- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
04computer and network security--Secure Architecture Principles
展开查看详情
1 .Secure Architecture Principles CS 155 Spring 2018 Isolation and Least Privilege Access Control Concepts Operating Systems Browser Isolation and Least Privilege
2 .Secure Architecture Principles Isolation and Least Privilege
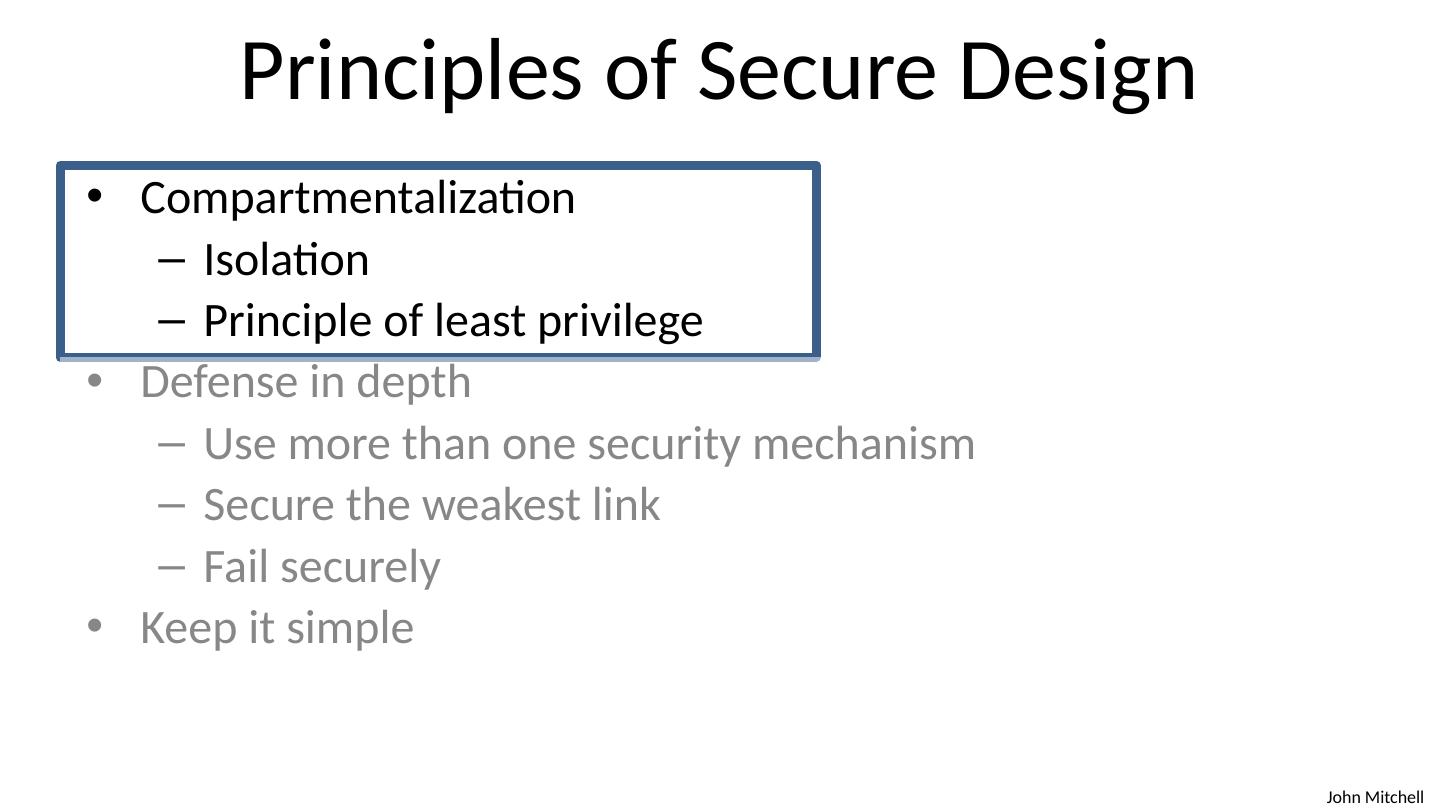
3 .Principles of Secure Design Compartmentalization Isolation Principle of least privilege Defense in depth Use more than one security mechanism Secure the weakest link Fail securely Keep it simple
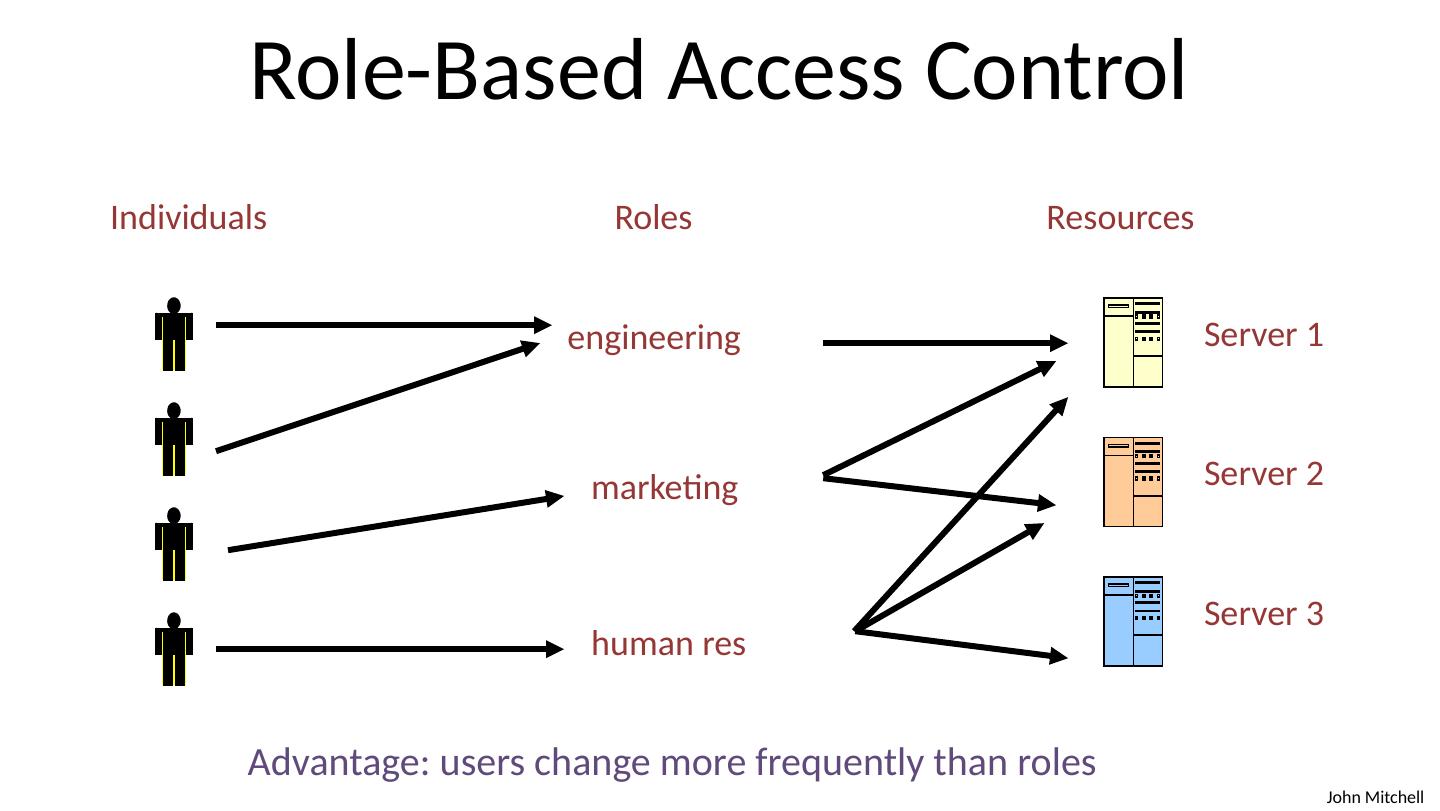
