- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
05现代密码学理论与实践--aes密码
展开查看详情
1 .现代密码学理论与实践 第 5 章 AES 密码 Fifth Edition by William Stallings 苗付友 mfy@ustc.edu.cn 2016 年 10 月
2 .高级加密标准 AES 要点 AES 是一种分组密码,用以取代 DES 的商业应用。其分组长度为 128 位,密钥长度为 128 位、 192 位或 256 位 AES 没有使用 Feistel 结构。每轮由四个独立的运算组成:字节代换、置换、有限域上的算术运算,以及与密钥的异或运算
3 .本章目录 5.1 AES 概述 5.2 The AES Cipher – Rijndael 5.3 AES 的一轮加密过程 1 ) 字节代替变换 2 ) 行移位变换 3 ) 列混淆变换 4 ) 轮密钥加变换
4 .AES 的评估准则 AES 的起源 因为 DES 的不安全,建议用 3DES ,密钥 168 位,抵御密码分析攻击。但是 3DES 用软件实现速度较慢,分组短,仅 64 位。 美国国家标准技术协会 NIST 在 1997 年征集新标准,要求分组 128 位,密钥 128 、 192 或 256 15 候选算法在 1998 年 6 月通过了第一轮评估,仅有 5 个候选算法在 1999 年 8 月通过了第二轮评估 2000 年 10 月, NIST 选择 Rijndael 作为 