- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
10computer and network security-Session Management
展开查看详情
1 . Session Management John Mitchell (based on Dan’s previous slides) CS 155 Spring 2018 Web Security
2 .Outline Cookie fundamentals Cookie policy: setting and retrieving cookies Cookie protocol problems Web session management Session state and authentication Session hijacking Token stealing Session fixation
3 .Cookies: client state Review from Lecture 8 3
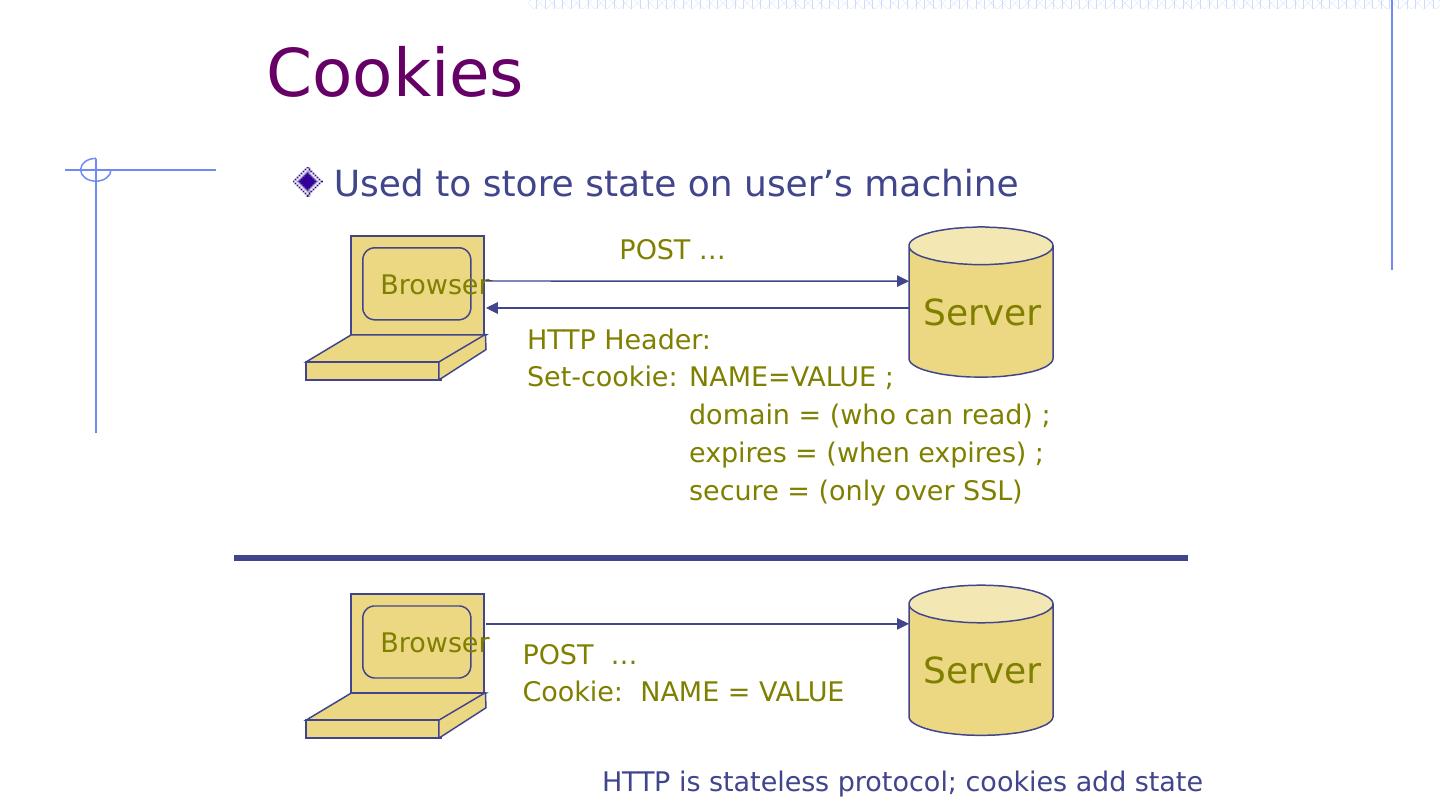
4 .Cookies Used to store state on user’s machine Browser Server POST … HTTP Header: Set-cookie: NAME=VALUE ; domain = (who can read) ; expires = (when expires) ; secure = (only over SSL) Browser Server POST … Cookie: NAME = VALUE HTTP is stateless protocol; cookies add state
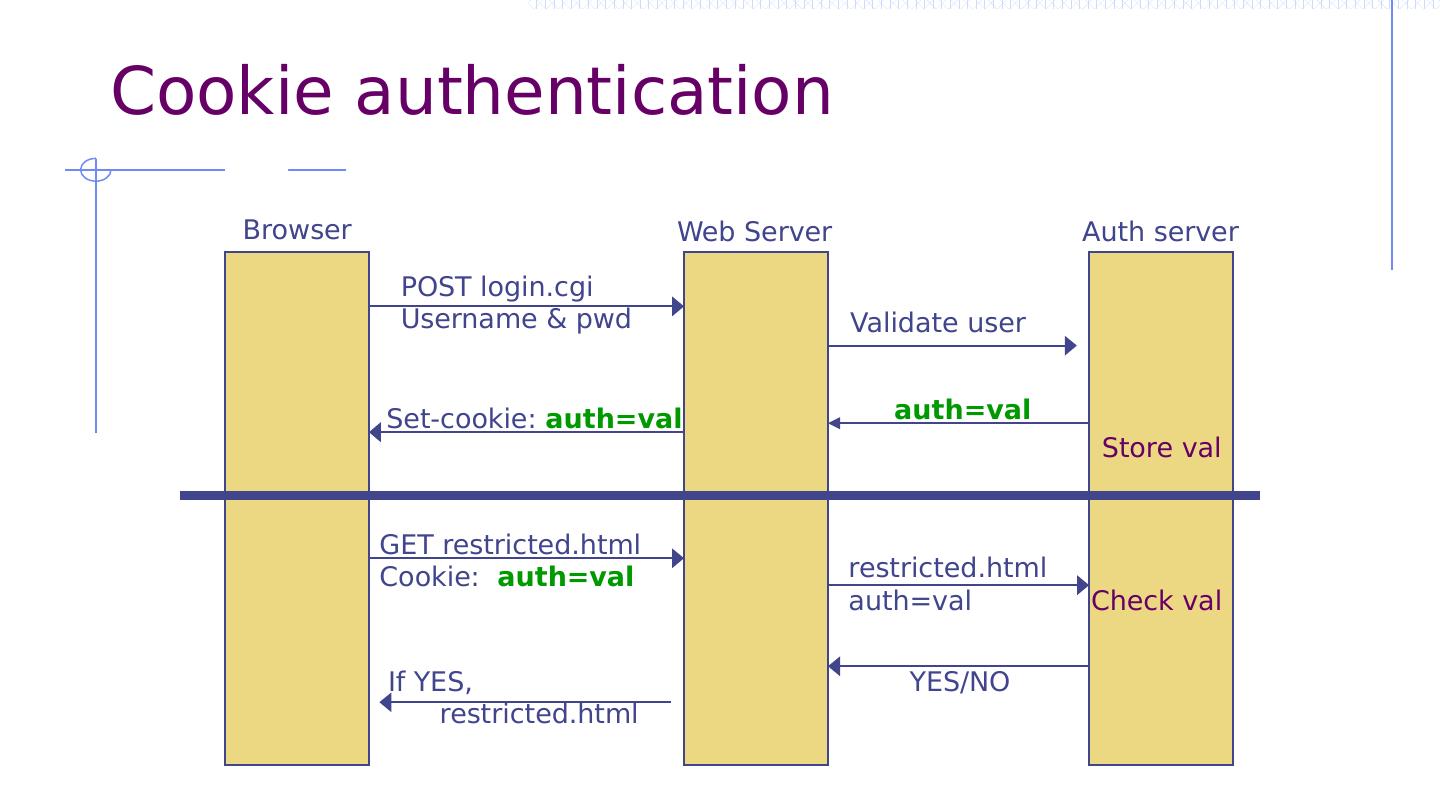
5 .Cookie authentication Browser Web Server Auth server POST login.cgi Username & pwd Validate user auth=val Store val Set-cookie: auth=val GET restricted.html Cookie: auth=val restricted.html auth=val YES/NO If YES, restricted.html Check val
