- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
Making Sense of It - CityU CS - City University of Hong Kong
展开查看详情
1 .CS1102 Lec10 – Computer Security Computer Science Department City University of Hong Kong
2 . Jean Wang / CS1102 - Lec10 2 Objectives Identify the various types of security risks/threats that can cause damages to computers or users Recognize how a computer virus works and take the necessary steps to prevent viruses Distinguish different malicious programs: viruses, worms, Trojan horses, spyware and cookies Discuss techniques to prevent unauthorized computer access and use Define encryption and explain why it is necessary Discuss public/private key infrastructure and explain how it could be used for secure communication and authentication Describe precautions you should take to safeguard your computer and data
3 .3 Computer Security Computer security is about protecting information from being attacked, while making it readily available to authorized users Security risk/threat is any thing, event or action, that could cause a loss of or damage to computer hardware, software, data, or processing capability. The threats originate from two main sources Human Malicious : usually come from users who have malicious intention, like hackers Non-malicious : usually come from careless users who are not trained on computers or are not aware of various computer security threats Nature Come from nature disasters such as Earthquakes, hurricanes, floods, lightening, fire and etc. Jean Wang / CS1102 - Lec10
4 .Computer Security Risks 4 Jean Wang / CS1102 - Lec10
5 .5 Types of Viruses Attacks Major threats to data are malicious software ( malware ) Viruses Self-replicating programs that attach themselves to executable files Can spread from file to file Can damage files or hardware Worms Programs that use computer networks and security holes to spread themselves (no need to attach themselves to files) Typical worms were designed only to replicate and spread, and do not attempt to change the systems they pass through Can cause system or network disruption by generating overwhelming amount of traffic Trojan horses Programs that claim to perform one function while actually doing something else Not designed to replicate themselves Can steal passwords or open backdoors (remote access for hackers) Jean Wang / CS1102 - Lec10
6 .6 Threats to Privacy Data privacy or information privacy (or simply privacy) is the right of individuals to decide when and how much they want to share with others Personal information is a marketable commodity, which raises many issues: Collecting public, but personal or private information (e.g., Google’s Street View) Spreading information without consent, leading to identity theft Spreading inaccurate information Threats to your privacy include Internet cookies Spyware and Adware Spamming and Phishing Jean Wang / CS1102 - Lec10
7 .7 Computer Virus A computer virus is like a biological virus, which can " infect " a program by attaching itself to it Viruses replicate themselves on the host (infected) computer One way is to infect executable files , such as .exe or . vbs files When computer executes the infected program, the virus instructions will get the chance to be executed, and infect more other files W hen the infected files are distributed to other machines, the virus spreads to other machines Can be classified according to types of files they infect: Executable file virus Boot sector virus Macro virus Email virus Jean Wang / CS1102 - Lec10
8 .8 Computer Virus An executable file virus is the virus that attaches to an application program (.exe, or . vbs ) The host program needs to be executed in order for the virus to replicate A boot sector virus infects some system files that the computer uses every time it boots up The boot sector of a floppy disk or hard disk contains the instructions how to load the operating system The virus can guarantee it gets executed every time the system starts Macro viruses infect a set of instructions called a macro that is used to automate tasks in documents and spreadsheets When the infected document or spreadsheet is opened and you choose to enable macros, the macro virus gets executed and infects other documents Email viruses are virus programs sent as email attachment that will cause the host machine infected if activated When the user view the attachment, the virus code gets executed Jean Wang / CS1102 - Lec10
