- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
18computer and network security--Mobile Device,Platform Security
展开查看详情
1 .Mobile Device and Platform Security John Mitchell CS 155 Spring 2018
2 .Two lectures on mobile security Introduction: platforms and trends Threat categories Physical, platform malware, malicious apps Defense against physical theft Malware threats System architecture and defenses Apple iOS security features and app security model Android security features and app security model Security app development WebView – secure app and web interface dev Device fragmentation Thurs Tues
3 .Mobile computing
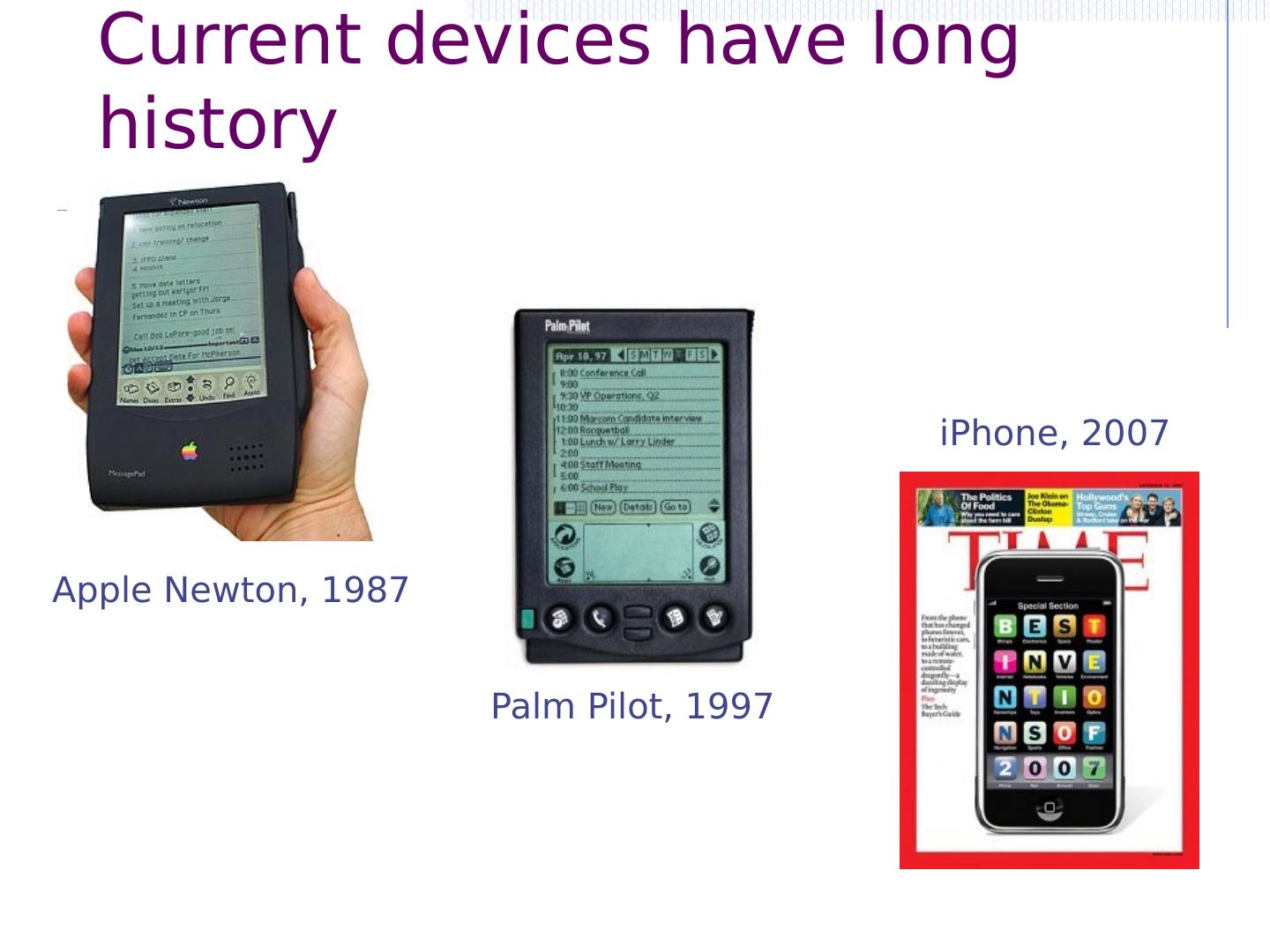
4 .Current devices have long history Apple Newton, 1987 Palm Pilot, 1997 iPhone, 2007
