- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
计算机系统信息安全:网络防火墙技术
展开查看详情
1 . Firewall Design 2003-11-27 1
2 . reference D. Brent Chapman & Elizabeth D. Zwicky, Building Internet Firewalls, 1st Edition September 1995. Chris Hare, Karanjit Siyan, Internet Firewalls and Network Security, New Ricers Publishing, Indeanapolis, Indiana, 1995. 刘成勇,刘明刚,王明举等译,网络安全技术系列 丛书,Internet防火墙与网络安全,机械工业出版 社,西蒙与舒斯特国际出版公司,1998年5月第1 版。 2003-11-27 南京大学计算机系讲义 2
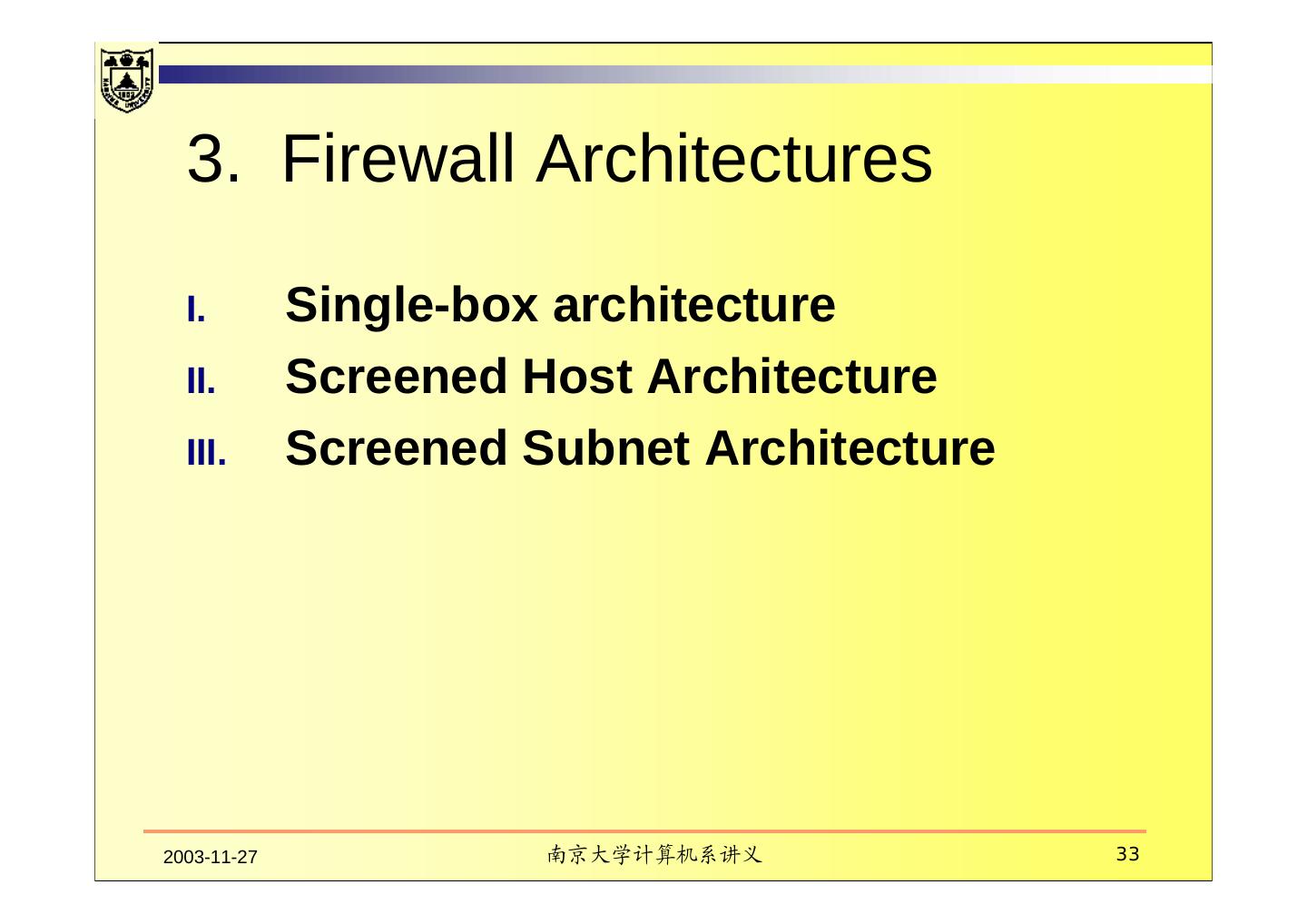
3 . Contents I. Introduction II. Firewall techniques III. Firewall Architectures IV. Components of a firewall 2003-11-27 南京大学计算机系讲义 3
4 . 1. Introduction 2003-11-27 南京大学计算机系讲义 4
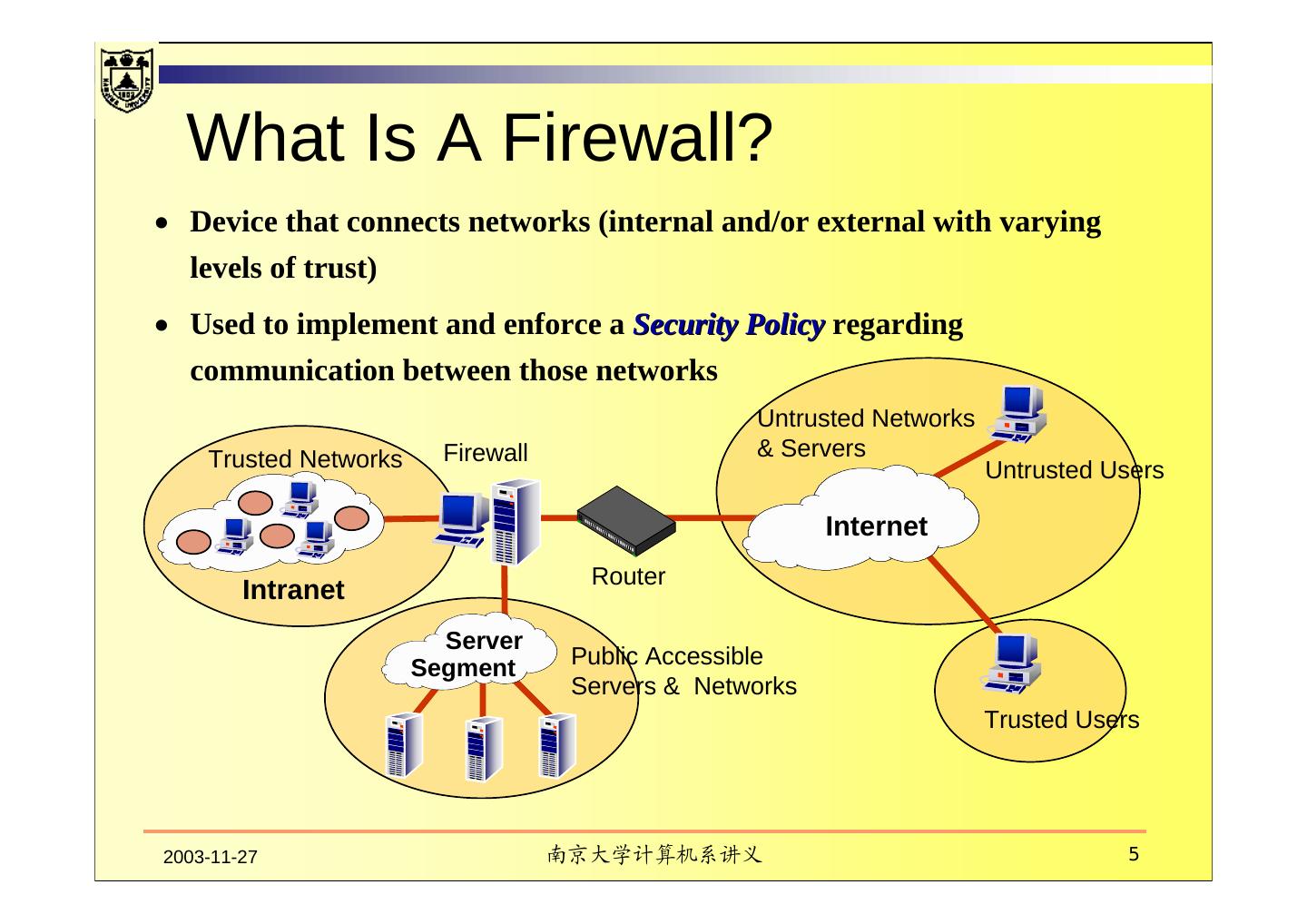
