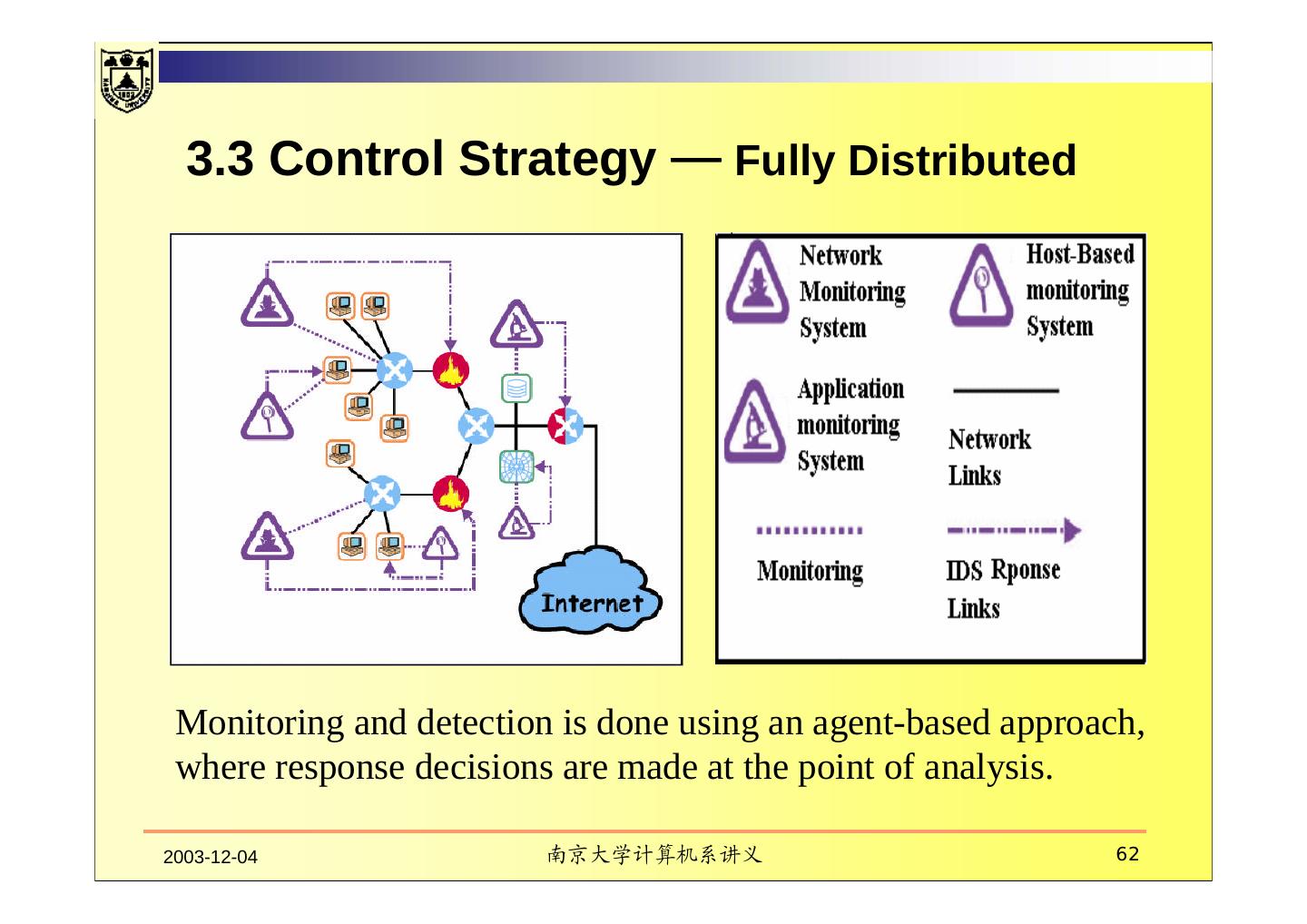
- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
计算机系统信息安全:入侵检测技术
展开查看详情
1 .Chapter 13 Intrusion Detect system
2 . References [1] Rebecca Bace, Peter Mell, Intrusion Detection Systems, NIST Special Publication on Intrusion Detection Systems; [2] Dorothy E. Denning, An Intrusion-Detection Model, IEEE Trans. Software Engineering, Vol. SE-13, No. 2, 1987, pp222-232. [3] Steven R. Snapp, et al. , DIDS (Distributed Intrusion Detection System) - Motivation, Architecture, and An Early Prototype. 2003-12-04 南京大学计算机系讲义 2
3 . [4] Jelena Mirkovic, Janice Martin and Peter Reiher, A Taxonomy of DDoS Attacks and DDoS Defense Mechanisms, Computer Science Department, University of California, Los Angeles, Technical report #020018. [5] Giovanni Vigna and Richard A. Kemmerer, NetSTAT: A Network-based Intrusion Detection Approach, Department of Computer Science, University of California Santa Barbara. 2003-12-04 南京大学计算机系讲义 3
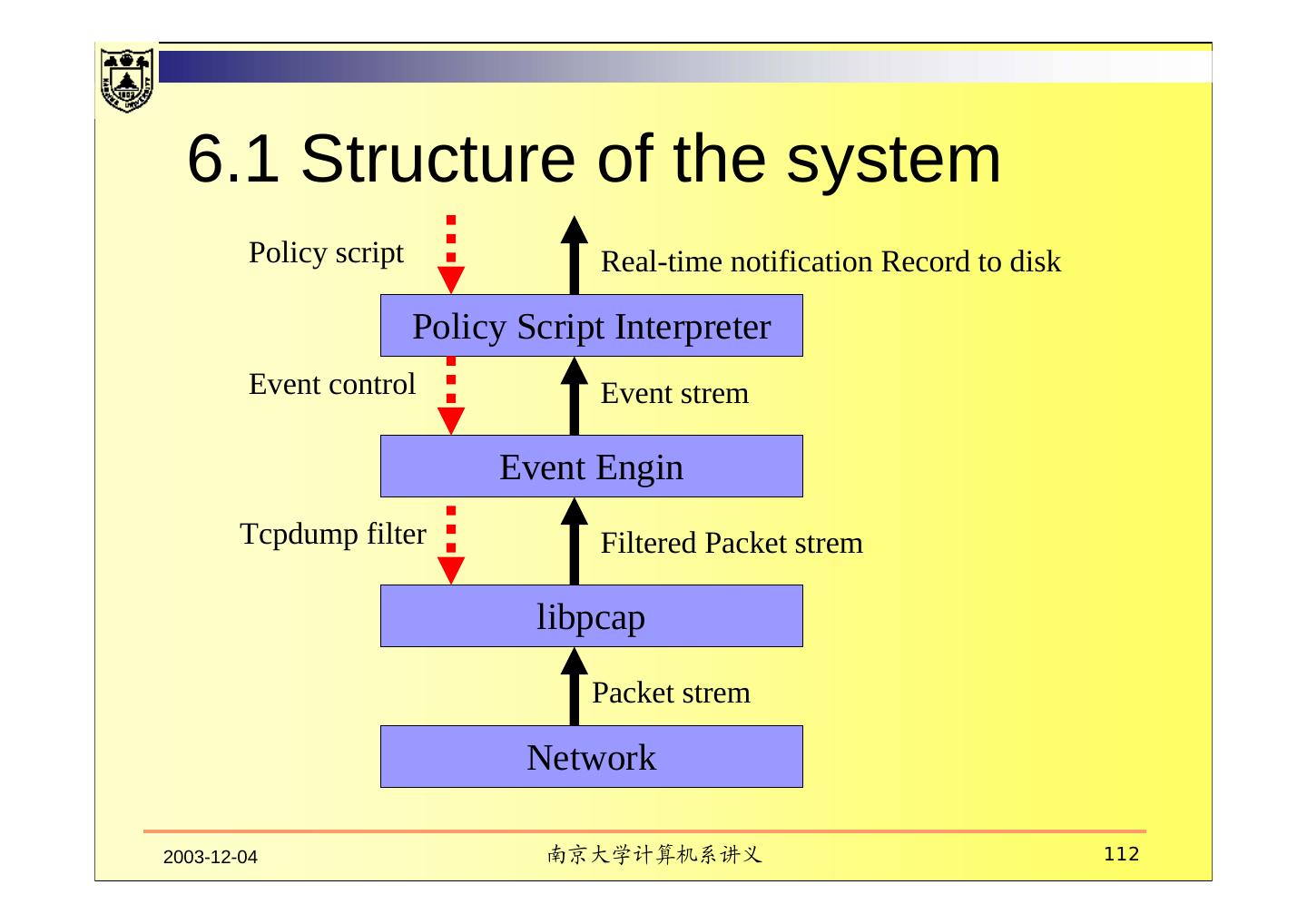
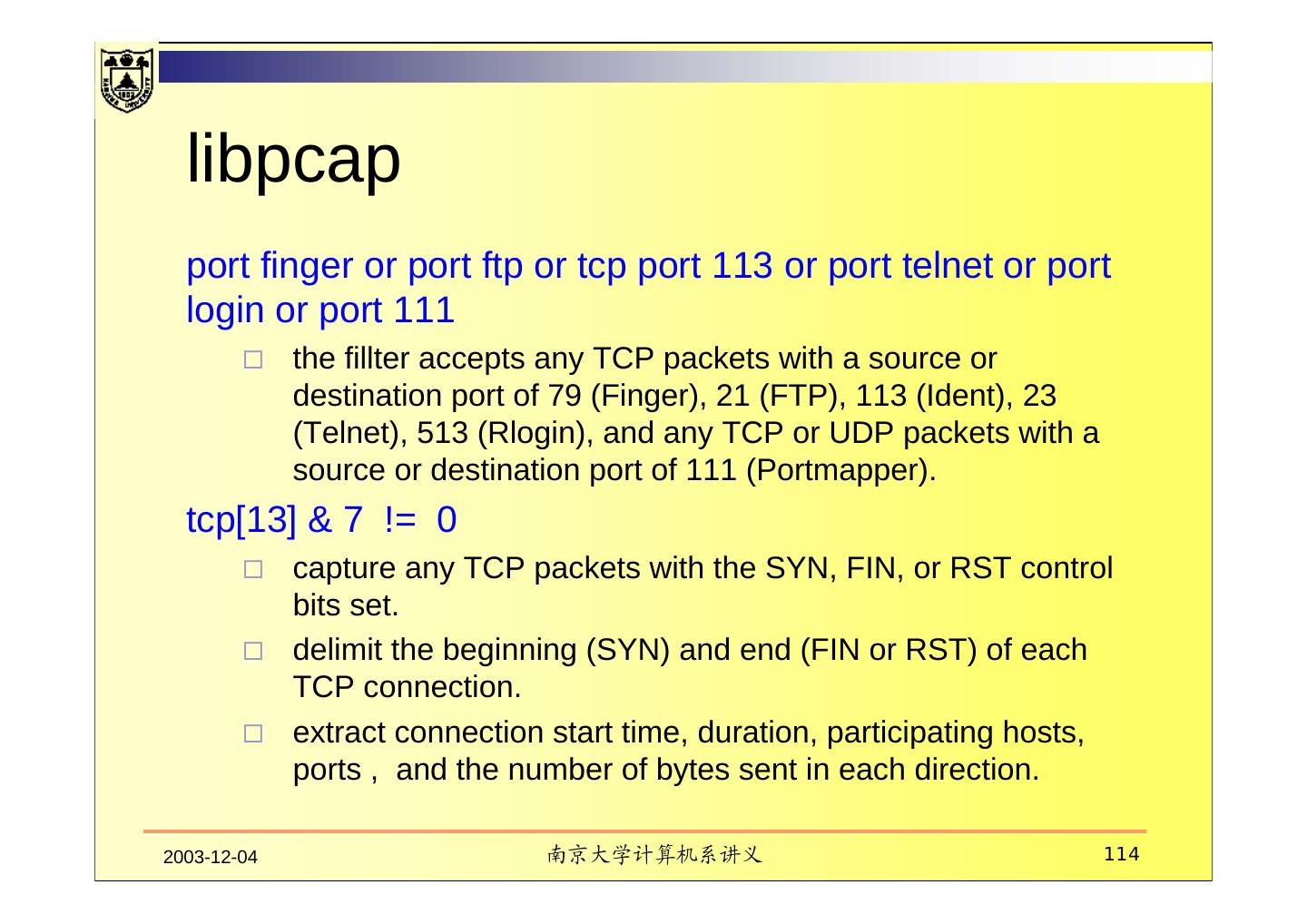
4 . Contents 1. Introduction 2. IDS Models 3. Major types of IDS 4. Deploying IDS 5. NetSTAT 6. BRO 7. Overview of DDOS detection 8. IP traceback 9. Strengths and Limitations of IDS 2003-12-04 南京大学计算机系讲义 4
5 . 1. Introduction Understand what security goals intrusion detection mechanisms serve; How to select and configure intrusion detection systems for their specific system and network environments; How to manage the output of intrusion detection systems; How to integrate intrusion detection functions with the rest of the organizational security infrastructure. 2003-12-04 南京大学计算机系讲义 5