6 .Cookie authentication Browser Web Server Auth server POST login.cgi Username & pwd Validate user auth=val Store val Set-cookie: auth=val GET restricted.html Cookie: auth=val restricted.html auth=val YES/NO If YES, restricted.html Check val
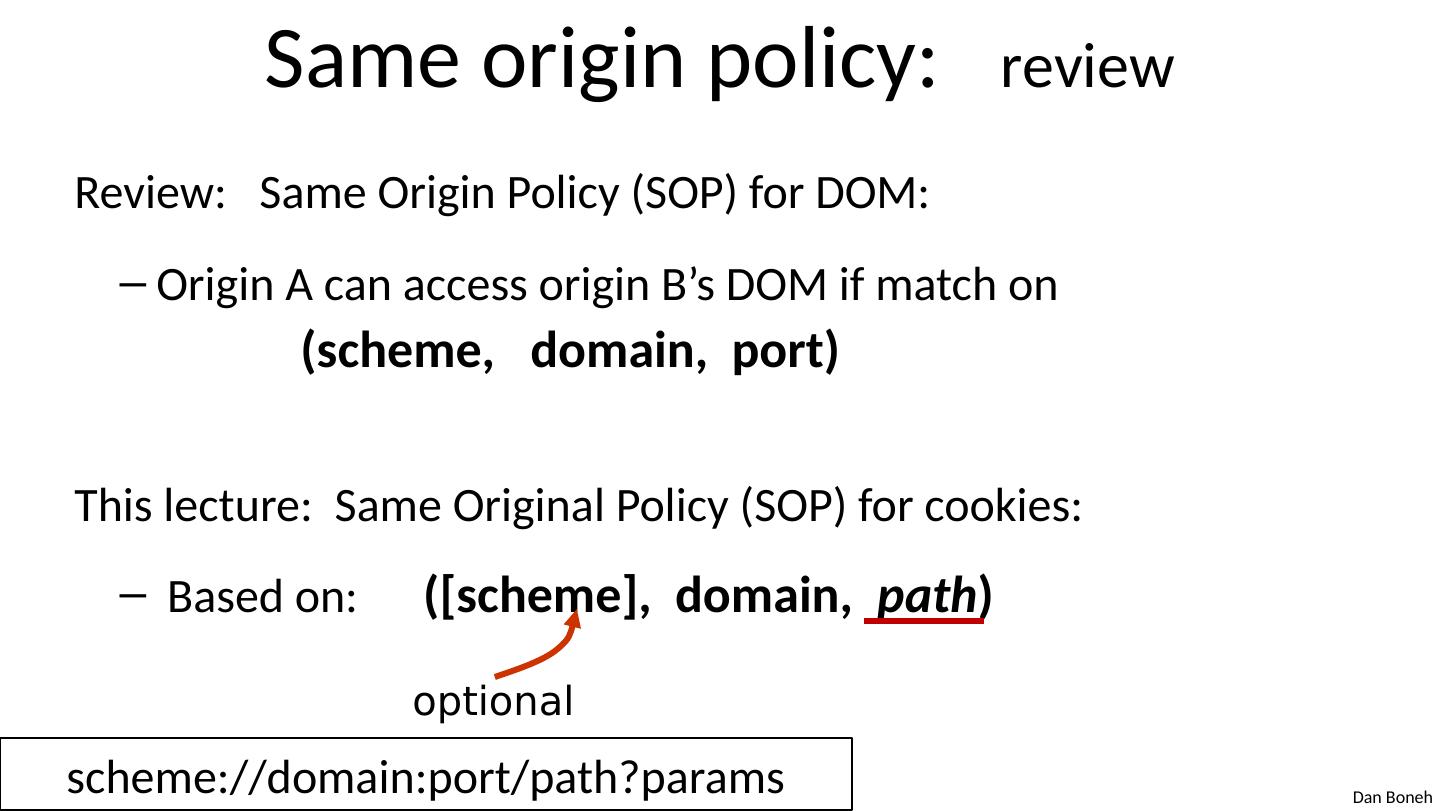
7 .Same origin policy: review Review: Same Origin Policy (SOP) for DOM: Origin A can access origin B’ s DOM if match on (scheme, domain, port) This lecture: Same Original Policy (SOP) for cookies: Based on: ([scheme], domain, path ) optional scheme://domain:port/path?params
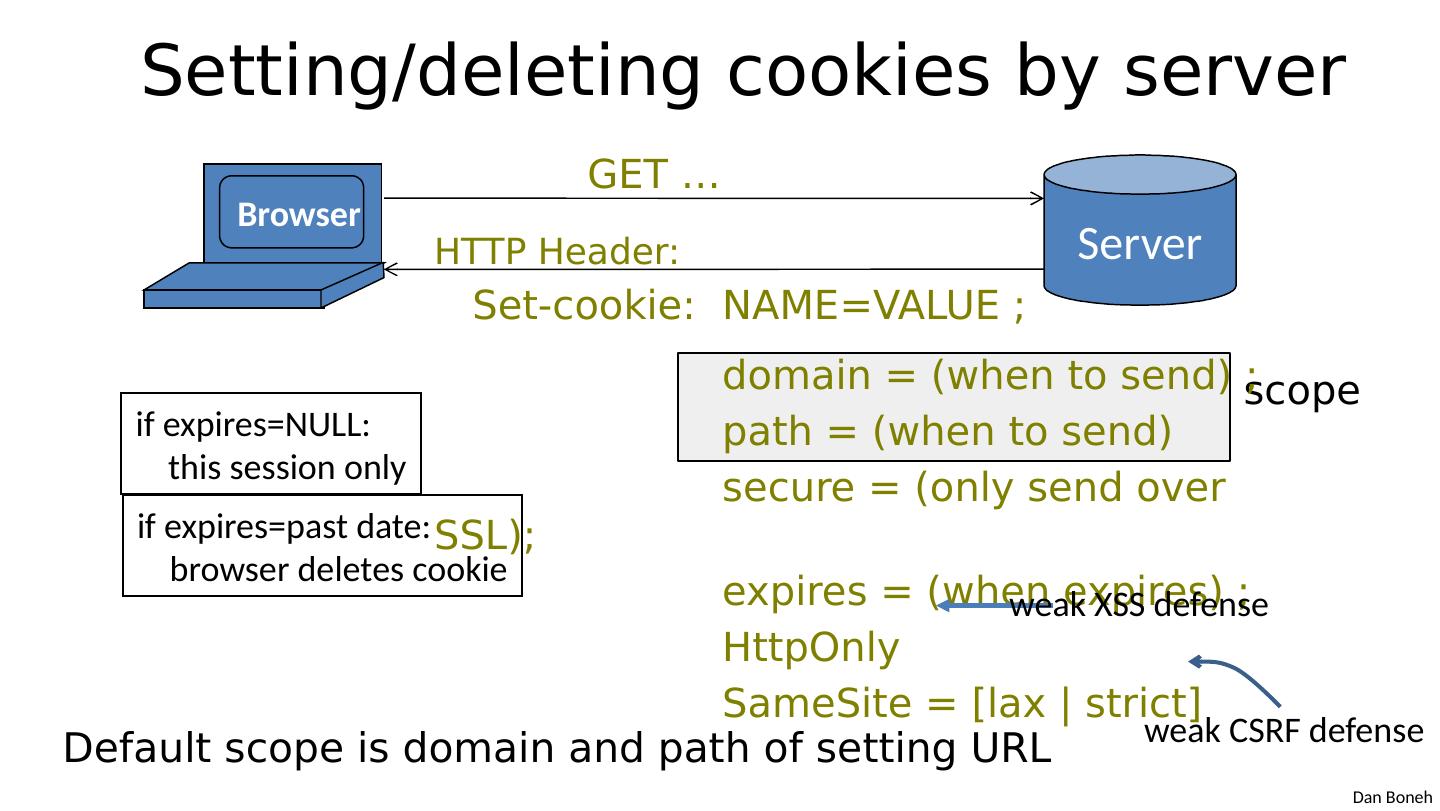
8 .scope Setting/deleting cookies by server Default scope is domain and path of setting URL Browser Server GET … HTTP Header: Set-cookie: NAME=VALUE ; domain = (when to send) ; path = (when to send) secure = (only send over SSL); expires = (when expires) ; HttpOnly SameSite = [lax | strict] if expires=NULL: this session only if expires= past date : browser deletes cookie weak XSS defense weak CSRF defense
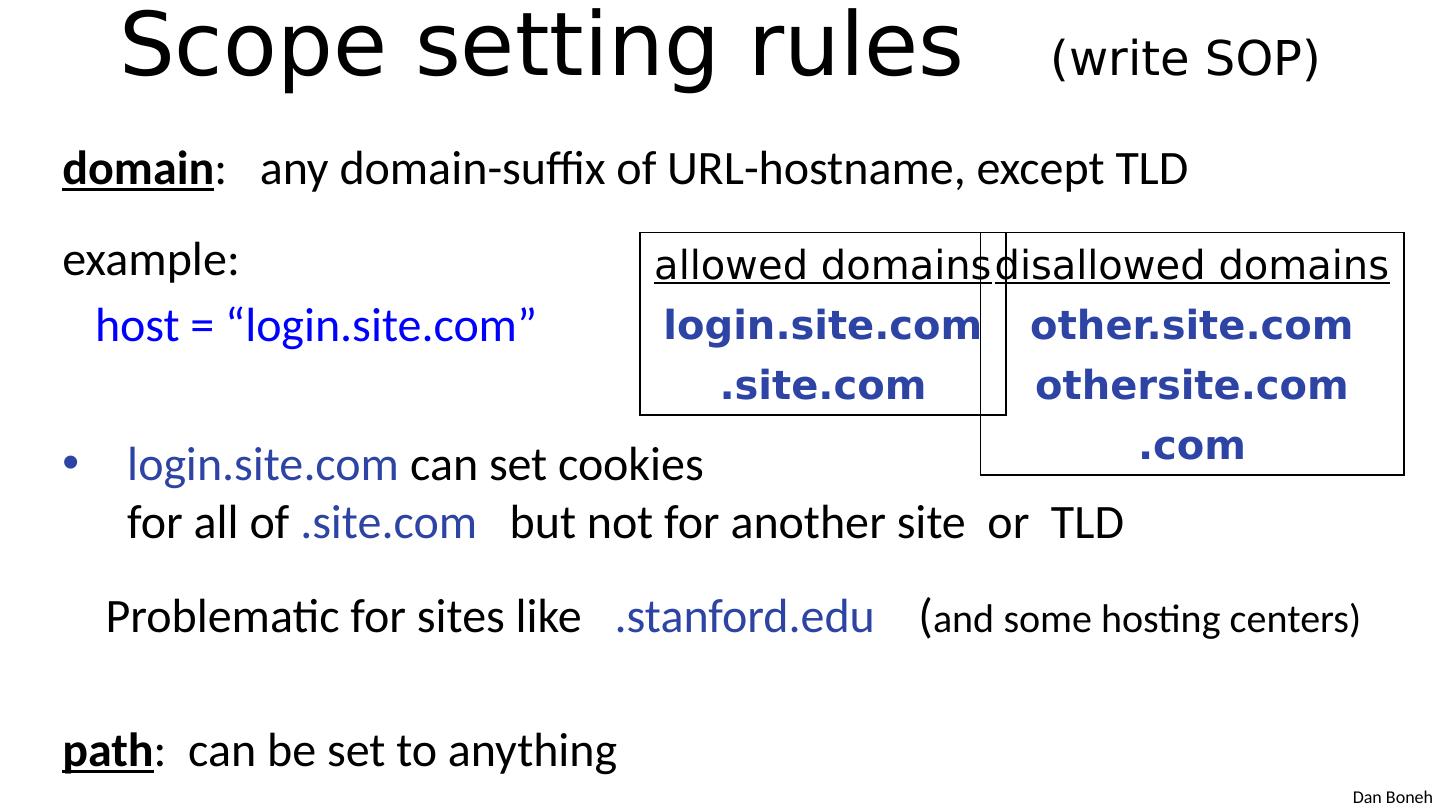