5 .Mobile devices Mainframe -> desktop/server -> mobile/cloud Trends Increasing reliance on personal device Communication, personal data, banking, work Data security, authentication increasingly important From enterprise perspective: BYOD Mobile device management (MDM) to protect enterprise Reliance on cloud: iCloud attack risks, etc Progress from web use to mobile device UI Apps provide custom interface, but limited screen size… System designs draw on best ideas of past
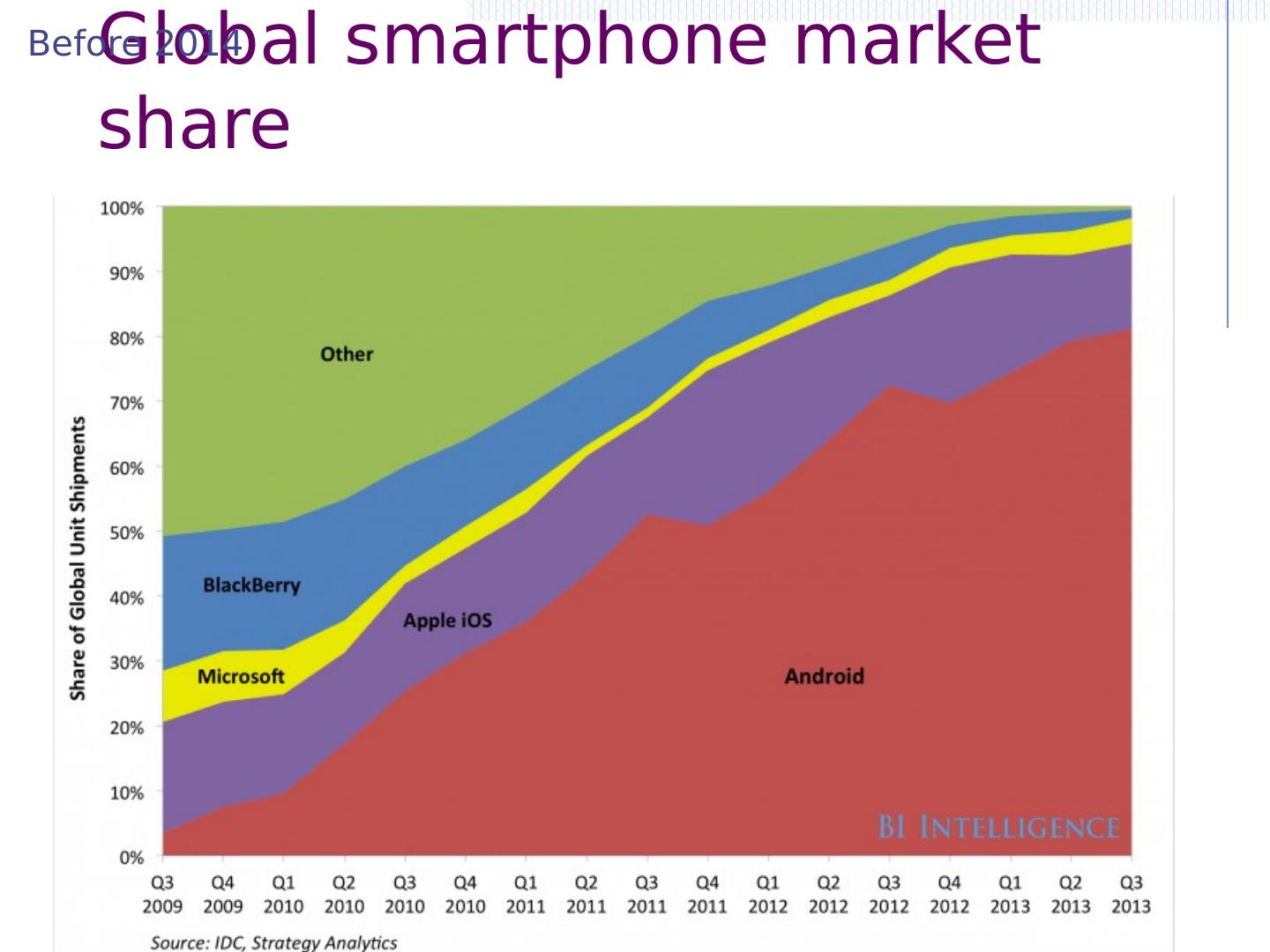
6 .Global smartphone market share Before 2014
7 .Global smartphone market share Since 2014
8 .US Mobile App Traffic http://www.ironpaper.com/webintel/articles/web-design-statistics-2015/
9 .Digital media usage time http://www.ironpaper.com/webintel/articles/web-design-statistics-2017/
10 .Zillions of apps
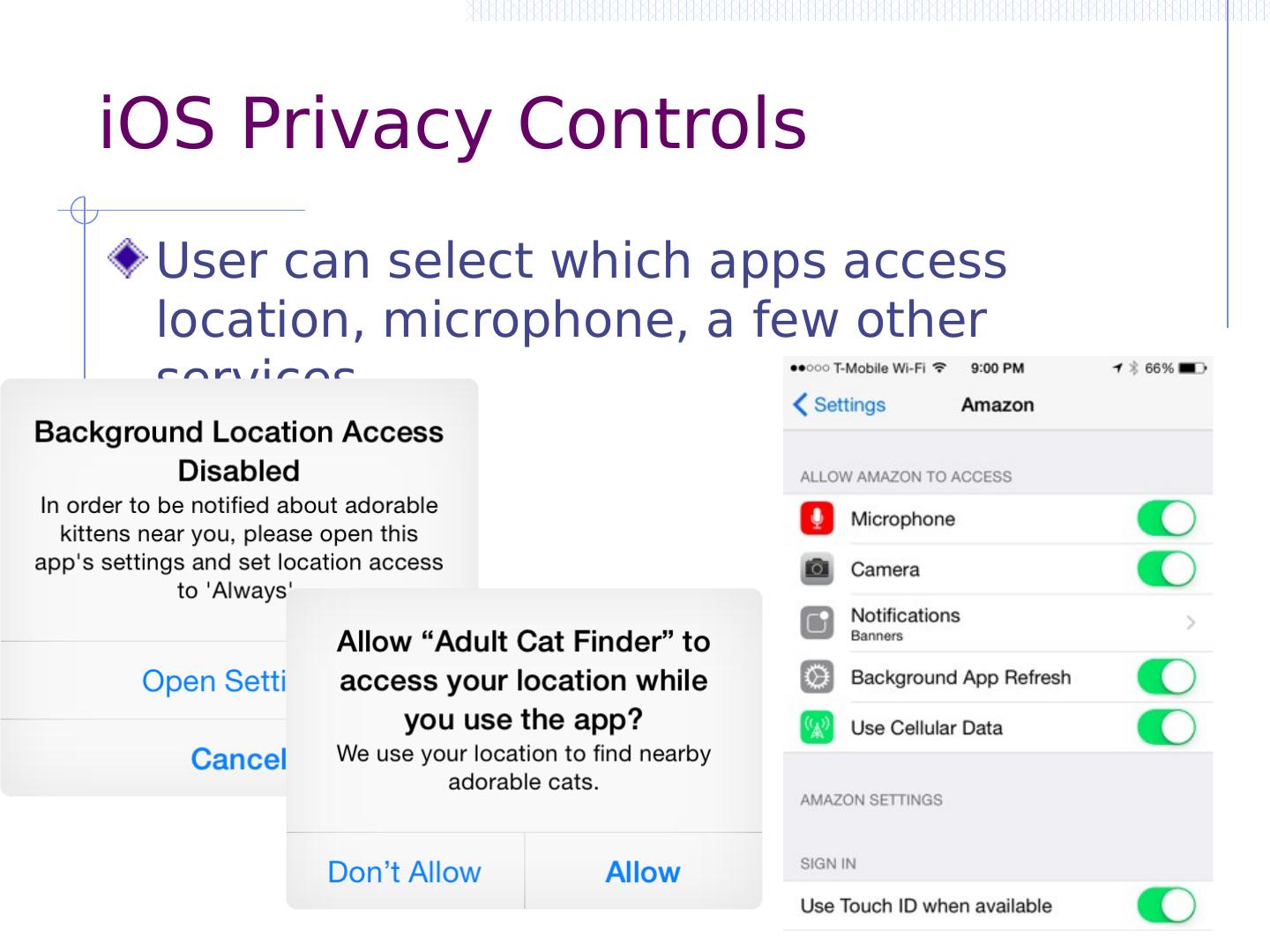
