- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
什么是操作系统
展开查看详情
1 .CS 6410: Advanced Systems Prof. Hakim Weatherspoon Principled Computer System Design Fall 2018
2 .Systems Research The study of tradeoffs Functionality vs performance E.g. where to place error checking Are there principles or rules of thumb that can help with large systems design?
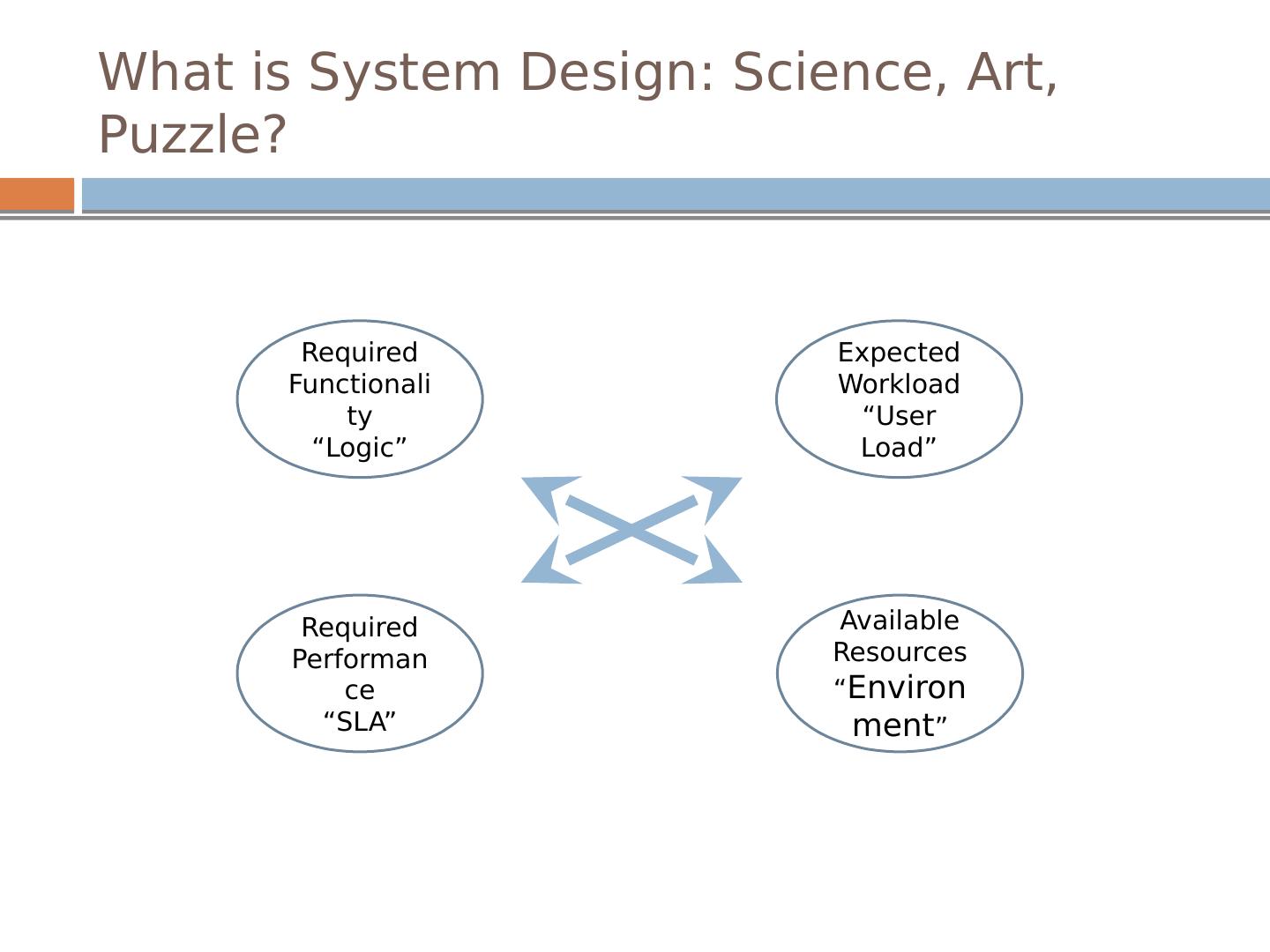
3 .What is System Design: Science, Art, Puzzle? Required Functionality “Logic” Expected Workload “User Load” Required Performance “SLA” Available Resources “ Environment ”
