- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
06computer and network security---fuzzing
展开查看详情
1 .CS 155: Real-World Security April 19, 2018 Alex Stamos CSO, Facebook
2 . ● How are bugs found? Agenda ● Real world bugs ● Who finds bugs? ● Real cyberattacks and defense ● Five basic tips for career success
3 .How are bugs found?
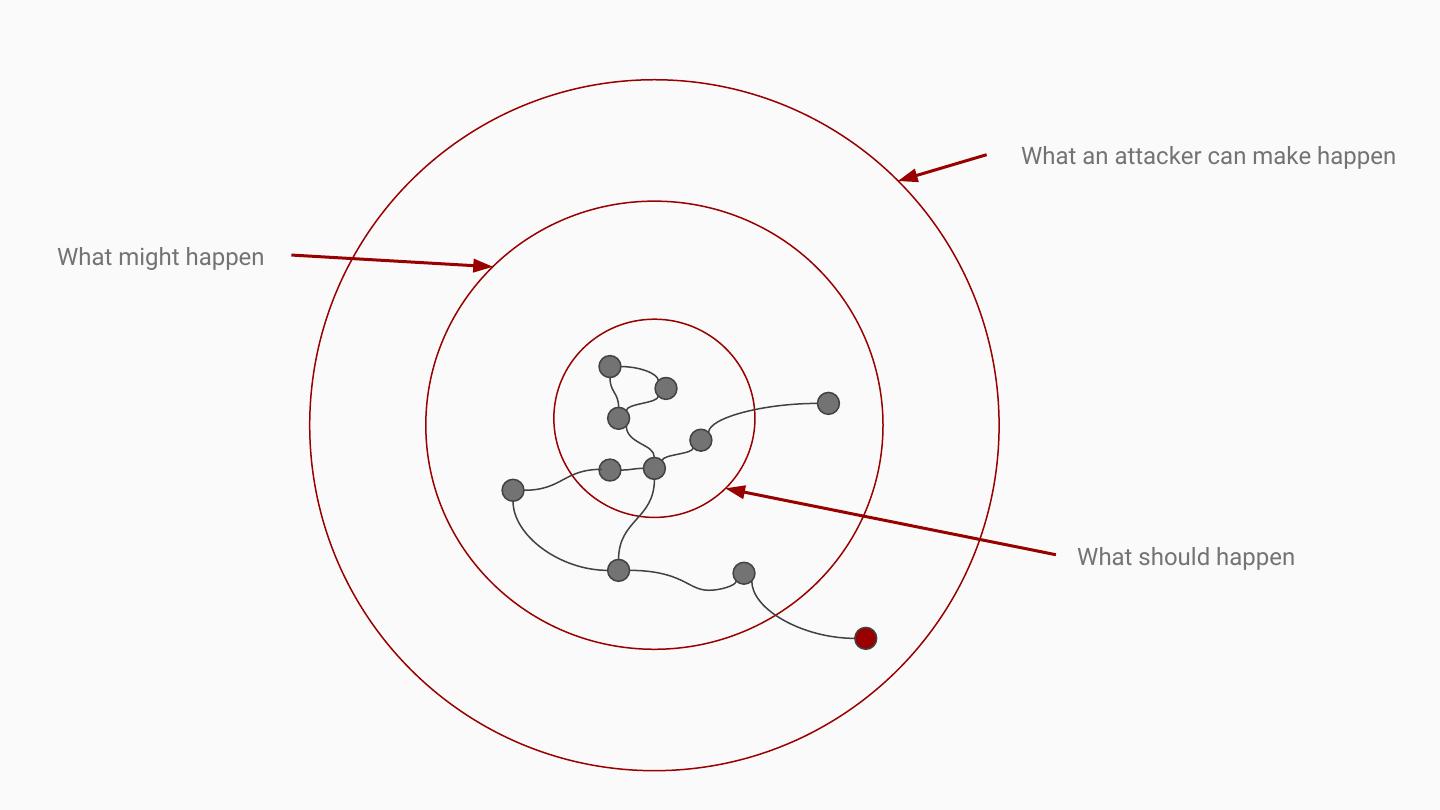
4 . What an attacker can make happen What might happen What should happen
5 .Vulnerability Discovery is the art of... ● Pushing software into exploitable states ● Predicting the kinds of mistakes engineers will make and QA/security teams will miss ● Making the impossible possible
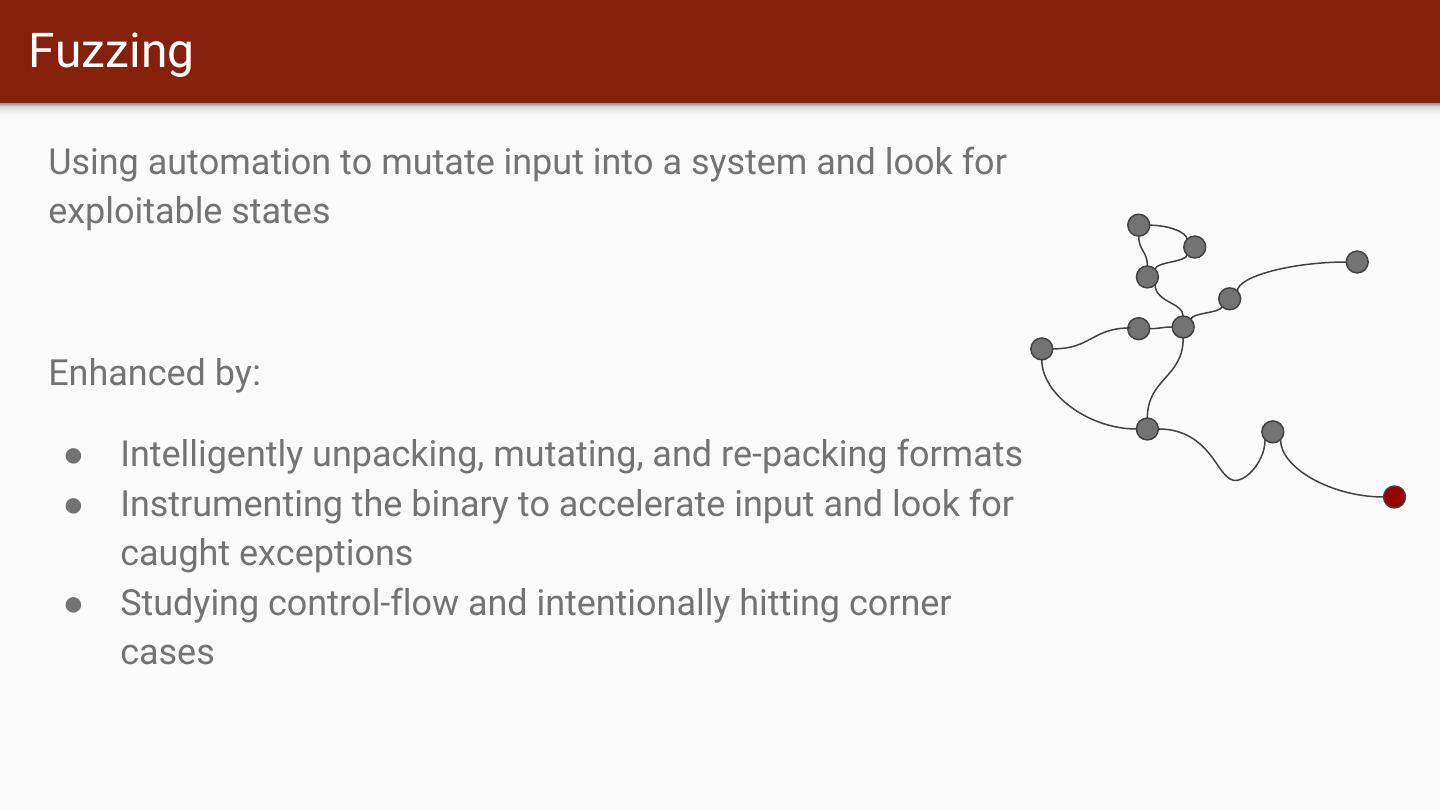
