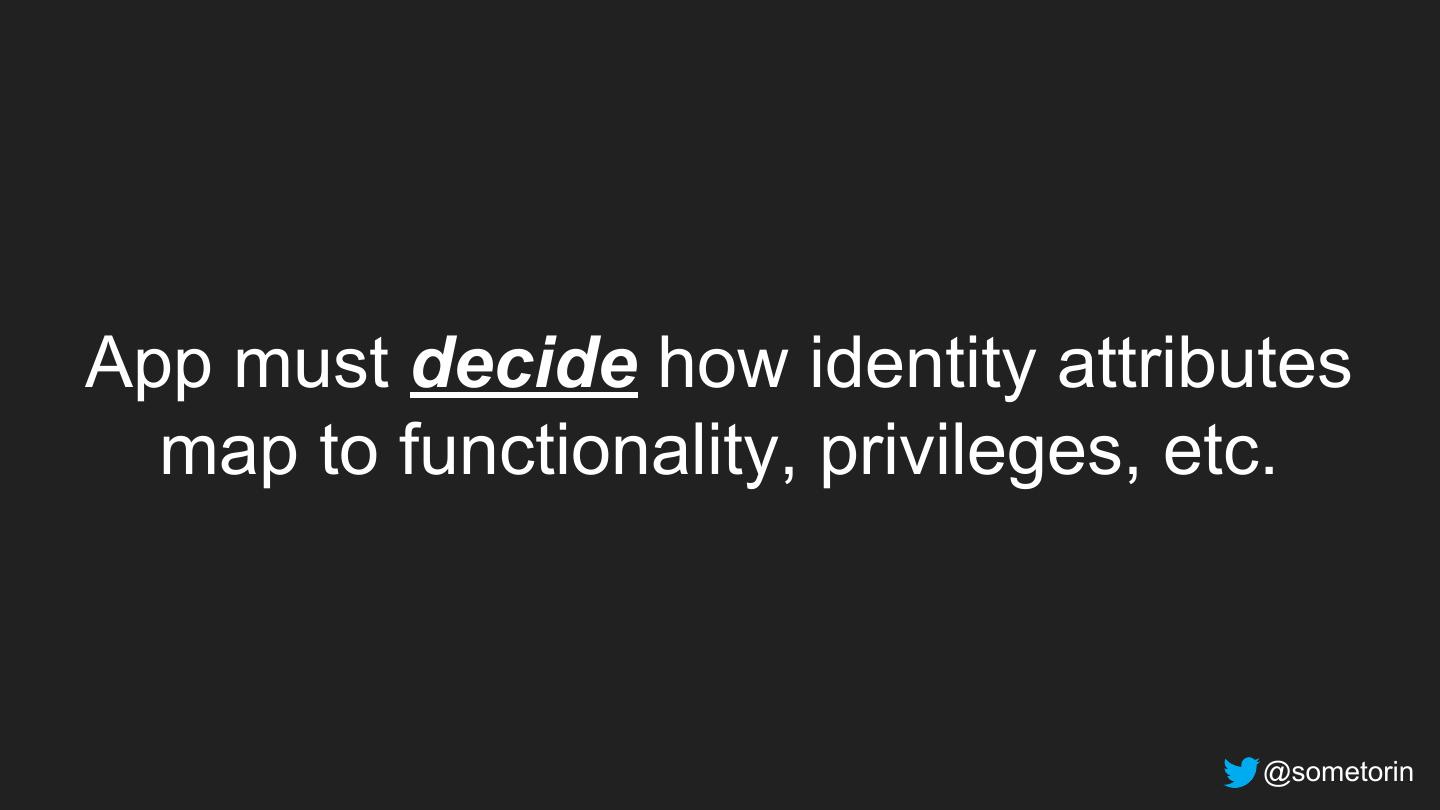
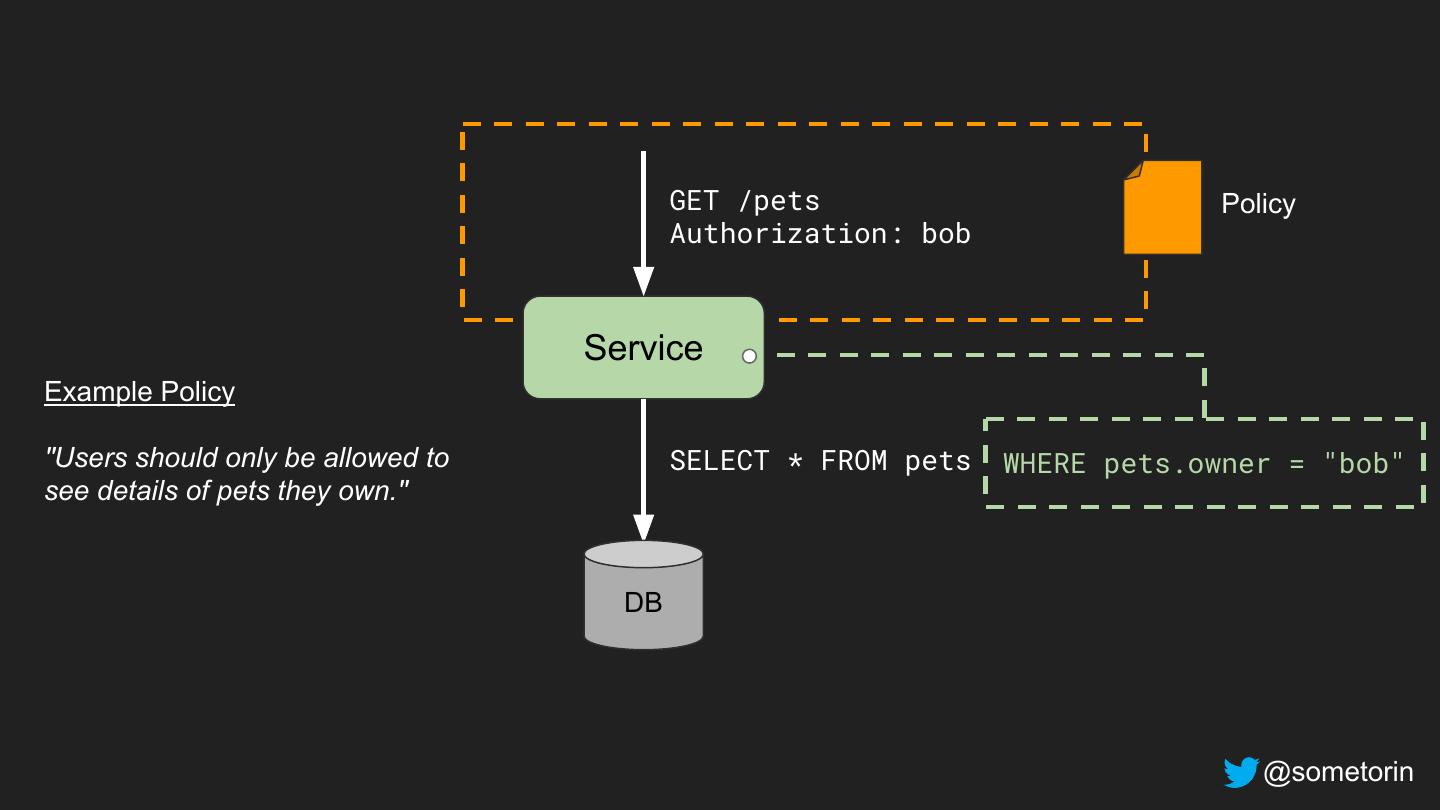
13 .App must decide how identity attributes map to functionality, privileges, etc. @sometorin
14 . RFC 6749 The OAuth 2.0 Authorization Framework Abstract What about OAuth? The OAuth 2.0 authorization framework enables a third-party application to obtain limited access to an HTTP service, either on behalf of a resource owner by orchestrating an approval interaction between the resource owner and the HTTP service, or by allowing the third-party application to obtain access on its own behalf. @sometorin
15 .OAuth 2.0 enables delegation. "Power of Attorney" for web and mobile applications. @sometorin