6 . What is a IDS Intrusions caused by attackers accessing the systems from the Internet; authorized users of the systems who attempt to gain additional privileges for which they are not authorized, authorized users who misuse the privileges given them. Intrusion detection monitoring the events occurring in a computer system or network analyzing them for signs of intrusions, defined as attempts to compromise the confidentiality, integrity, availability, or to bypass the security mechanisms of a computer or network. Intrusion Detection Systems software or hardware products that automate this monitoring and analysis process. 2003-12-04 南京大学计算机系讲义 6
7 . 为什么需要IDS (1) Preventing problems increasing the perceived risk of discovery increasing punishment of attackers affect the behavior of individual users 2003-12-04 南京大学计算机系讲义 7
8 . Why should IDS (2) Detecting problems that are not prevented by other security measures The operating systems cannot be patched or updated. Administrators sometimes have neither sufficient time nor resource to track and install all the necessary patches. Both users and administrators make errors in configuring and using systems. Discrepancies of an organization’s procedural computer use policy. Flaws and vulnerabilities are discovered on a daily basis. 2003-12-04 南京大学计算机系讲义 8
9 . Why should IDS (3) Detecting the preambles to attacks Adversaries attack a system typically in predictable stages. probing or examining a system. searching for an optimal point of entry. With no IDS, the attacker is free to thoroughly examine the system with little risk of discovery or retribution. Network with an IDS monitoring its operations presents a much more formidable challenge to that attacker. IDS will observe the probes, will identify them as suspicious, may actively block the attacker’s access, will alert security personnel. 2003-12-04 南京大学计算机系讲义 9
10 . Why should IDS (4) Documenting the existing threat IDS verify, itemize, and characterize the threat. Assisting you in making sound decisions regarding your allocation of computer security resources. The information from IDS regarding the source and nature of attacks, allows you to make decisions regarding security strategy. 2003-12-04 南京大学计算机系讲义 10
11 . Why should IDS (5) Quality control for security design and administration Highlight flaws in the design and management of security for the system Supports security management correcting those deficiencies before they cause an incident. Providing useful information about actual intrusions Collect relevant, detailed, and trustworthy information about the attack Supports incident handling and recovery efforts. 2003-12-04 南京大学计算机系讲义 11
12 .2. IDS Models