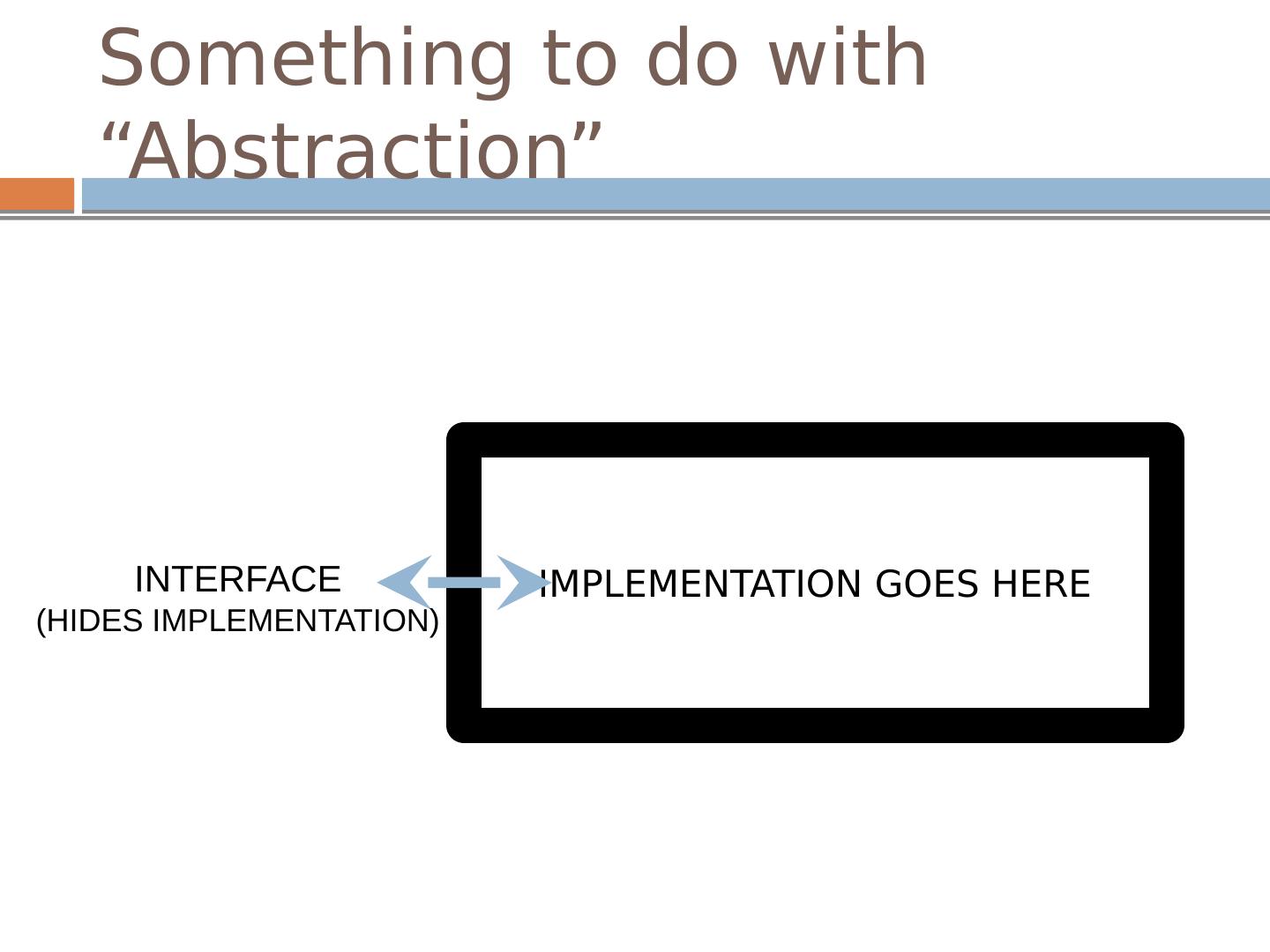
4 .Something to do with “Abstraction” IMPLEMENTATION GOES HERE INTERFACE (HIDES IMPLEMENTATION)
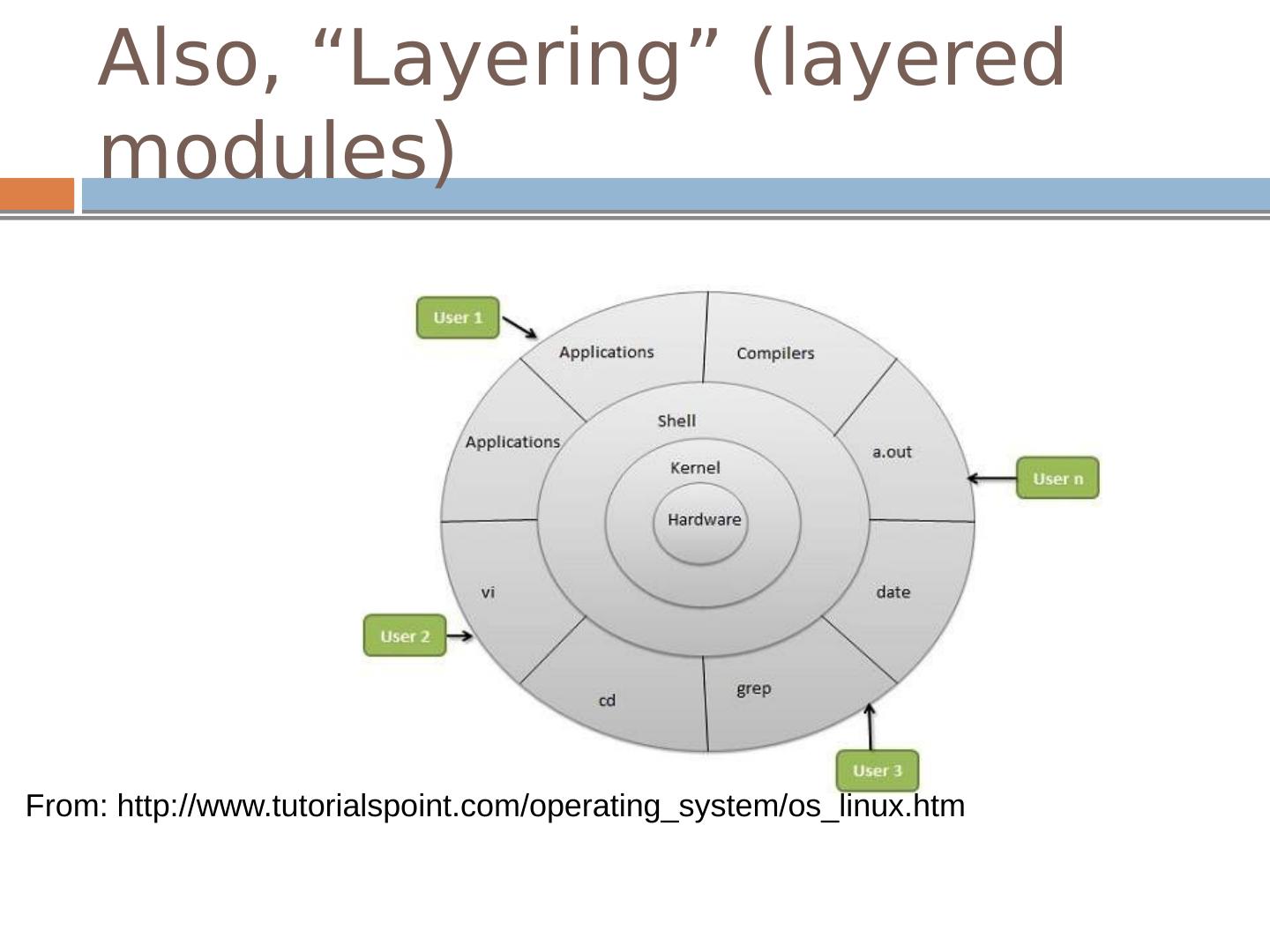
5 .Also, “Layering” (layered modules) From: http:// www.tutorialspoint.com / operating_system / os_linux.htm
6 .Any problem in computer science can be solved with another level of indirection Attributed to David Wheeler (by Butler Lampson)
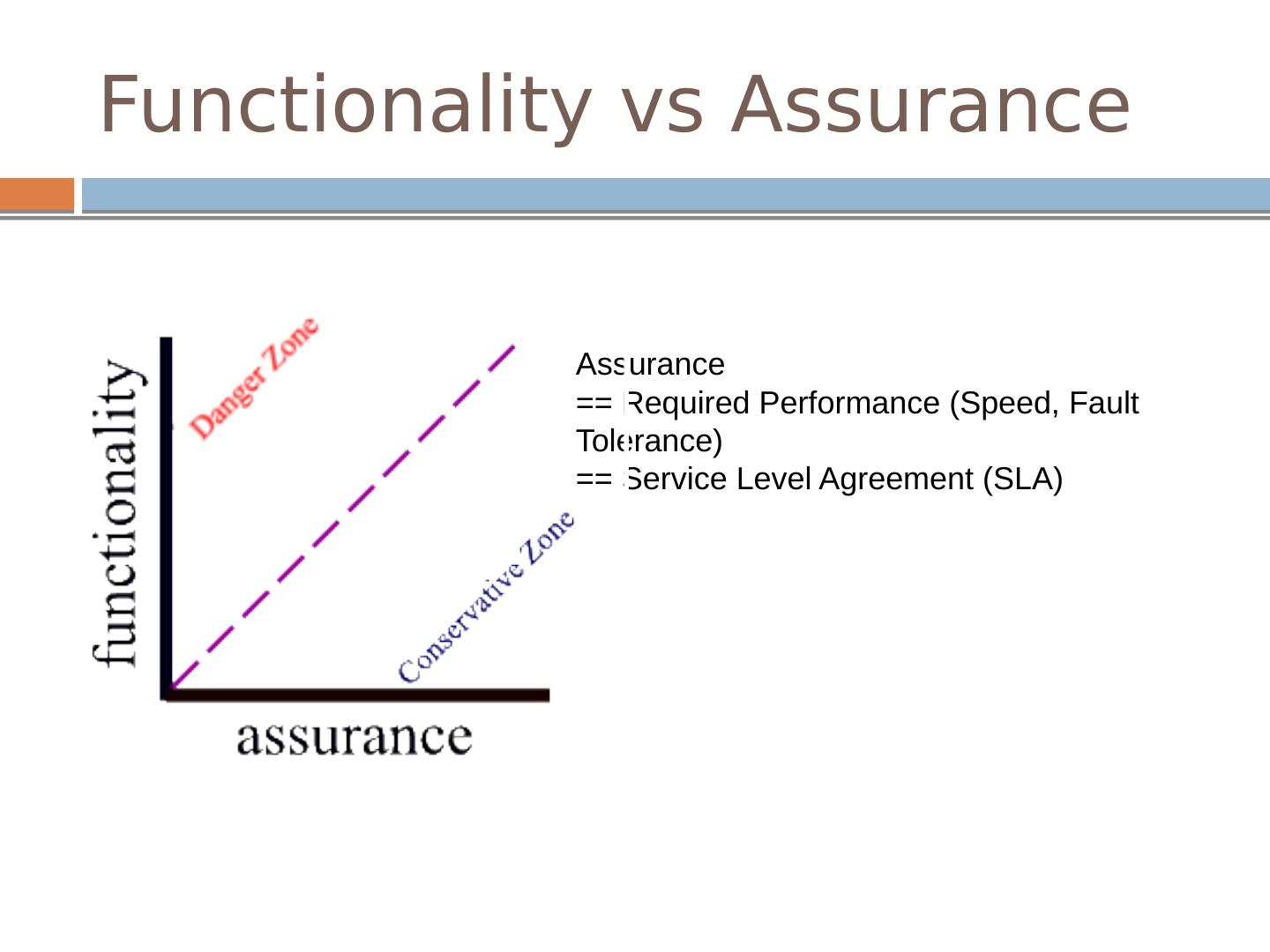
7 .Functionality vs Assurance Assurance == Required Performance (Speed, Fault Tolerance) == Service Level Agreement (SLA)
8 .End-to-End arguments in System Design – Jerry H. Saltzer , David P. Reed, David D. Clark (MIT) Jerry H. Saltzer A leader of Multics , key developer of the Internet, and a LAN (local area network) ring topology, project Athena David P. Reed Early development of TCP/IP, designer of UDP David D. Clark I/O of Multics , Protocol architect of Internet “We reject: kings, presidents and voting. We believe in: rough consensus and running code.”
