- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
01computer and network security---Course overview
展开查看详情
1 .CS155 Computer Security https:// crypto.stanford.edu /cs155 Course overview
2 .The computer security problem Lots of buggy software Social engineering is very effective Money can be made from finding and exploiting vulns . Marketplace for vulnerabilities Marketplace for owned machines (PPI) Many methods to profit from owned machines current state of computer security
3 .source: https:// www.cvedetails.com /top-50-products.php?year=2017
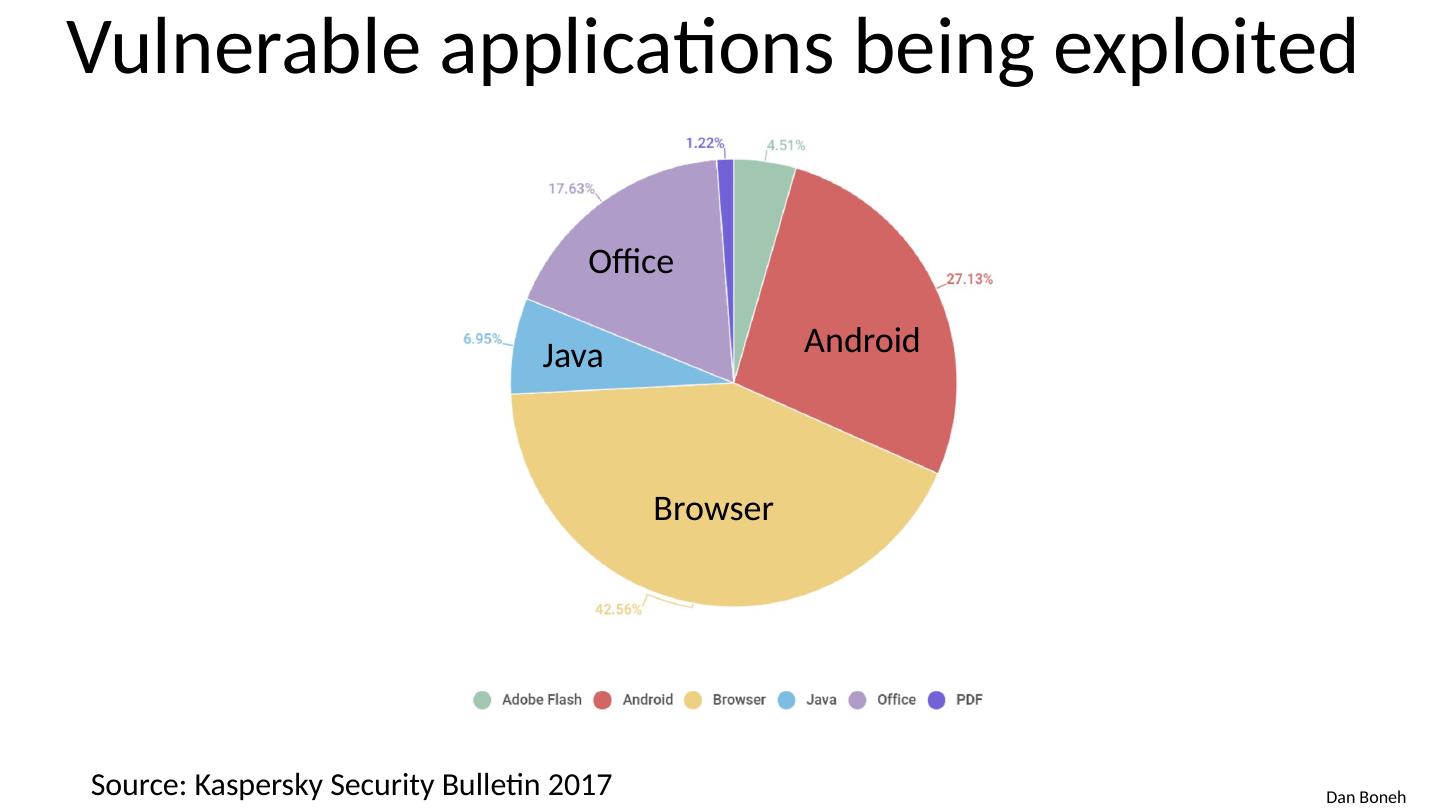
4 .Vulnerable applications being exploited Source: Kaspersky Security Bulletin 2017 Browser Android Office Java
5 .Mobile malware (Nov. 2013 – Oct. 2014) date The rise of mobile banking Trojans (Kaspersky Security Bulletin 2014)
6 .Introduction Sample attacks
7 .Why own client machines: 1. IP address and bandwidth stealing Attacker’s goal: look like a random Internet user Use the IP address of infected machine or phone for: Spam (e.g. the storm botnet) Spamalytics : 1:12M pharma spams leads to purchase 1:260K greeting card spams leads to infection Denial of Service: Services: 1 hour (20$), 24 hours (100$) Click fraud (e.g. Clickbot.a )
8 .Why own machines: 2. Steal user credentials and inject ads keylog for banking passwords, web passwords, gaming pwds . Example: SilentBanker (and many like it) Bank Malware injects Javascript Bank sends login page needed to log in When user submits information, also sent to attacker User requests login page Similar mechanism used by Zeus botnet Man-in-the-Browser (MITB)
9 .Lots of financial malware Source: Kaspersky Security Bulletin 2017 records banking passwords via keylogger spread via spam email and hacked web sites maintains access to PC for future installs
10 .Users attacked: stats ≈ 300,000 users/month worldwide A worldwide problem Source: Kaspersky Security Bulletin 2015
11 .Why own machines: 3. Ransomware a worldwide problem Worm spreads via a vuln . in SMB (port 445) Apr. 14, 2017 : Eternalblue vuln . released by ShadowBrokers May 12, 2017 : Worm detected (3 weeks to weaponize )
12 .WannaCry ransomware
13 .Ransomware in 2017: # users attacked Source: Kaspersky Security Bulletin 2017
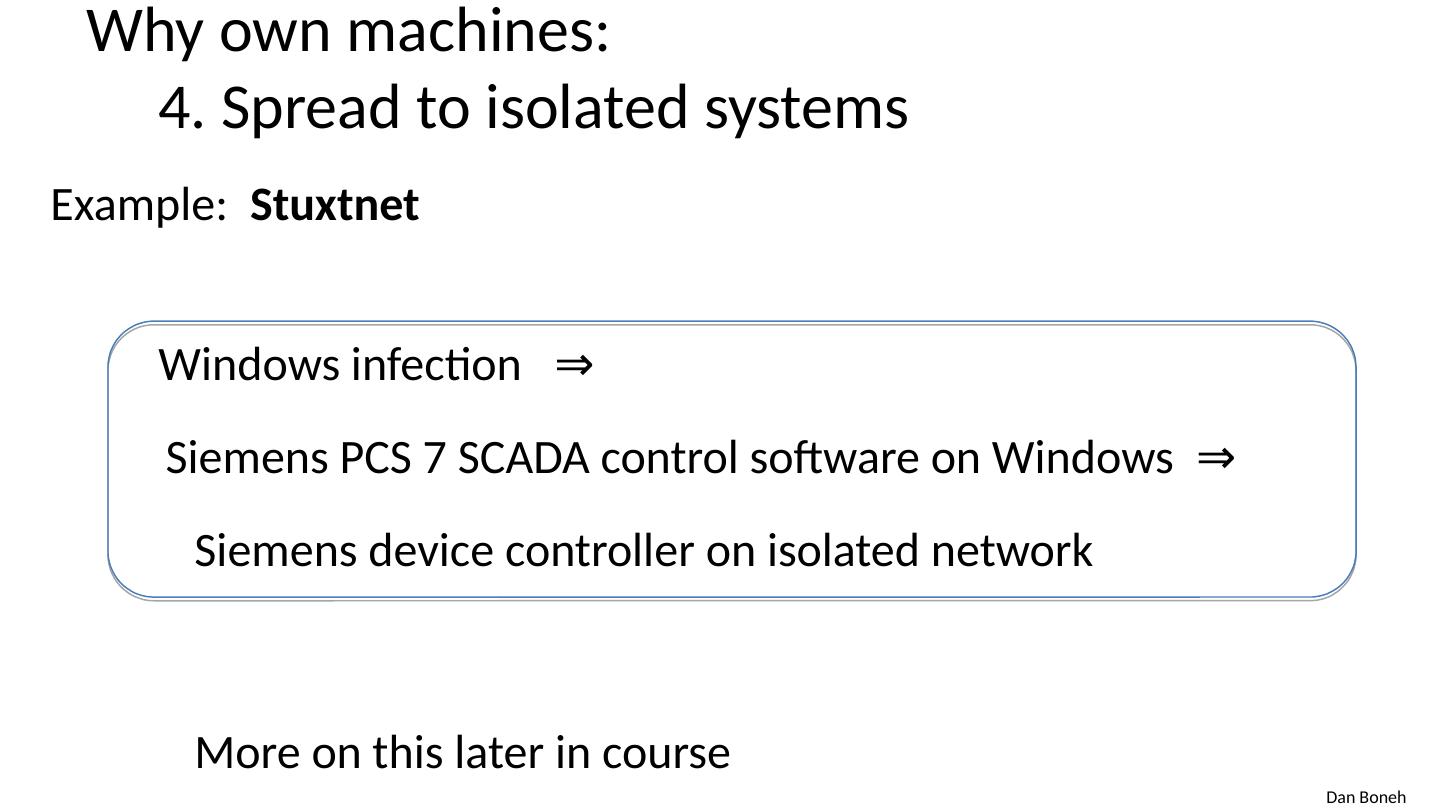
14 .Why own machines: 4. Spread to isolated systems Example: Stuxtnet Windows infection ⇒ Siemens PCS 7 SCADA control software on Windows ⇒ Siemens device controller on isolated network More on this later in course
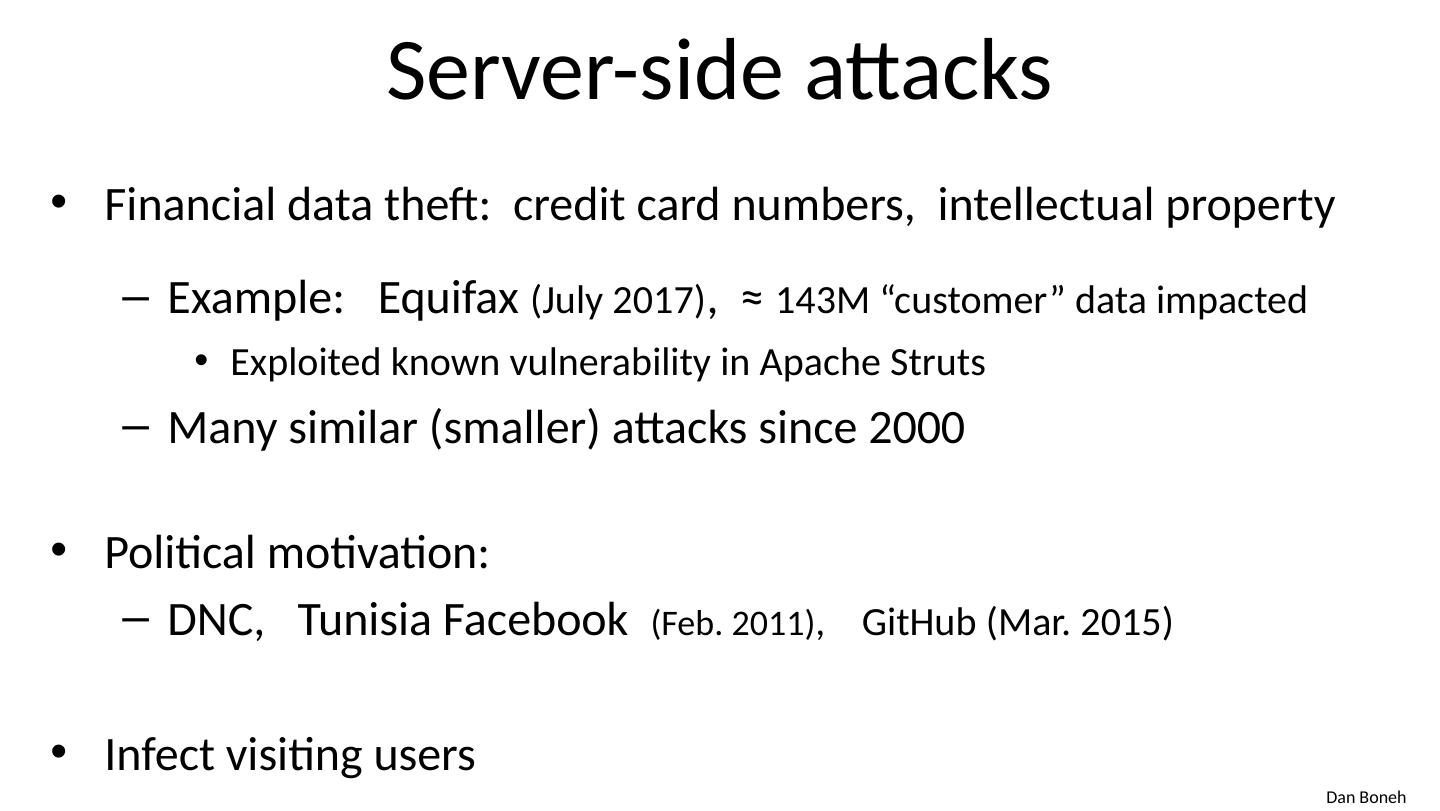
15 .Server-side attacks Financial data theft: credit card numbers, intellectual property Example: Equifax (July 2017) , ≈ 143M “customer” data impacted Exploited known vulnerability in Apache Struts Many similar (smaller) attacks since 2000 Political motivation: DNC, Tunisia Facebook (Feb. 2011) , GitHub (Mar. 2015) Infect visiting users
16 .Types of data stolen (2012-2015) Source: California breach notification report, 2015
17 .Example: Mpack PHP-based tools installed on compromised web sites Embedded as an iframe on infected page Infects browsers that visit site Features management console provides stats on infection rates Sold for several 100$ Customer care can be purchased, one-year support contract Impact: 500,000 infected sites (compromised via SQL injection) Several defenses: e.g. Google safe browsing
18 .Insider attacks: example Hidden trap door in Linux ( nov 2003) Allows attacker to take over a computer Practically undetectable change (uncovered via CVS logs) Inserted line in wait4() Looks like a standard error check, but … if ((options == (__WCLONE|__WALL)) && (current-> uid = 0)) retval = -EINVAL; See: http:// lwn.net /Articles/57135/
19 .Many more examples Access to SIPRnet and a CD-RW: 260,000 cables ⇒ Wikileaks SysAdmin for city of SF government. Changed passwords, locking out city from router access Inside logic bomb took down 2000 UBS servers ⋮ Can security technology help?
20 .How companies lose data Source: California breach notification report, 2015 lost/stolen laptops malware/phishing insider attack insider error How do we have this data?