AES 算法, Rijndael 的作者是比利时的密码学家 Joan Daemen 博士和 Vincent Rijmen 博士 2001 年 11 月, NIST 完成评估并发布了最终标准 FIPS PUB 197
5 .AES Requirements Private key symmetric block cipher 128-bit data, 128/192/256-bit keys Stronger and faster than Triple-DES Active life of 20-30 years (+ archival use) Provide full specification and design details Both C and Java implementations NIST have released all submissions and unclassified analyses
6 .AES Shortlist After testing and evaluation, shortlist in Aug-99: MARS (IBM) - complex, fast, high security margin RC6 (USA) - v. simple, v. fast, low security margin Rijndael (Belgium) - clean, fast, good security margin Serpent (Euro) - slow, clean, v. high security margin Twofish (USA) - complex, v. fast, high security margin
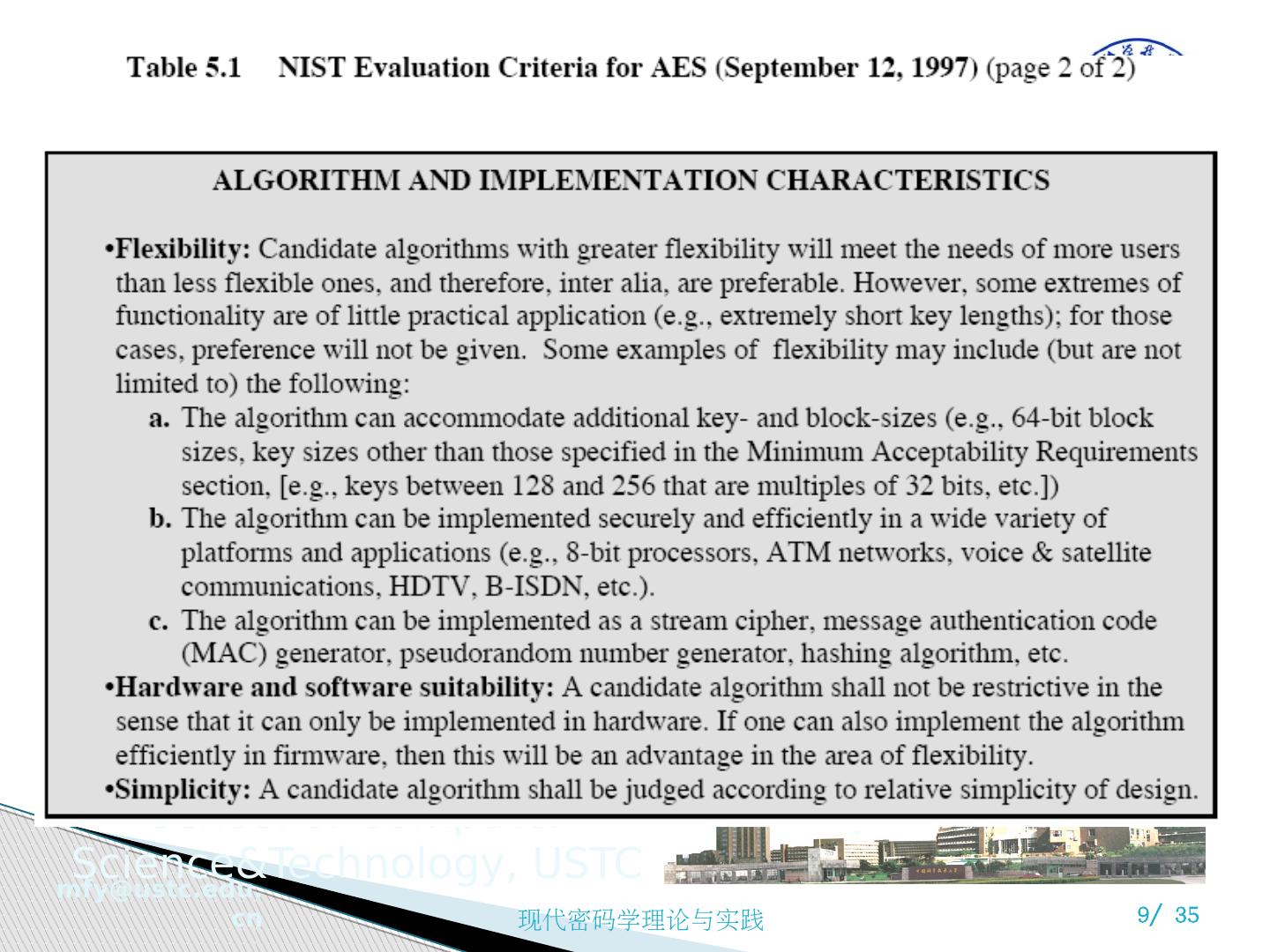
7 .AES 的评估 AES 评估准则的三大类别 安全性:指密码分析方法分析一个算法所需的代价 成本:期望 AES 能够广泛应用于各种实际应用,计算效率要高 算法和执行特征:算法灵活性、适合于多种硬件和软件方式的实现、简洁性,便于分析安全性
8 .
9 .
10 .AES 评估准则 一般安全性 依赖于密码学界的公共安全分析 软件实现 软件执行速度,跨平台执行能力及密钥长度改变时速度变化 受限空间环境 在诸如智能卡中的应用 硬件实现 硬件实现时能够提高执行速度或缩短代码长度 抵御密码分析攻击 密钥灵活性 快速改变密钥长度的能力 其他的多功能性和灵活性 指令级并行执行的潜力
11 .2016/10/17 现代密码学理论与实践05 11 /34
12 .2016/10/17 现代密码学理论与实践05 11 /34
13 .5.2 The AES Cipher - Rijndael Designed by Rijmen-Daemen in Belgium Has 128/192/256 bit keys, 128 bit data An iterative rather than Feistel Cipher treats data in 4 groups of 4 bytes operates