9 .9 Symptoms of Infection Viruses, worms, and Trojan horses spread by sharing files, USB, CD’s, web site download, email attachments The downside of all those free stuff from the Internet are the security threats If you have the following symptoms in your machine, you may be infected by some malicious software See some unknown or not-making-sense Windows messages Frequent annoying pop-up ads Encounter problems when saving files or notice missing files Computer runs slower than usual Frequent or unexpected reboots or shuts down Sending out e-mails or Internet traffic on its own Available memory is less than expected Increase in size of executable files Periodic network activities when you are not accessing the network Jean Wang / CS1102 - Lec10
10 .10 Anti-Virus Software Anti-virus software are the utility programs that monitor your computer, looking for potential viruses, worms and Trojan horses The most common technique for antivirus software is to store virus signatures in a Database and scan your files regularly for these signatures A virus signature is a known identifier of the virus, usually some specific pattern of virus code Works for known viruses, BUT is not able to detect new viruses Once a virus is found The anti-virus program will attempt to remove the detected viruses or Quarantine infected files in a separate area of hard disk Jean Wang / CS1102 - Lec10
11 .10 Anti-Virus Software Anti-virus software are the utility programs that monitor your computer, looking for potential viruses, worms and Trojan horses The most common technique for antivirus software is to store virus signatures in a Database and scan your files regularly for these signatures A virus signature is a known identifier of the virus, usually some specific pattern of virus code Works for known viruses, BUT is not able to detect new viruses Once a virus is found The anti-virus program will attempt to remove the detected viruses or Quarantine infected files in a separate area of hard disk Jean Wang / CS1102 - Lec10
12 .12 Spamming and Phishing Spamming is the act of sending unsolicited (un-welcomed) electronic messages to many recipients The most common form of spam is email spamming Spammer obtain email addresses by a number of means From mailing list From Web pages By guessing Phishing refers to faked websites or emails that are designed to steal your personal information especially credit card numbers, bank accounts and passwords Common Internet phishing includes Sending out many email messages that appear to be legitimate (legal and genuine) Designing web sites look official but actually not Jean Wang / CS1102 - Lec10
13 .13 Unauthorized Access and Use Another kind of security threats is unauthorized access to someone’s computer (data and programs) without permission A port probe (or port scan) uses automated software to locate computers that have open ports and are vulnerable to unauthorized access Servers use TCP Port (a number ranges from 0 to 65535) to communication with remote clients, which leaves vulnerable points for malicious attacks Denial of Service attack that jams servers (e.g., web server) or networks with traffic such that servers become unable to server normal requests A back door is a piece of program that allows intruders to bypass security controls Spoofing is a technique that intruders use to concealing the identity of the sender to make their network transmission appear legitimate Jean Wang / CS1102 - Lec10