16 . RFC 6749 Section 7 The client accesses protected resources by presenting Application of access tokens the access token to the resource server. The resource server MUST validate the access token and ensure that it has not expired and that its scope covers the is beyond the scope of the requested resource. The methods used by the resource server to validate the access token (as well as any specification. error responses) are beyond the scope of this specification but generally involve an interaction or coordination between the resource server and the authorization server. @sometorin
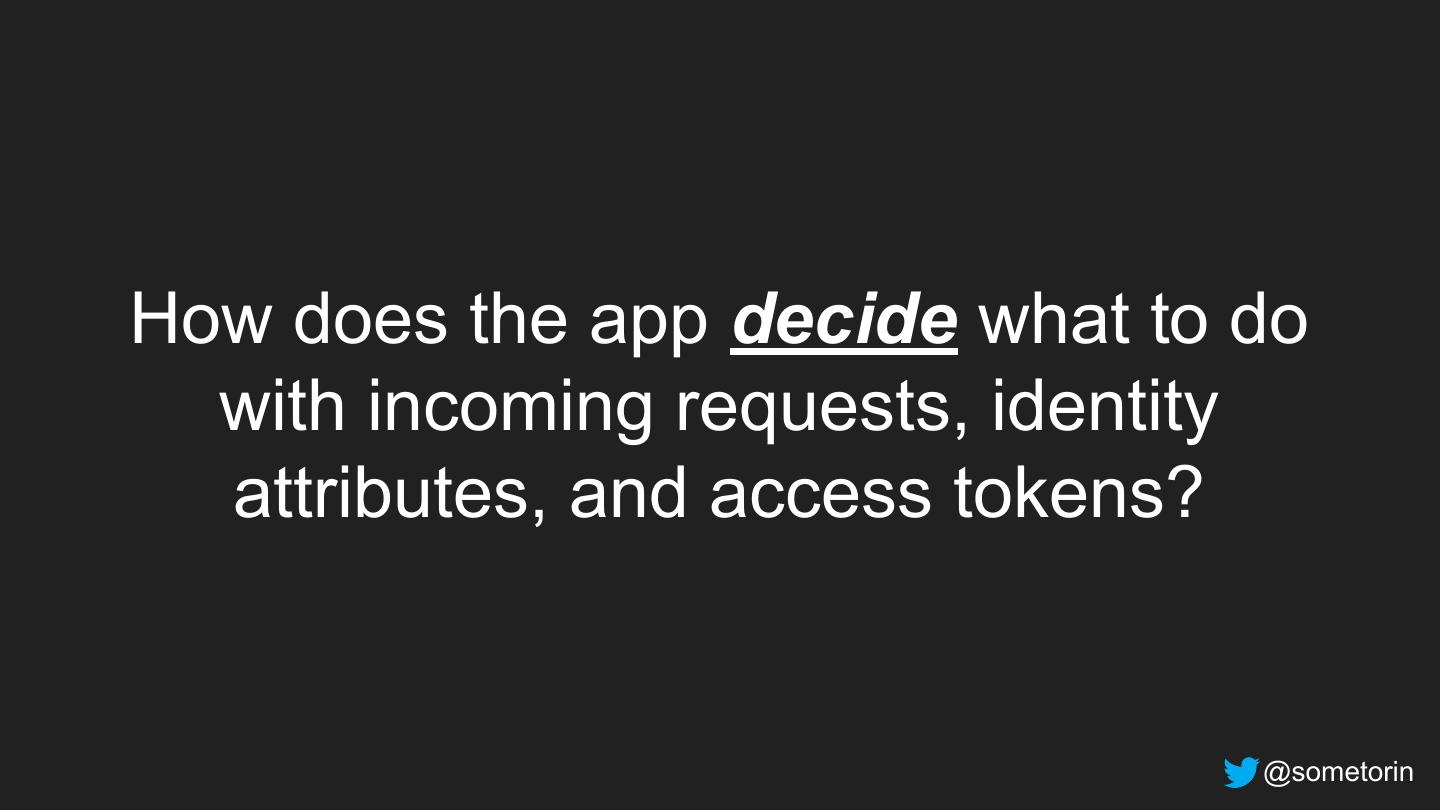