13 . 2.1 Intrusion Detection Expert System (IDES) Dorothy E. Denning, An Intrusion-Detection Model, IEEE Trans. Software Engineering, Vol. SE-13, No. 2, 1987, pp222-232. 2003-12-04 南京大学计算机系讲义 13
14 . Hypothesis exploitation of a system's vulnerabilities involves abnormal use, of the system; therefore, security violations could be detected from abnormal patterns of system usage. 2003-12-04 南京大学计算机系讲义 14
15 . Hypothesis Examples(1) Attempted break-in Someone attempting to break into a system might generate an abnormally high rate of password failures with respect to a single account or the system as a whole. Masquerading or successful break-in Someone logging into a system through an unauthorized account and password might have a different login time, location, or connection type from that of the account's legitimate user. He might spend most of his time browsing through directories and executing system status commands The legitimate user might concentrate on editing or compiling and linking programs. 2003-12-04 南京大学计算机系讲义 15
16 . Hypothesis Examples(2) Penetration by legitimate user A user attempting to penetrate the security mechanisms in the operating system might execute different programs or trigger more protection violations from attempts to access unauthorized files or programs. If his attempt succeeds, he will have access to commands and files not normally permitted to him. Leakage by legitimate user A user trying to leak sensitive documents might log into the system at unusual times or route data to remote printers not normally used. 2003-12-04 南京大学计算机系讲义 16