14 .Prevent Unauthorized Access How companies or organizations protect their computers against malicious intrusion? Using access control that defines who can access computer and what actions they can take Requiring user name and password for users to log in the system OR Requiring using possessed objects such as smart cards OR Using biometric input devices Installing firewall system (consisting of hardware and software) to analyze network traffic, and block unwanted traffic and identify suspicious behaviors Firewall does its job by monitoring every packet that goes in and out of your computer Setting up virtual private network (VPN) access to secure remote connections via a public network to corporate LAN 14 Jean Wang / CS1102 - Lec10 14
15 .15 Password-based Authorization Your choice of password can actually affect overall system security You should choose one that is long enough and difficult for others to make guesses about what you have chosen, but at the same time easy to remember Brute-force attack v.s . dictionary attack Jean Wang / CS1102 - Lec10
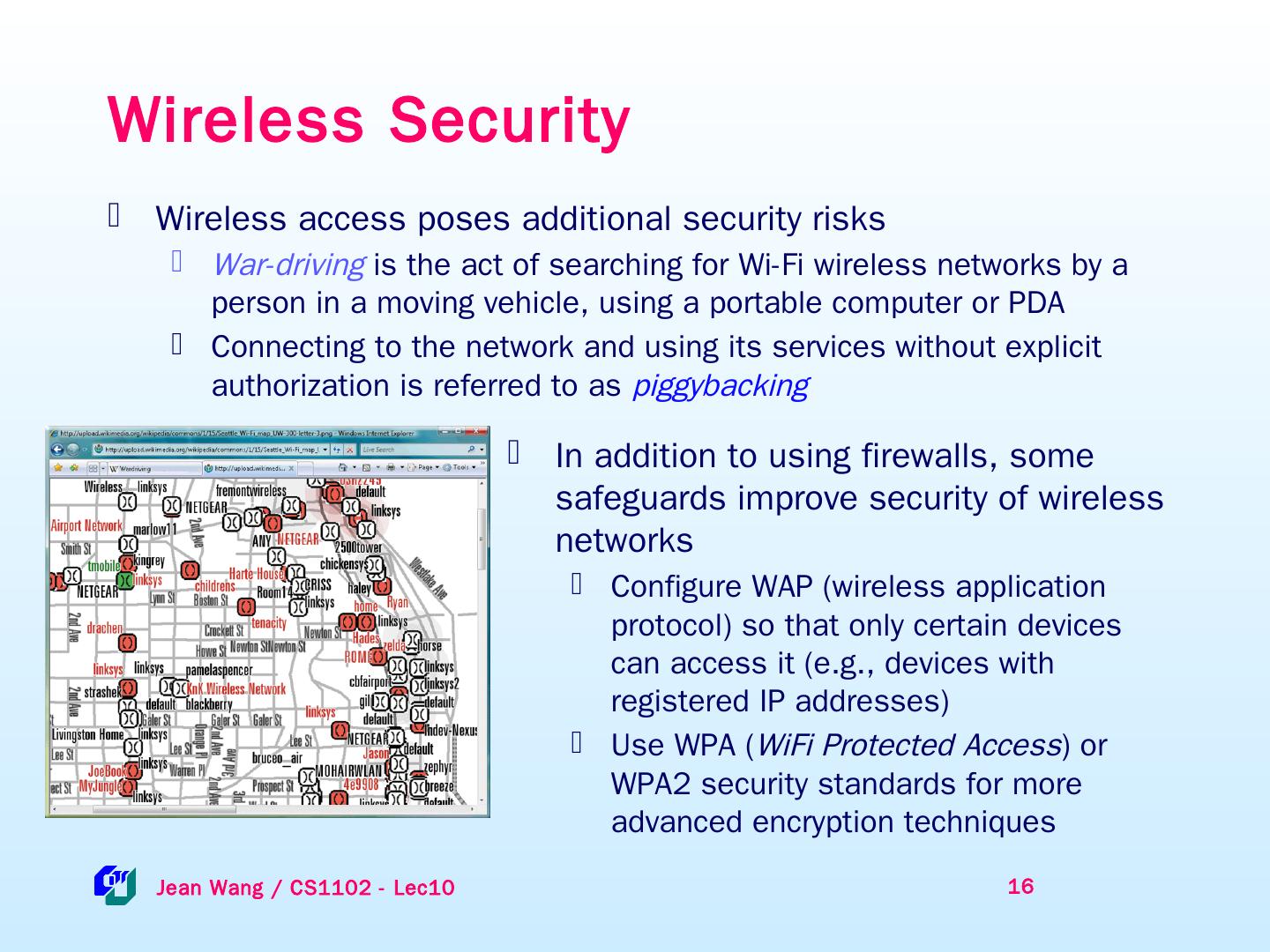
16 .Wireless Security Wireless access poses additional security risks War-driving is the act of searching for Wi-Fi wireless networks by a person in a moving vehicle, using a portable computer or PDA Connecting to the network and using its services without explicit authorization is referred to as piggybacking 16 Jean Wang / CS1102 - Lec10 In addition to using firewalls, some safeguards improve security of wireless networks Configure WAP (wireless application protocol) so that only certain devices can access it (e.g., devices with registered IP addresses) Use WPA ( WiFi Protected Access ) or WPA2 security standards for more advanced encryption techniques
17 .Data Protection through Encryption
18 .18 Encryption - Data Protection Encryption is the process of converting readable data into unreadable characters (called cipher text ) to prevent information theft Just like encoding and decoding, to convert the cipher text back to the original data, a decryption process is needed The encryption/decryption process usually involves a cryptographic algorithm + some cryptographic key(s) Many encryption methods exist, for example Name Method Original text Ciphertext Transposition Switch the order of characters WIRELESS IWERELSS Substitution Replace characters with other characters I LOVE YOU V YBIR LBH Expansion Insert characters MOUSE MDODUDSDED Compaction Remove characters and store elsewhere COMMUNICATION COMUICTIN Jean Wang / CS1102 - Lec10
19 .19 Motivation of Encryption Bob Alice Attacker ( Eve) intercepts and reads messages Hello Hello Jean Wang / CS1102 - Lec10
20 .20 Motivation of Encryption Bob Alice Attacker ( Eve) intercepts but can not read messages @#%%^ @#%%^ Hello Hello Jean Wang / CS1102 - Lec10
21 .Symmetric & Asymmetric Encryption Symmetric key encryption techniques use the same key for encryption and decryption Requires the key to be distributed before someone else can read the cipher-text Problem: someone else can capture the key which makes it vulnerable to attack Asymmetric key encryption also known as public key encryption Uses a pair of different keys A public key is a widely distributed one (could be posted on a Web page or emailed) A private key is kept secretly Encryption can be done by either key, with the other key for decryption 21 Jean Wang / CS1102 - Lec10
22 .Symmetric & Asymmetric Encryption Symmetric key encryption techniques use the same key for encryption and decryption Requires the key to be distributed before someone else can read the cipher-text Problem: someone else can capture the key which makes it vulnerable to attack Asymmetric key encryption also known as public key encryption Uses a pair of different keys A public key is a widely distributed one (could be posted on a Web page or emailed) A private key is kept secretly Encryption can be done by either key, with the other key for decryption 21 Jean Wang / CS1102 - Lec10