17 .How does the app decide what to do with incoming requests, identity attributes, and access tokens? @sometorin
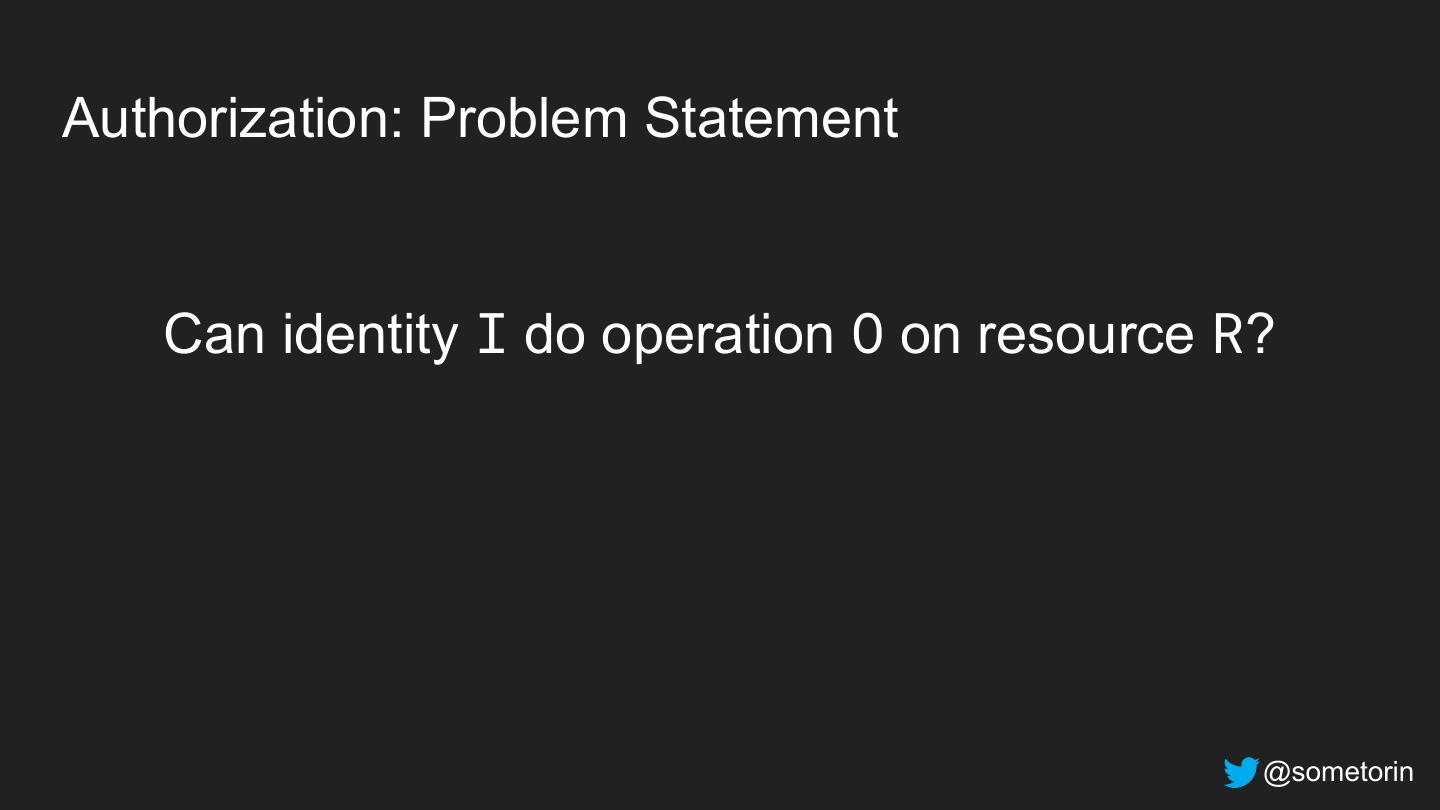
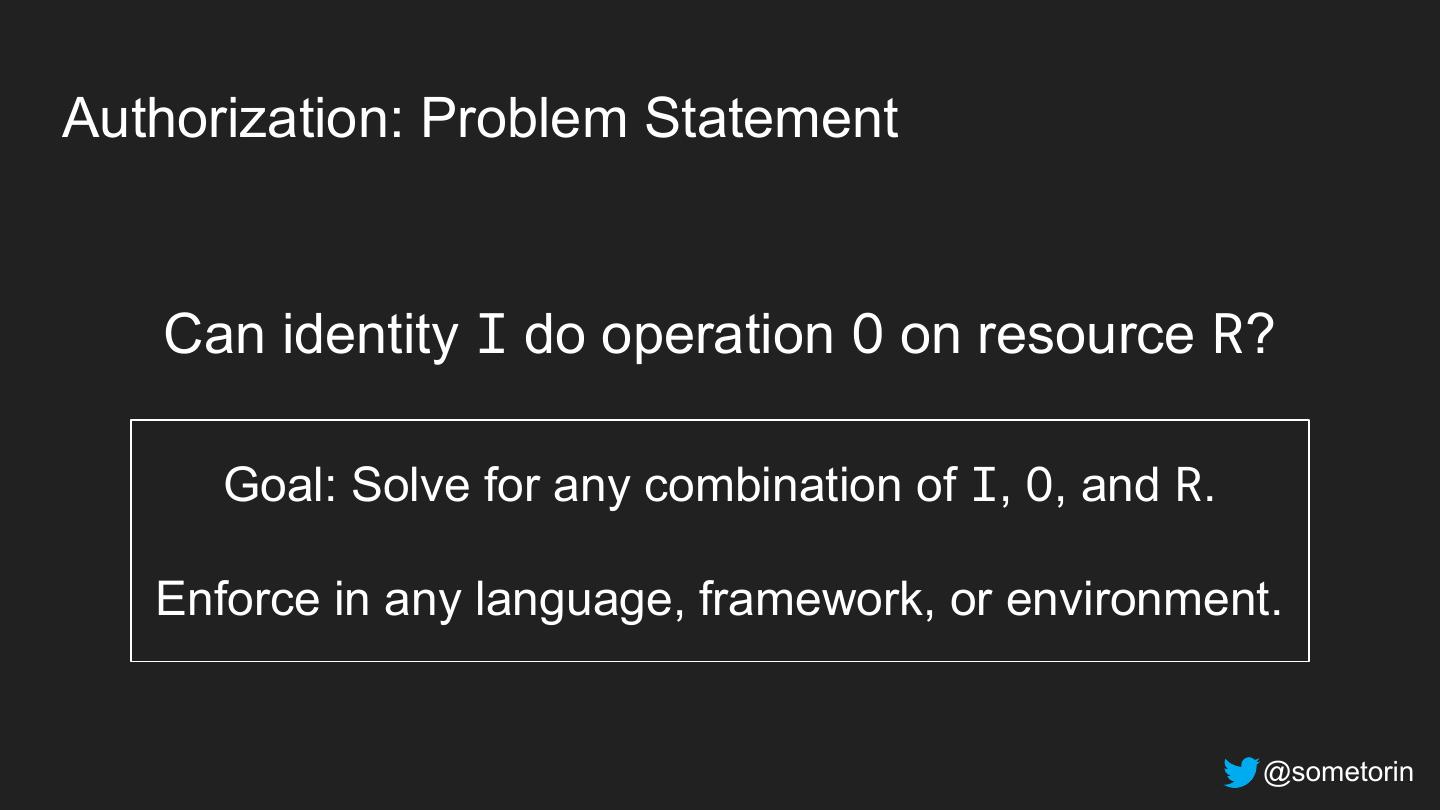
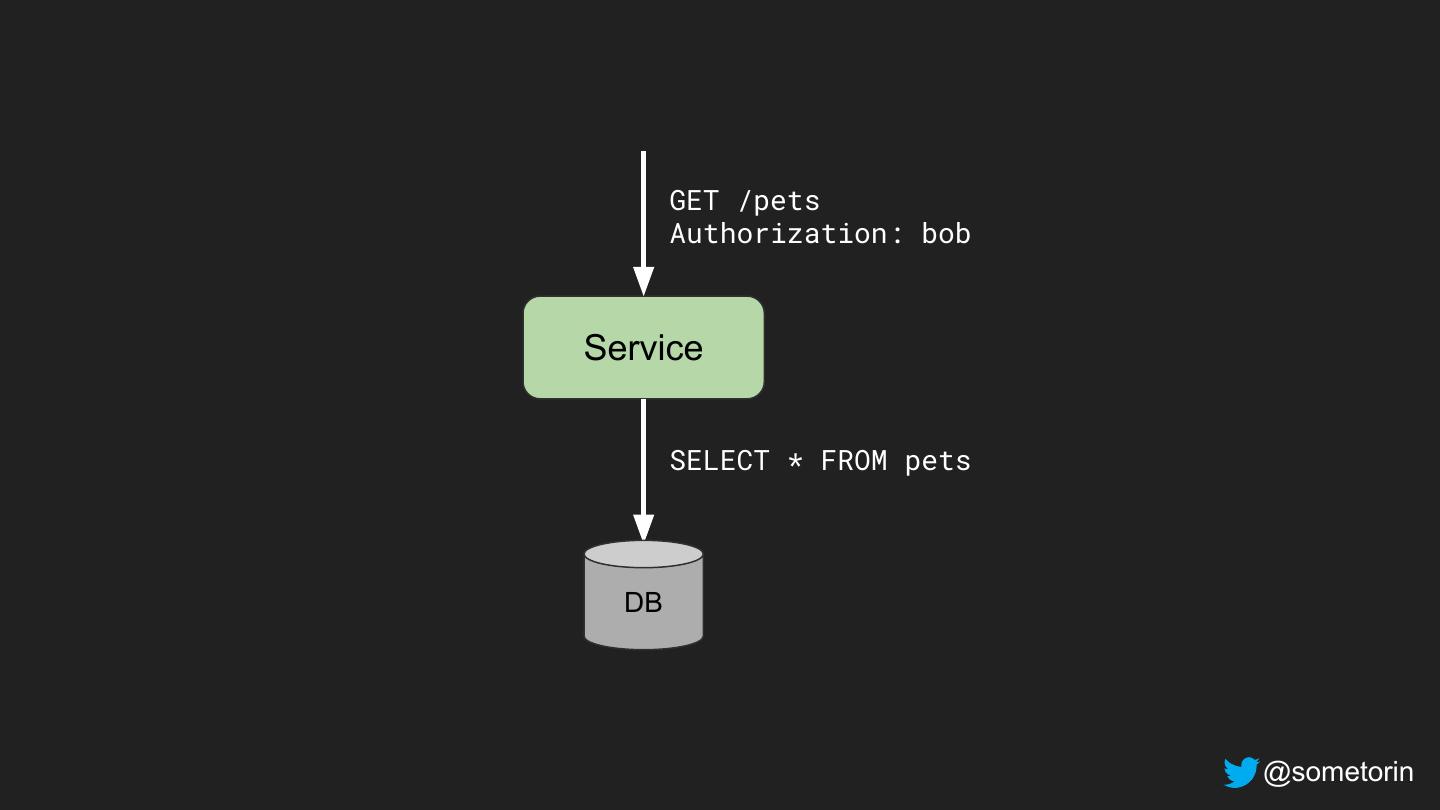
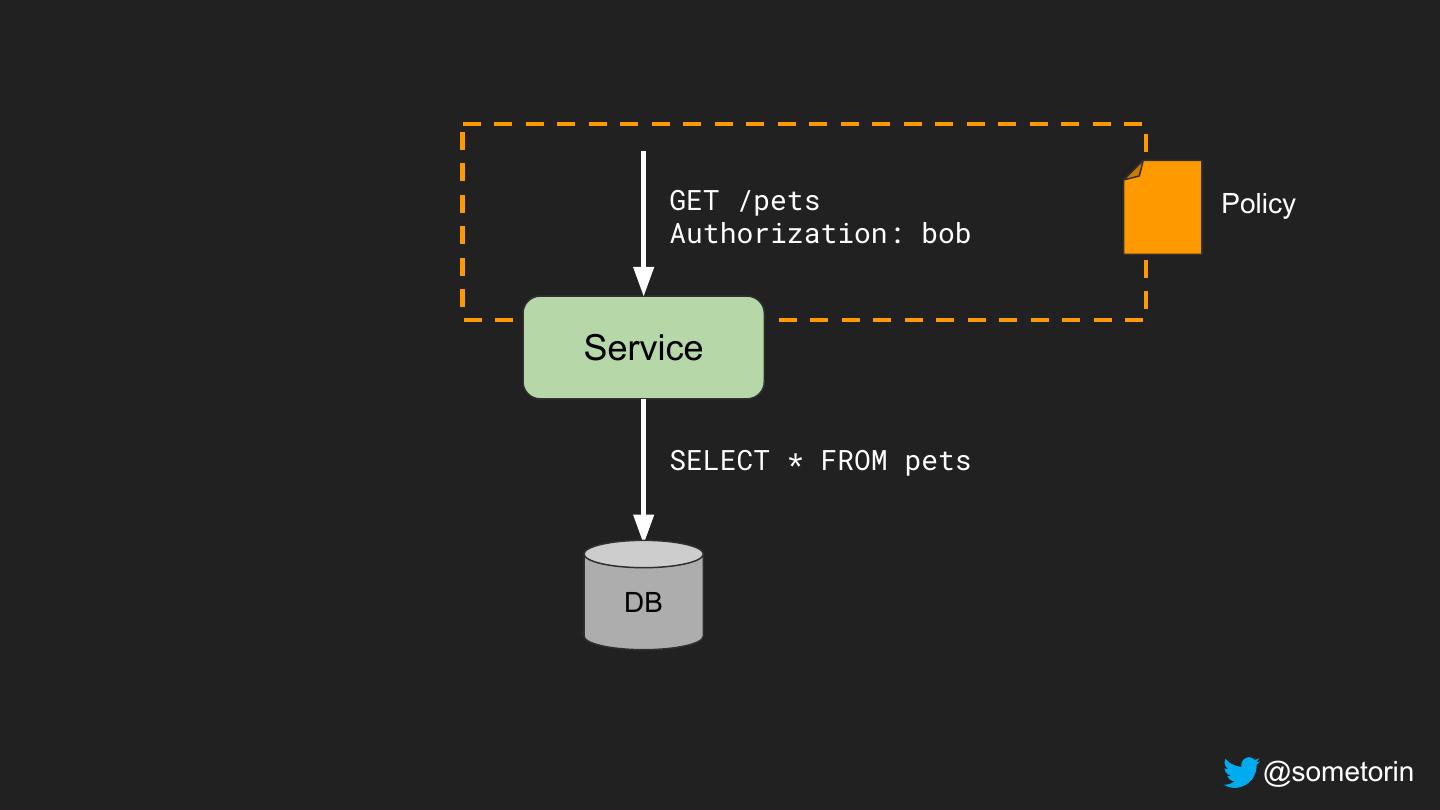
18 .Authorization: Problem Statement Can identity I do operation O on resource R? @sometorin
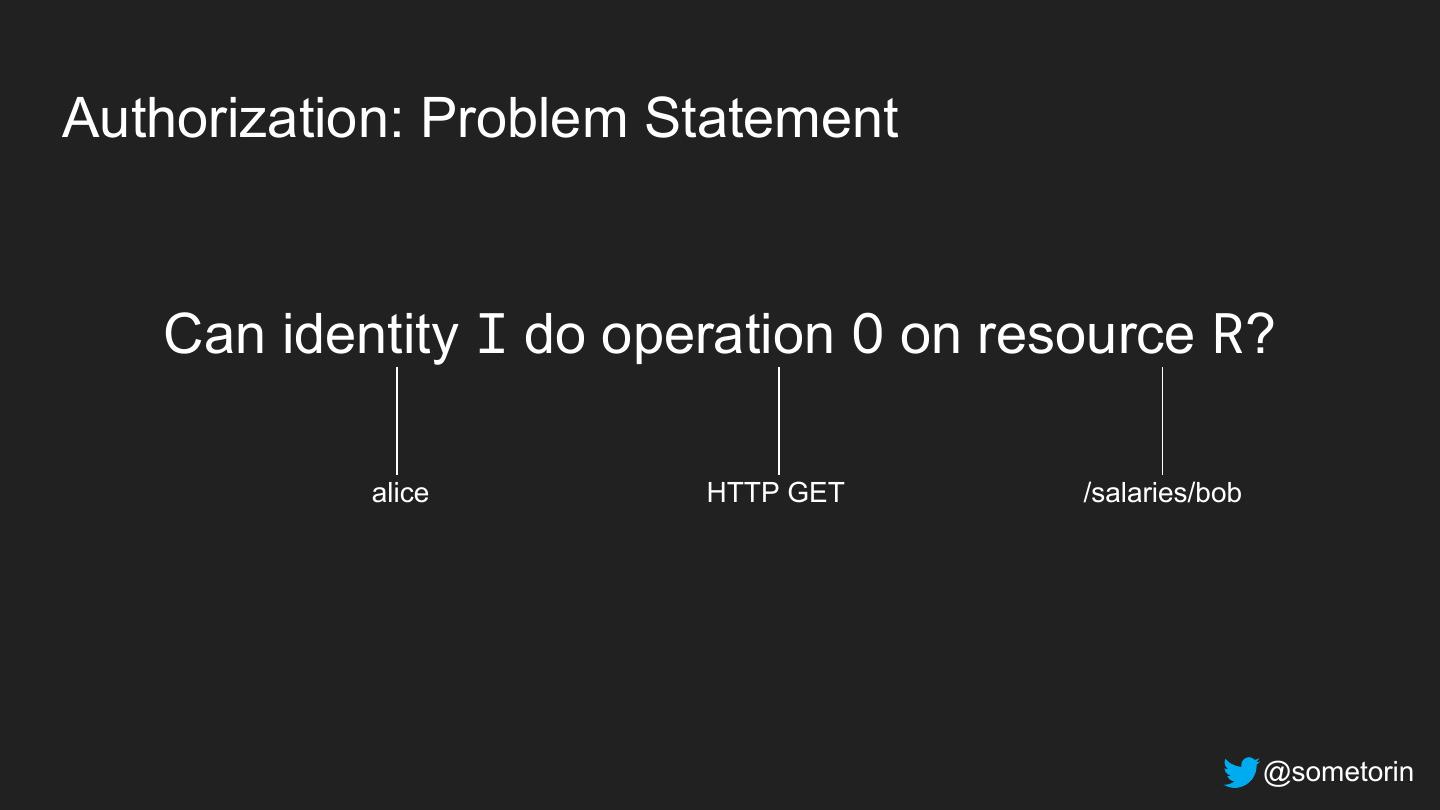
19 .Authorization: Problem Statement Can identity I do operation O on resource R? alice HTTP GET /salaries/bob @sometorin
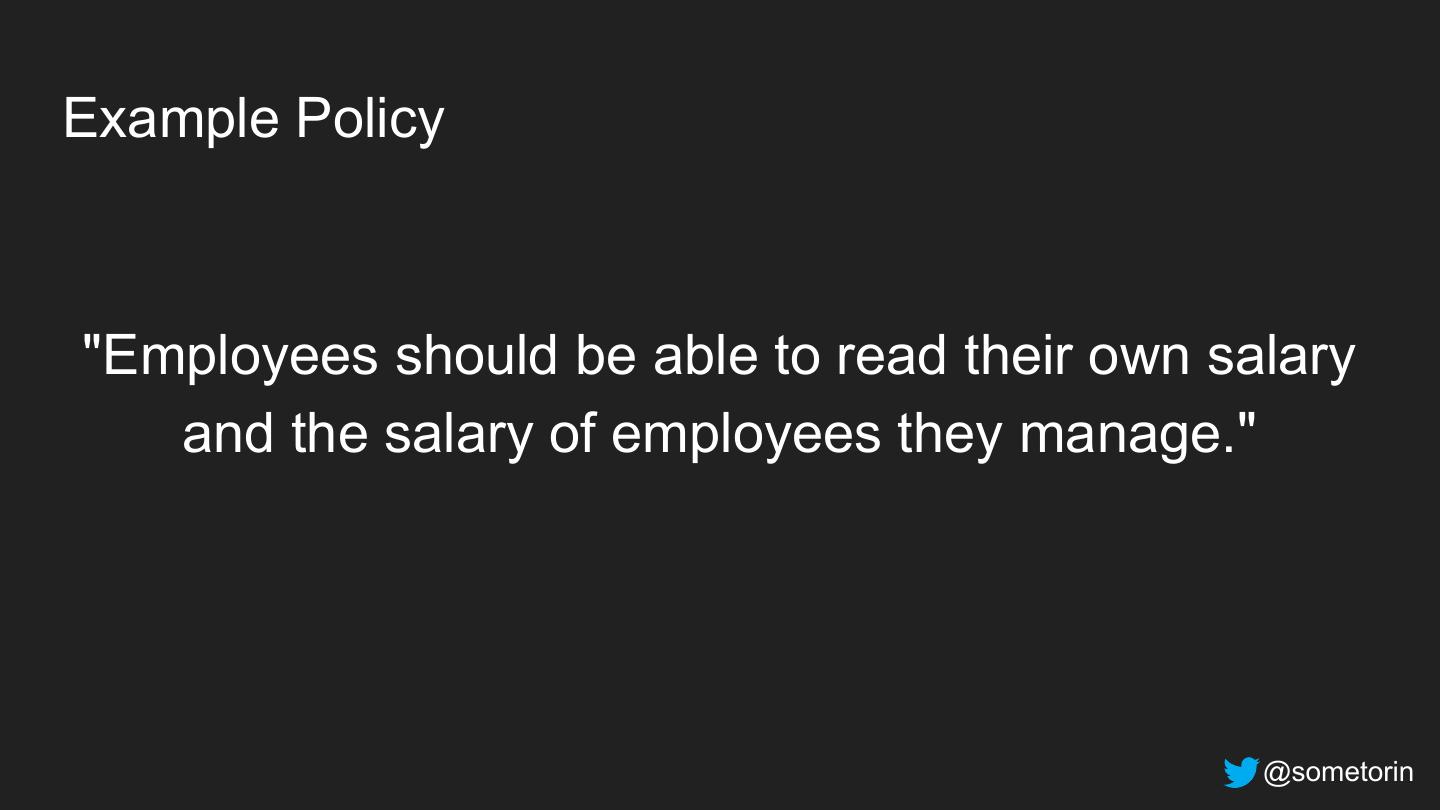
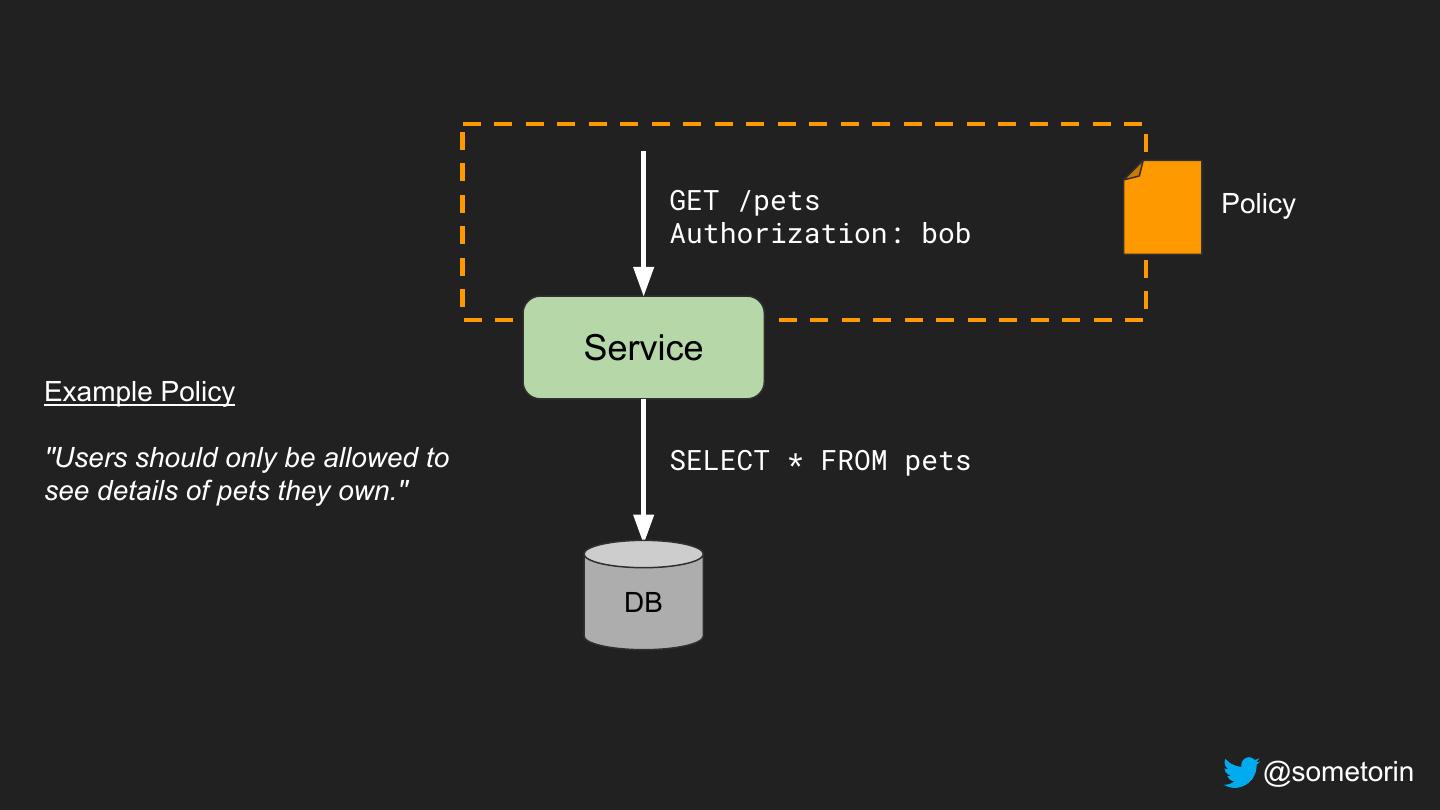
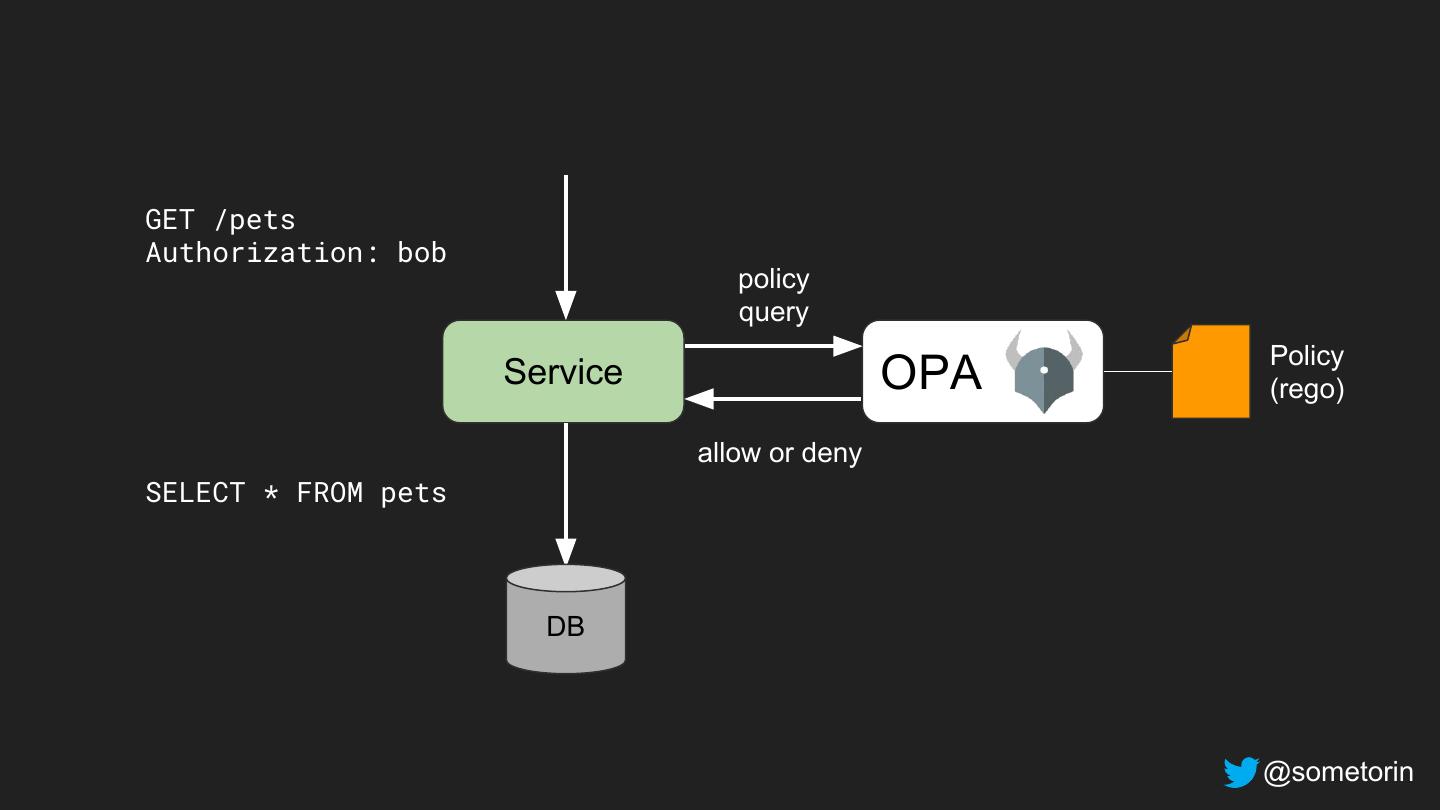