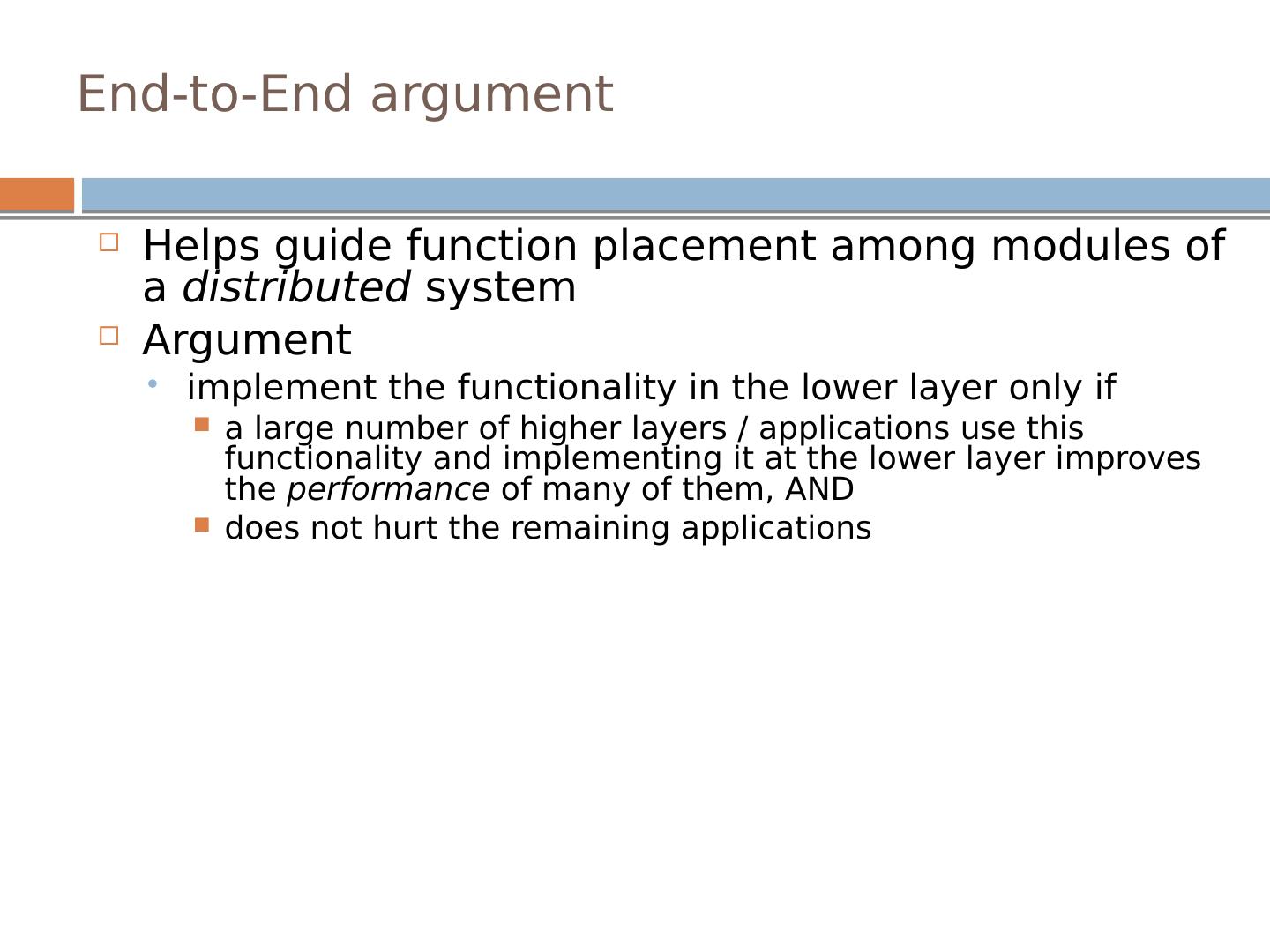
9 .End-to-End argument Helps guide function placement among modules of a distributed system Argument implement the functionality in the lower layer only if a large number of higher layers / applications use this functionality and implementing it at the lower layer improves the performance of many of them, AND does not hurt the remaining applications
10 .Example : File Transfer (A to B) A B Read File Data blocks App buffers File Data Pass (copy) data to the network subsystem 4. Pass msg/packet down the protocol stack 5. Send the packet over the network 6. Route packet
11 .Example : File Transfer (A to B) A B 7. Receive packet and buffer msg. 8. Send data to the application 9. Store file data blocks
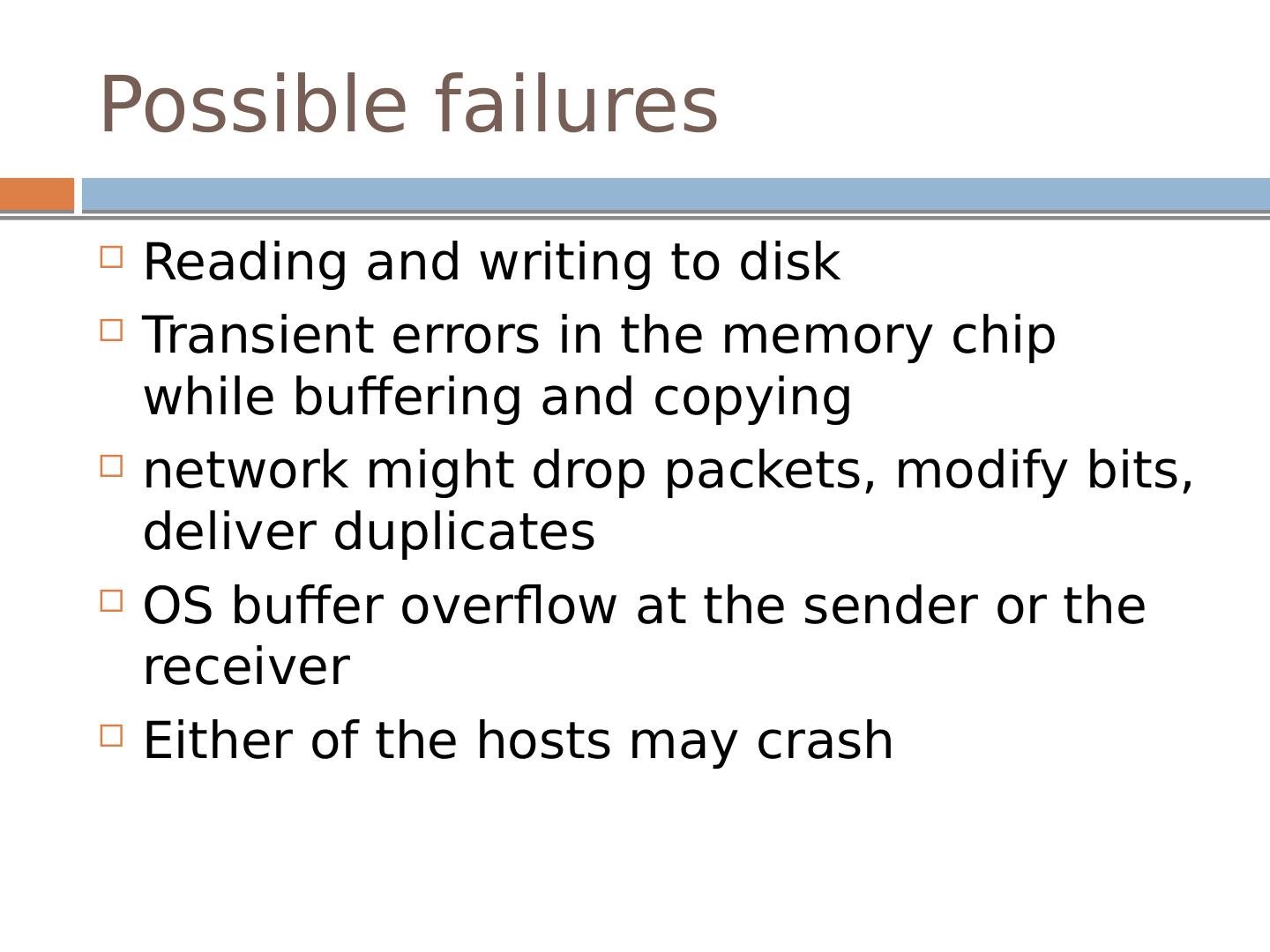
12 .Possible failures Reading and writing to disk Transient errors in the memory chip while buffering and copying network might drop packets, modify bits, deliver duplicates OS buffer overflow at the sender or the receiver Either of the hosts may crash
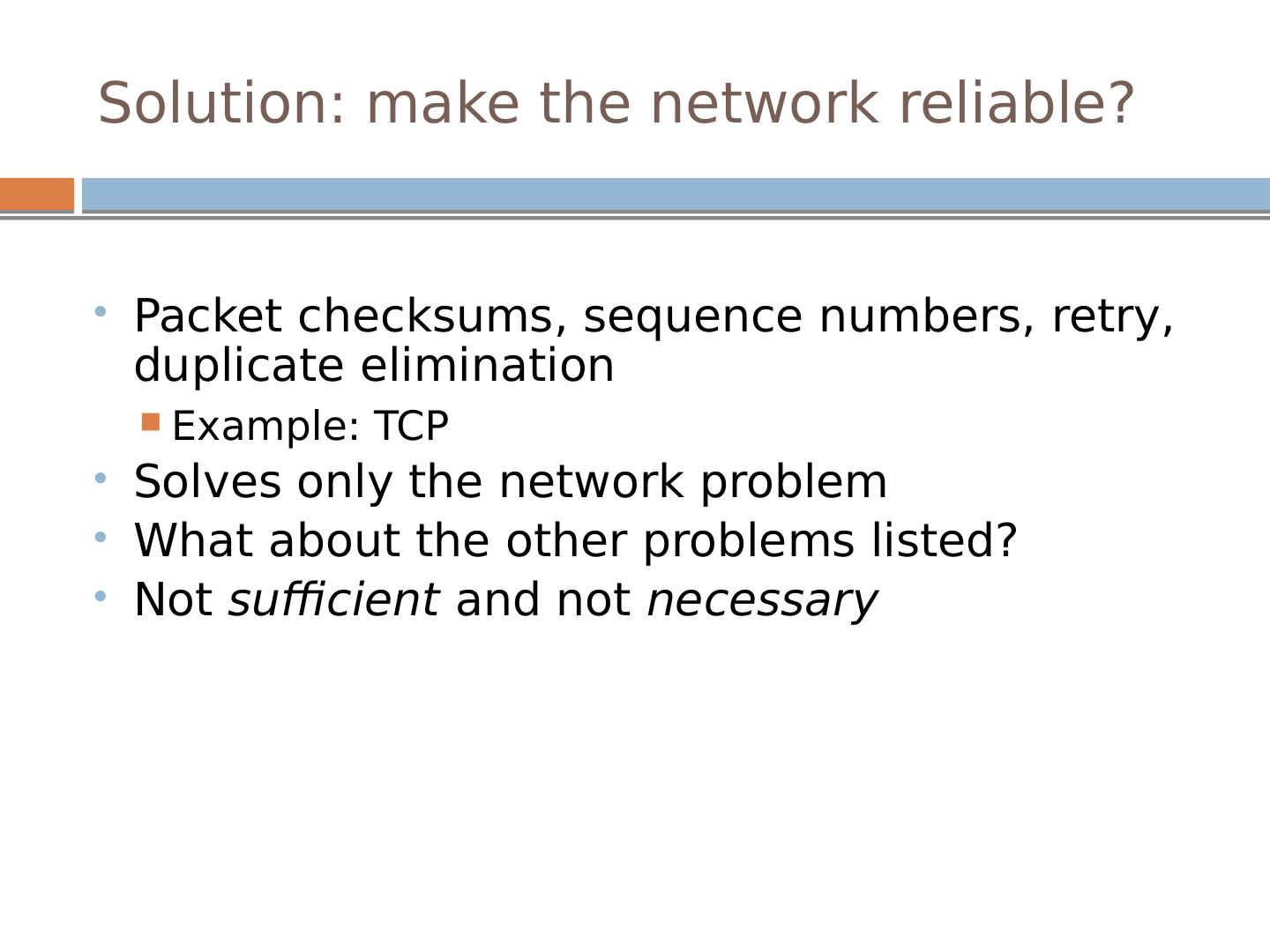
13 .Solution: make the network reliable? Packet checksums, sequence numbers, retry, duplicate elimination Example: TCP Solves only the network problem What about the other problems listed ? Not sufficient and not necessary
14 .Solution: end-to-end retransmission? Introduce file checksums and verify once transfer completes – end-to-end check . On failure – retransmit file Works! (modulo rotting bits on disk)
15 .Is network-level reliability useful? Per-link retransmission leads to faster recovery from dropped packets than end-to-end Seems particularly useful in wireless networks or very high latency networks But this may not benefit all applications Huge unnecessary overhead for, say, Real-Time speech transmission
16 .TCP/IP Transmission Control Protocol (TCP) It is a transport protocol providing error detection, retransmission, congestion control, and flow control TCP is almost-end-to-almost- end kernel-to-kernel, socket-to-socket, but not app-to-app Internet Protocol (IP) IP is a simple ("dumb"), stateless protocol that moves datagrams across the network The network itself (the routers) needs only to support the simple, lightweight IP; the endpoints run the heavier TCP on top of it when needed.