23 .Symmetric & Asymmetric Encryption Symmetric key encryption techniques use the same key for encryption and decryption Requires the key to be distributed before someone else can read the cipher-text Problem: someone else can capture the key which makes it vulnerable to attack Asymmetric key encryption also known as public key encryption Uses a pair of different keys A public key is a widely distributed one (could be posted on a Web page or emailed) A private key is kept secretly Encryption can be done by either key, with the other key for decryption 21 Jean Wang / CS1102 - Lec10
24 .Symmetric & Asymmetric Encryption Symmetric key encryption techniques use the same key for encryption and decryption Requires the key to be distributed before someone else can read the cipher-text Problem: someone else can capture the key which makes it vulnerable to attack Asymmetric key encryption also known as public key encryption Uses a pair of different keys A public key is a widely distributed one (could be posted on a Web page or emailed) A private key is kept secretly Encryption can be done by either key, with the other key for decryption 21 Jean Wang / CS1102 - Lec10
25 .Symmetric & Asymmetric Encryption Symmetric key encryption techniques use the same key for encryption and decryption Requires the key to be distributed before someone else can read the cipher-text Problem: someone else can capture the key which makes it vulnerable to attack Asymmetric key encryption also known as public key encryption Uses a pair of different keys A public key is a widely distributed one (could be posted on a Web page or emailed) A private key is kept secretly Encryption can be done by either key, with the other key for decryption 21 Jean Wang / CS1102 - Lec10
26 .26 A Sample Certificate This is a certificate issued by Ace CA: Data Version : v1 (0x0) Serial Number: 1 (0x1) Signature Algorithm: PKCS #1 MD5 With RSA Encryption Issuer : OU=Ace Certificate Authority, O=Ace Ltd, C=US Validity : Not Before: Fri Nov 15 00:24:11 1996 Not After: Sat Nov 15 00:24:11 1997 Subject : CN=Jane Doe, O=Ace Industry, C=US Subject Public Key Info: Algorithm : PKCS #1 RSA Encryption Public Key: 00:d0:e5:60:7c:82:19:14:cf:38 : F7:5b:f7:35:4e:14:41:2b:ec:24: 33:73:be:06:aa:3d:8b:dc:0d:06 : 35:10:92:25:da:8c:c3:ba:b3:d7: lf:1d:5a:50:6f:9a:86:53:15:f2 : 53:63:54:40:88:a2:3f:53:11:ec: 68:fa:e1:f2:57 Public Exponent: 65537 (0x10001) Signature Algorithm: PKCS #1 MD5 With RSA Encryption Signature: 12:f6:55:19:3a:76:d4:56:87:a6 : 39:65:f2:66:f7:06:f8:10:de:cd: 1f:2d:89:33:90:3d:a7:e3:ec:27 : ac:e1:c0:29:c4:5a:69:17:51:dc: 1e:0c:c6:5f:eb:dc:53:55:77:01 : 83:8f:4a:ab:41:46:02:d7:c8:9a: fe:7a:91:5c
27 .27 Sign an Email / Read a Signed Email A signed email ensures you the email is truly from the owner of the email-address (the sender cannot deny it): When user click “sign” to sign an outgoing email, his private key is used to generate a signature from the email. (An email’s signature is the encrypted abstract of the email.) The email is attached with two files: 1) the email’s signature and 2) the sender’s certificate When the recipient receives this signed email, the mail-reader (e.g., outlook ) will: Verify the attached certificate by using the CA’s public key Verify the attached email’s signature by using the certificate Save the certificate in local database for future use…
28 .28 Encrypt / Decrypt Emails When a user clicks “encrypt ” to send an email, the email will be encrypted by using the recipient’s public key (embedded in the recipient’s certificate). The user needs to have the recipient’s certificate for encrypting the email (the certificate was already saved in local database when receiving a signed email earlier from the recipient). When the recipient receives the encrypted email, the mail-system will use his private key to decrypt it. An encrypted email will not be eavesdropped or tampered.
29 .29 SSL - Secure Sockets Layer SSL (Secure Sockets Layer) provides encryption of all data that passes between clients and Internet servers You will probably see a key icon becoming whole or a padlock closing indicating the session is secure Also notice that the http in the address bar, becomes https Use public/private keys for authentication and symmetric session keys for data communication Jean Wang / CS1102 - Lec10