20 .Example Policy "Employees should be able to read their own salary and the salary of employees they manage." @sometorin
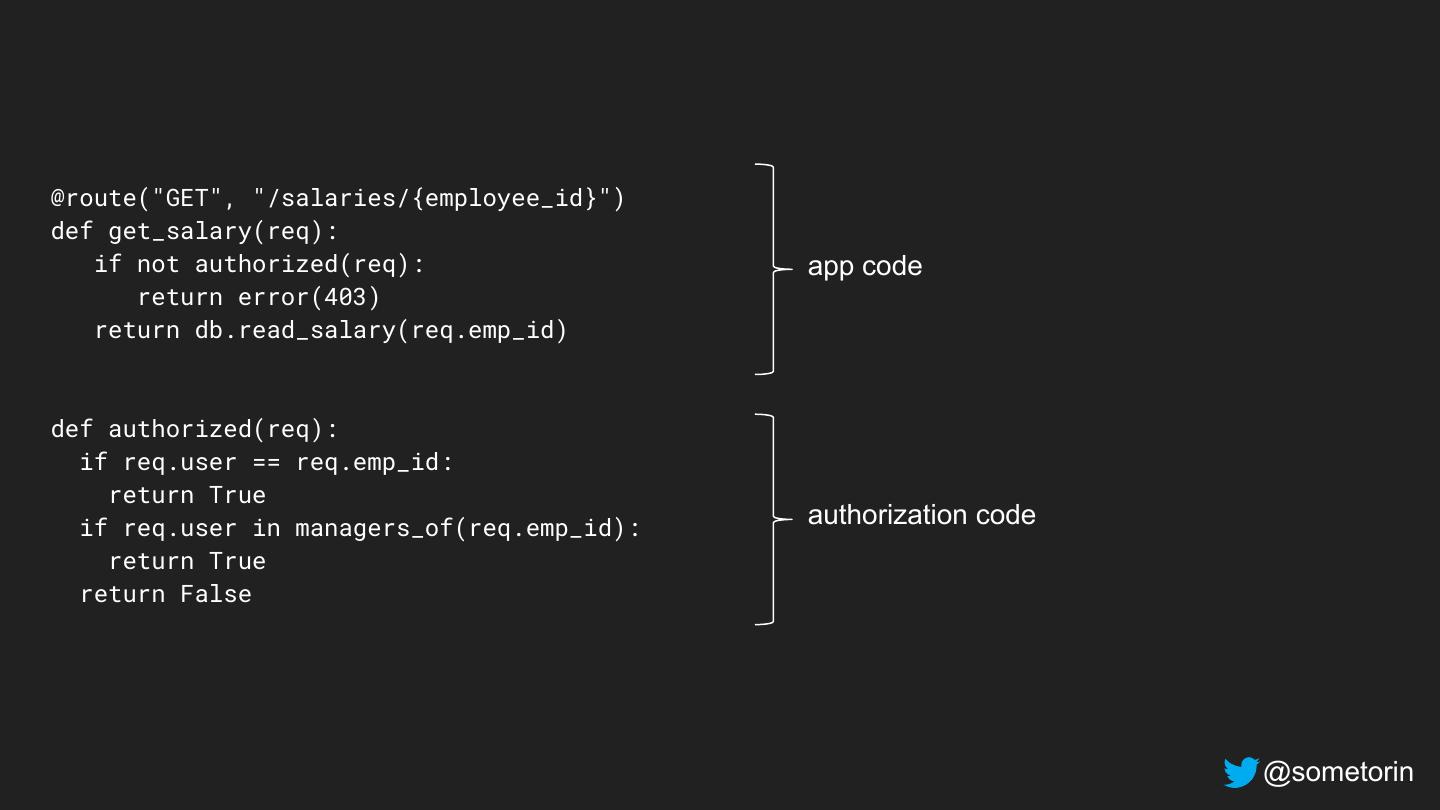
21 .@route("GET", "/salaries/{employee_id}") def get_salary(req): if not authorized(req): app code return error(403) return db.read_salary(req.emp_id) def authorized(req): if req.user == req.emp_id: return True if req.user in managers_of(req.emp_id): authorization code return True return False @sometorin
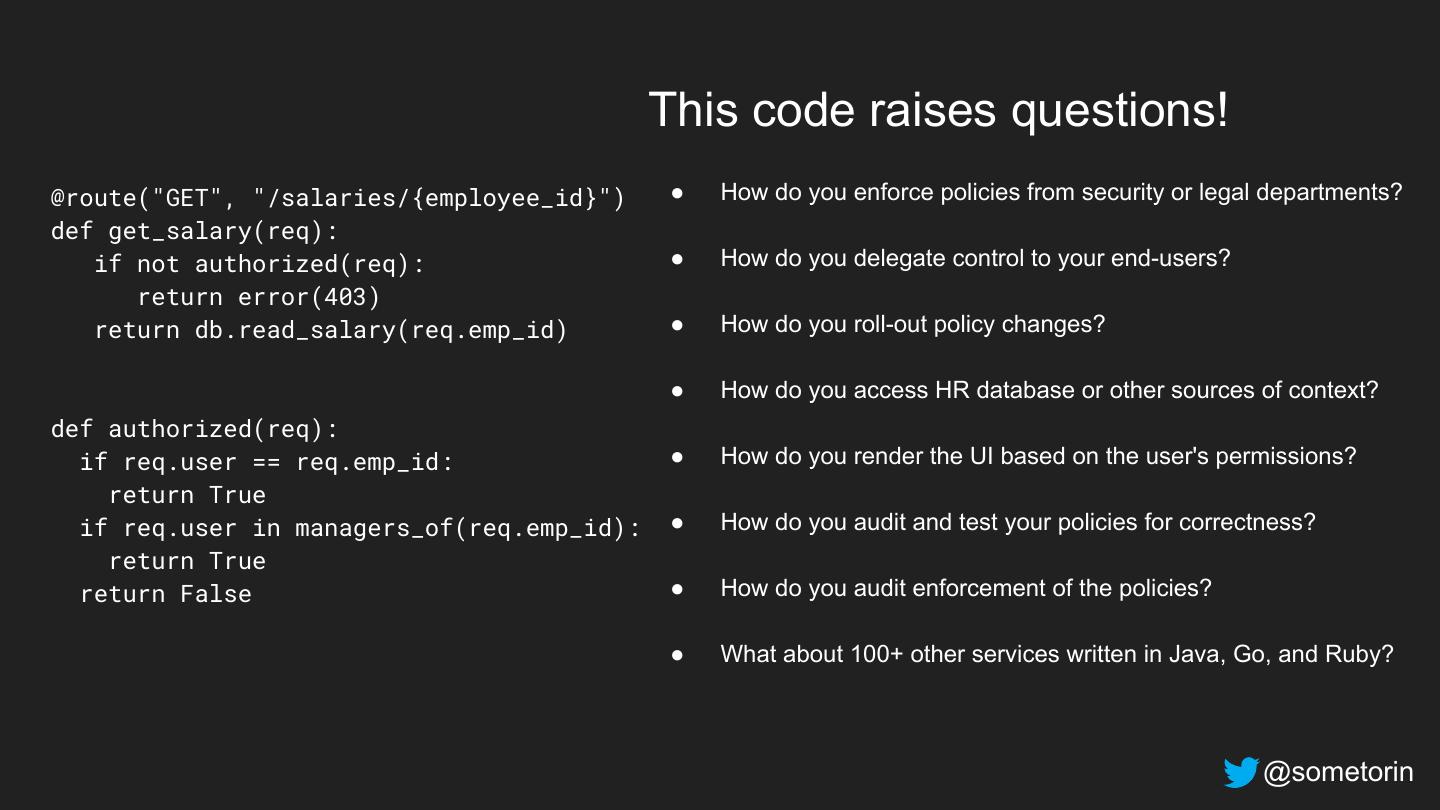
22 . This code raises questions! @route("GET", "/salaries/{employee_id}") ● How do you enforce policies from security or legal departments? def get_salary(req): if not