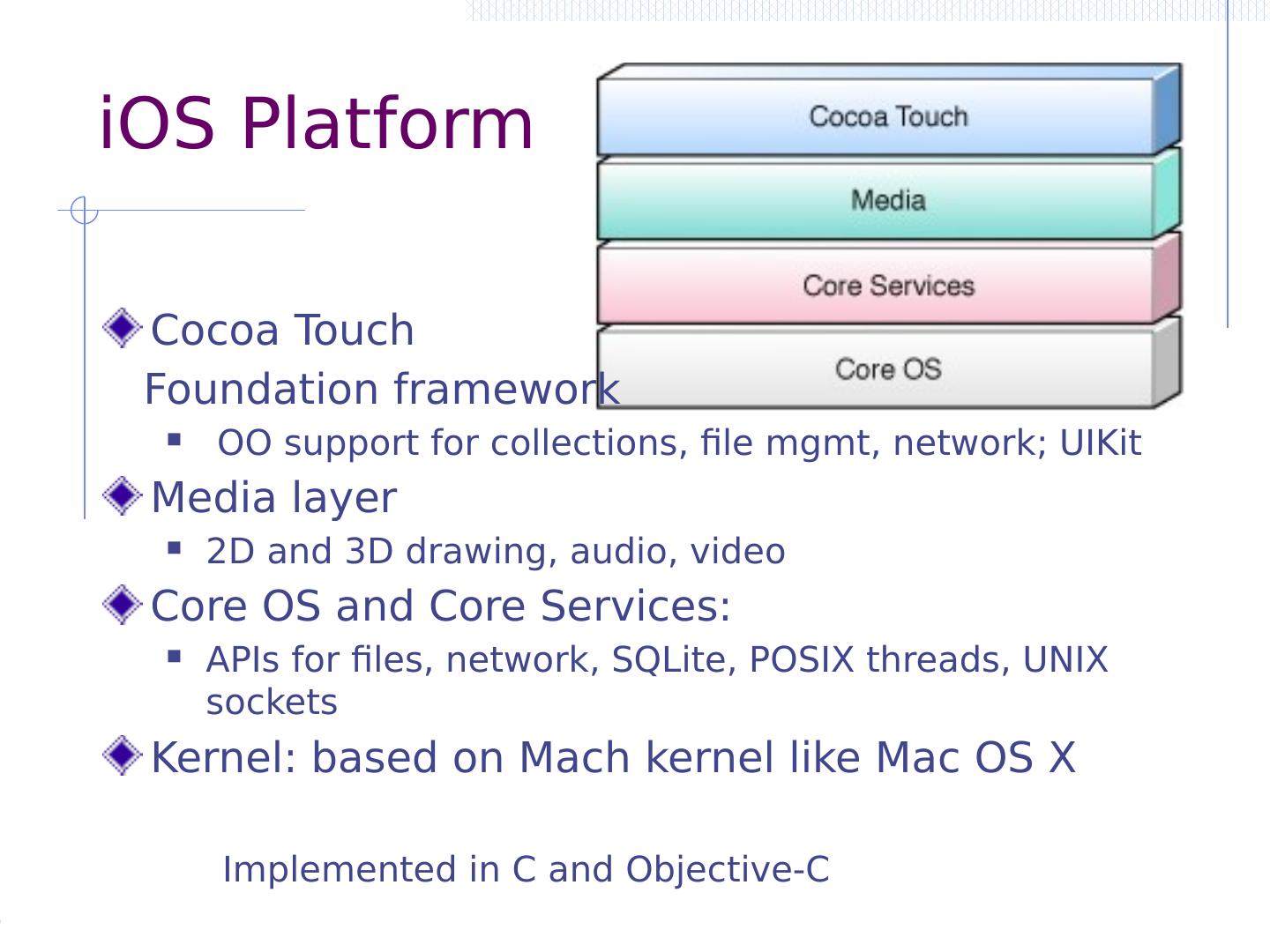
11 .App Marketplace Better protection, isolation than laptop install App review before distribution iOS: Apple manual and automated vetting Android Easier to get app placed on market Transparent automated scanning, removal via Bouncer App isolation and protection Sandboxing and restricted permission Android Permission model Defense against circumvention
12 .Mobile Threats
13 .What’s on your phone? Contact list? Email, messaging, social networking? Banking, financial apps? Pictures, video, …? Music, movies, shows? Location information and history Access to cloud data and services? What would happen if someone picked up your unlocked phone?
14 .Mobile platform threat models Attacker with physical access Try to unlock phone Exploit vulnerabilities to circumvent locking System attacks