4 .Principle of Least Privilege Principle of Least Privilege A system module should only have the minimal privileges needed for its intended purposes What’s a privilege? Ability to access or modify a resource Assumes compartmentalization and isolation Separate the system into isolated compartments Limit interaction between compartments
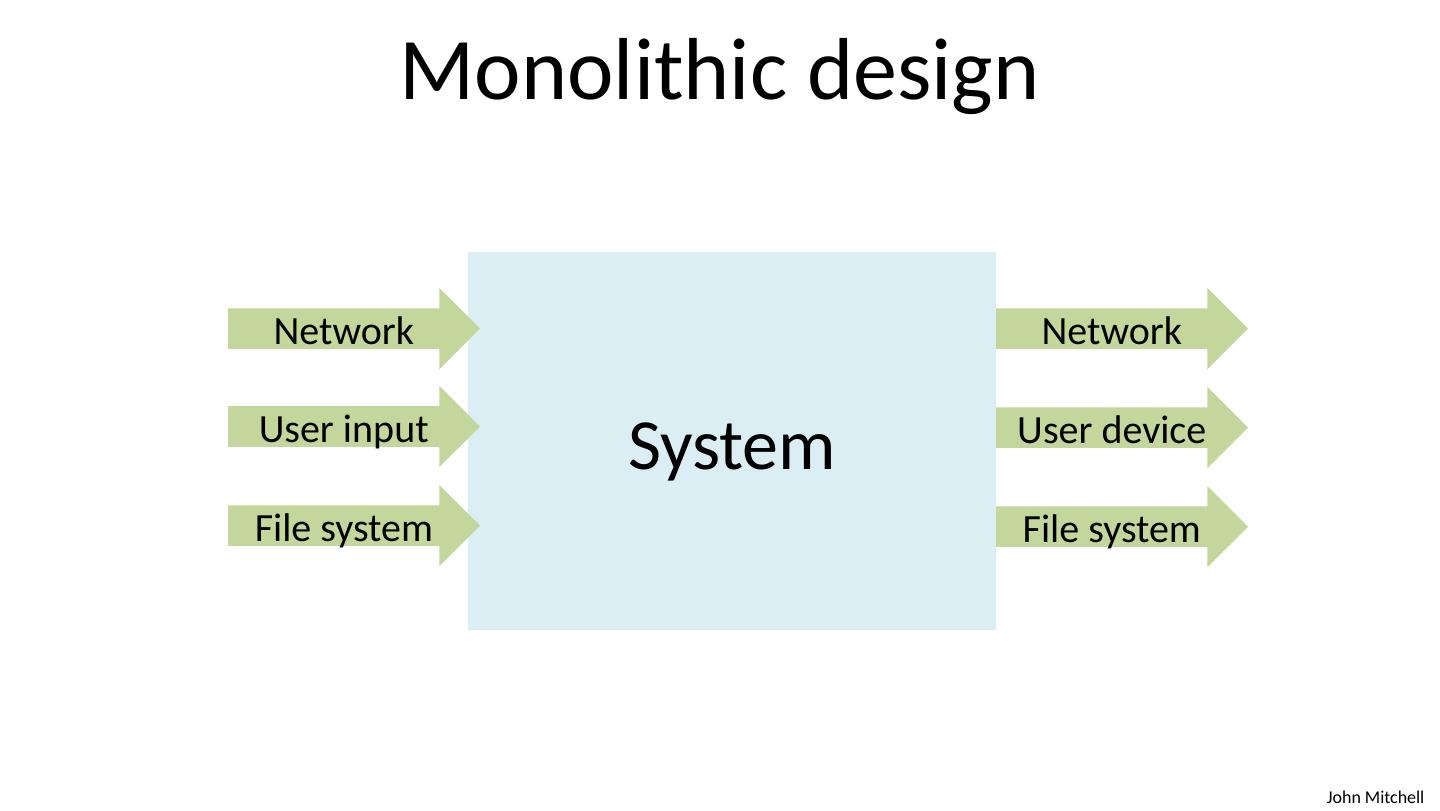
5 .Monolithic design System Network User input File system Network User device File system
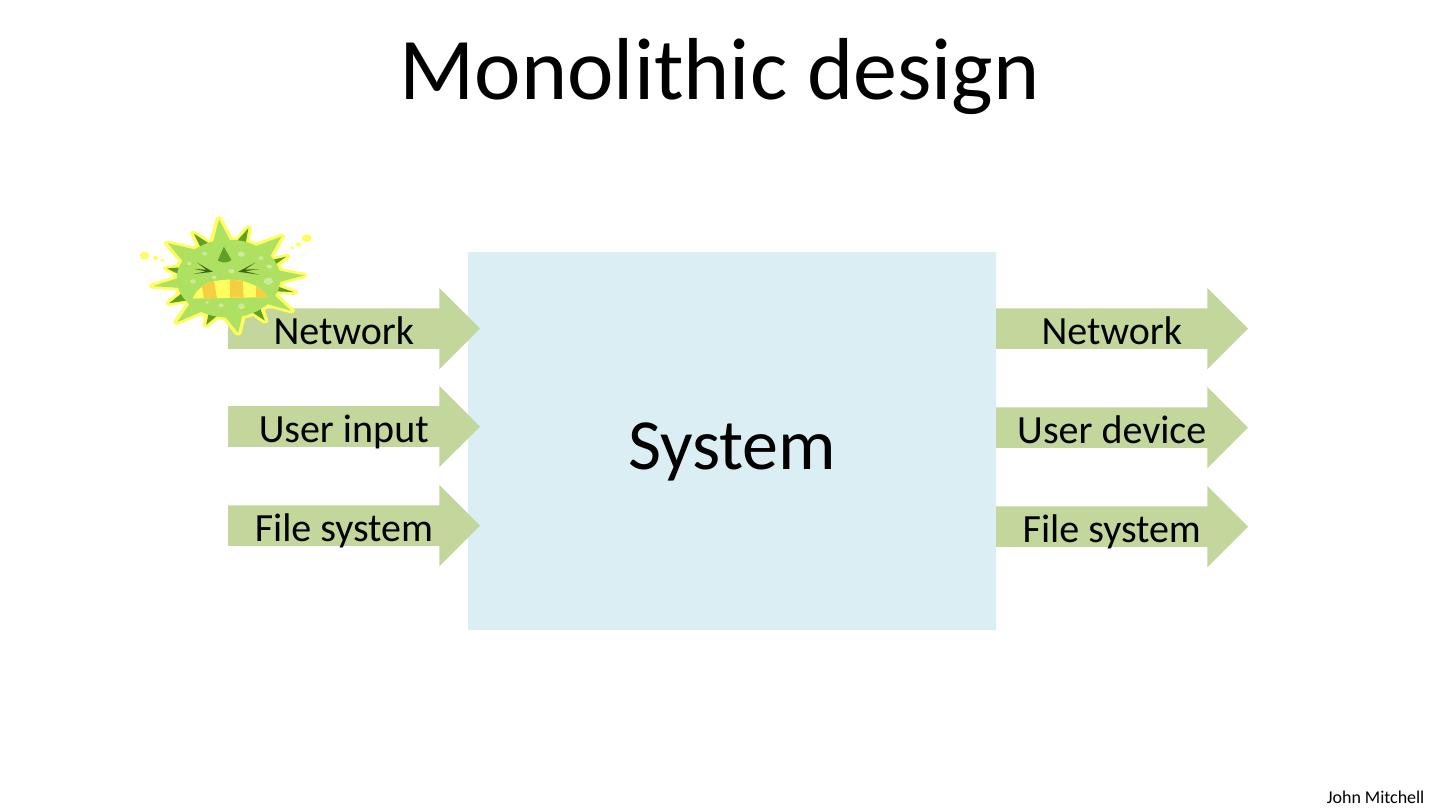
6 .Monolithic design System Network User input File system Network User device File system
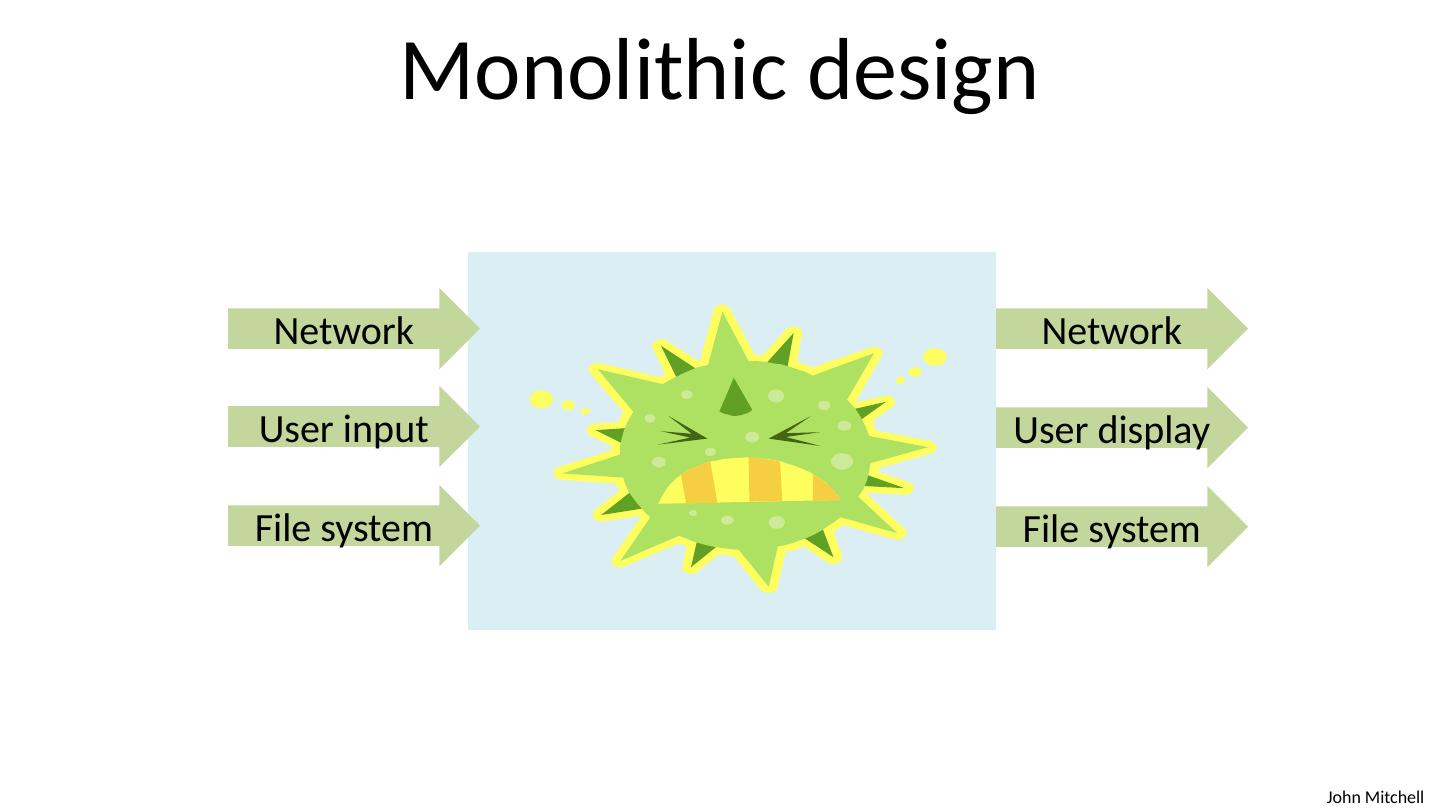
7 .Monolithic design System Network User input File system Network User display File system