an entire block in every round Designed to be: resistant against known attacks speed and code compactness on many CPUs design simplicity
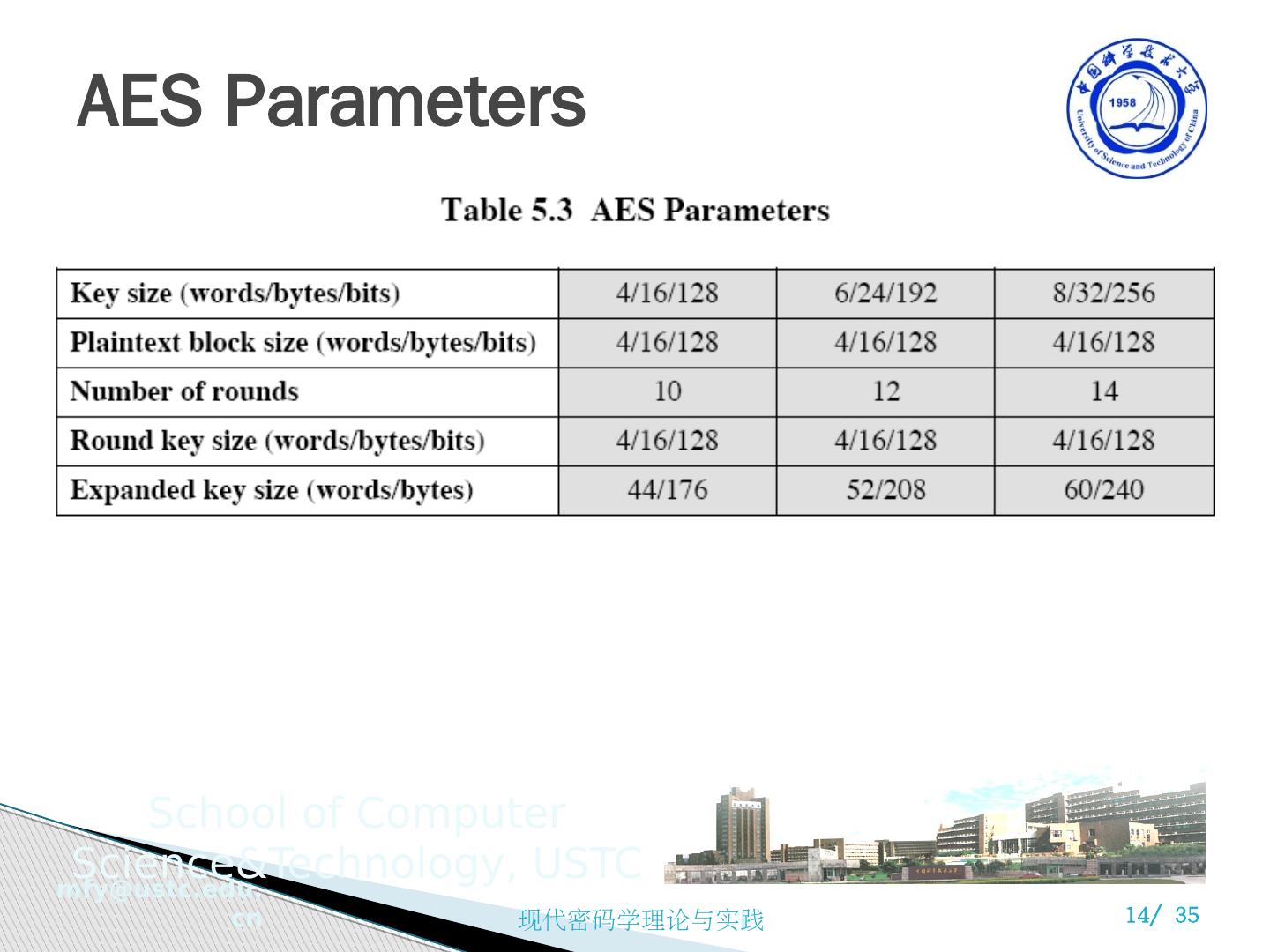
14 .AES Parameters
15 .Rijndael Processes data as 4 groups of 4 bytes (state) Has 9/11/13 rounds in which state undergoes: byte substitution (1 S-box used on every byte) shift rows (permute bytes between groups/columns) mix columns (subs using matrix multiply of groups) add round key (XOR state with key material) Initial XOR key material & incomplete last round All operations can be combined into XOR and table lookups - hence very fast & efficient