21 .Introduction The Marketplace for Vulnerabilities
22 .Marketplace for Vulnerabilities Option 1 : bug bounty programs (many) Google Vulnerability Reward Program: up to $31,337 Microsoft Bounty Program: up to $100K Apple Bug Bounty program: up to $200K (secure boot firmware) Pwn2Own competition: $15K Option 2 : Zero day initiative (ZDI), iDefense ( accenture ) : up to $25K Zerodium : $1.5M for iOS10 , $200K for Android 7 (Sep. 2016)
23 .Example: Mozilla
24 .Marketplace for Vulnerabilities Option 3 : black market Source: Andy Greenberg (Forbes, 3/23/2012 ) … and even up to $1.5M
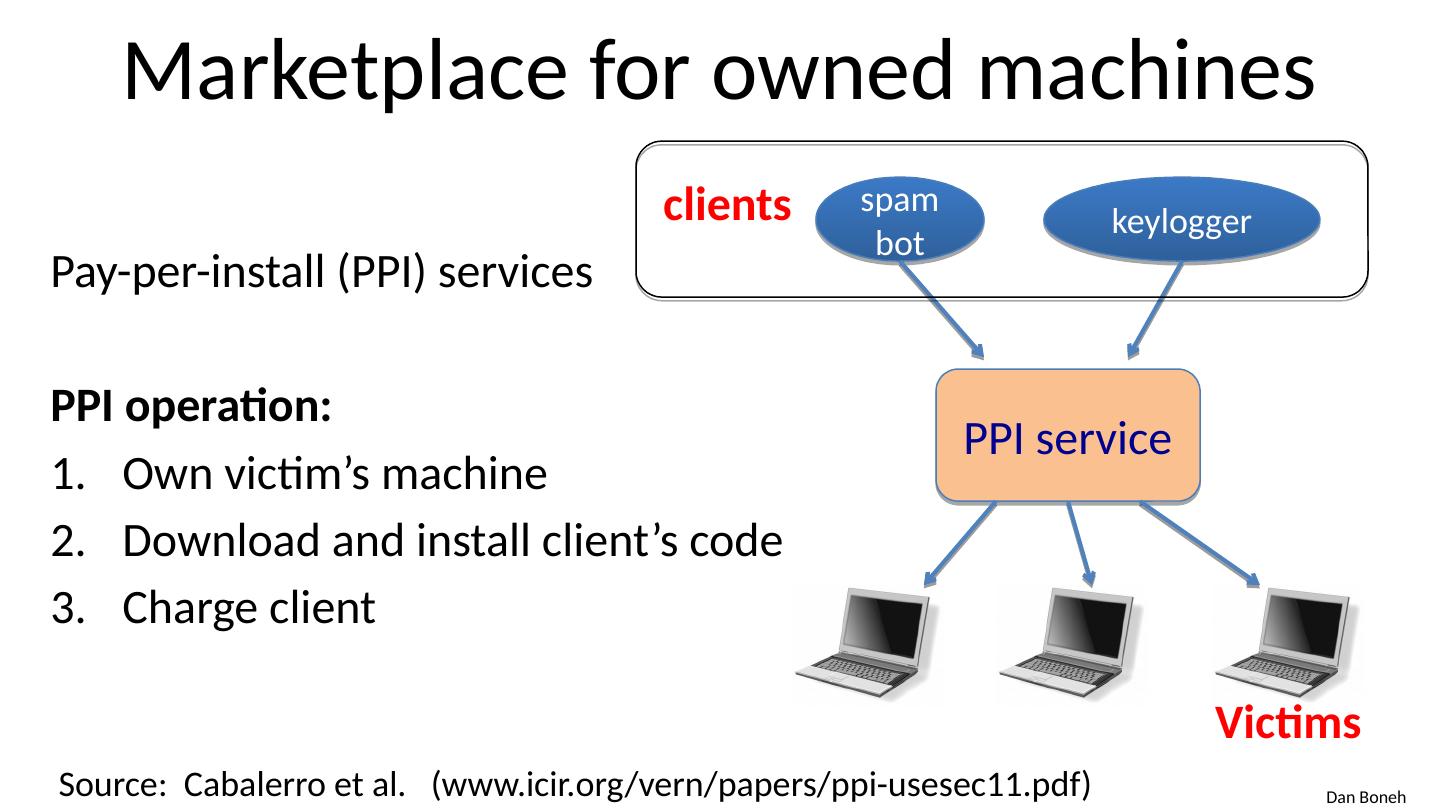
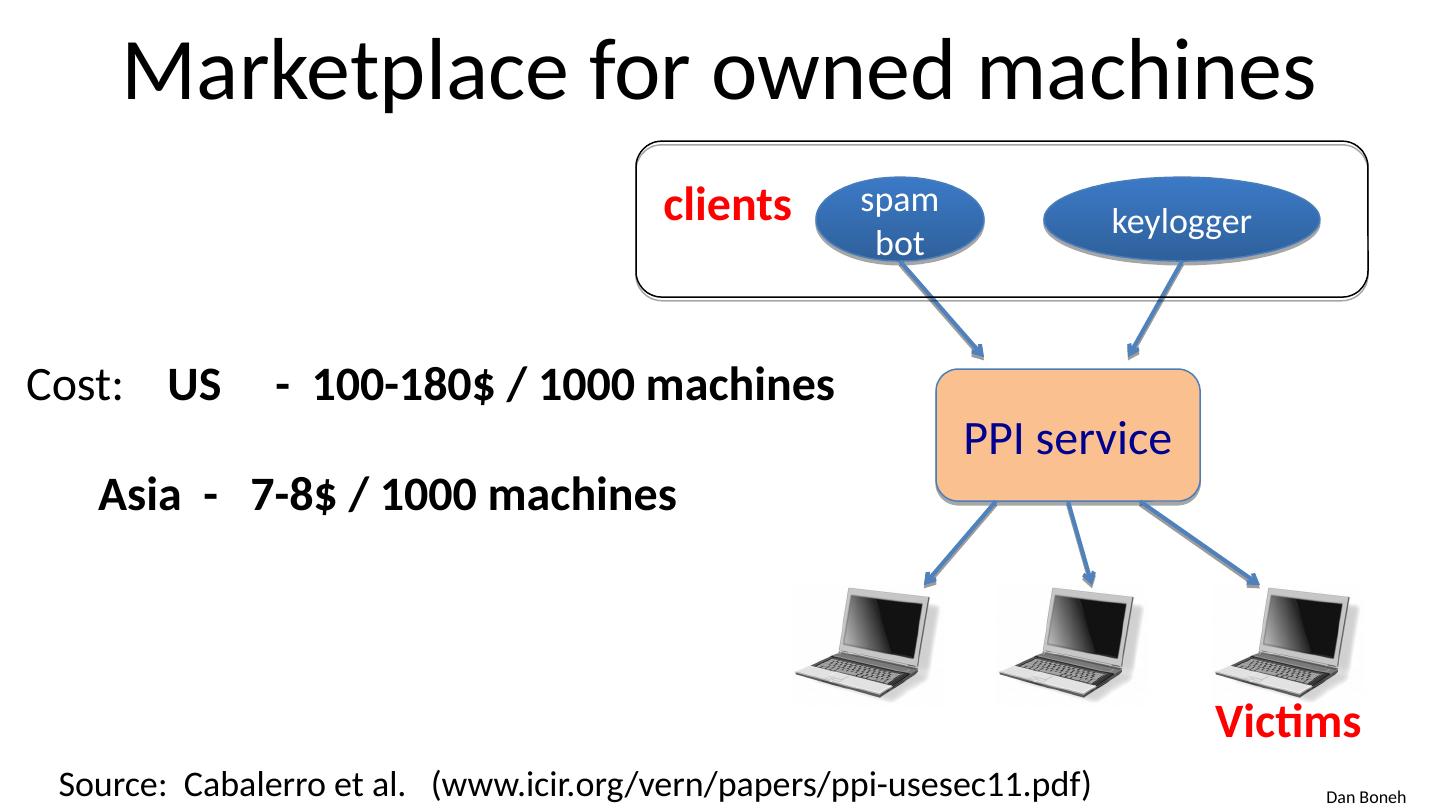
25 .Marketplace for owned machines Pay-per-install (PPI) services PPI operation: Own victim’s machine Download and install client’s code Charge client Source: Cabalerro et al. ( www.icir.org / vern /papers/ppi-usesec11.pdf) spam bot keylogger clients PPI service Victims
26 .Marketplace for owned machines Source: Cabalerro et al. ( www.icir.org / vern /papers/ppi-usesec11.pdf) spam bot keylogger clients PPI service Victims Cost: US - 100-180$ / 1000 machines Asia - 7-8$ / 1000 machines
27 .This course Goals: Be aware of exploit techniques Learn to defend and avoid common exploits Learn to architect secure systems
28 .This course Part 1: basics (architecting for security) Securing apps, OS, and legacy code Isolation, authentication, and access control Part 2: Web security (defending against a web attacker) Building robust web sites, understand the browser security model Part 3: network security (defending against a network attacker) Monitoring and architecting secure networks. Part 4: securing mobile applications
29 .Don’t try this at home !