17 . Hypothesis Examples(3) Inference by legitimate user A user attempting to obtain unauthorized data from a database through aggregation and inference might retrieve more records than usual. Trojan horse The behavior of a Trojan horse planted in or substituted for a program may differ from the legitimate program in terms of its CPU time or 1/0 activity. Denial-of-Service An intruder able to monopolize a resource (e.g., network) might have abnormally high activity with respect to the resource, while activity for all other users is abnormally low. 2003-12-04 南京大学计算机系讲义 17
18 . The model is independent of any particular System application environment system vulnerability type of intrusion 2003-12-04 南京大学计算机系讲义 18
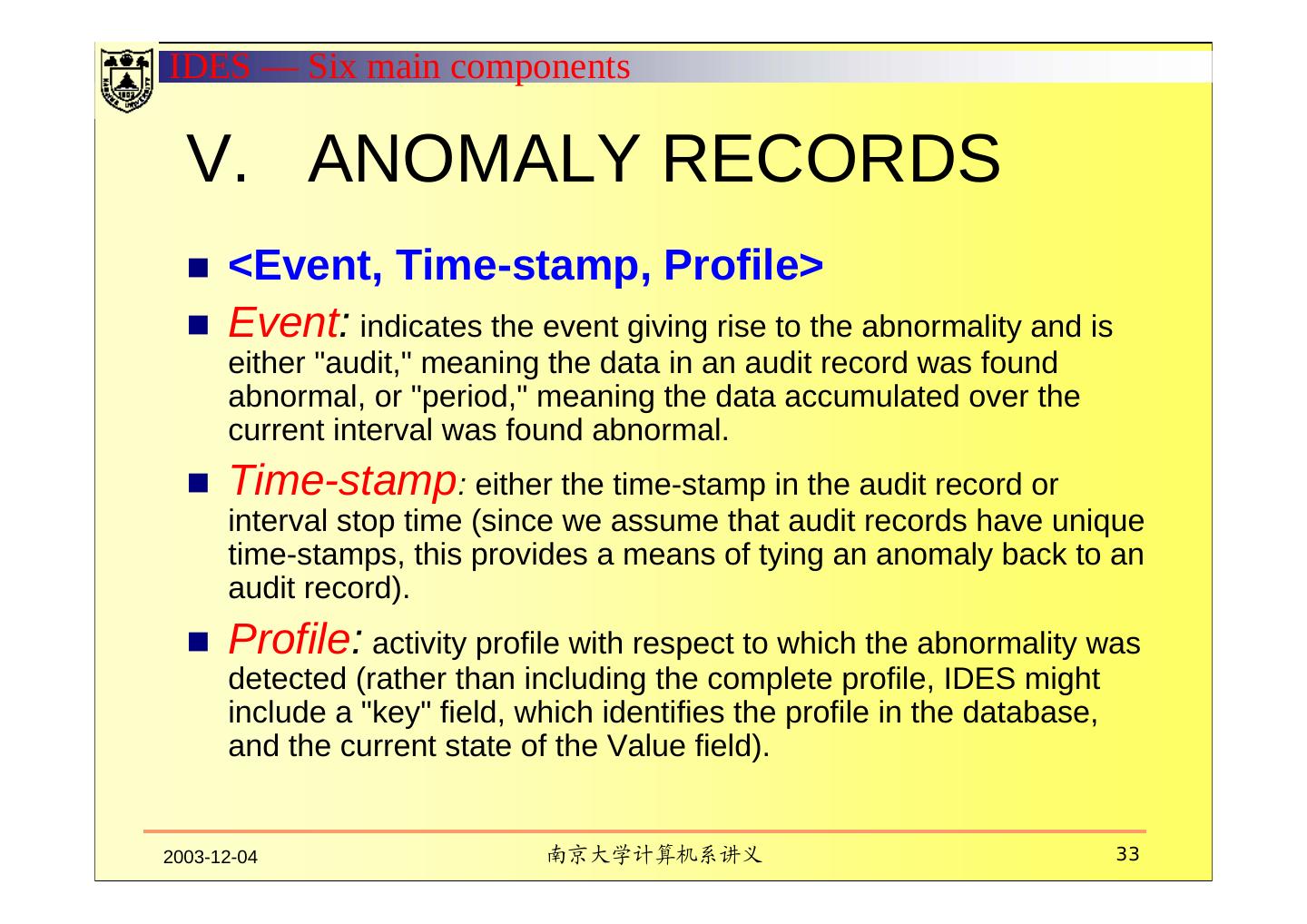
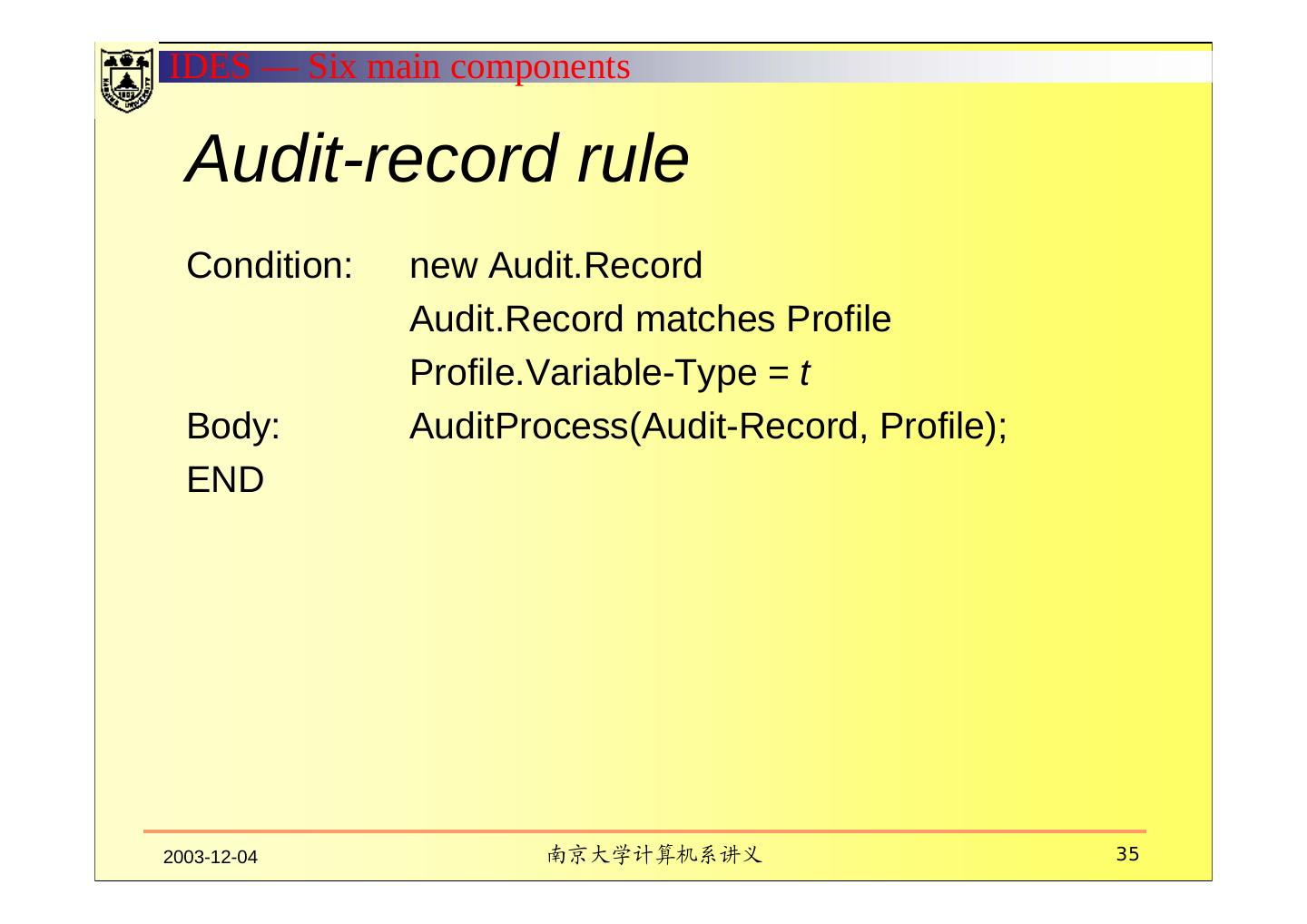
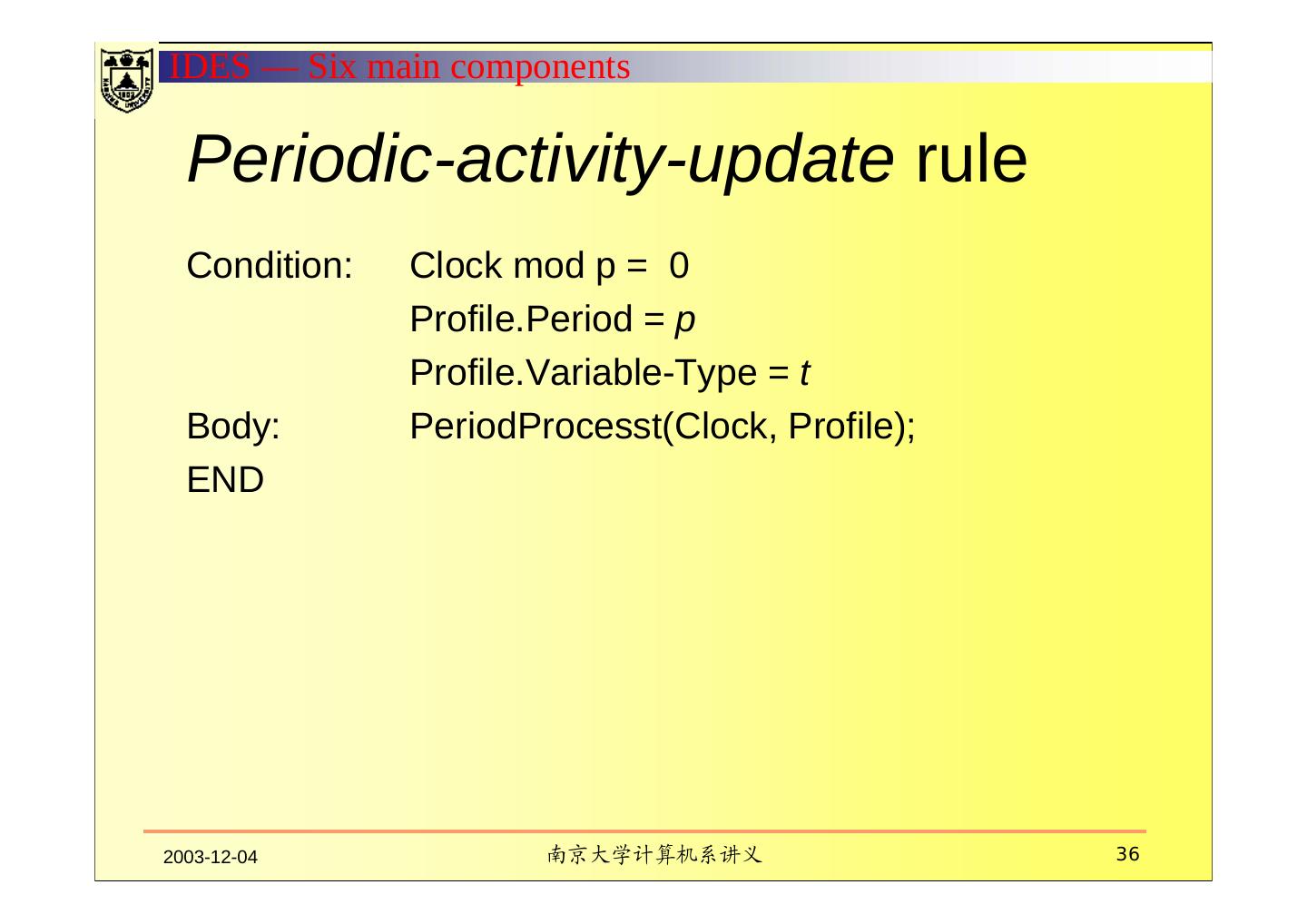
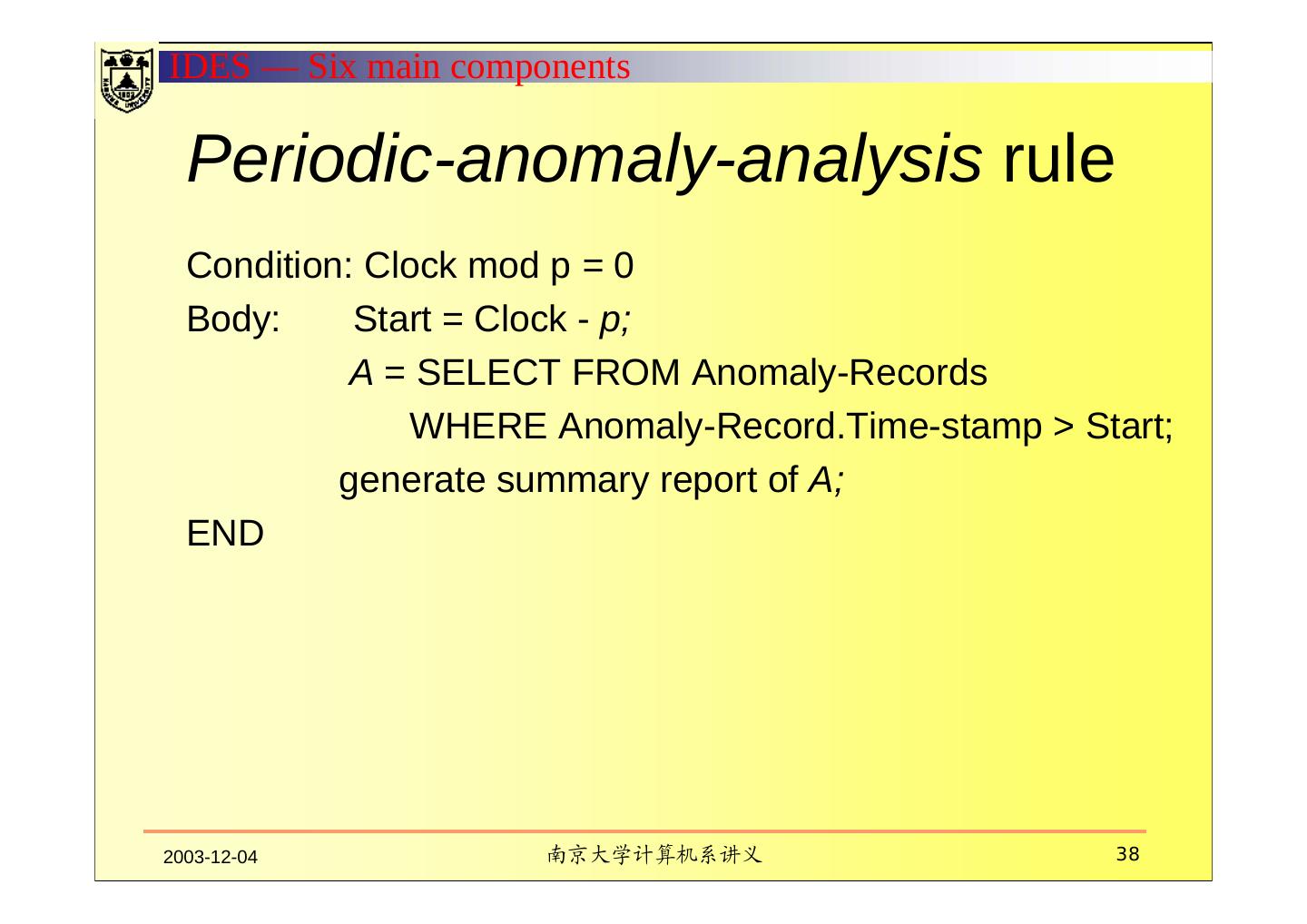
19 . Six main components Subjects Initiators of activity on a target system Objects Resources managed by the system-files, commands, devices Audit records Generated by the target system in response to actions performed or attempted by subjects on objects-user login, command execution, file access, etc. Profiles Structures that characterize the behavior of subjects with respect to objects in terms of statistical metrics and models of observed activity. Profiles are automatically generated and initialized from templates. Anomaly records Generated when abnormal behavior is detected. Activity rules Actions taken when some condition is satisfied, which update profiles, detect abnormal behavior, relate anomalies to suspected intrusions, and produce reports. 