16 .Rijndael Processes data as 4 groups of 4 bytes (state) Has 9/11/13 rounds in which state undergoes: byte substitution (1 S-box used on every byte) shift rows (permute bytes between groups/columns) mix columns (subs using matrix multiply of groups) add round key (XOR state with key material) Initial XOR key material & incomplete last round All operations can be combined into XOR and table lookups - hence very fast & efficient
17 .AES 的数据结构
18 .5.2 AES 的结构 非 Feistel 结构 密钥被扩展成由 44 个 32 位字组成的数组 w[i] 一个混淆和三个代换 字节代换:用一个 S 盒完成分组中的按字节代换 行移位:一个简单的置换 列混淆:利用在域 GF(2 8 ) 上的算术特性的代换 轮密钥加:利用当前分组和扩展密钥的一部分进行按位 XOR 算法结构简单 仅在轮加密阶段中使用密钥 轮密钥加配合其他三个混淆的交替使用提供了安全性 每个阶段均可逆 解密按逆序方式使用扩展密钥,但是算法不一样 一旦将四个阶段求逆,可以证明解密函数可以恢复明文 加密和解密过程的最后一轮均只包括三个阶段
19 .5.3 AES 的一轮加密过程
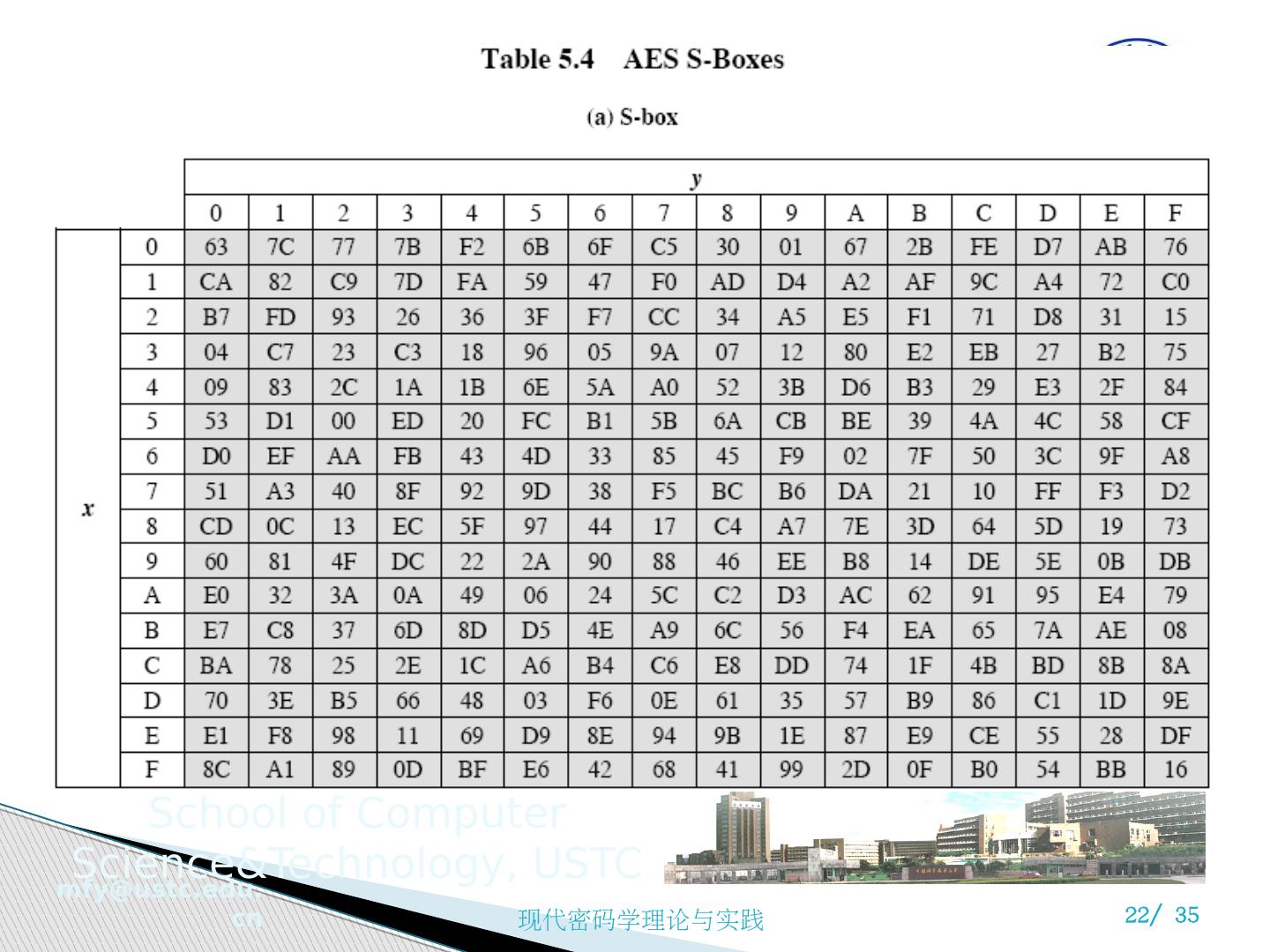
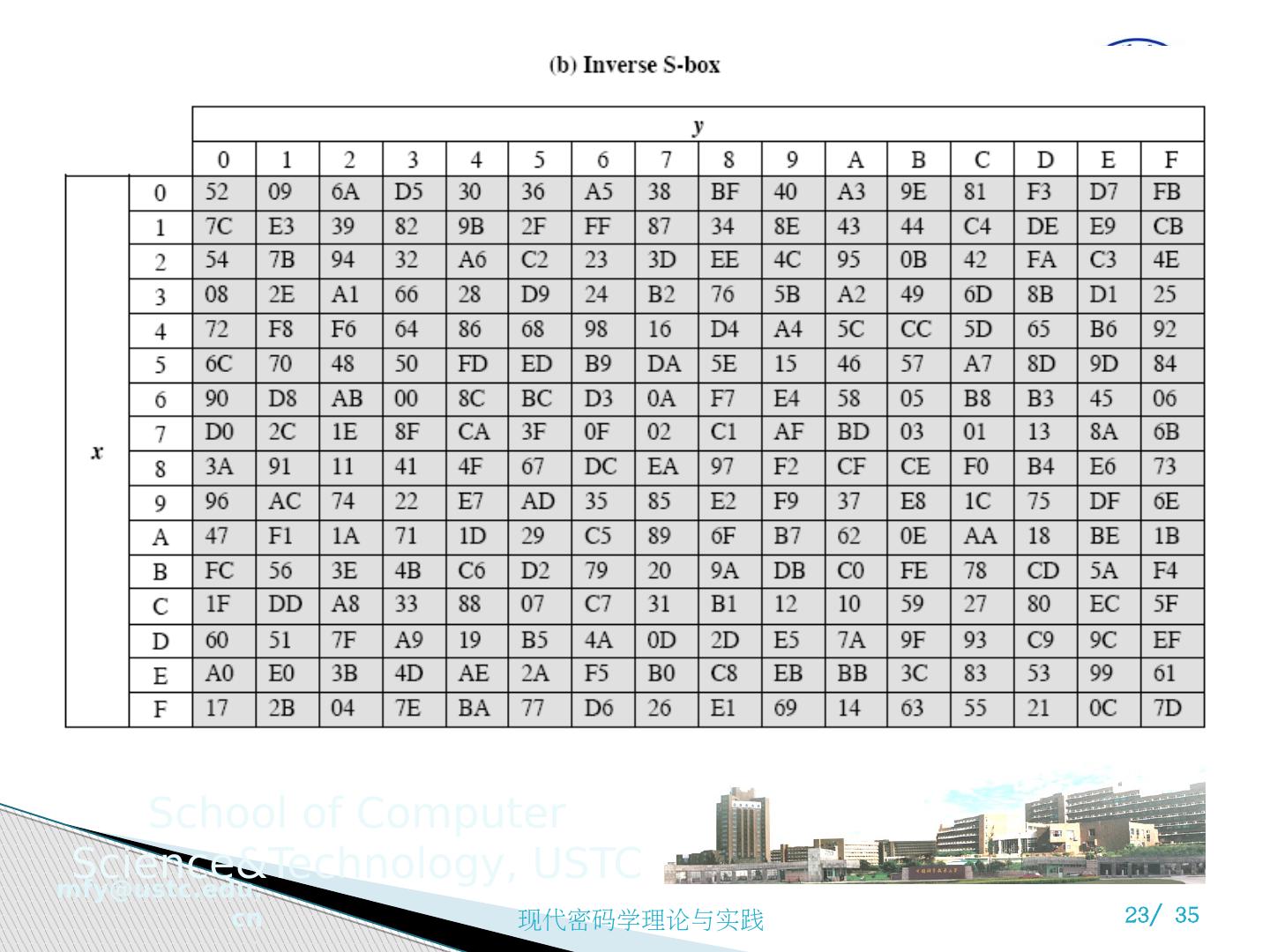
20 .1 ) 字节代替变换 A simple substitution of each byte Uses one table of 16x16 bytes containing a permutation of all 256 8-bit values Each byte of state is replaced by byte in row (left 4-bits) & column (right 4-bits) eg. byte {95} is replaced by row 9 col 5 byte which is the value {2A}
21 .字节代换变换
22 .字节代换变换
23 .字节代换变换
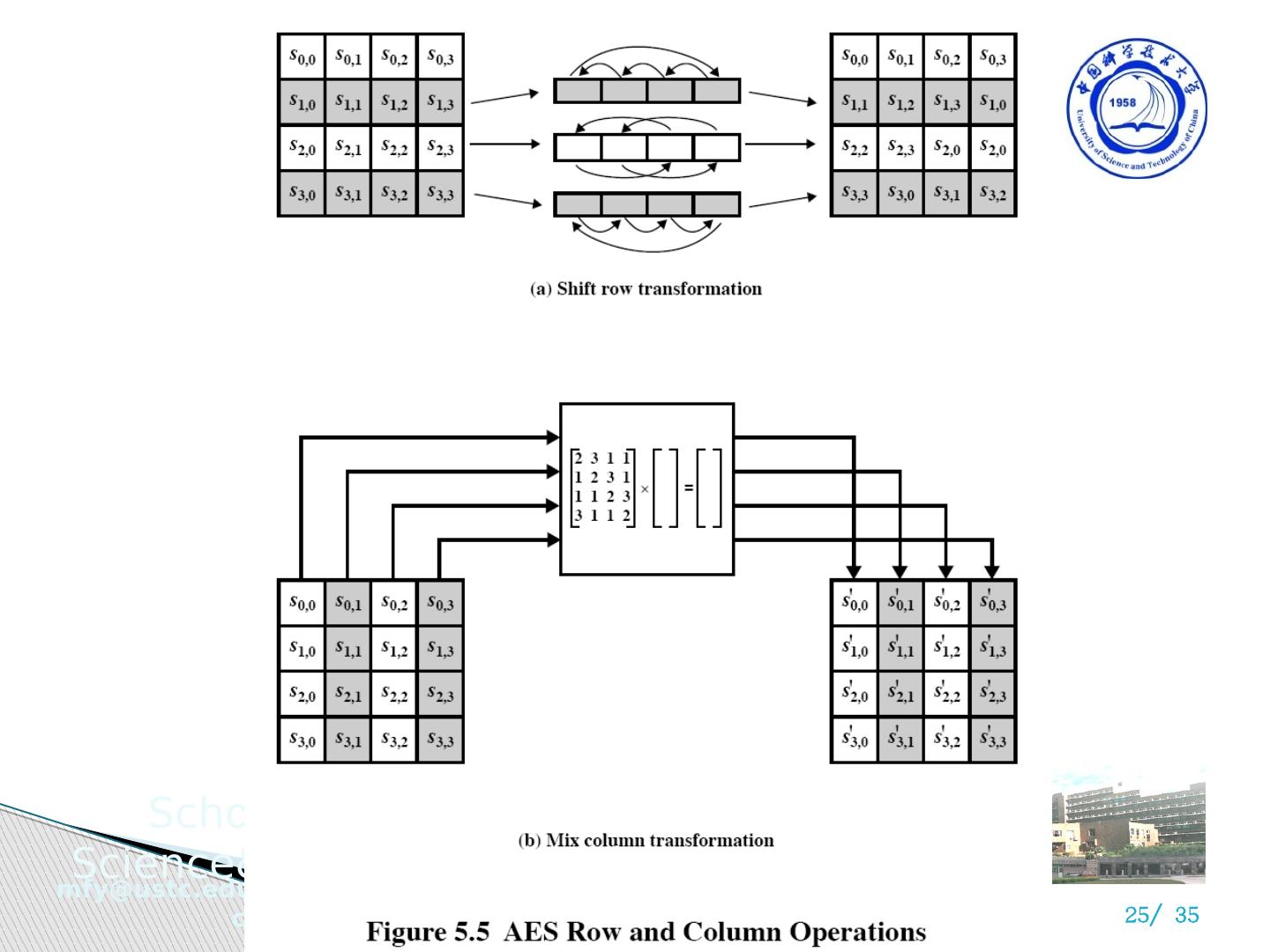
24 .2 ) 行移位变换 A circular byte shift in each 1 st row is unchanged 2 nd row does 1 byte circular shift to left 3 rd row does 2 byte circular shift to left 4 th row does 3 byte circular shift to left