6 .Fuzzing Using automation to mutate input into a system and look for exploitable states Enhanced by: ● Intelligently unpacking, mutating, and re-packing formats ● Instrumenting the binary to accelerate input and look for caught exceptions ● Studying control-flow and intentionally hitting corner cases
7 .Fuzzing http://lcamtuf.coredump.cx/afl/
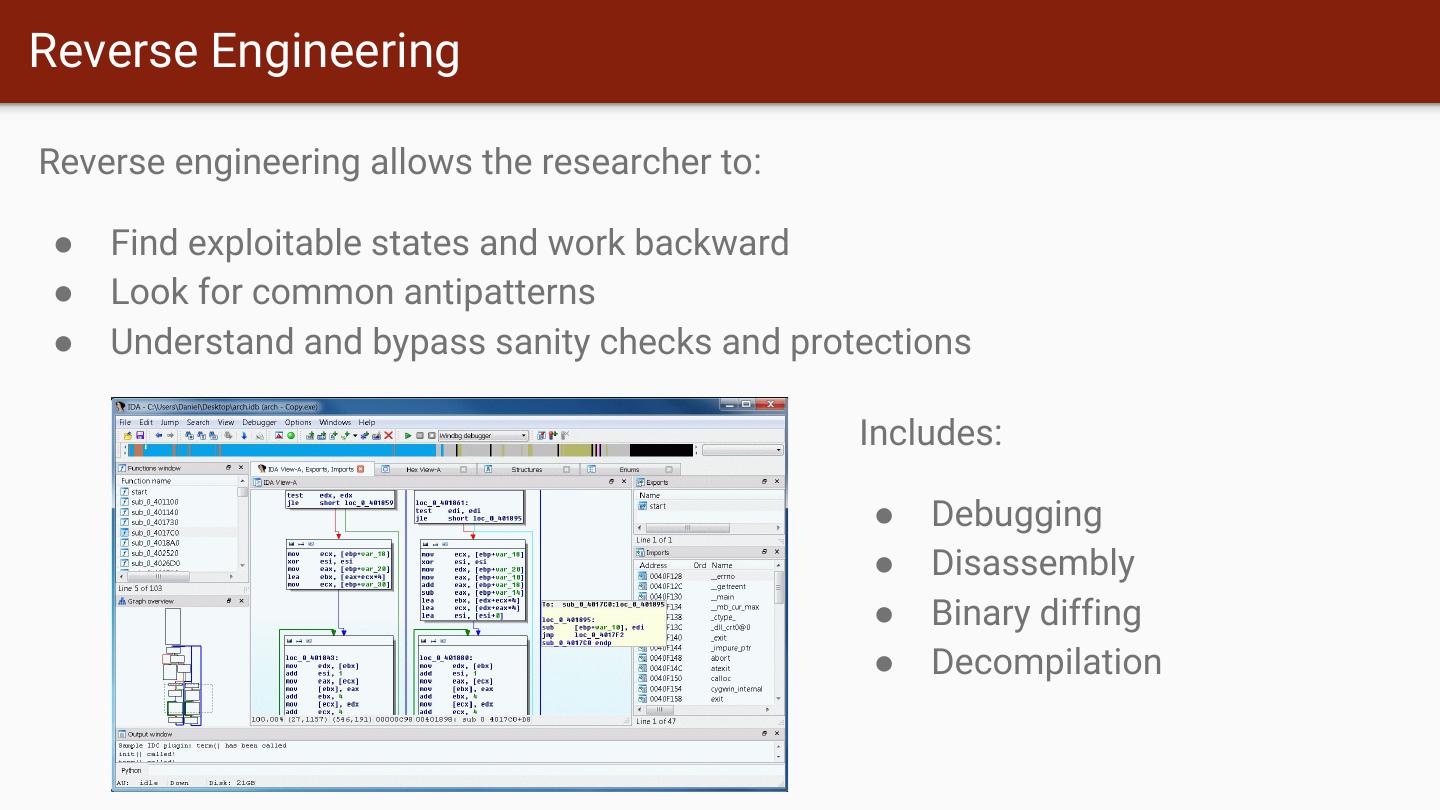
8 .Reverse Engineering Reverse engineering allows the researcher to: ● Find exploitable states and work backward ● Look for common antipatterns ● Understand and bypass sanity checks and protections Includes: ● Debugging ● Disassembly ● Binary diffing ● Decompilation
9 .Manual Manipulation ● Many interesting flaws boil down to asking the software to do something ● Due to: ○ Confused deputy problems ○ Missing access control checks ○ Lack of data consistency checks ● Often using tools to intercept and manipulate inputs
10 .Pulling it Together Professional bug hunters often pull many techniques together: 1. Disassemble a binary to discover:
11 .Pulling it Together 2. Use format-aware fuzzing to try to find entry points that lead to format string https://lcamtuf.blogspot.com/2016/02/say-hello-to-afl-analyze.html
12 .Pulling it Together 3. Researcher carefully modifies crash-creating documents by the fuzzer to obtain execution
13 .Real World Bugs
14 .