authorized(req): ● How do you delegate control to your end-users? return error(403) return db.read_salary(req.emp_id) ● How do you roll-out policy changes? ● How do you access HR database or other sources of context? def authorized(req): if req.user == req.emp_id: ● How do you render the UI based on the user's permissions? return True if req.user in managers_of(req.emp_id): ● How do you audit and test your policies for correctness? return True return False ● How do you audit enforcement of the policies? ● What about 100+ other services written in Java, Go, and Ruby? @sometorin
23 .Authorization: Problem Statement Can identity I do operation O on resource R? Goal: Solve for any combination of I, O, and R. Enforce in any language, framework, or environment. @sometorin
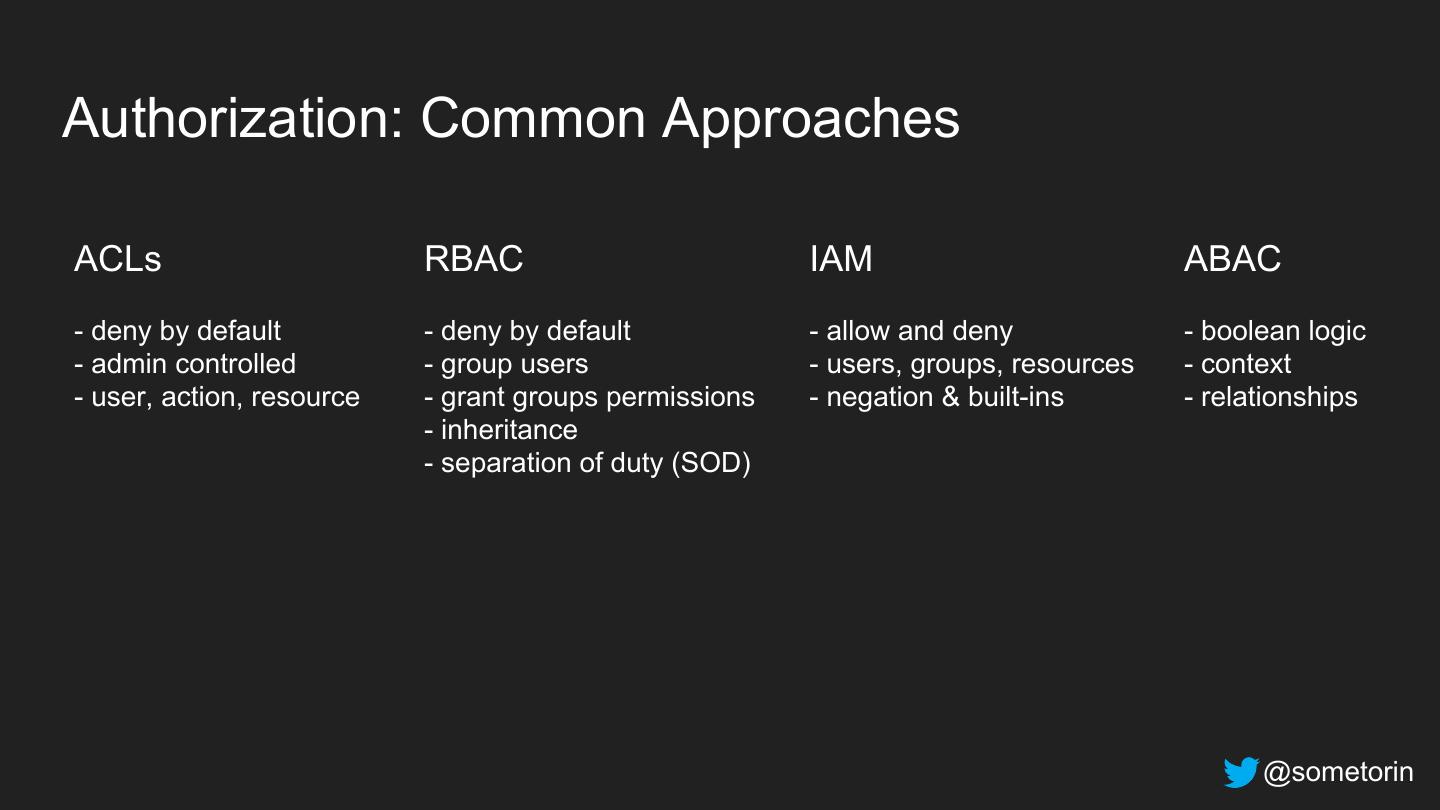
24 .Authorization: Common Approaches ACLs RBAC IAM ABAC - deny by default - deny by default - allow and deny - boolean logic - admin controlled - group users - users, groups, resources - context - user, action, resource - grant groups permissions - negation & built-ins - relationships - inheritance - separation of duty (SOD) @sometorin
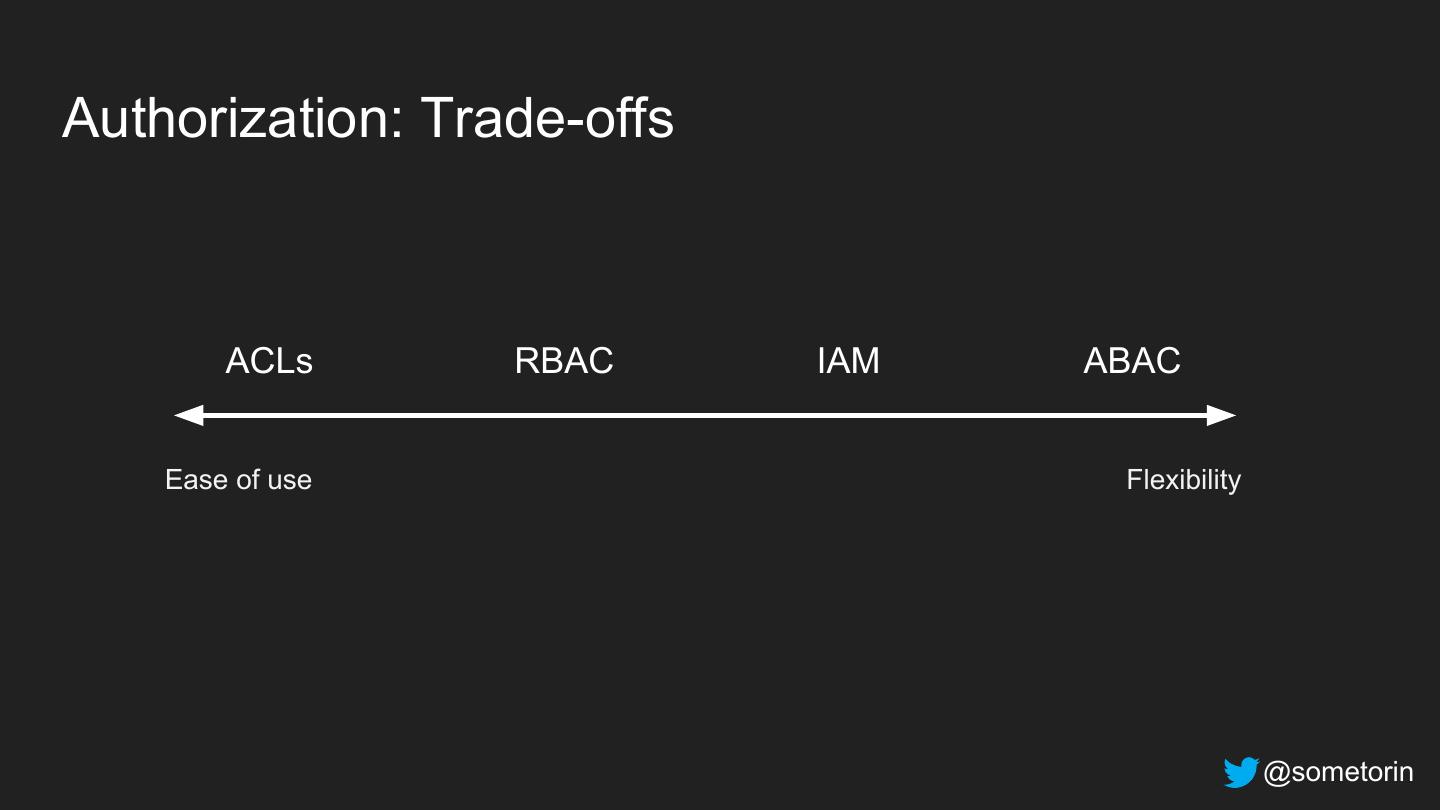
25 .Authorization: Trade-offs ACLs RBAC IAM ABAC Ease of use Flexibility @sometorin