2003-12-04 南京大学计算机系讲义 19
20 .IDES — Six main components I. Subjects I. Subjects are the initiators of actions II. A terminal user III. A process acting on behalf of users or groups of users IV. The system itself V. Subjects may be grouped into different classes (e.g., user groups) for the purpose of controlling access to objects in the system. 2003-12-04 南京大学计算机系讲义 20
21 . II. Objects the receptors of actions Files Programs Messages Records Terminals Printers user- or program-created structures 2003-12-04 南京大学计算机系讲义 21
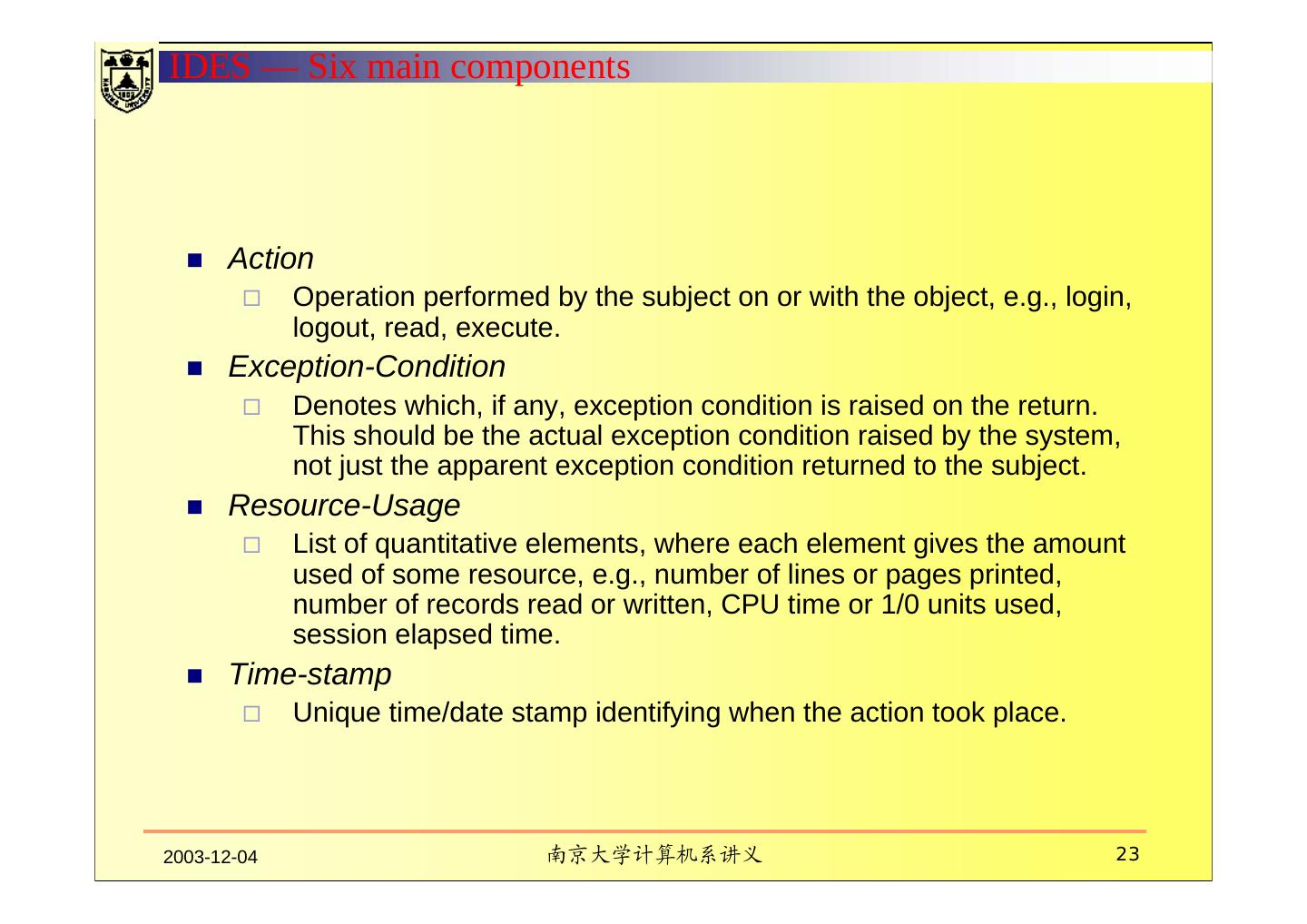
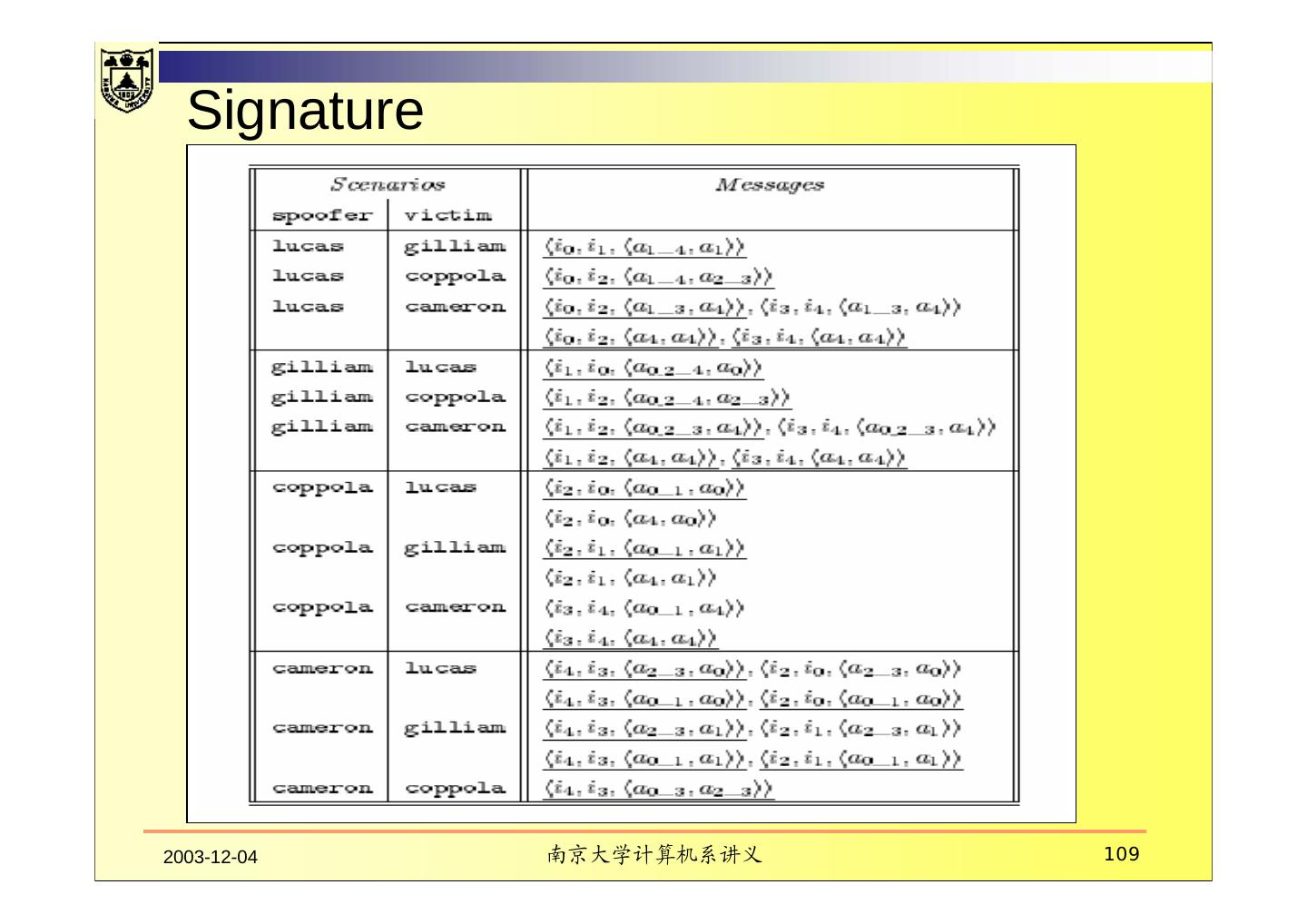
22 .IDES — Six main components III. AUDIT RECORDS Audit Records are 6-tuples representing actions performed by subjects on objects: 1. <Subject, 2. Action, 3. Object, 4. Exception-Condition, 5. Resource-Usage, 6. Time-stamp > 2003-12-04 南京大学计算机系讲义 22
23 .IDES — Six main components Action Operation performed by the subject on or with the object, e.g., login, logout, read, execute. Exception-Condition Denotes which, if any, exception condition is raised on the return. This should be the actual exception condition raised by the system, not just the apparent exception condition returned to the subject. Resource-Usage List of quantitative elements, where each element