15 .
16 .Apple’s TLS Code hashOut.data = hashes + SSL_MD5_DIGEST_LEN; hashOut.length = SSL_SHA1_DIGEST_LEN; if ((err = SSLFreeBuffer(&hashCtx)) != 0) goto fail; if ((err = ReadyHash(&SSLHashSHA1, &hashCtx)) != 0) goto fail; if ((err = SSLHashSHA1.update(&hashCtx, &clientRandom)) != 0) goto fail; if ((err = SSLHashSHA1.update(&hashCtx, &serverRandom)) != 0) goto fail; if ((err = SSLHashSHA1.update(&hashCtx, &signedParams)) != 0) goto fail; goto fail; if ((err = SSLHashSHA1.final(&hashCtx, &hashOut)) != 0) goto fail; err = sslRawVerify(...);
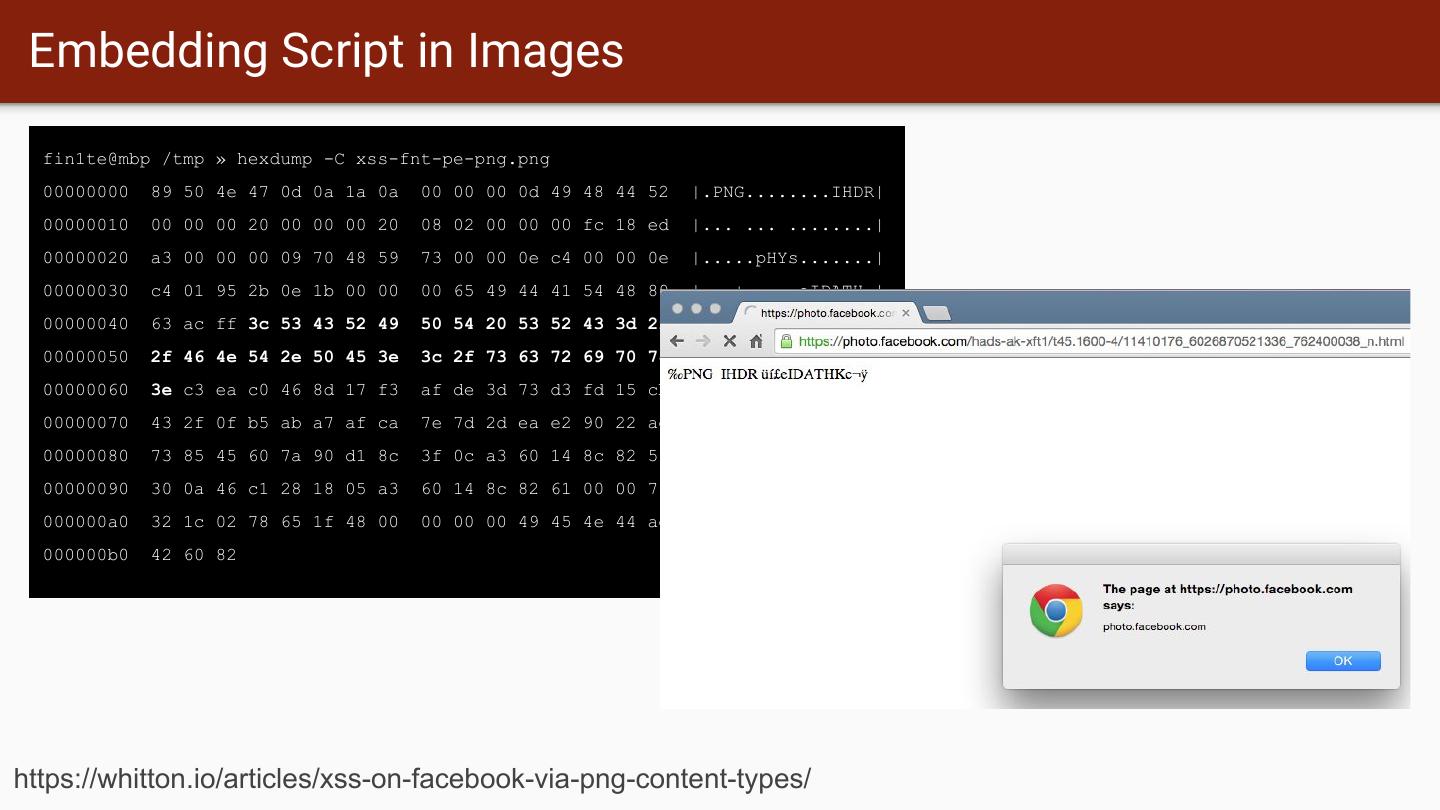
17 . Embedding Script in Images fin1te@mbp /tmp » hexdump -C xss-fnt-pe-png.png 00000000 89 50 4e 47 0d 0a 1a 0a 00 00 00 0d 49 48 44 52 |.PNG........IHDR| 00000010 00 00 00 20 00 00 00 20 08 02 00 00 00 fc 18 ed |... ... ........| 00000020 a3 00 00 00 09 70 48 59 73 00 00 0e c4 00 00 0e |.....pHYs.......| 00000030 c4 01 95 2b 0e 1b 00 00 00 65 49 44 41 54 48 89 |...+.....eIDATH.| 00000040 63 ac ff 3c 53 43 52 49 50 54 20 53 52 43 3d 2f |c..