9 .Scope setting rules (write SOP) domain : any domain-suffix of URL-hostname, except TLD example: host = “ login.site.com ” login.site.com can set cookies for all of . site.com but not for another site or TLD Problematic for sites like .stanford.edu ( and some hosting centers) path : can be set to anything allowed domains login.site.com . site.com disallowed domains other.site.com othersite.com .com
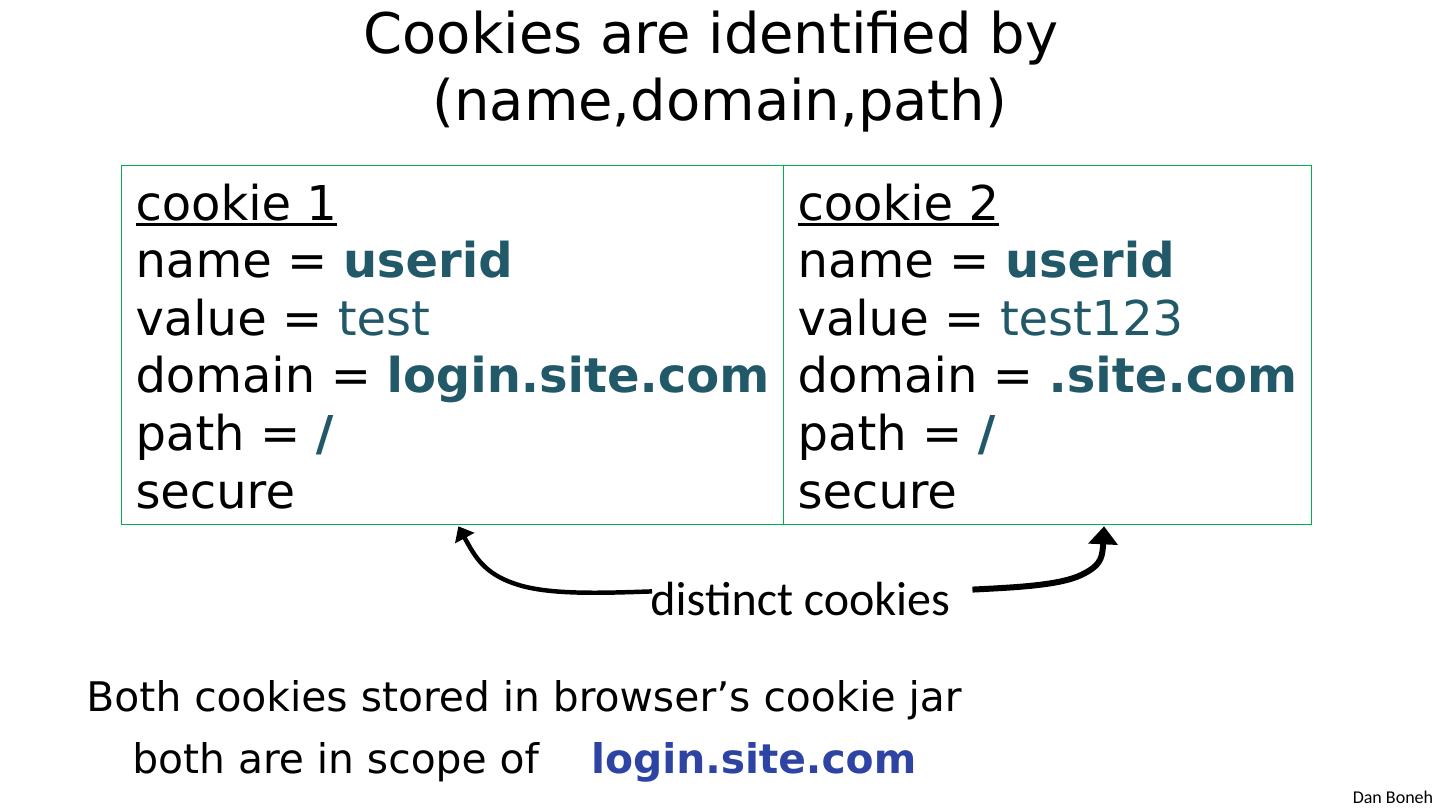
10 .Cookies are identified by (name,domain,path) Both cookies stored in browser’ s cookie jar both are in scope of login.site.com cookie 1 name = userid value = test domain = login.site.com path = / secure cookie 2 name = userid value = test123 domain = . site.com path = / secure distinct cookies
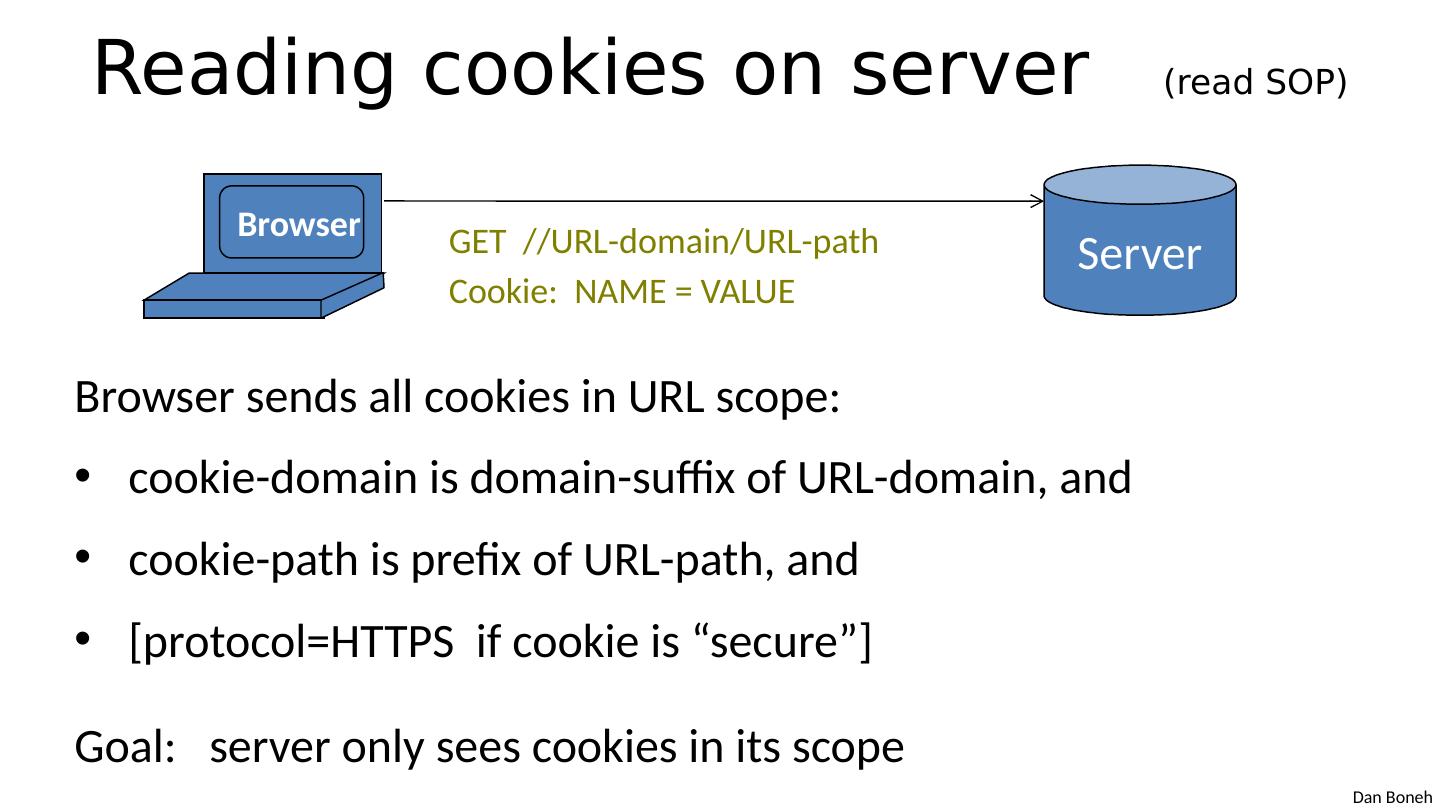
11 .Reading cookies on server (read SOP) Browser sends all cookies in URL scope: cookie-domain is domain-suffix of URL-domain, and cookie-path is prefix of URL-path, and [protocol=HTTPS if cookie is “ secure ” ] Goal: server only sees cookies in its scope Browser Server GET //URL-domain/URL-path Cookie: NAME = VALUE