gives the amount used of some resource, e.g., number of lines or pages printed, number of records read or written, CPU time or 1/0 units used, session elapsed time. Time-stamp Unique time/date stamp identifying when the action took place. 2003-12-04 南京大学计算机系讲义 23
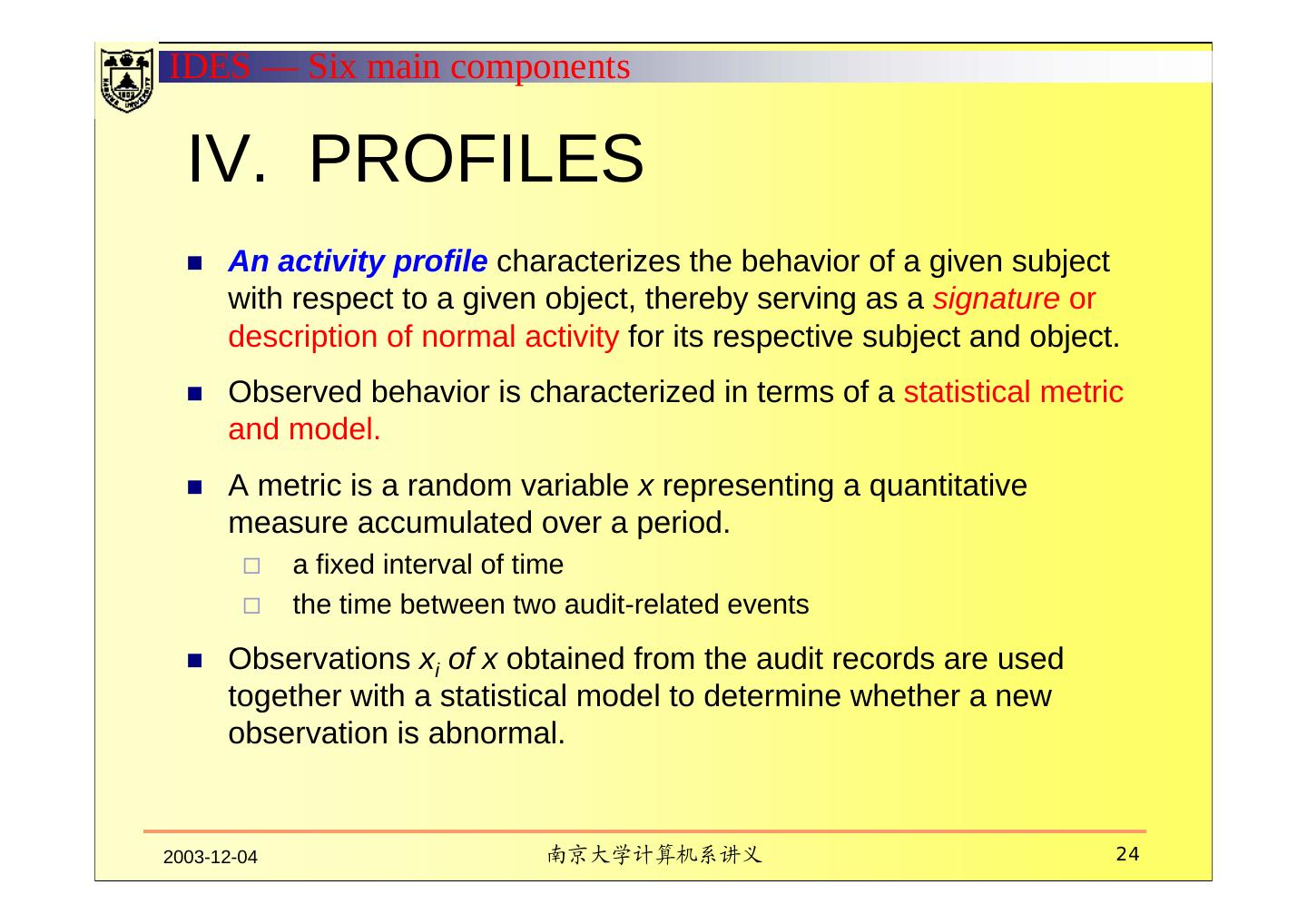
24 .IDES — Six main components IV. PROFILES An activity profile characterizes the behavior of a given subject with respect to a given object, thereby serving as a signature or description of normal activity for its respective subject and object. Observed behavior is characterized in terms of a statistical metric and model. A metric is a random variable x representing a quantitative measure accumulated over a period. a fixed interval of time the time between two audit-related events Observations xi of x obtained from the audit records are used together with a statistical model to determine whether a new observation is abnormal. 2003-12-04 南京大学计算机系讲义 24
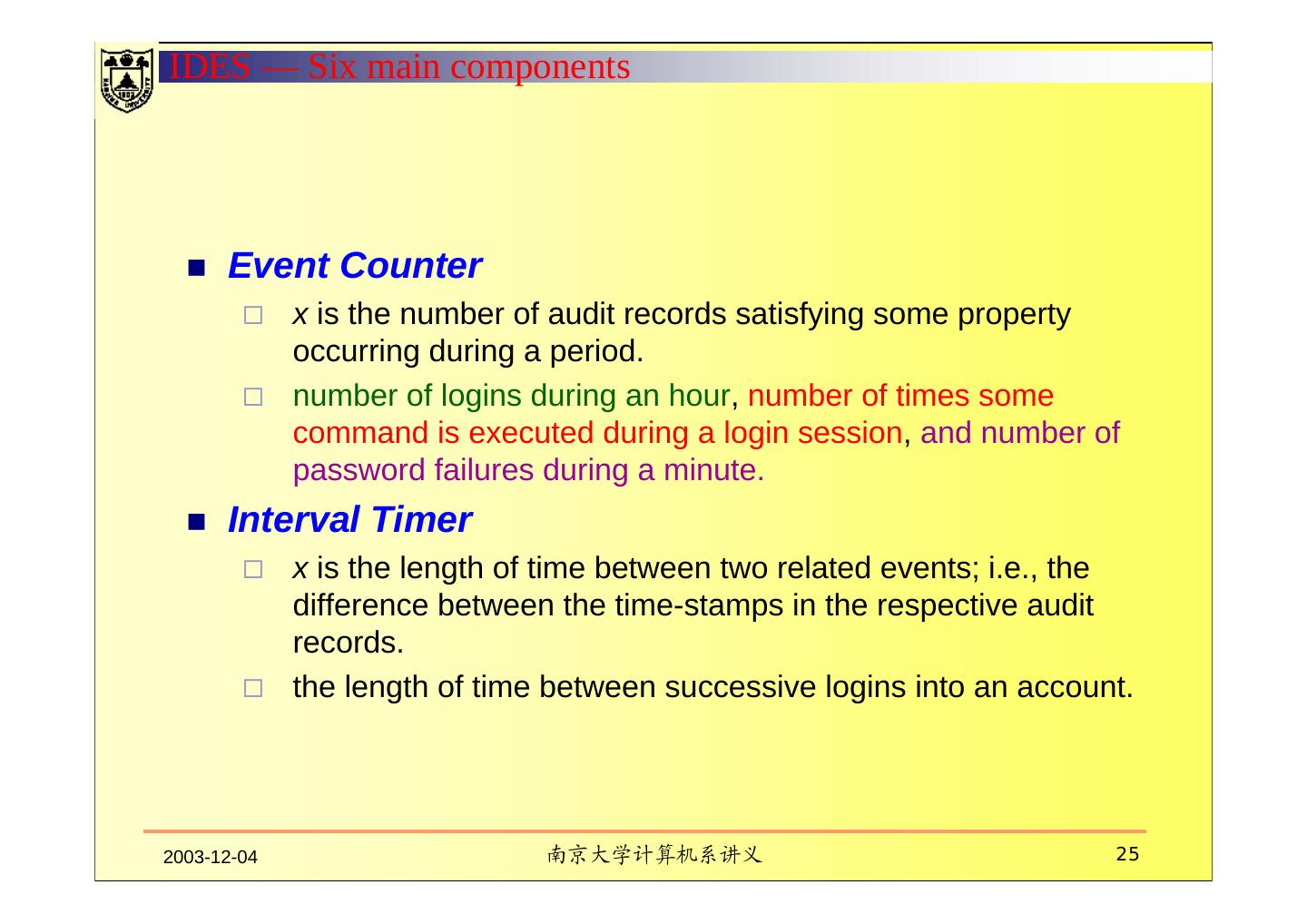
25 .IDES — Six main components Event Counter x is the number of audit records satisfying some property occurring during a period. number of logins during an hour, number of times some command is executed during a login session, and number of password failures during a minute. Interval Timer x is the length of time between two related events; i.e., the difference between the time-stamps in the respective audit records. the length of time between successive logins into an account. 2003-12-04 南京大学计算机系讲义 25