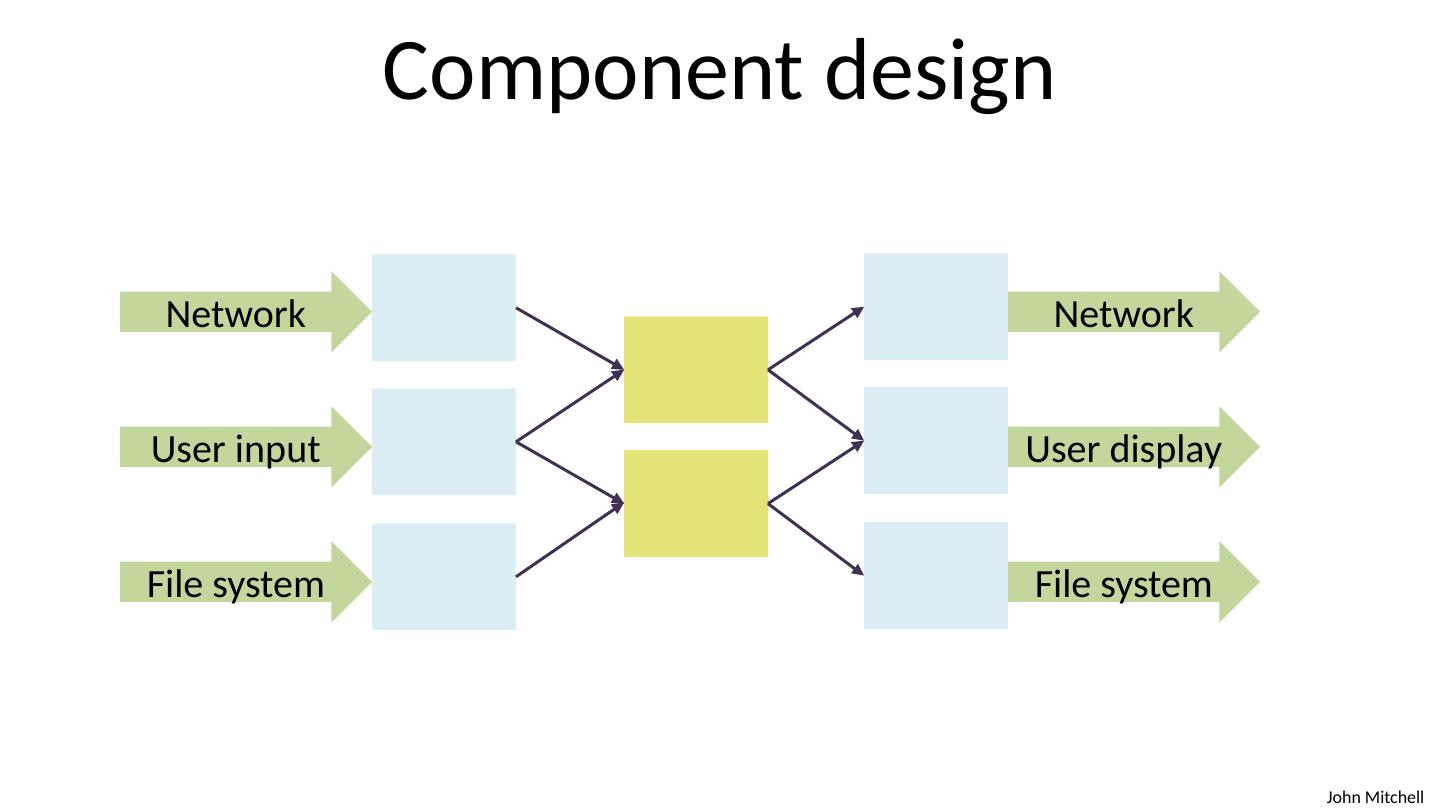
8 .Component design Network User input File system Network User display File system
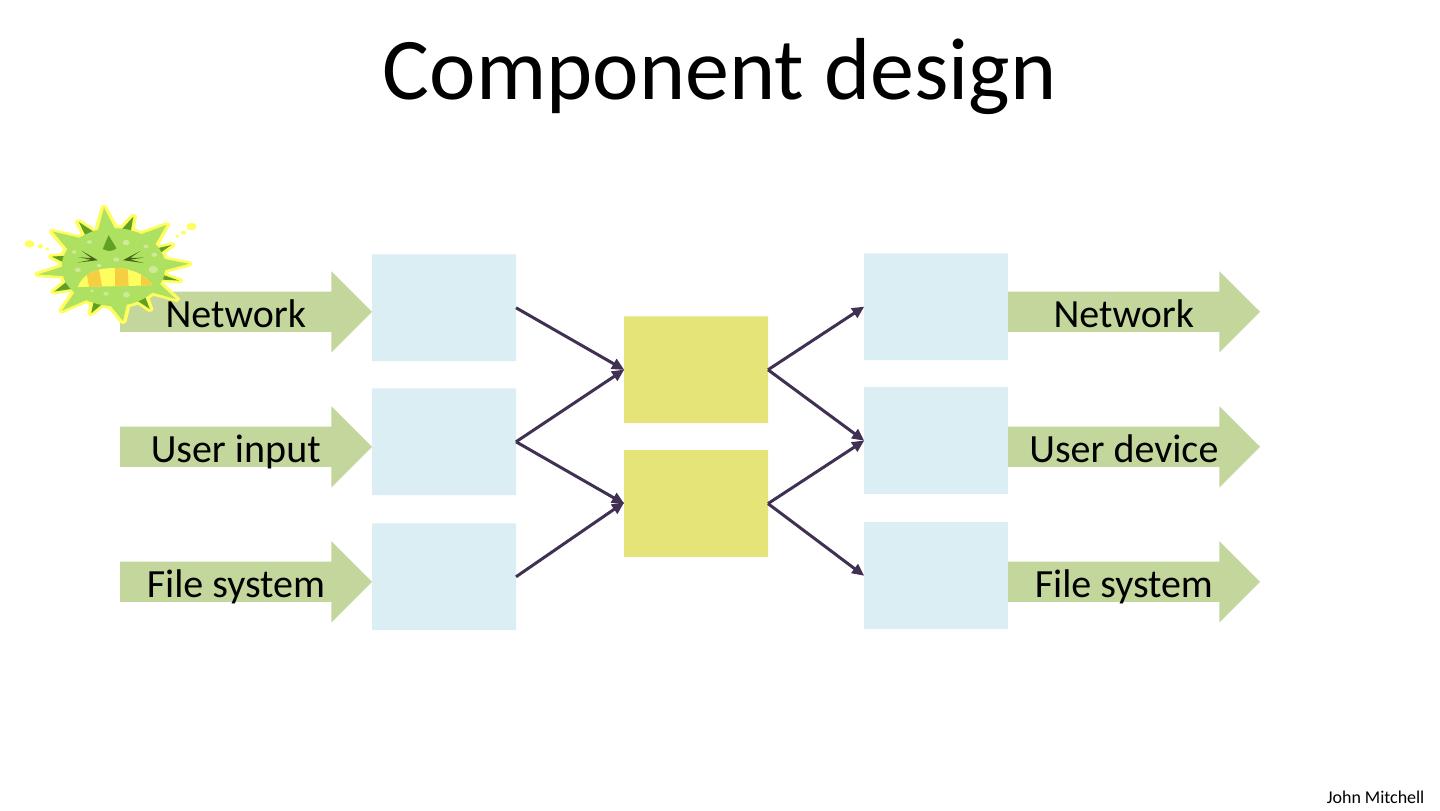
9 .Component design Network User input File system Network User device File system
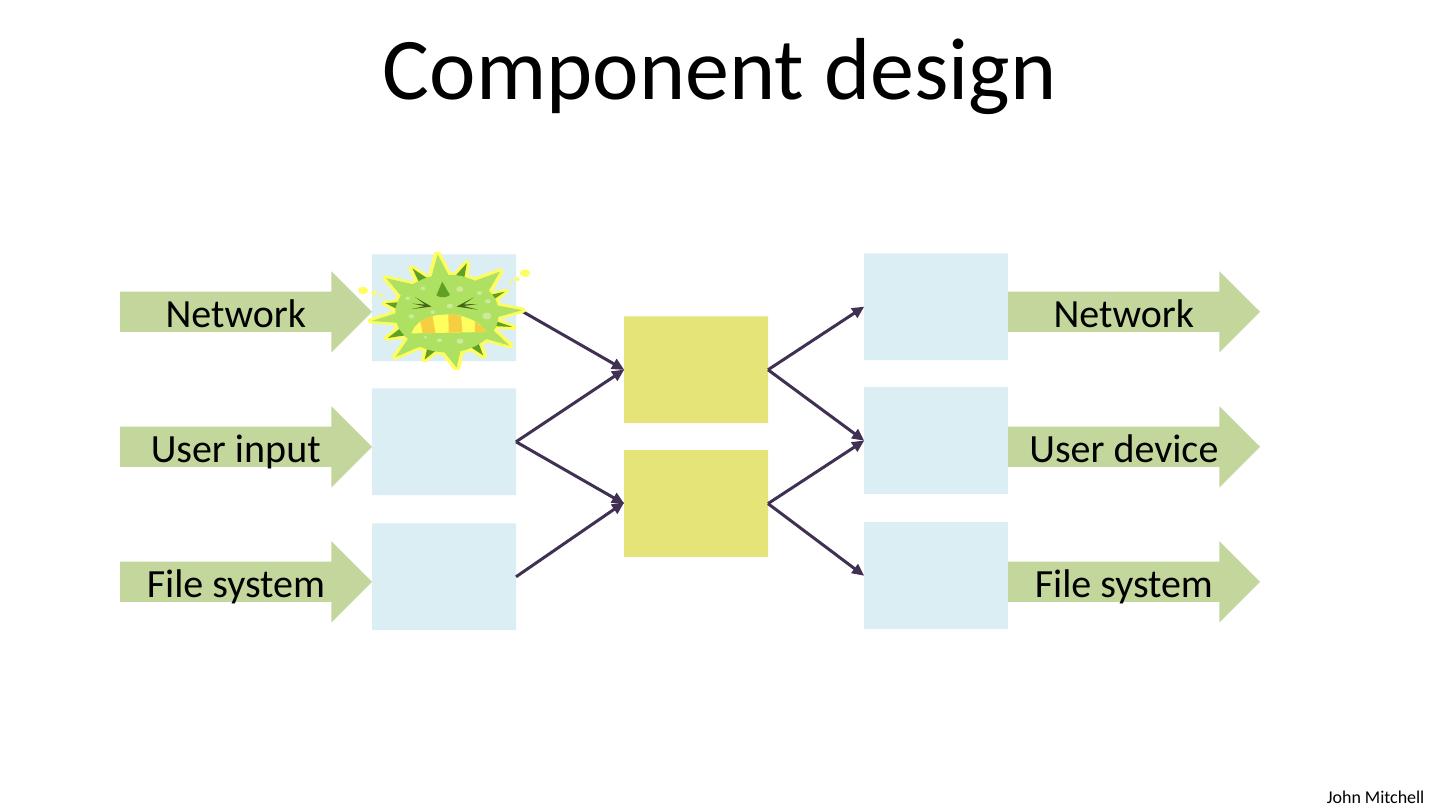
10 .Component design Network User input File system Network User device File system
11 .Component design Network User input File system Network User device File system
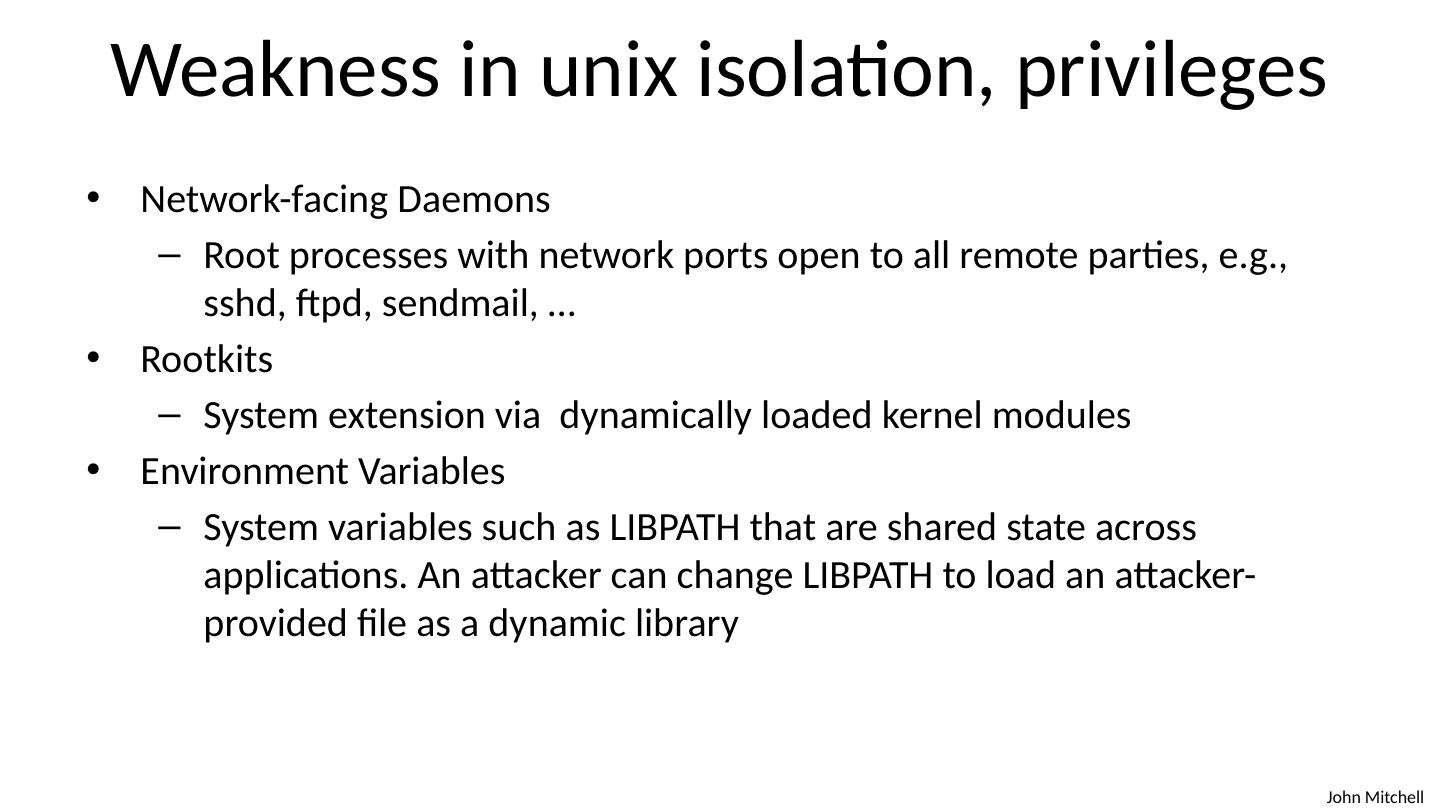
12 .Example: Mail Agent Requirements Receive and send email over external network Place incoming email into local user inbox files Sendmail