12 .Examples http:// checkout.site.com / http:// login.site.com / https:// login.site.com / cookie 1 name = userid value = u1 domain = login.site.com path = / secure cookie 2 name = userid value = u2 domain = . site.com path = / non-secure both set by login.site.com cookie: userid =u2 cookie: userid =u2 cookie: userid =u1; userid =u2
13 .Client side read/write: document.cookie Setting a cookie in Javascript : document.cookie = “ name=value; expires=…; ” Reading a cookie : alert( document.cookie ) prints string containing all cookies available for document (based on [protocol], domain, path) Deleting a cookie : document.cookie = “ name=; expires= Thu, 01-Jan-70 ” HttpOnly cookies: not included in document.cookie
14 .javascript: alert( document.cookie ) Javascript URL Displays all cookies for current document
15 .Viewing/deleting cookies in Browser UI
16 .Viewing/deleting cookies in Browser UI
17 .Cookie protocol problems Server is blind: Does not see cookie attributes (e.g. secure, HttpOnly ) Does not see which domain set the cookie Server only sees: Cookie: NAME=VALUE
18 .Example 1: login server problems Alice logs in at login.site.com login.site.com sets session-id cookie for . site.com 2. Alice visits evil.site.com overwrites . site.com session-id cookie with session-id of user “ badguy ” 3. Alice visits course.site.com to submit homework course.site.com thinks it is talking to “ badguy ” Problem: course.site.com expects session-id from login.site.com ; cannot tell that session-id cookie was overwritten
19 .Example 2: “ secure ” cookies are not secure Alice logs in at https :// accounts.google.com Alice visits http :// www.google.com (cleartext) Network attacker can inject into response Set-Cookie: SSID= badguy ; secure and overwrite secure cookie Problem: network attacker can re-write HTTPS cookies ! HTTPS cookie value cannot be trusted set-cookie: SSID =A7_ESAgDpKYk5TGnf; Domain=.google.com; Path=/ ; Expires=Wed, 09-Mar-2026 18:35:11 GMT; Secure; HttpOnly set-cookie: SAPISID =wj1gYKLFy-RmWybP/ANtKMtPIHNambvdI4; Domain=. google.com;Path =/ ; Expires=Wed, 09-Mar-2026 18:35:11 GMT; Secure