Decrypt does shifts to right Since state is processed by columns, this step permutes bytes between the columns
25 .2 ) 行移位变换 A circular byte shift in each 1 st row is unchanged 2 nd row does 1 byte circular shift to left 3 rd row does 2 byte circular shift to left 4 th row does 3 byte circular shift to left Decrypt does shifts to right Since state is processed by columns, this step permutes bytes between the columns
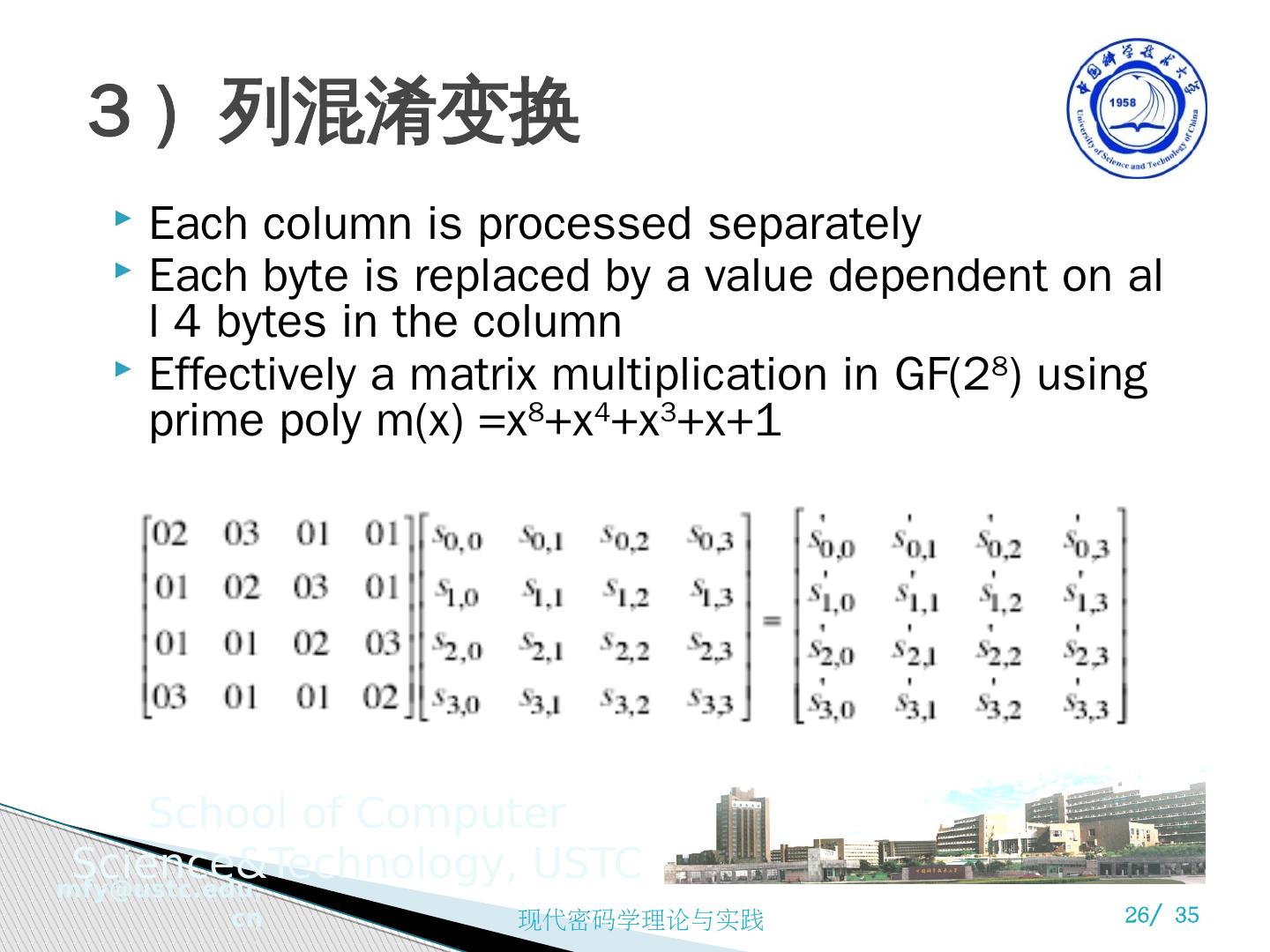
26 .3 ) 列混淆变换 Each column is processed separately Each byte is replaced by a value dependent on all 4 bytes in the column Effectively a matrix multiplication in GF(2 8 ) using prime poly m(x) =x 8 +x 4 +x 3 +x+1