<SCRIPT SRC=/| 00000050 2f 46 4e 54 2e 50 45 3e 3c 2f 73 63 72 69 70 74 |/FNT.PE></script| 00000060 3e c3 ea c0 46 8d 17 f3 af de 3d 73 d3 fd 15 cb |>...F.....=s....| 00000070 43 2f 0f b5 ab a7 af ca 7e 7d 2d ea e2 90 22 ae |C/......~}-...".| 00000080 73 85 45 60 7a 90 d1 8c 3f 0c a3 60 14 8c 82 51 |s.E`z...?..`...Q| 00000090 30 0a 46 c1 28 18 05 a3 60 14 8c 82 61 00 00 78 |0.F.(...`...a..x| 000000a0 32 1c 02 78 65 1f 48 00 00 00 00 49 45 4e 44 ae |2..xe.H....IEND.| 000000b0 42 60 82 |B`.| https://whitton.io/articles/xss-on-facebook-via-png-content-types/
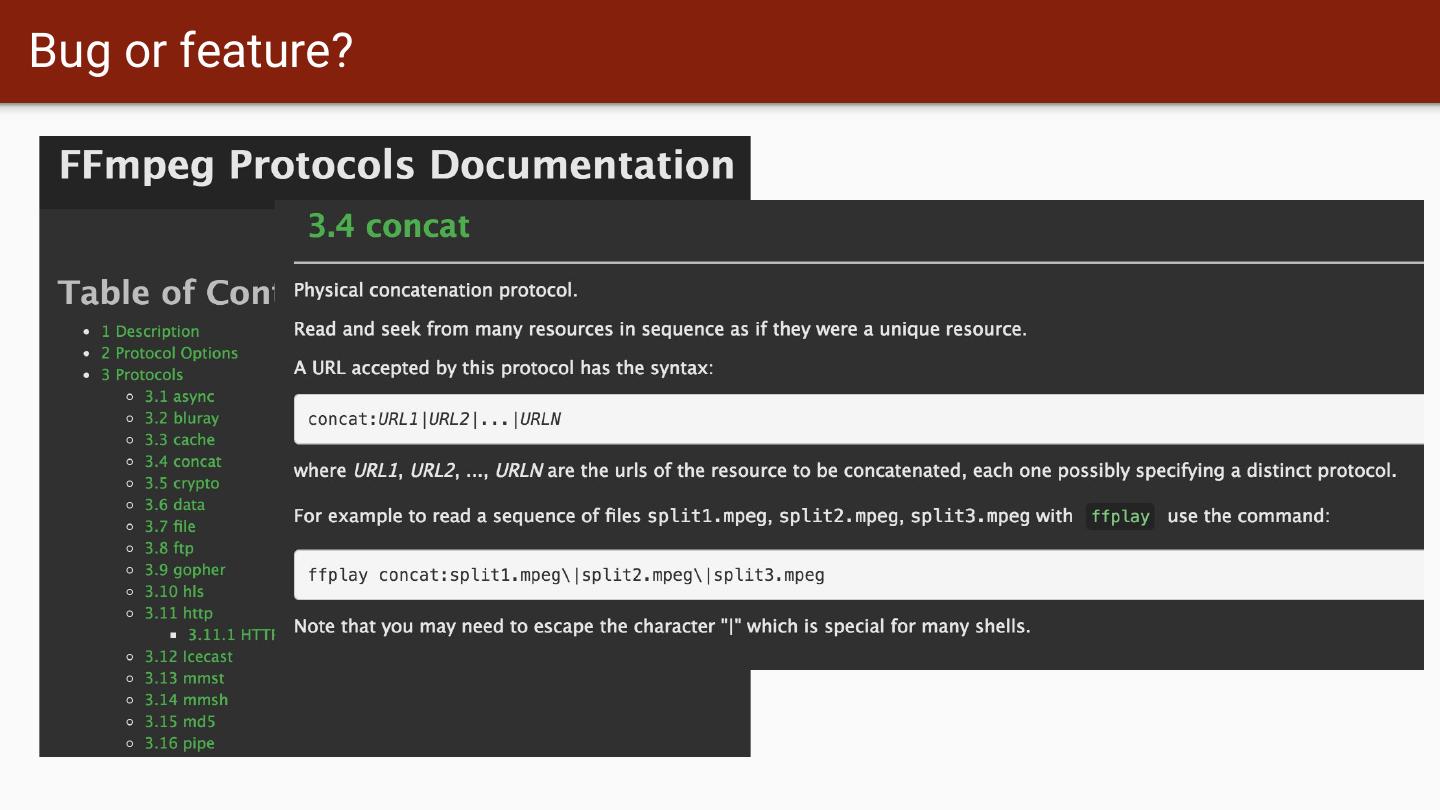
18 .Bug or feature?
19 .Bug or feature?
20 .Memory Management http://perception-point.io/2016/01/14/analysis-and-exploitation-of-a-linux-kernel-vulnerability-cve-2016-0728/
21 .Who Finds Bugs?
22 .Who Looks for Bugs? Defenders: Attackers: ● Have benefit of source code, access to ● Have less information, not a huge problem engineers with shipped code ● Target 100% coverage, so broad-and-shallow ● Only need a handful of flaws to chain them testing is common together ● Generally need automation to assist ● Need to find and explore issues