17 .Other end-to-end examples End-to-end authentication TLS, SSL Duplicate msg suppression
18 .Is argument complete? E.g. congestion control TCP leaves it to the ends Should the network trust the ends? RED In a wireless setting packet loss != congestion performance problems may appear in end-end systems under heavy load Performance enhancing Proxies
19 .“Hints for Computer System Design” --- Butler Lampson, 1983 Based on author’s experience in systems design Founding member of Xerox PARC (1970) Currently Technical Fellow at MSR and adjunct prof. at MIT Winner of ACM Turing Award (1994). IEEE Von Neumann Medal (2001) Was involved in the design of many famous systems, including databases and networks
20 .Some Projects & Collaborators Charles Simonyi - Bravo: WYSIWYG editor (MS Office) Bob Sproull - Alto operating system, Dover: laser printer, Interpress : page description language (VP Sun/Oracle) Mel Pirtle - 940 project, Berkeley Computer Corp. Peter Deutsch - 940 operating system, QSPL: system programming language (founder of Ghostscript ) Chuck Geschke , Jim Mitchell, Ed Satterthwaite - Mesa: system programming language
21 .Some Projects & Collaborators (cont.) Roy Levin - Wildflower: Star workstation prototype, Vesta : software configuration Andrew Birrell , Roger Needham, Mike Schroeder - Global name service and authentication Eric Schmidt - System models: software configuration (CEO/Chairman of Google/Executive Chairman of Alphabet) Rod Burstall - Pebble: polymorphic typed language