Traditional Unix Monolithic design Historical source of many vulnerabilities Qmail Compartmentalized design
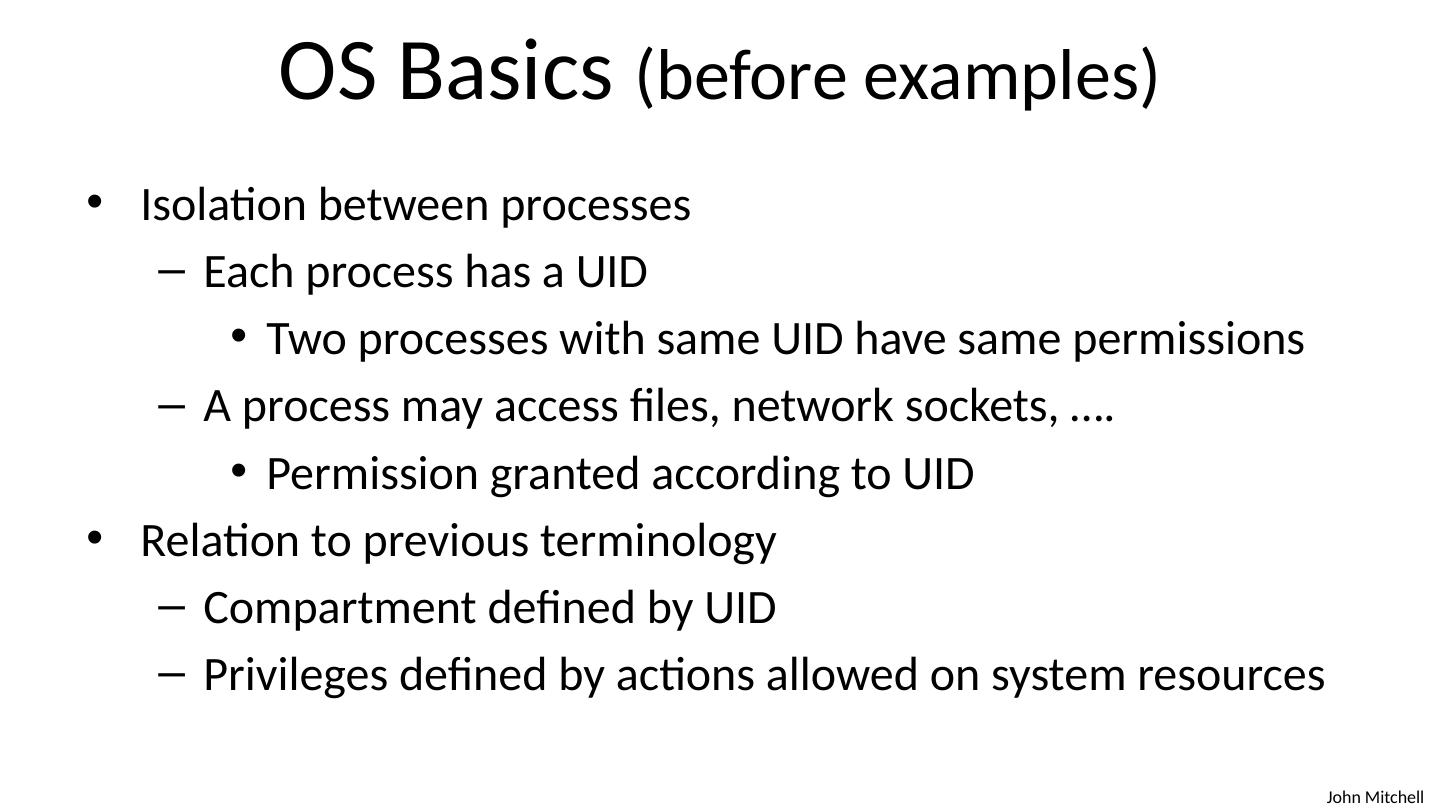
13 .OS Basics (before examples) Isolation between processes Each process has a UID Two processes with same UID have same permissions A process may access files, network sockets, …. Permission granted according to UID Relation to previous terminology Compartment defined by UID Privileges defined by actions allowed on system resources
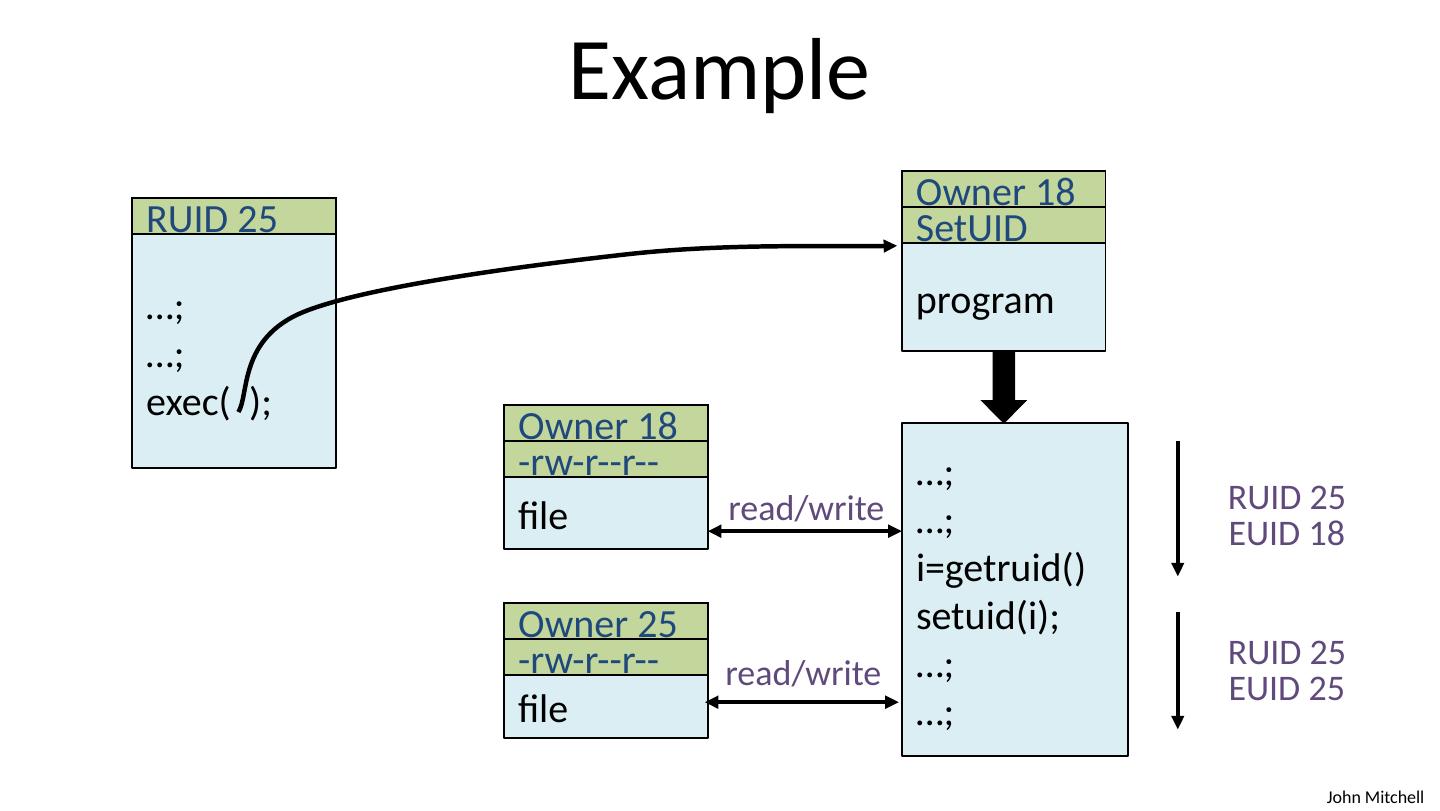
14 .Qmail design Isolation based on OS isolation Separate modules run as separate “users” Each user only has access to specific resources Least