Exploit vulnerabilities in mobile platform via drive-by web downloads, malformed data, etc. App attacks Use malicious app to steal data, misuse system, hijack other apps
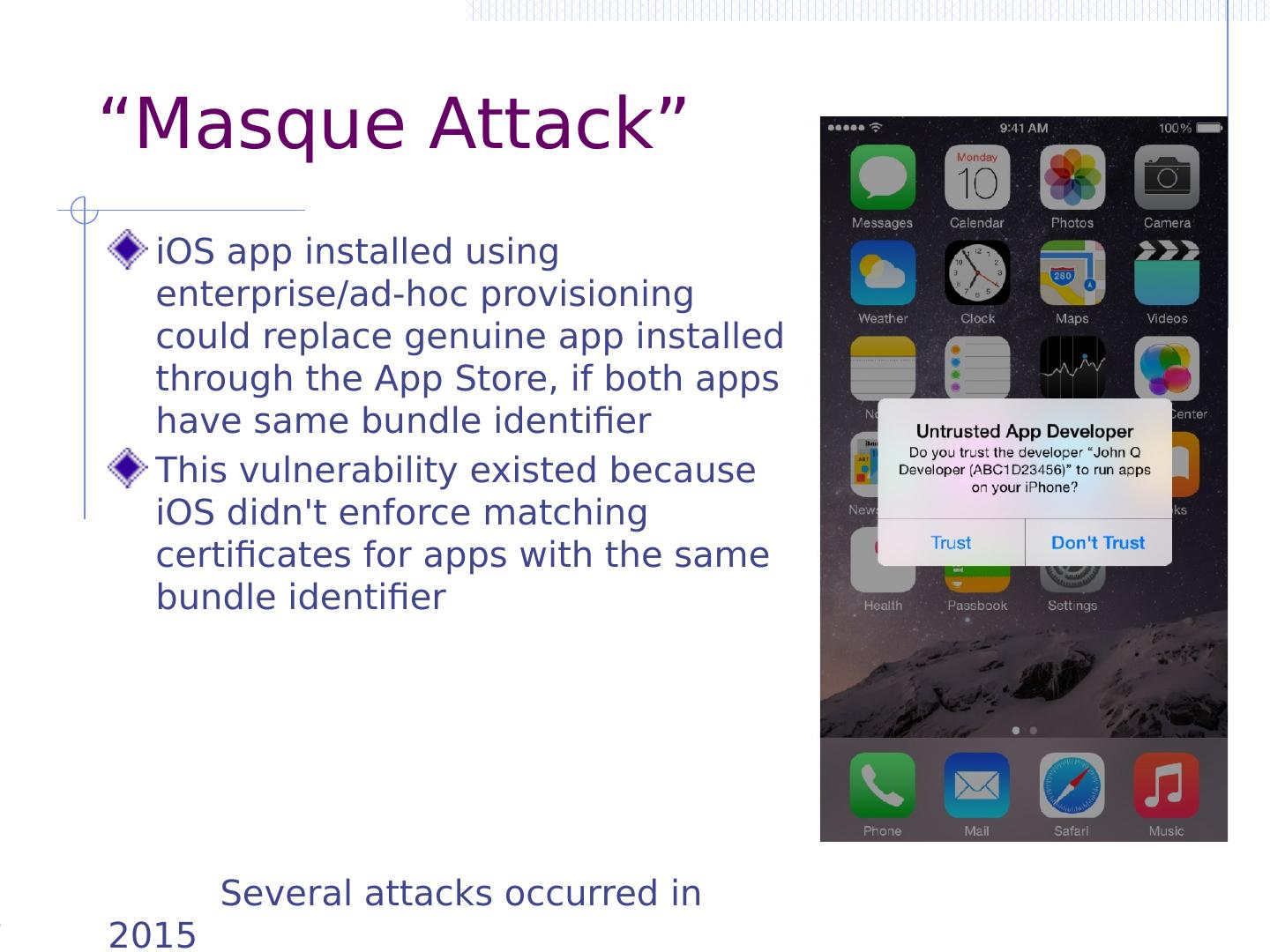
15 .OWASP Mobile Top Ten (final 2016) M1: Improper Platform Usage M2: Insecure Data Storage M3: Insecure Communication M4: Insecure Authentication M5: Insufficient Cryptography M6: Insecure Authorization M7: Client Code Quality M8: Code Tampering M9: Reverse Engineering M10: Extraneous Functionality https://www.owasp.org/index.php/OWASP_Mobile_Security_Project
16 .protection against physical attacker
17 .protection against physical attacker Device locking and unlocking
18 .Today: PINs or Patterns Need PIN or pattern to unlock device Once unlocked all apps are accessible Twist: set a PIN or pattern