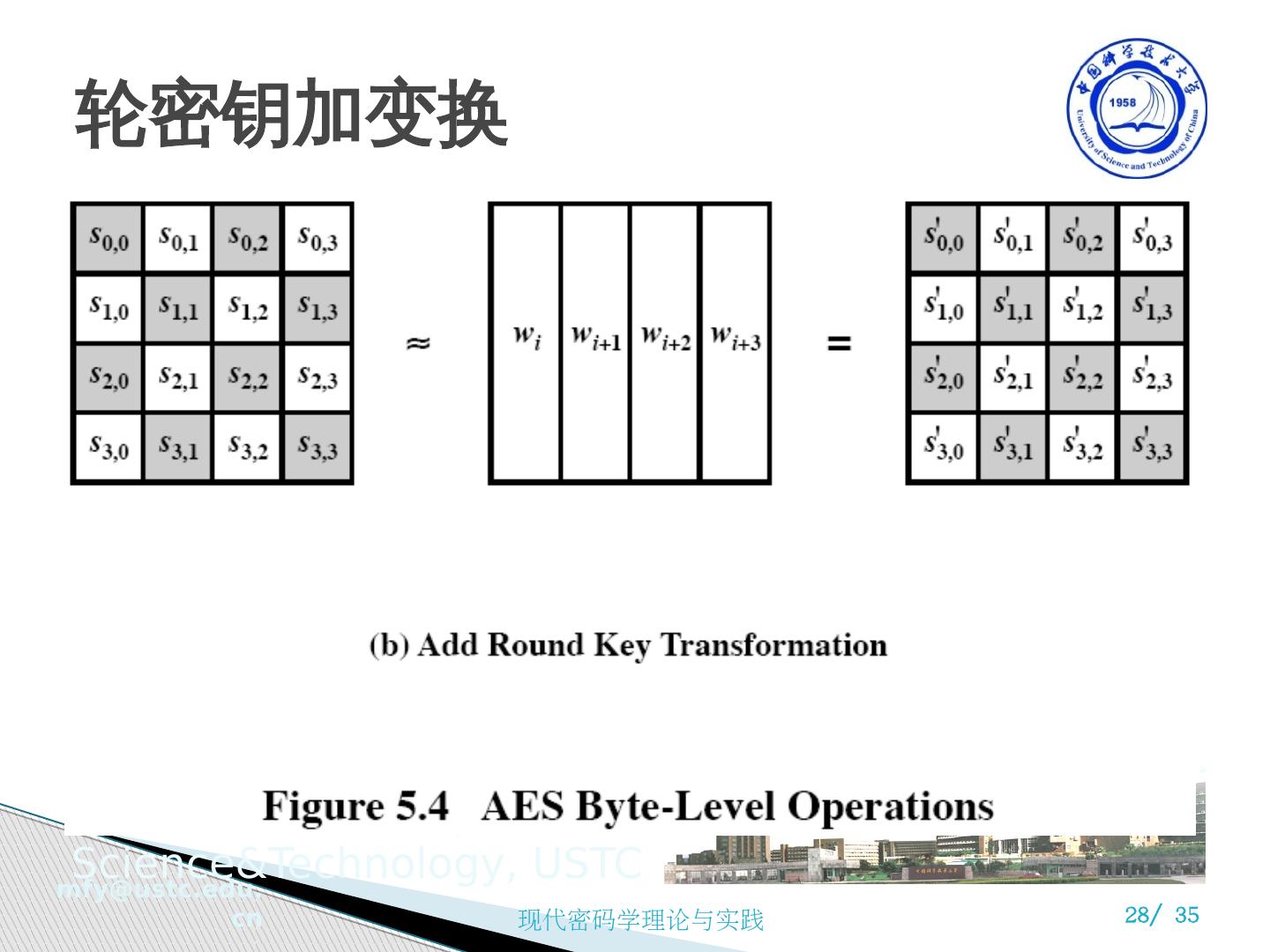
27 .4 ) 轮密钥加变换 XOR state with 128-bits of the round key Again processed by column (though effectively a series of byte operations) Inverse for decryption is identical since XOR is own inverse, just with correct round key Designed to be as simple as possible
28 .轮密钥加变换
29 .5 ) AES 的密钥扩展 Takes 128-bit (16-byte) key and expands into array of 44/52/60 32-bit words Start by copying key into first 4 words Then loop creating words that depend on values in previous & 4 places back in 3 of 4 cases just XOR these together every 4 th has S-box + rotate + XOR constant of previous before XOR together Designed to resist known attacks