privilege Minimal privileges for each UID Only one “ setuid ” program setuid allows a program to run as different users Only one “root” program root program has all privileges
15 .Structure of qmail qmail-smtpd qmail-local qmail-remote qmail-lspawn qmail-rspawn qmail-send qmail-inject qmail -queue Incoming external mail Incoming internal mail
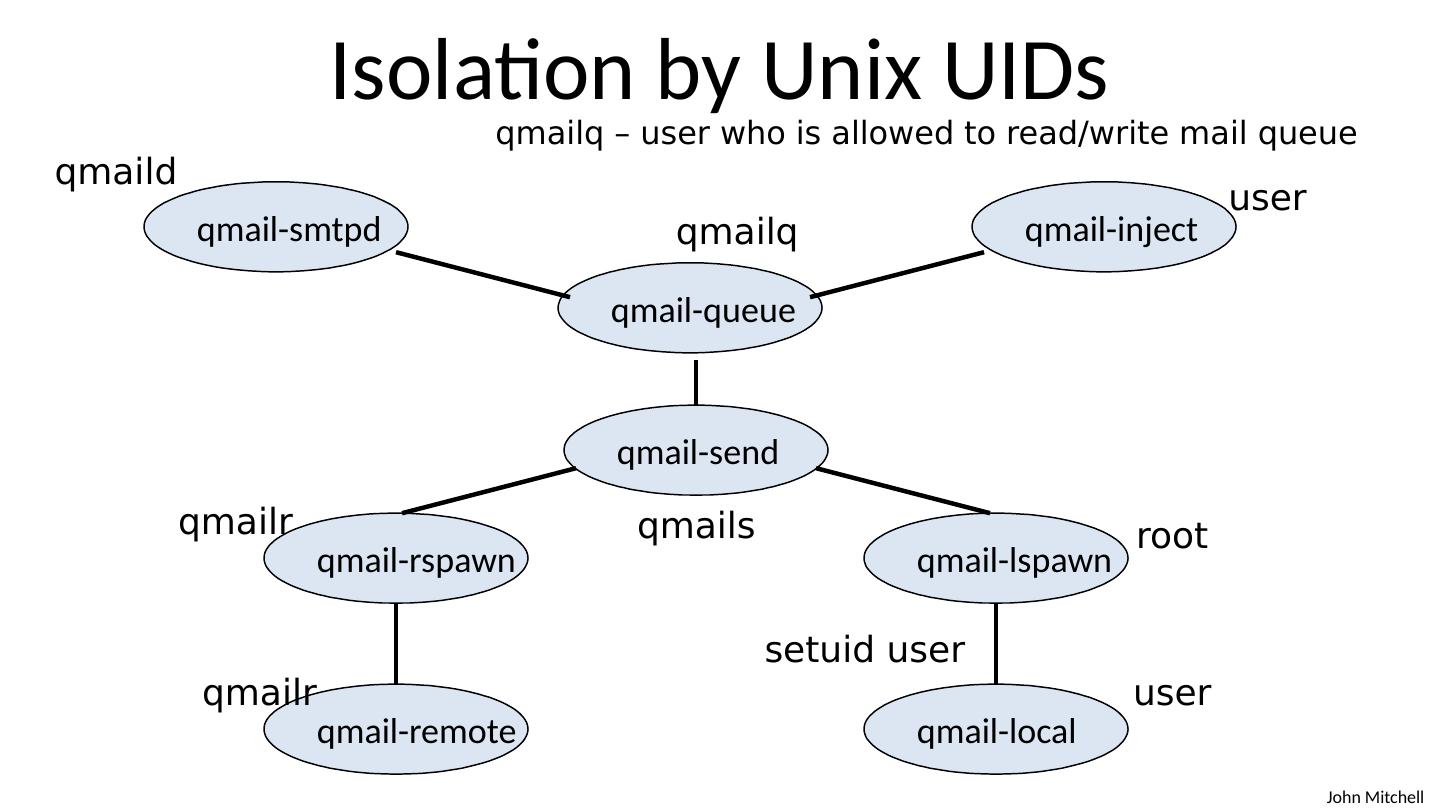
16 .Isolation by Unix UIDs qmail-smtpd qmail-local qmail-remote qmail-lspawn qmail-rspawn qmail-send qmail-inject qmail-queue qmaild user qmailq qmails qmailr qmailr root user setuid user qmailq – user who is allowed to read/write mail queue