per app (per photo, video) Protect settings, market, Gmail even if phone unlocked. Examples: App Protector Pro, Seal, Smart lock, … Another twist: Front camera takes picture when wrong PIN entered Example: GotYa
19 .Background: brute force pwd attack Offline attack Traditionally: steal pwd file, try all pwd Unix pwd file has hashed passwords Cannot reverse hash, but can try dictionary hash( pwd , salt) = pwd_file_entry Online attack Can you try all passwords at a web site? What does this mean for phone pin attacks? dictionary
20 .Attacks Smudge attacks [Aviv et al., 2010] Entering pattern leaves smudge that can be detected with proper lighting Smudge survives incidental contact with clothing Potential defense [Moxie 2011] After entering pattern, require user to swipe across Another problem: entropy People choose simple patterns – few strokes At most 1600 patterns with <5 strokes 1 2 3 4 5
21 .Biometric unlocking Biometric unlock: Fingerprint ( Morotola Atrix 4G) Requires backup PIN ⇒ no more secure than PIN Android ICS: Face Unlock Concerns about security Standard biometric security concerns: Not secret and cannot be changed. fingerprint scanner
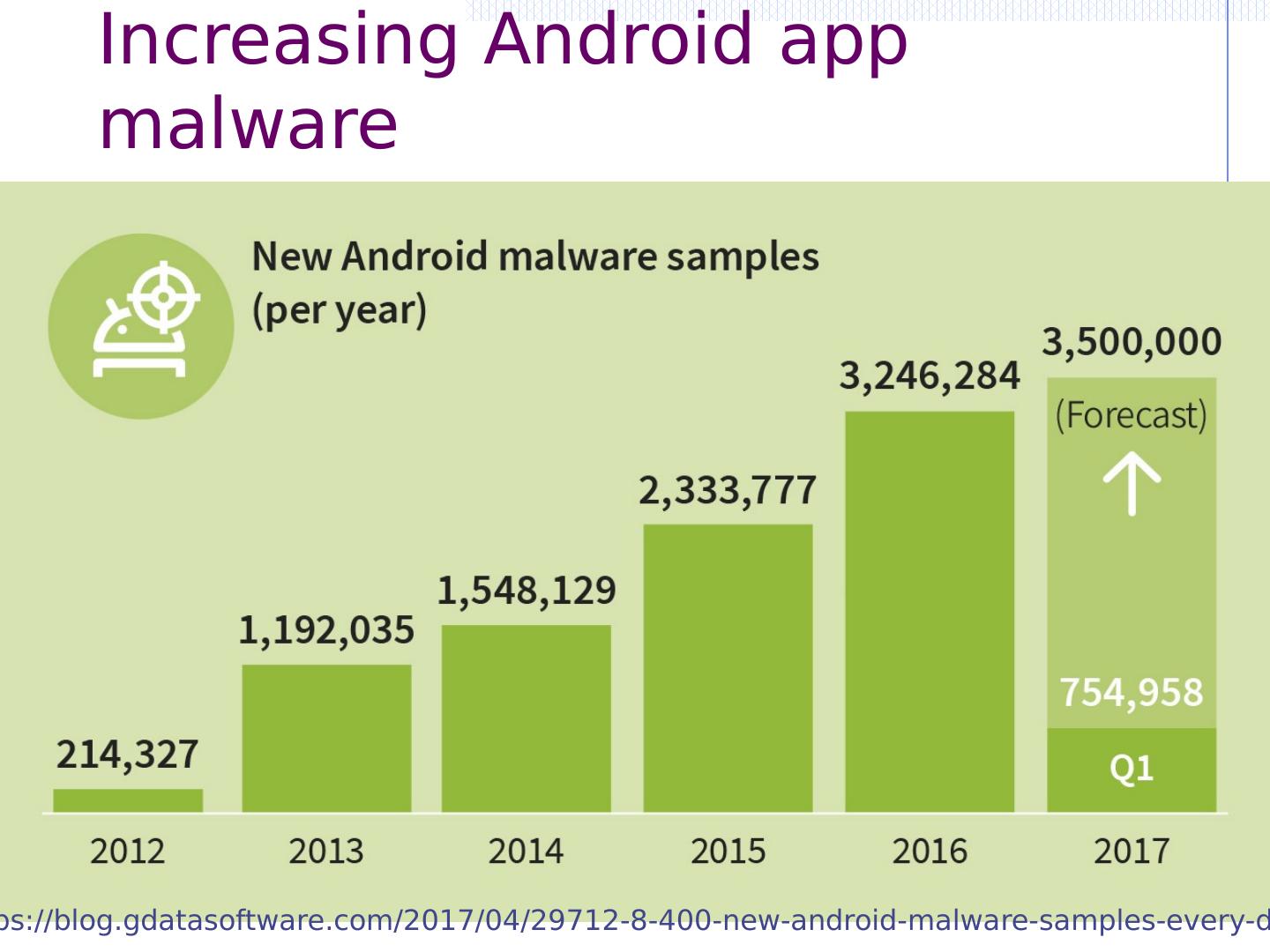
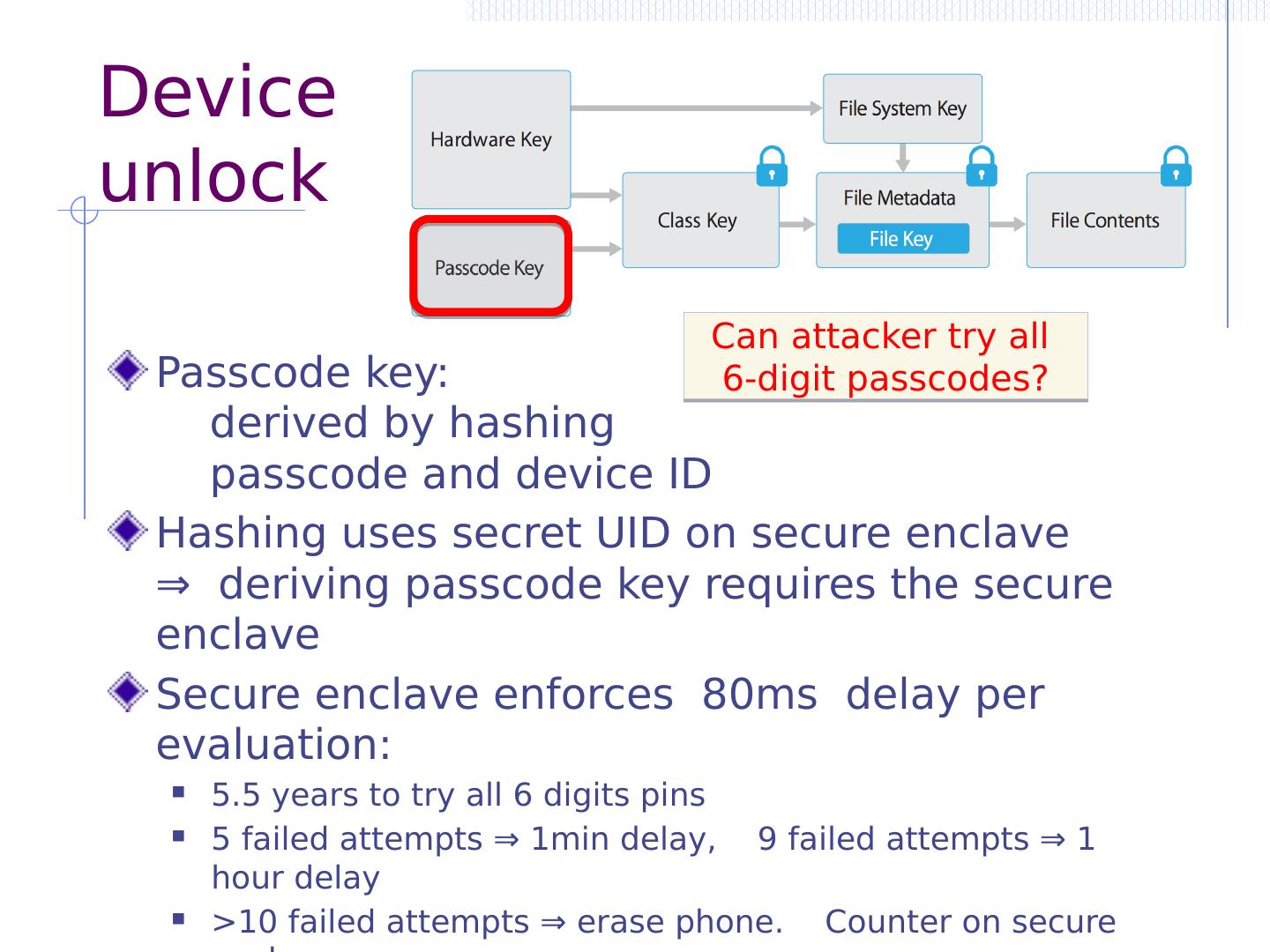
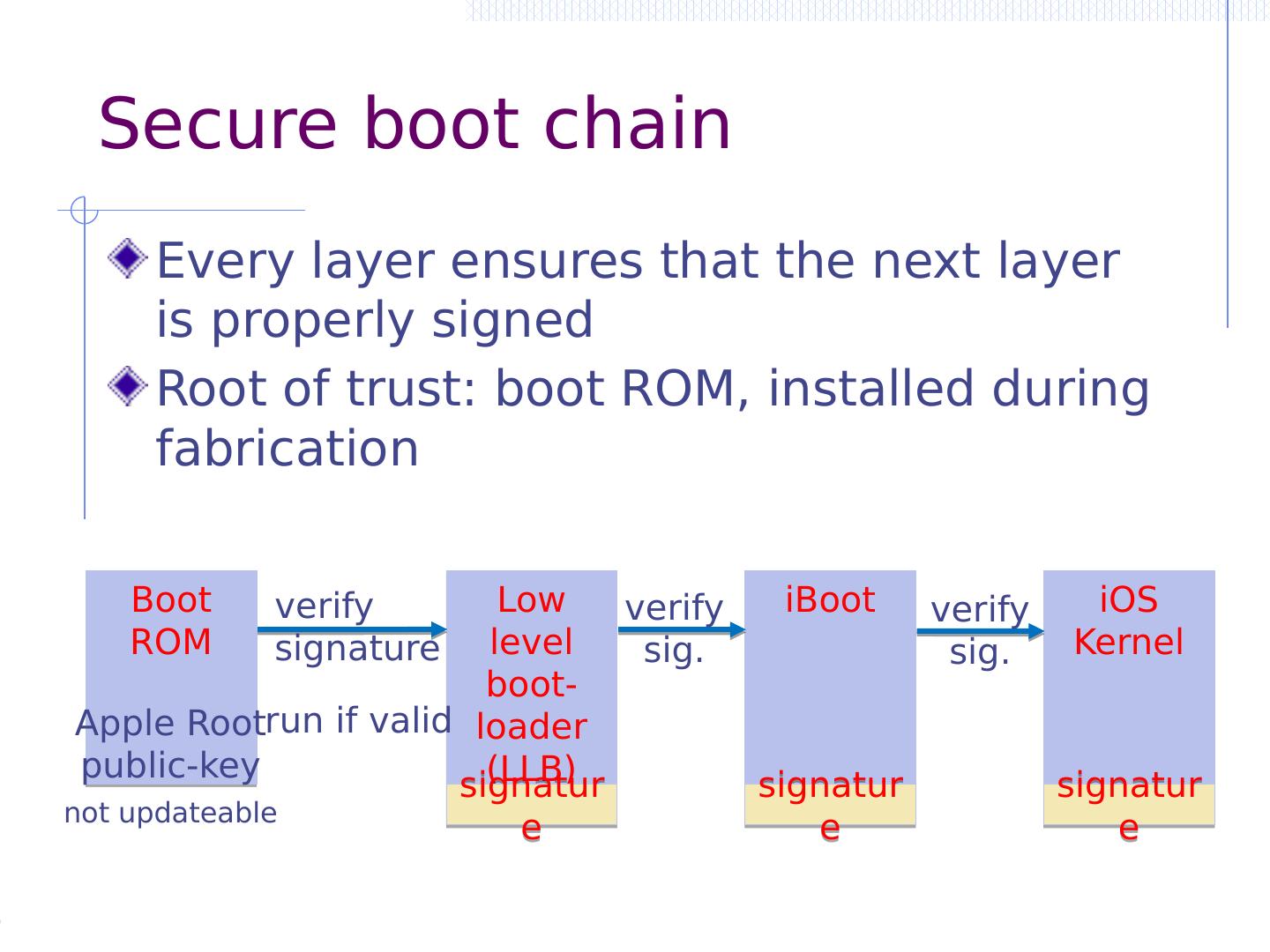
22 .iOS 4.0: PIN brute force attack After device is jail broken, can PIN be extracted? [Needed to read encrypted data partition (later topic)] iOS key management (abstract): Testing 10,000 PINs for each, derive and test class key ≈ 20 mins on iPhone 4 [ Bedrune , Sigwald , 2011] HW UID key (AES key unique to device, cannot extract) | 4 digit PIN | decrypt stored key class key (decrypts keychain) ( code.google.com /p/ iphone-dataprotection )