26 . "Allow all HTTP requests "Restrict employees from accessing from 10.1.2.0/24." the service outside of work hours." "QA must sign-off on images "Restrict ELB changes to senior deployed to the production SREs that are on-call." namespace." "Analysts can read client data but PII must be redacted." ACLs, RBAC, and IAM are not enough. "Give developers SSH access to machines listed in JIRA tickets assigned to them." "Prevent developers from running containers with privileged security contexts in the production namespace." "Workloads for euro-bank must be deployed on PCI-certified clusters in the EU." @sometorin
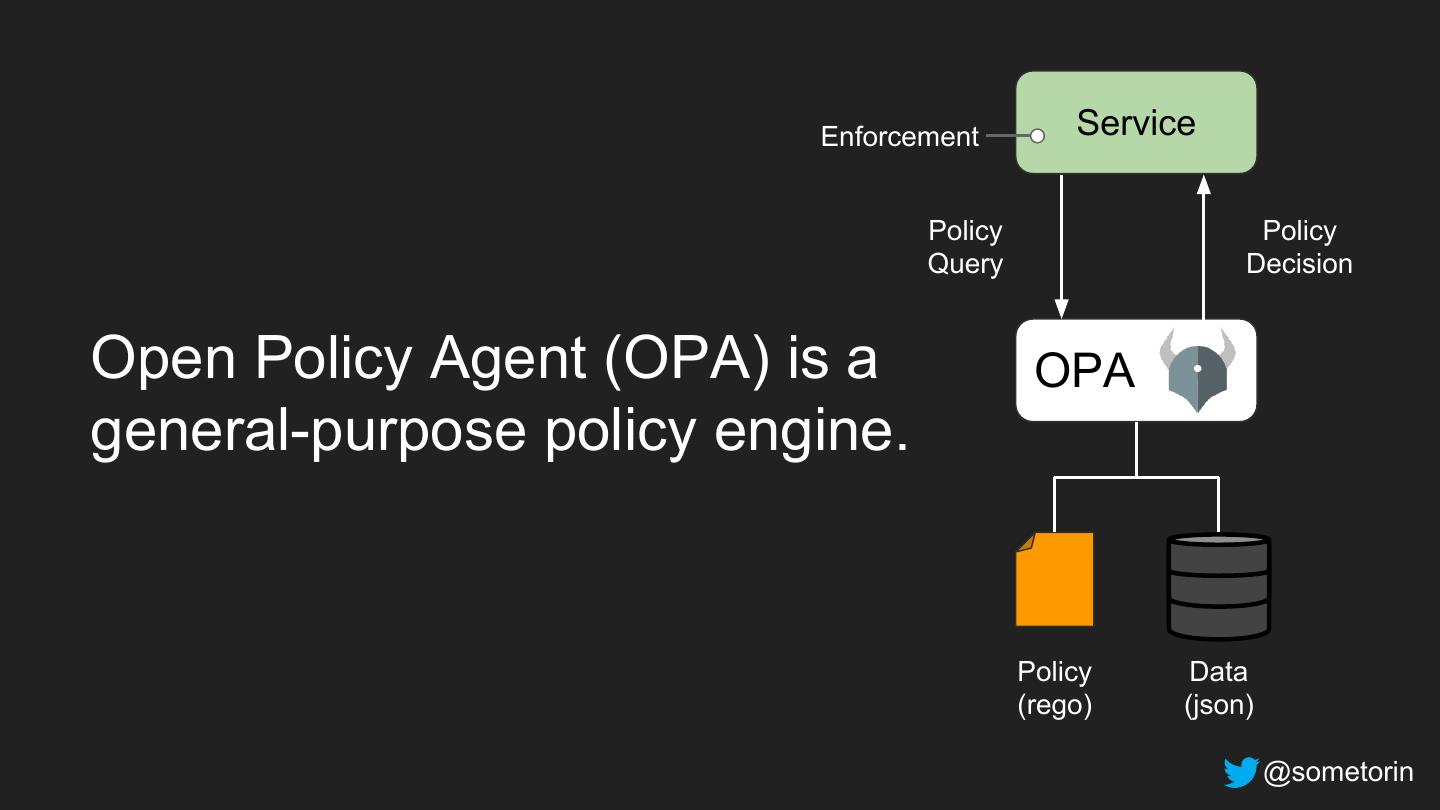
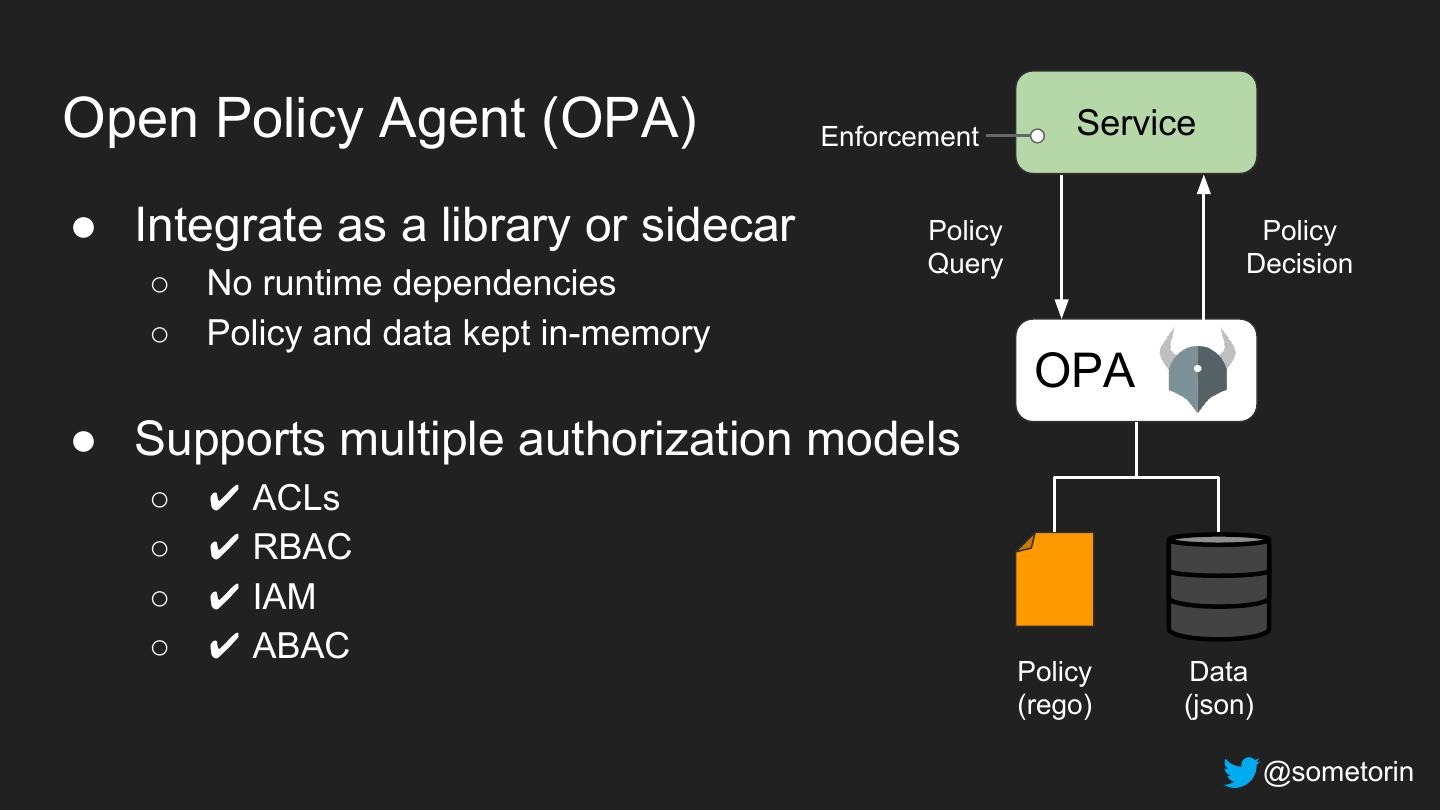