17 .Structure of qmail qmail-smtpd qmail-local qmail-remote qmail-lspawn qmail-rspawn qmail-send qmail-inject qmail-queue Reads incoming mail directories Splits message into header, body Signals qmail -send
18 .Structure of qmail qmail-smtpd qmail-local qmail-remote qmail-lspawn qmail-rspawn qmail-send qmail-inject qmail-queue qmail -send signals qmail-lspawn if local qmail -remote if remote
19 .Structure of qmail qmail-smtpd qmail-local qmail-lspawn qmail-send qmail-inject qmail-queue qmail-lspawn Spawns qmail -local qmail -local runs with ID of user receiving local mail
20 .Structure of qmail qmail-smtpd qmail-local qmail-lspawn qmail-send qmail-inject qmail-queue qmail -local Handles alias expansion Delivers local mail Calls qmail -queue if needed
21 .Structure of qmail qmail-smtpd qmail-remote qmail-rspawn qmail-send qmail-inject qmail-queue qmail -remote Delivers message to remote MTA
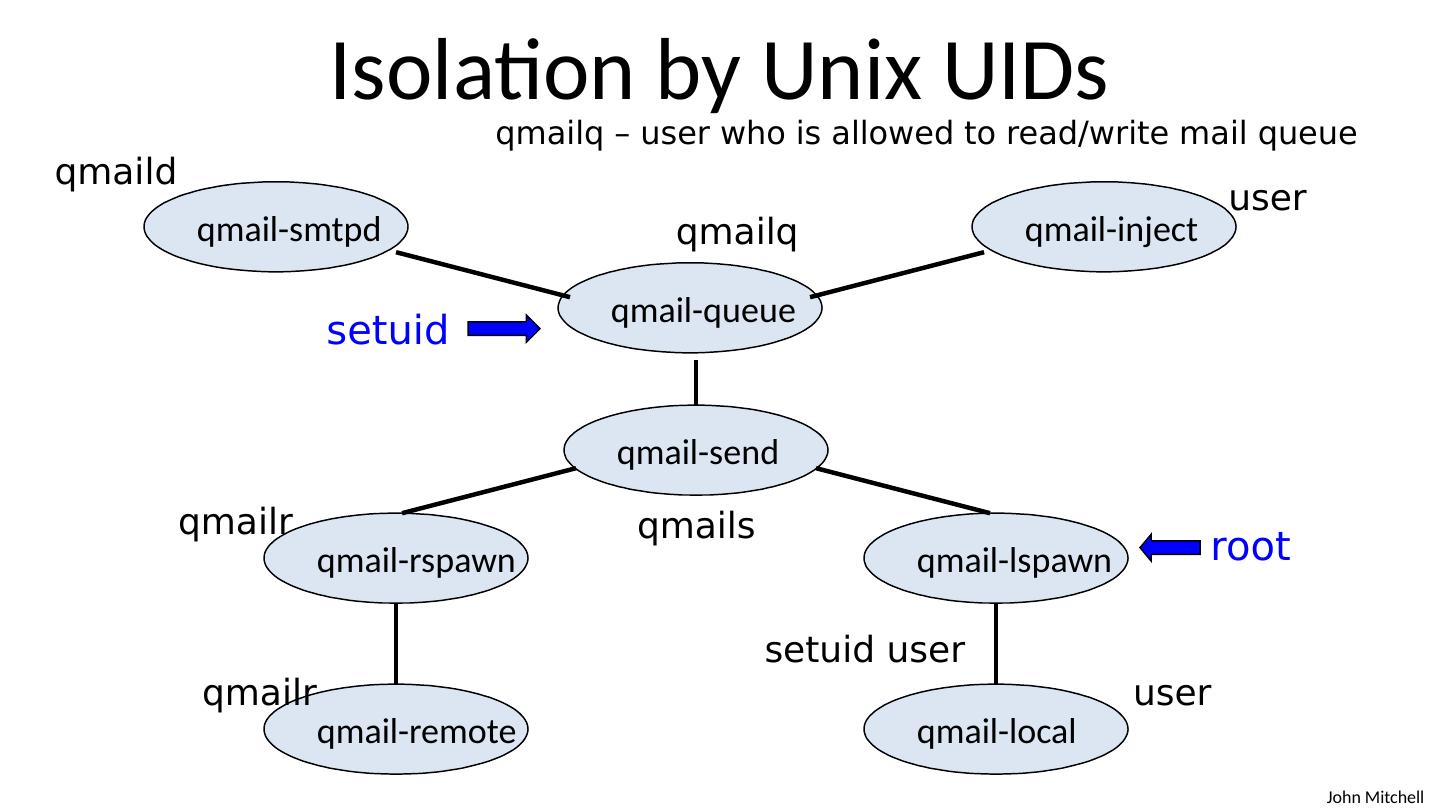
22 .root Isolation by Unix UIDs qmail-smtpd qmail-local qmail-remote qmail-lspawn qmail-rspawn qmail-send qmail-inject qmail-queue qmaild user qmailq qmails qmailr qmailr user setuid user qmailq – user who is allowed to read/write mail queue setuid root
23 .Least privilege qmail-smtpd qmail-local qmail-remote qmail-lspawn qmail-rspawn qmail-send qmail-inject qmail-queue root setuid
24 .Android process isolation Android application sandbox Isolation: Each application runs with its own UID in own VM Provides memory protection Communication limited to using Unix domain sockets Only ping, zygote (spawn another process) run as root Interaction: reference monitor checks permissions on inter-component communication Least Privilege: Applications announces permission User grants access at install time
25 .
26 .App Isolation: different apps under different UIDs
27 .Isolation: different apps under different UIDs App UID1 App UID2
28 .Privileges set at install time App UID1, priv 1, priv 2, … App UID2, priv 3, priv 4, …
29 .Discussion? Principle of Least Privilege Qmail example Android app sandbox example