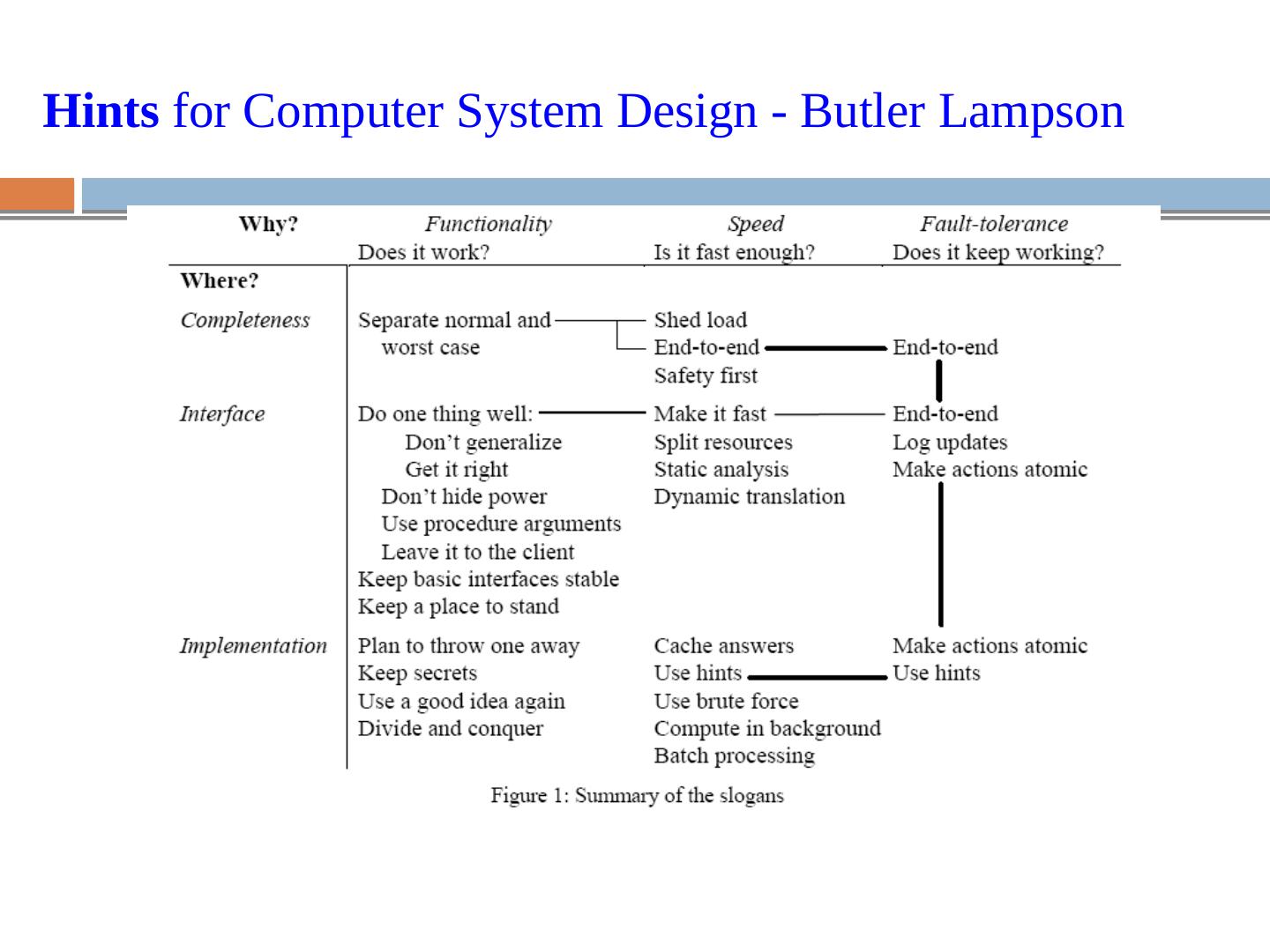
22 .System Design Hints organized along two axes: Why and Where Why: Functionality: does it work? Speed: is it fast enough? Fault-tolerance: does it keep working? Where: Completeness Interface Implementation
23 .Hints for Computer System Design - Butler Lampson
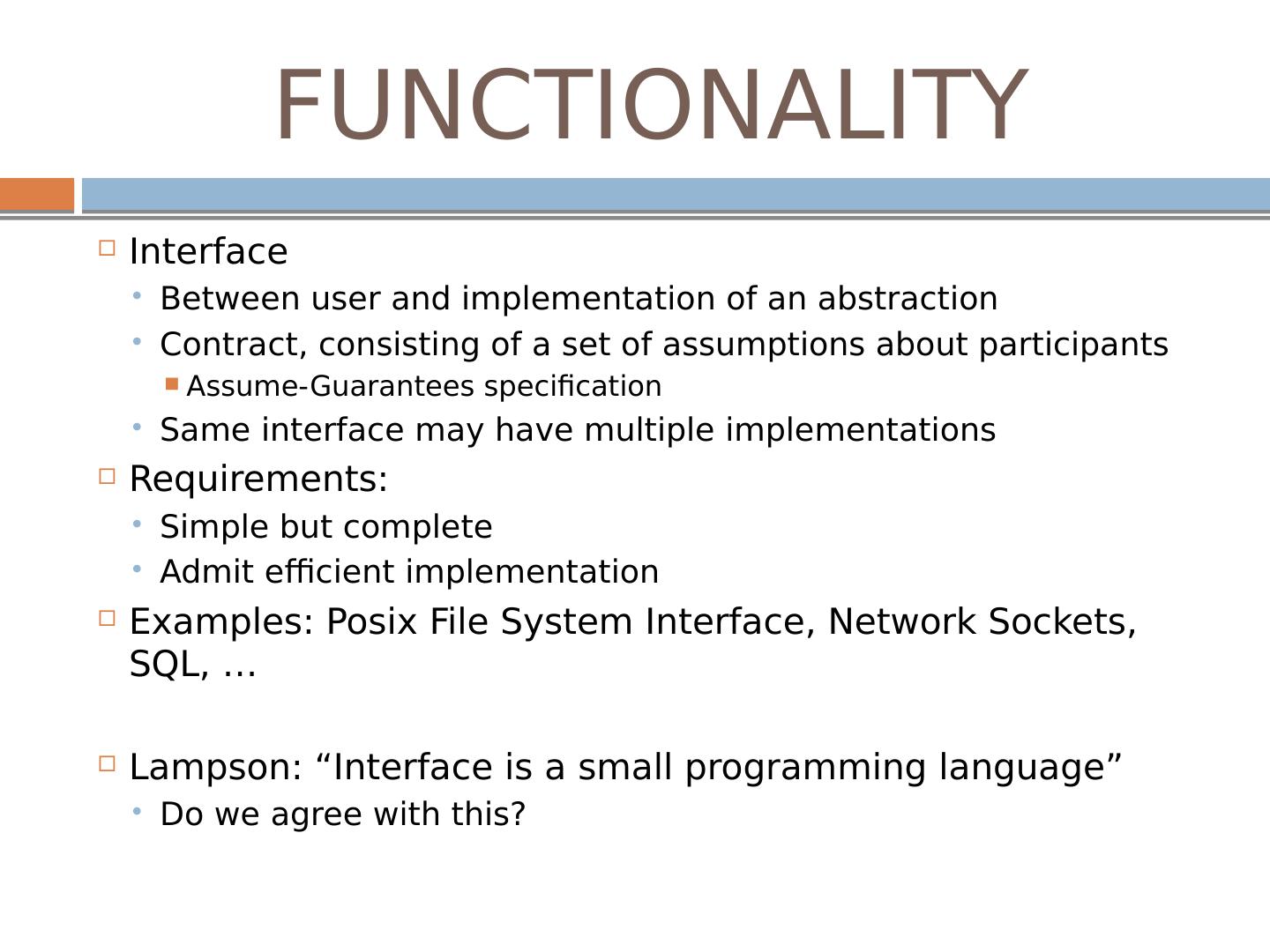
24 .FUNCTIONALITY Interface Between user and implementation of an abstraction Contract, consisting of a set of assumptions about participants Assume-Guarantees specification Same interface may have multiple implementations Requirements: Simple but complete Admit efficient implementation Examples: Posix File System Interface, Network Sockets, SQL, … Lampson: “Interface is a small programming language” Do we agree with this?
25 .Keep it Simple Stupid (KISS Principle) Attributed to aircraft e ngineer Kelly Johnson (1910—1990) Based on observation: systems work best if they are kept simple Related: Make everything as simple as possible, but not simpler (Einstein) It seems that perfection is reached not when there is nothing left to add, but when there is nothing left to take away (Antoine de Saint Exupéry ) If in doubt, leave it out (Anon.) Complexity is the Enemy: Exterminate Features (Charles Thacker) The unavoidable price of reliability is simplicity (Tony Hoare)