26 .IDES — Six main components Resource Measure x is the quantity of resources consumed by some action during a period. the total number of pages printed by a user per day total amount of CPU time consumed by some program during a single execution 2003-12-04 南京大学计算机系讲义 26
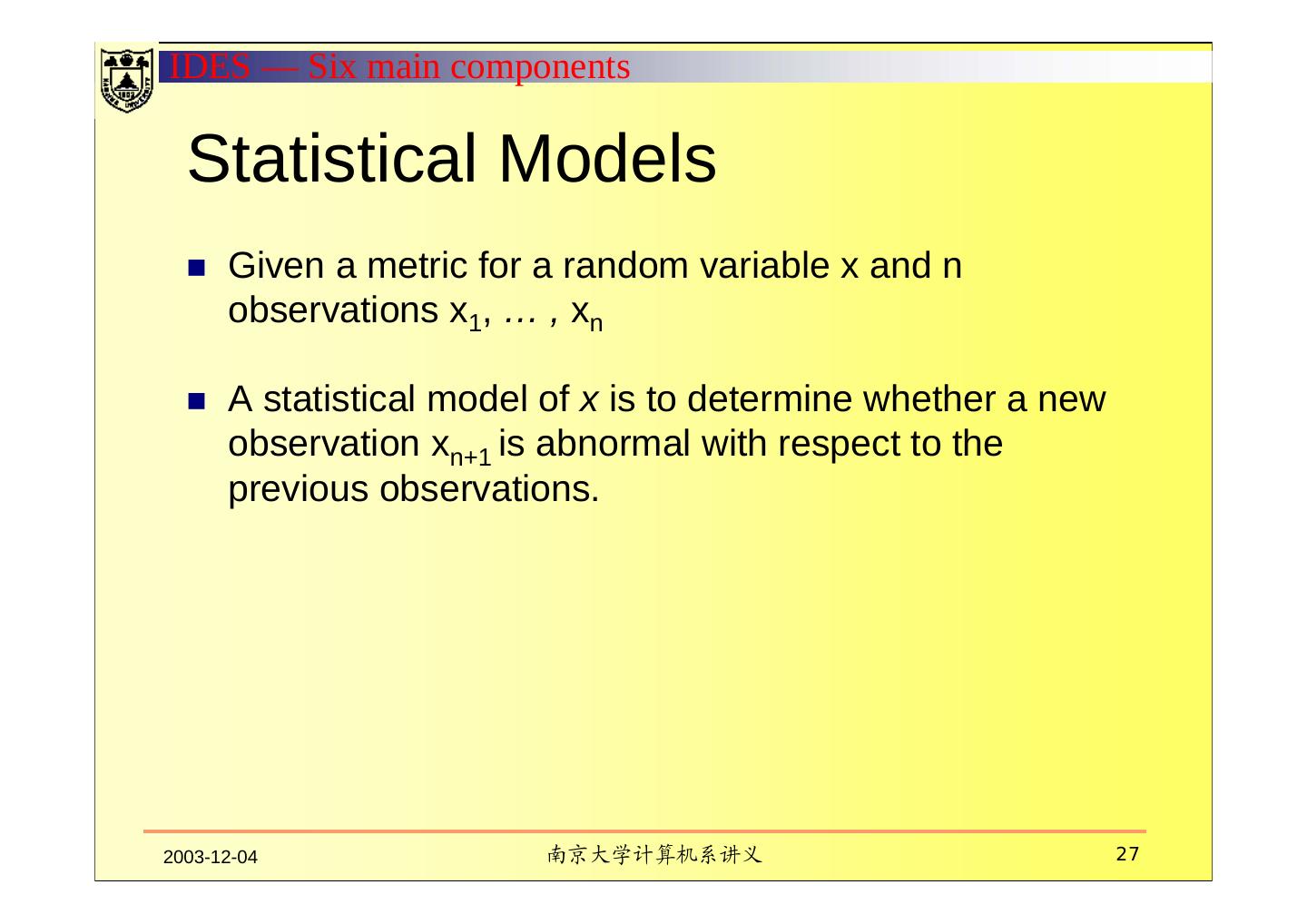
27 .IDES — Six main components Statistical Models Given a metric for a random variable x and n observations x1, … , xn A statistical model of x is to determine whether a new observation xn+1 is abnormal with respect to the previous observations. 2003-12-04 南京大学计算机系讲义 27
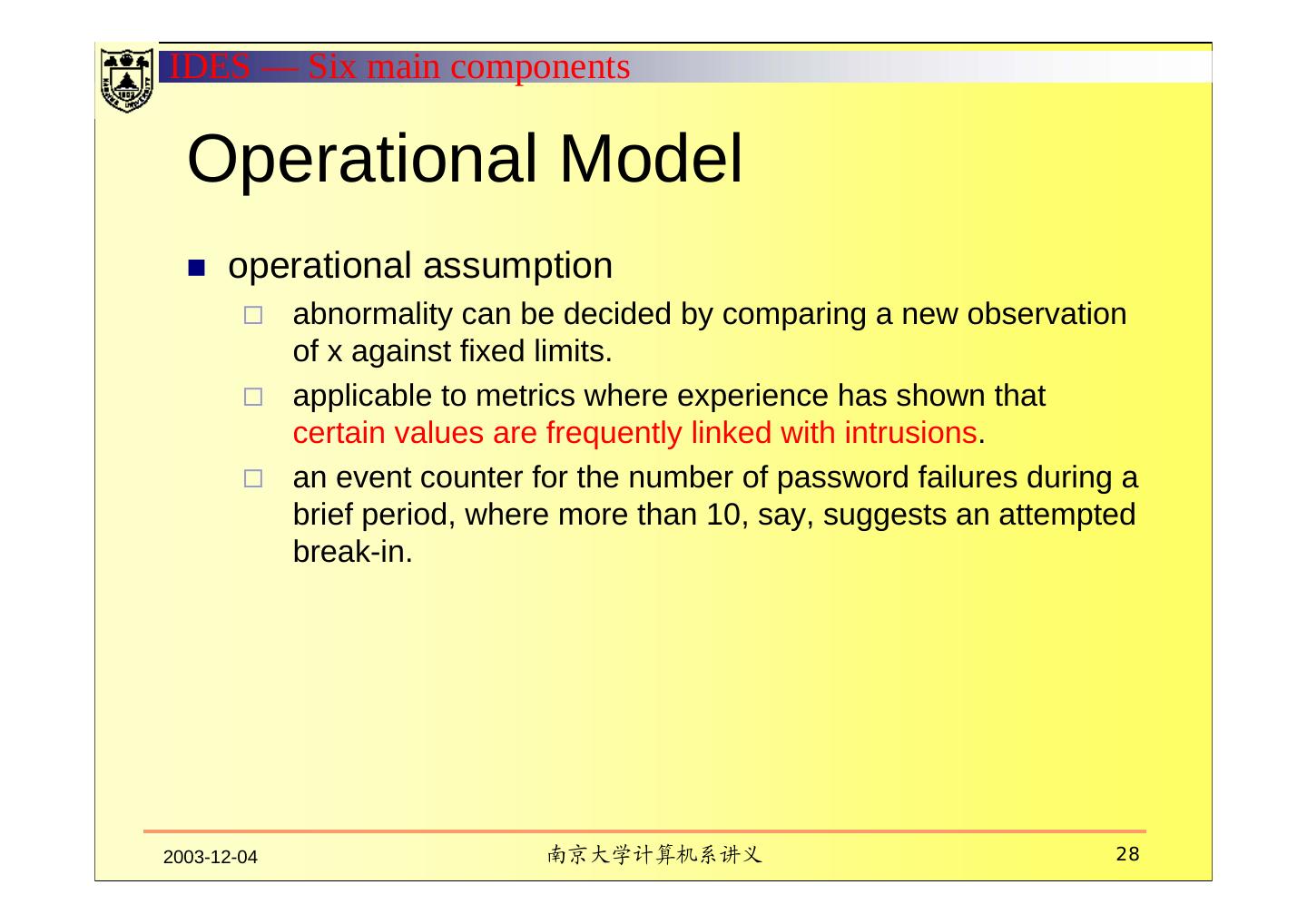
28 .IDES — Six main components Operational Model operational assumption abnormality can be decided by comparing a new observation of x against fixed limits. applicable to metrics where experience has shown that certain values are frequently linked with intrusions. an event counter for the number of password failures during a brief period, where more than 10, say, suggests an attempted break-in. 2003-12-04 南京大学计算机系讲义 28
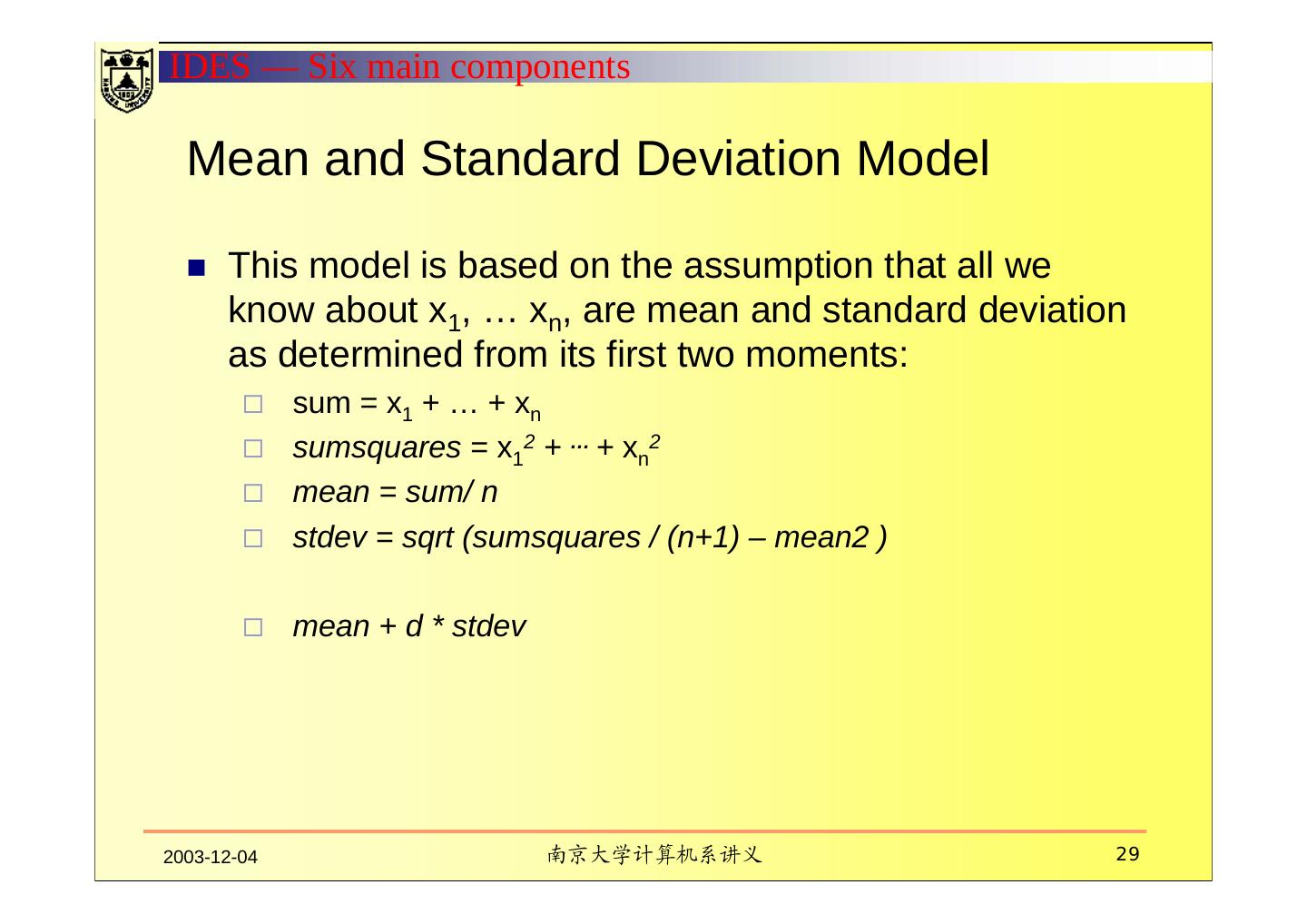
29 .IDES — Six main components Mean and Standard Deviation Model This model is based on the assumption that all we know about x1, … xn, are mean and standard deviation as determined from its first two moments: sum = x1 + … + xn sumsquares = x12 + … + xn2 mean = sum/ n stdev = sqrt (sumsquares / (n+1) – mean2 ) mean + d * stdev 2003-12-04 南京大学计算机系讲义 29