23 .Better Device Unlocking A more secure approach to unlocking: Unlock phone using a security token on body wrist watch, glasses, clothing Requirements Cheap token, should not require charging
24 .Summary: locking and unlocking Protect from thief via user authentication Commonly: pin, swipe, etc. Future: Biometric? Token on body? Can phone destroy itself if too many tries? Physical access can allow Thief to jailbreak and crack password/pin Subject phone to other attacks Next defense: erase phone when stolen
25 .protection against physical attacker Mobile device management (MDM)
26 .MDM:Mobile Device Management Manage mobile devices across organization Consists of central server and client-side software Functions: Diagnostics, repair, and update Backup/restore Policy enforcement (e.g. only allowed apps) Remote lock and wipe GPS tracking
27 .MDM Sample Deployment MDM enterprise server policy file user’s phone enrollment push notification to request check in HTTPS connection to report status and receive instructions configure, query, lock, wipe, … server cert User consent
28 .Summary: mobile device mgmt Protect stolen phone from thief GPS: where’s my phone? Device wipe Preventing brute force attacks Phone can “lock” if too many bad pin tries Use MDM to reset to allow user pin Backup, backup, backup! Frequent backup makes auto-wipe possible
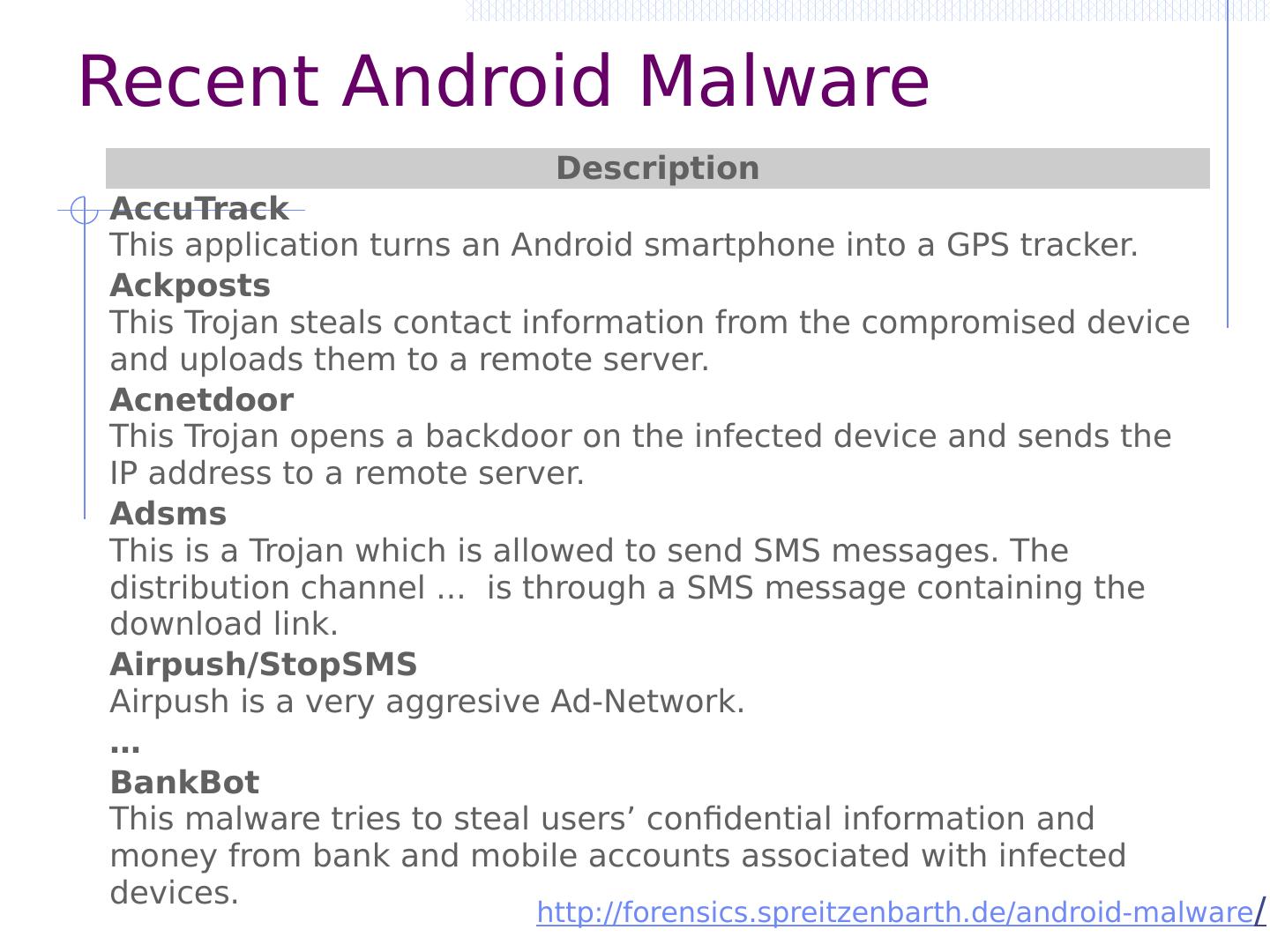
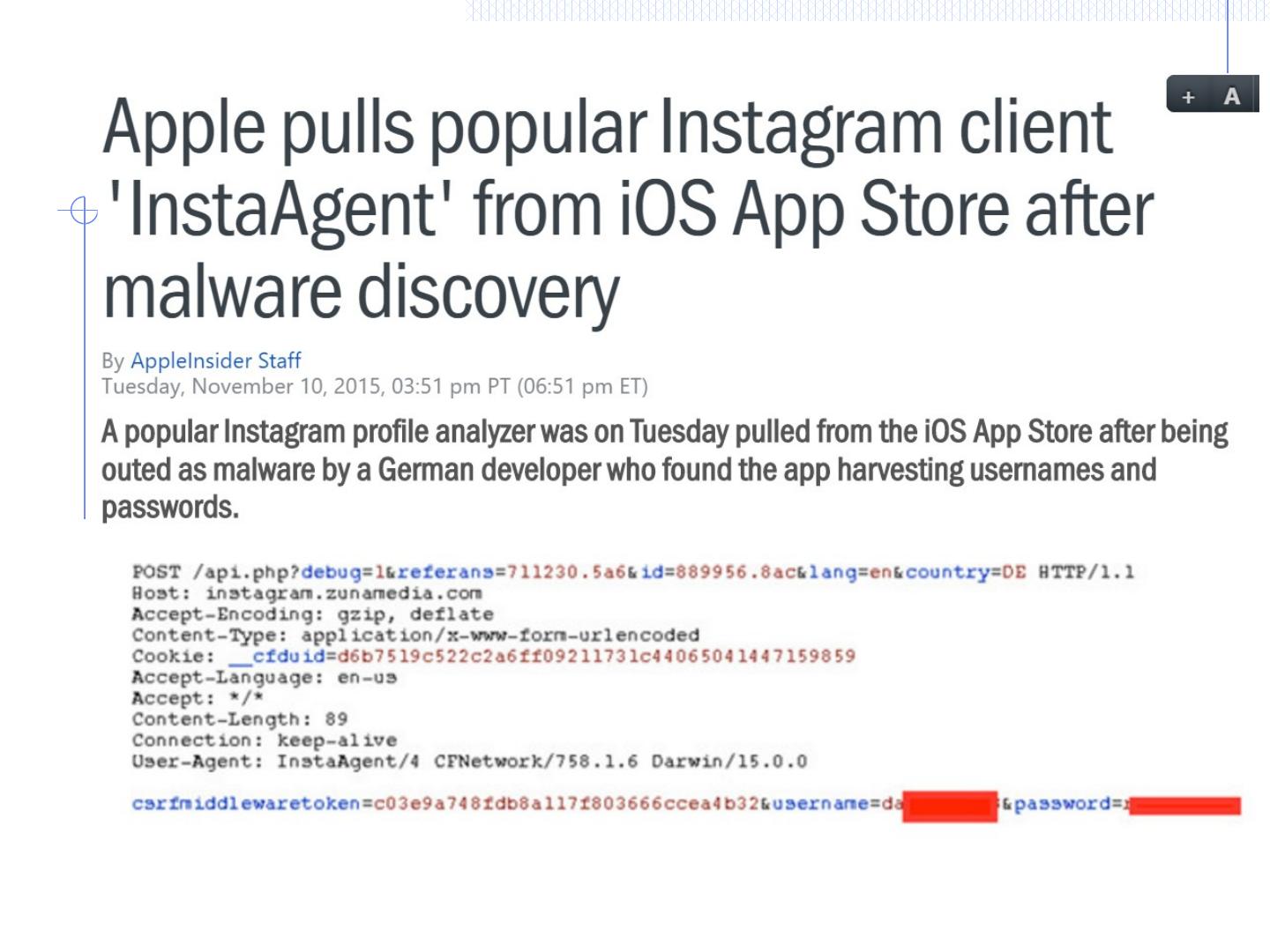
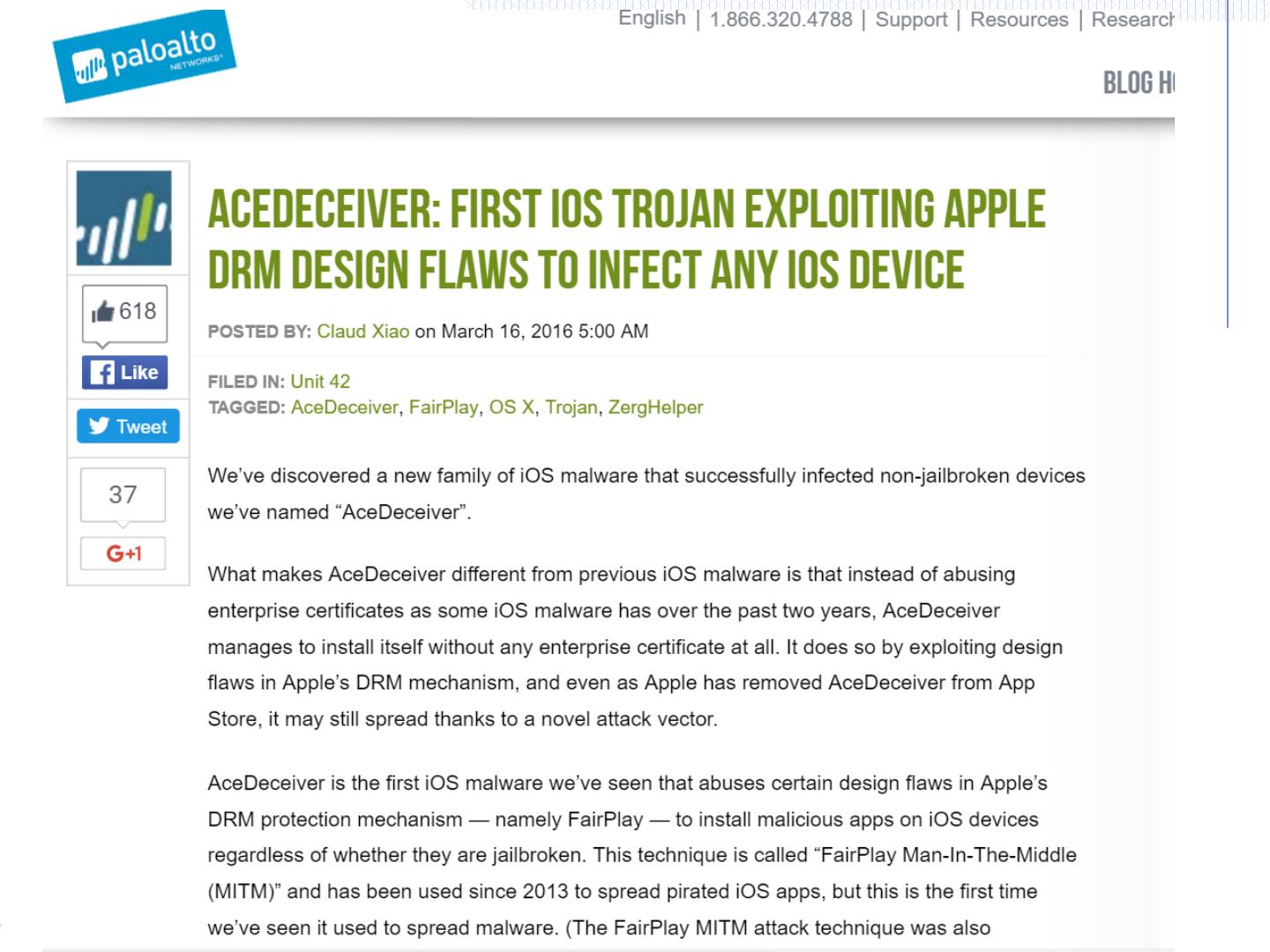
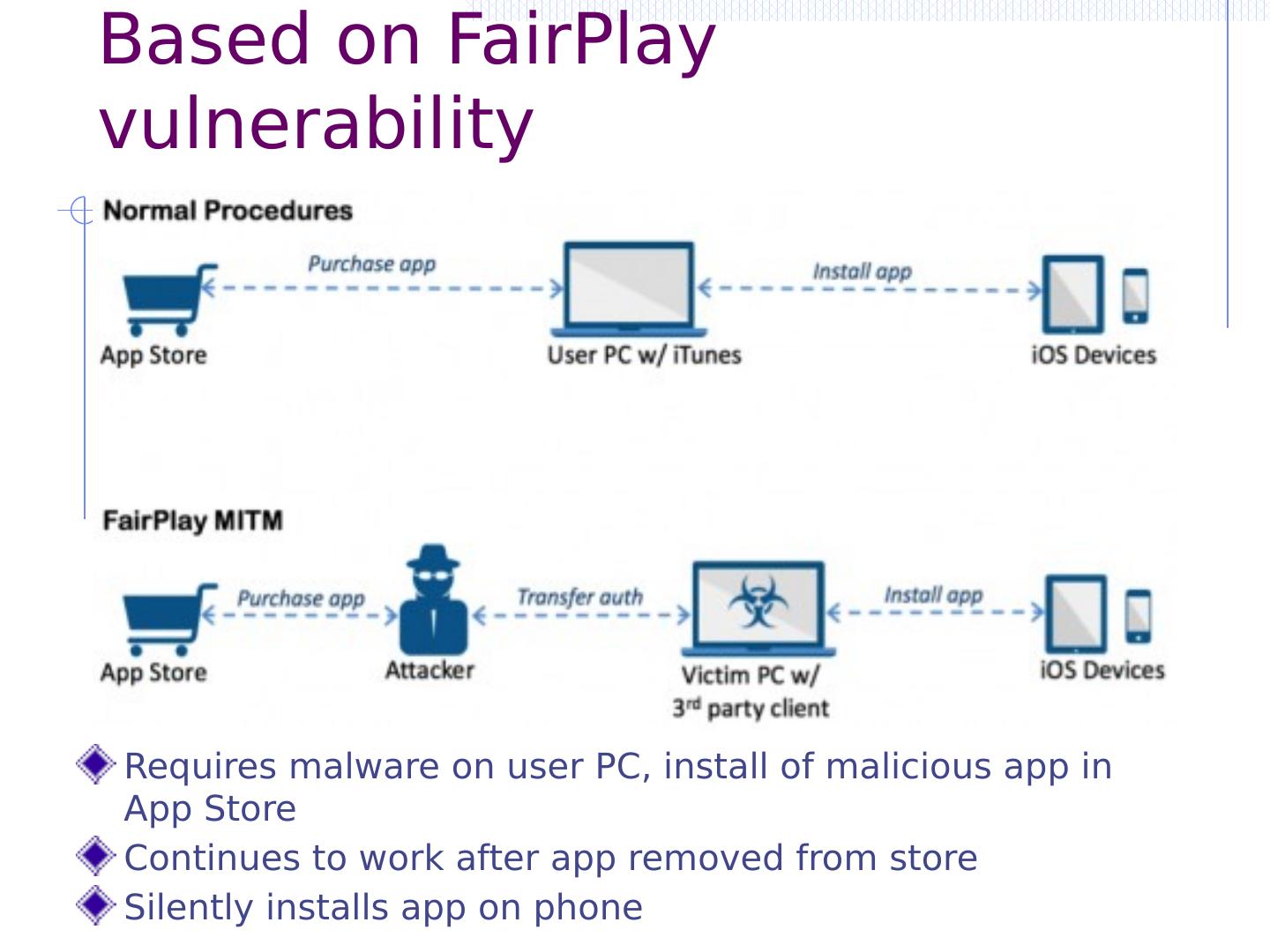
29 .Malware attacks