26 .Do one thing at a time, and do it well Don’t generalize Get it right! A complex interface is hard to implement correctly, efficiently Don’t penalize all for wishes by just a few Basic (fast) operations rather than generic/powerful (slow) ones Good interface admits implementation that is Correct Efficient Predictable Performance Simple does not imply good A simple but badly designed interface makes it hard to build applications that perform well and/or predictably
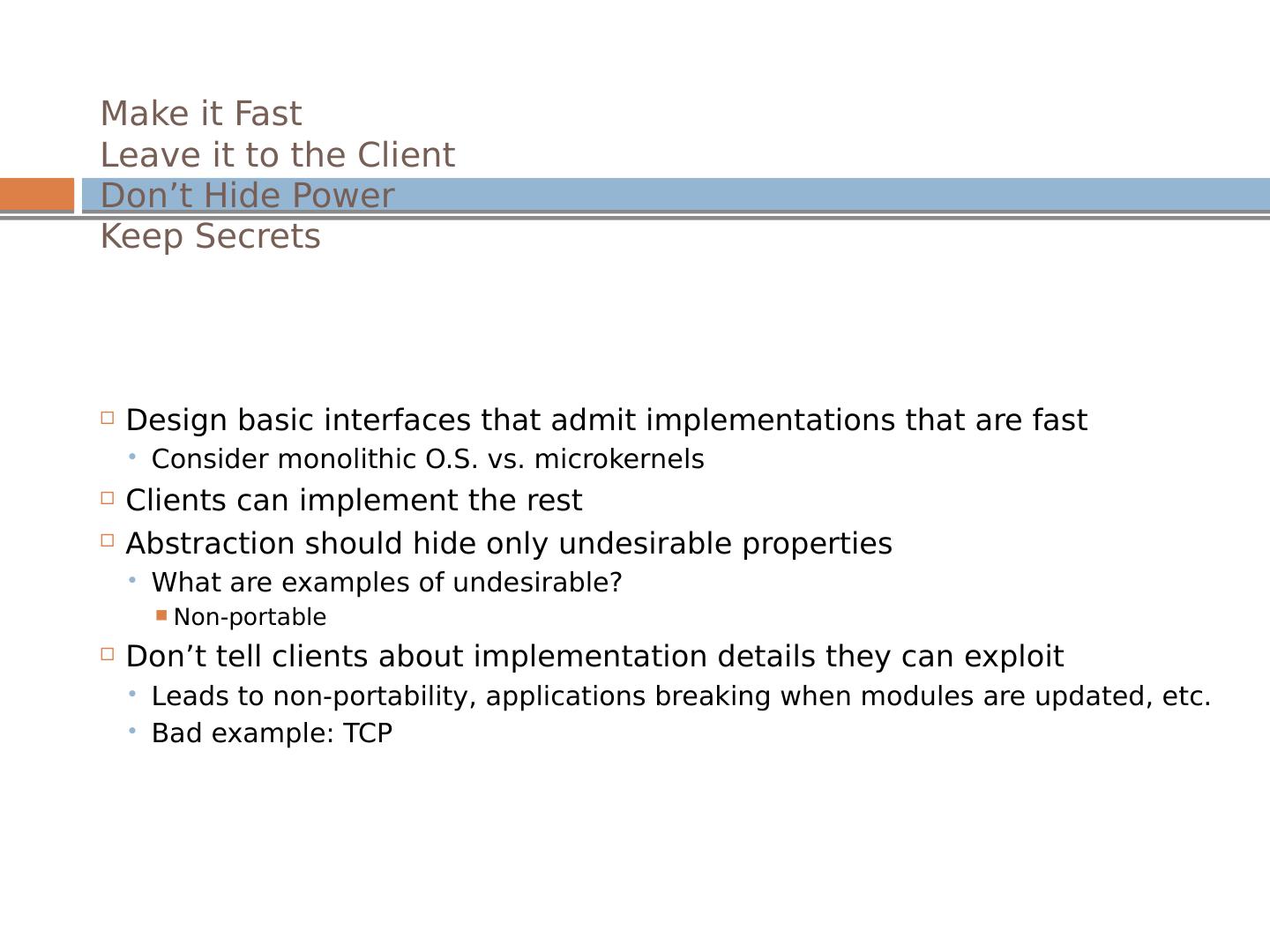
27 .Make it Fast Leave it to the Client Don’t Hide Power Keep Secrets Design basic interfaces that admit implementations that are fast Consider monolithic O.S. vs. microkernels Clients can implement the rest Abstraction should hide only undesirable properties What are examples of undesirable? Non-portable Don’t tell clients about implementation details they can exploit Leads to non-portability, applications breaking when modules are updated, etc. Bad example: TCP
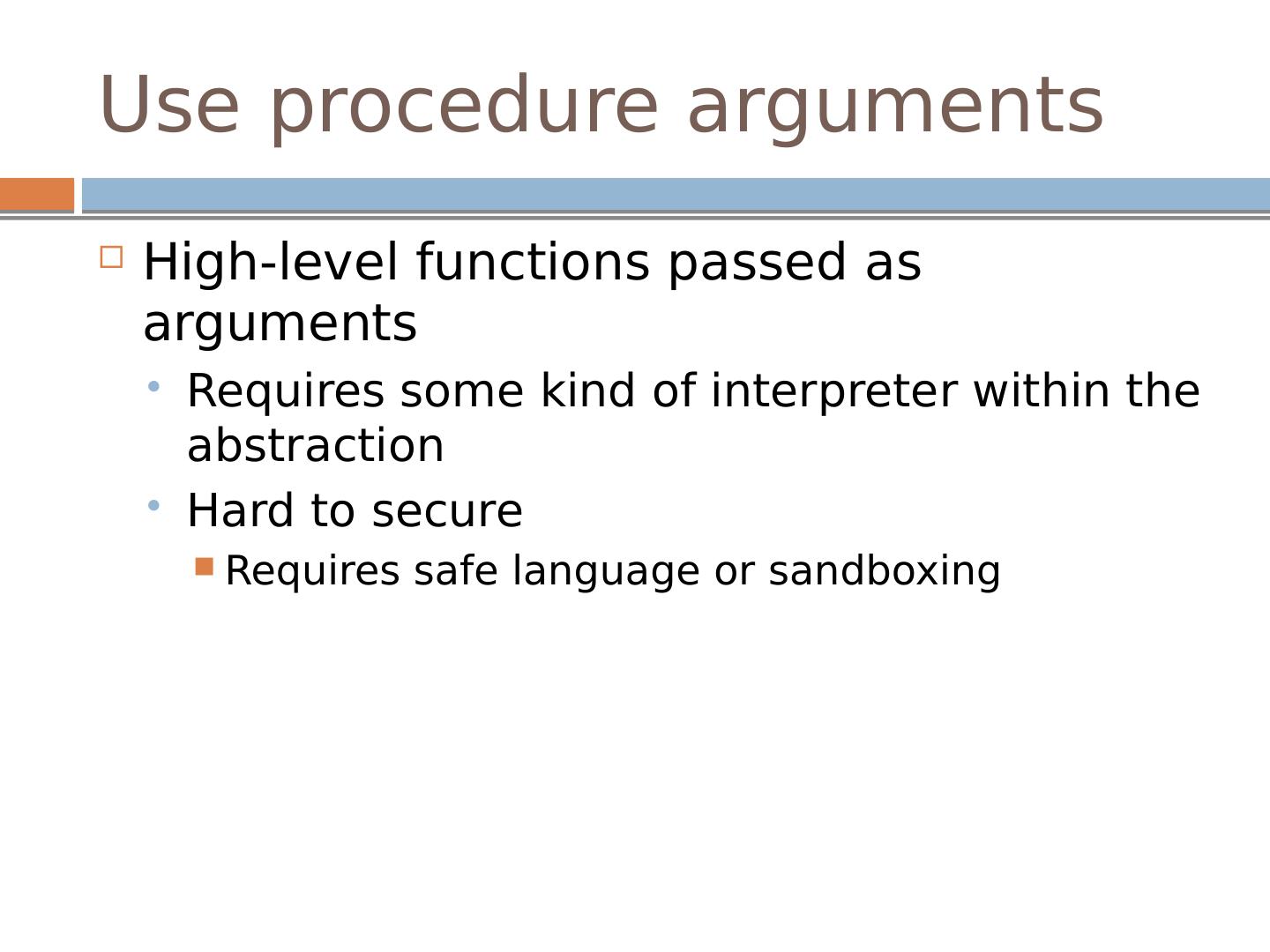
28 .Use procedure arguments High-level functions passed as arguments Requires some kind of interpreter within the abstraction Hard to secure Requires safe language or sandboxing
29 .Keep basic interfaces stable Keep a place to stand Ideally do not change interfaces Extensions are ok If you have to change the interface, provide a backward compatibility option Good example: Microsoft Windows