without alerting defenders Researchers: ● Various motivations. Money? Fame? ● Lots of ethical reporting options via bug bounties ● Generally want to stay on right side of the law
23 .Real World Defense
24 .Let’s talk about kill chains 24
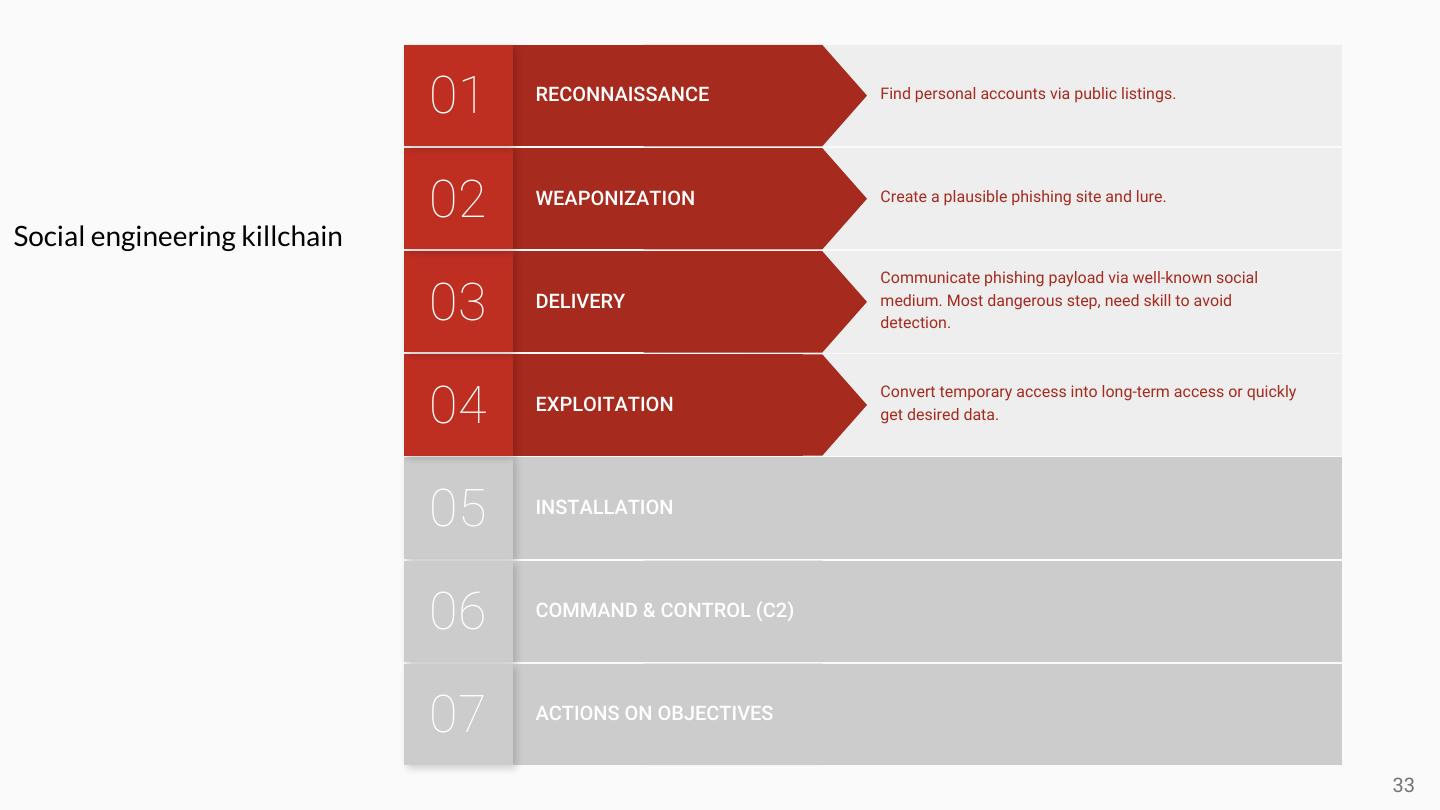
25 . The adversaries are in the planning phase of their 01 RECONNAISSANCE operation. They conduct research to understand which targets will enable them to meet their objectives. THE The adversaries are in the preparation and staging phase 02 WEAPONIZATION of their operation. Malware generation is likely not done by hand – they use automated tools. A “weaponizer” couples malware and exploit into a deliverable payload. CYBER KILL CHAIN ® 03 DELIVERY The adversaries convey the malware to the target. They have launched their operation. The adversaries must exploit a vulnerability to gain access. 04 EXPLOITATION The phrase “zero day” refers to the exploit code used in just this step. Typically, the adversaries install a persistent backdoor or 05 INSTALLATION implant in the victim environment to maintain access for an extended period of time. 06 COMMAND & CONTROL (C2) Malware opens a command channel to enable the adversary to remotely manipulate the victim. With hands-on keyboard access, intruders accomplish the 07 ACTIONS ON OBJECTIVES mission’s goal. What happens next depends on who is on the keyboard. 25
26 . Seems a little… complex and sterile 26
27 .Pulling off this kind of traditional “APT” attack is hard 1. Professional-grade, never seen software and infrastructure 2. Operational team, possibly available 24x7 3. Understanding of how real companies operate 4. Anti-attribution is extremely difficult, lots of fingerprints In 2018, much more focus on attacks against personal accounts and watering holes. IPS 268: Hack Lab 27
28 .Leadership Model of high-end operations Tasking Strategy Target Selection Operational Teams East-West Exploit Passive Recon Grooming Movement Exfiltration Deployment / Escalation East-West Exploit Passive Recon Grooming Movement Exfiltration Deployment / Escalation Central R&D team Vulnerability Research Weaponization Infrastructure Creation 28
29 .29