27 . Enforcement Service Policy Policy Query Decision Open Policy Agent (OPA) is a OPA general-purpose policy engine. Policy Data (rego) (json) @sometorin
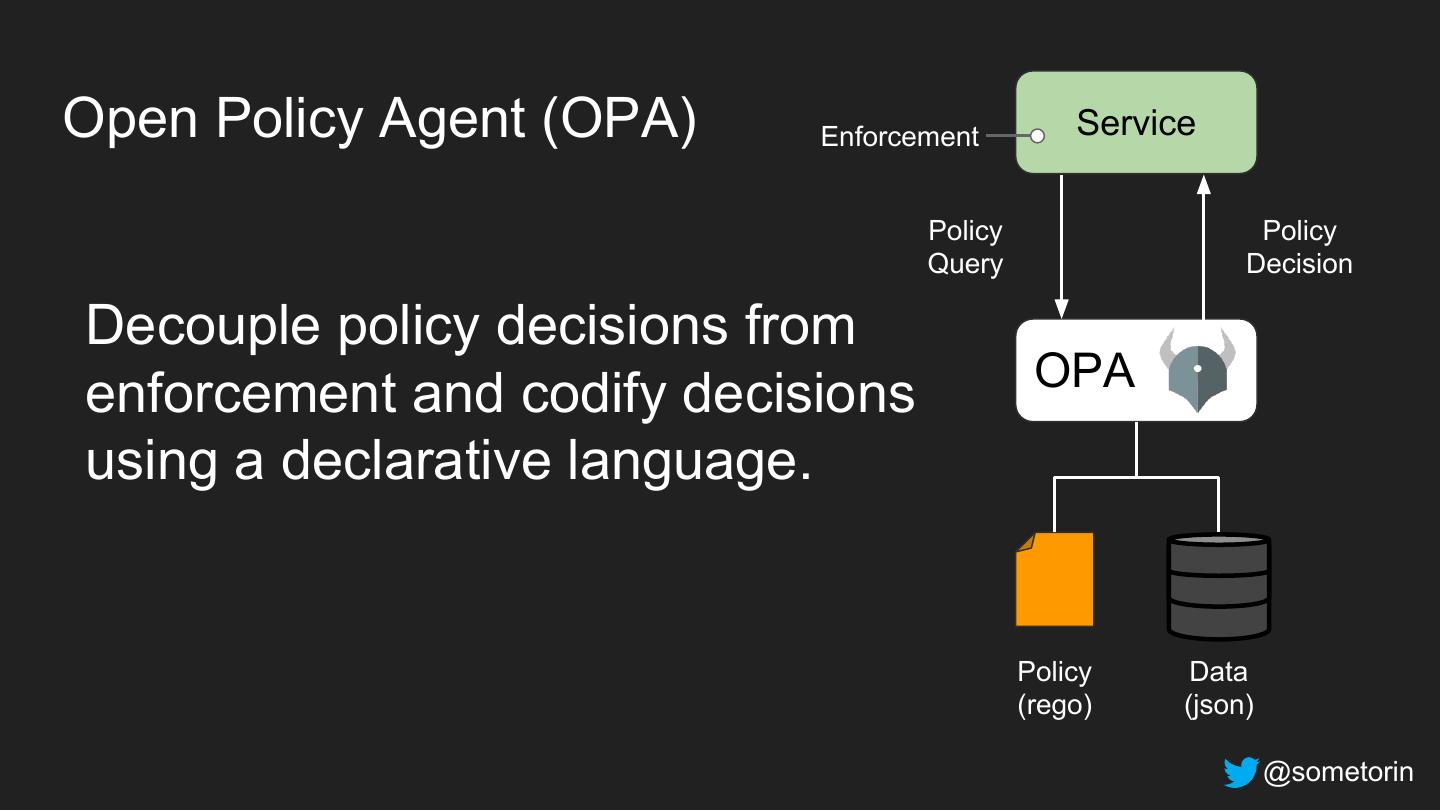
28 .Open Policy Agent (OPA) Enforcement Service Policy Policy Query Decision Decouple policy decisions from OPA enforcement and codify decisions using a declarative language. Policy Data (rego) (json) @sometorin
29 .Open Policy Agent (OPA) Enforcement Service ● Integrate as a library or sidecar Policy Policy Query Decision ○ No runtime dependencies ○ Policy and data kept in-memory OPA ● Supports multiple authorization models ○ ✔ ACLs ○ ✔ RBAC ○ ✔ IAM ○ ✔ ABAC Policy Data (rego) (json) @sometorin