20 .Interaction with the DOM SOP Cookie SOP path separation: x.com /A does not see cookies of x.com /B Not a security measure: x.com /A has access to DOM of x.com /B < iframe src =“ x.com /B"></ iframe > a lert(frames[0]. document.cookie ); Path separation is done for efficiency not security: x.com /A is only sent the cookies it needs
21 .Cookies have no integrity User can change and delete cookie values Edit cookie database (FF: cookies.sqlite ) Modify Cookie header (FF: TamperData extension) Silly example: shopping cart software Set-cookie: shopping-cart-total = 150 ($) User edits cookie file (cookie poisoning): Cookie: shopping-cart-total = 15 ($) Similar problem with hidden fields <INPUT TYPE= “ hidden ” NAME=price VALUE= “ 150 ” > 21
22 .22 Not so silly … (old) D3.COM Pty Ltd: ShopFactory 5.8 @Retail Corporation: @Retail Adgrafix : Check It Out Baron Consulting Group: WebSite Tool ComCity Corporation: SalesCart Crested Butte Software: EasyCart Dansie.net : Dansie Shopping Cart Intelligent Vending Systems: Intellivend Make-a-Store: Make-a-Store OrderPage McMurtrey /Whitaker & Associates: Cart32 3.0 pknutsen@nethut.no : CartMan 1.04 Rich Media Technologies: JustAddCommerce 5.0 SmartCart : SmartCart Web Express: Shoptron 1.2 Source: http://xforce.iss.net/xforce/xfdb/4621
23 .Solution: cryptographic checksums Binding to session-id (SID) makes it harder to replay old cookies Goal: data integrity Requires server-side secret key k unknown to browser Browser Server k Set-Cookie: NAME = value T Cookie: NAME = value T Generate tag: T ⟵ MACsign (k, SID ll name ll value ) Verify tag: MACverify ( k, SID ll name ll value, T )
24 .24 Example: ASP.NET System.Web.Configuration.MachineKey Secret web server key intended for cookie protection Creating an encrypted cookie with integrity: HttpCookie cookie = new HttpCookie ( name , val ); HttpCookie encodedCookie = HttpSecureCookie.Encode ( cookie ); Decrypting and validating an encrypted cookie: HttpSecureCookie . De code ( cookie );
25 .24 Example: ASP.NET System.Web.Configuration.MachineKey Secret web server key intended for cookie protection Creating an encrypted cookie with integrity: HttpCookie cookie = new HttpCookie ( name , val ); HttpCookie encodedCookie = HttpSecureCookie.Encode ( cookie ); Decrypting and validating an encrypted cookie: HttpSecureCookie . De code ( cookie );
26 .Sessions A sequence of requests and responses from one browser to one (or more) sites Session can be long (e.g. Gmail) or short without session mgmt : users would have to constantly re-authenticate Session mgmt : authorize user once; All subsequent requests are tied to user
27 .Pre-history: HTTP auth HTTP request: GET / index.html HTTP response contains: WWW-Authenticate: Basic realm="Password Required “ Browsers sends hashed password on all subsequent HTTP requests: Authorization: Basic ZGFddfibzsdfgkjheczI1NXRleHQ=
28 .HTTP auth problems Hardly used in commercial sites: User cannot log out other than by closing browser What if user has multiple accounts? multiple users on same machine? Site cannot customize password dialog Confusing dialog to users Easily spoofed
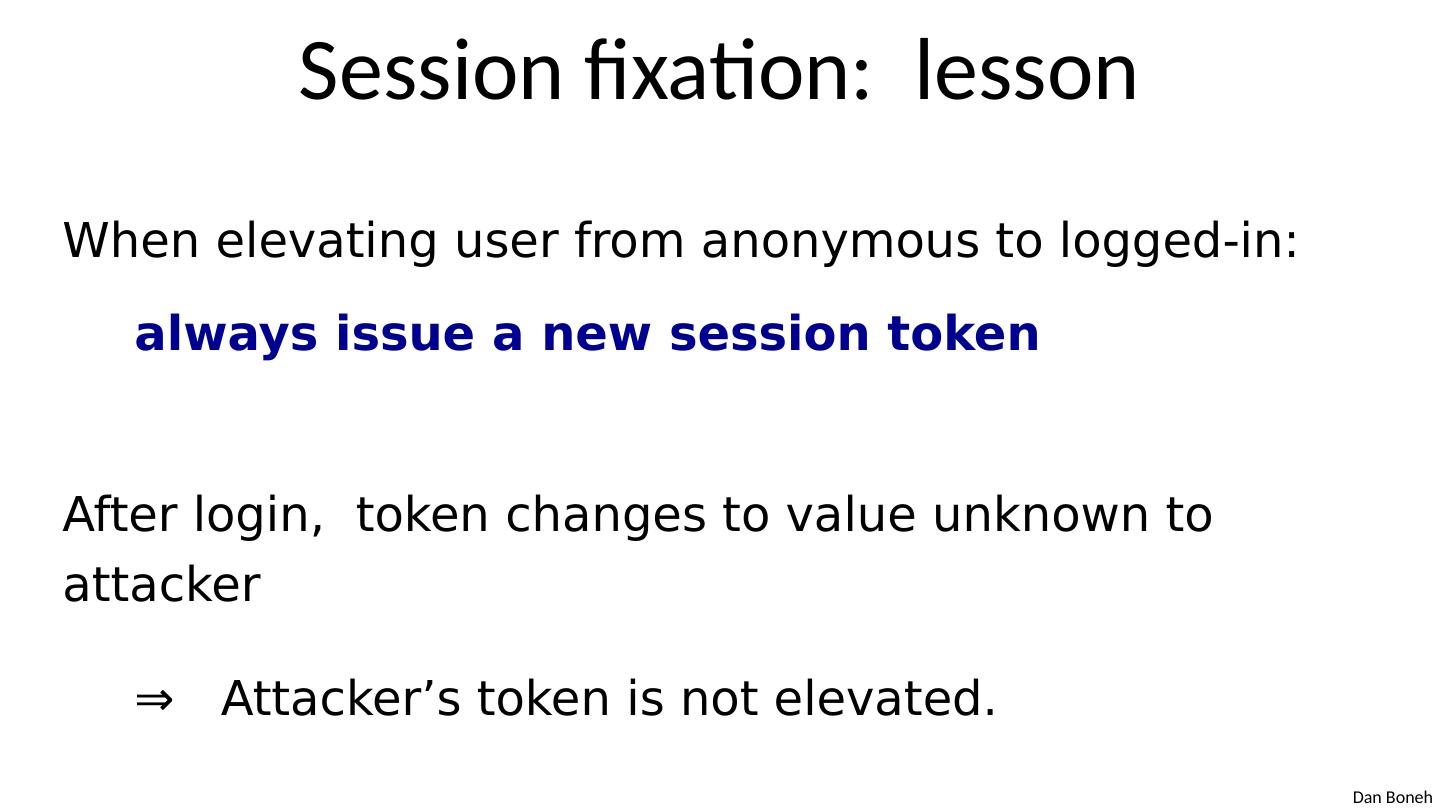
29 .Session tokens Browser GET / index.html set anonymous session token GET / books.html anonymous session token POST /do-login Username & password elevate to a logged-in session token POST /checkout logged-in session token check credentials (crypto) Validate token web site