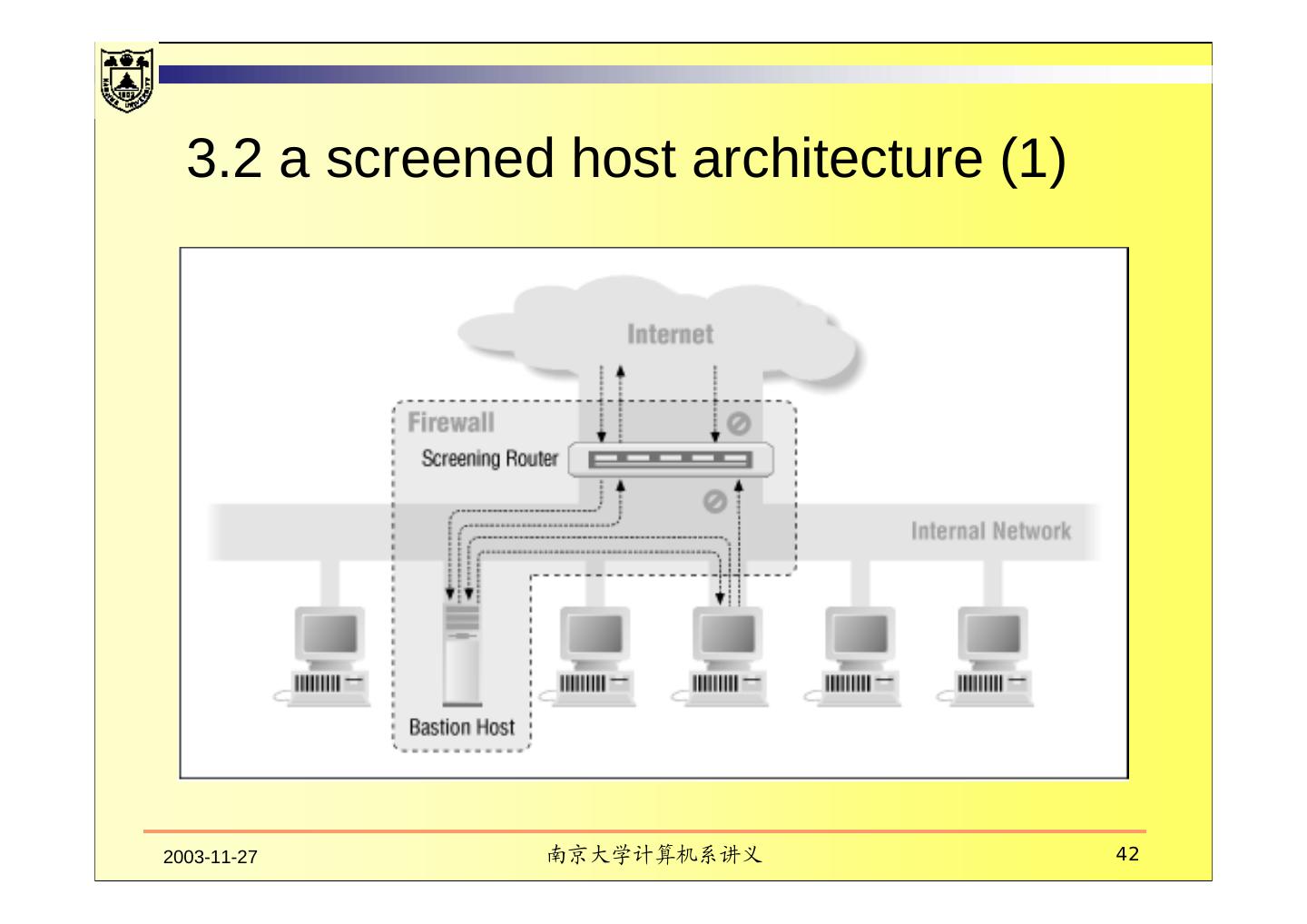
5 . What Is A Firewall? • Device that connects networks (internal and/or external with varying levels of trust) • Used to implement and enforce a Security Policy regarding communication between those networks Untrusted Networks Trusted Networks Firewall & Servers Untrusted Users Internet Router Intranet Server Segment Public Accessible Servers & Networks Trusted Users 2003-11-27 南京大学计算机系讲义 5
6 . Firewall can do A firewall is a focus for security decisions All traffic in and out must pass through this single , narrow choke point which connects your network to Internet. A firewall can enforce a security policy. A firewall can log Internet activity efficiently. A firewall limits your exposure Firewall can be used to keep one section of your site’s network separate from another section. 2003-11-27 南京大学计算机系讲义 6
7 . Firewall can’t do A firewall can’t protect you against malicious insiders; A firewall can’t protect you against connections that don’t go through it A firewall can’t protect against completely new threats A firewall can’t fully protect against viruses A firewall can’t set itself up correctly 2003-11-27 南京大学计算机系讲义 7
8 .2003-11-27 南京大学计算机系讲义 8
9 . 2. Firewall techniques I. Packet filter II. Circuit level firewall III. Application Layer Firewall IV. Dynamic Packet Filter 2003-11-27 南京大学计算机系讲义 9
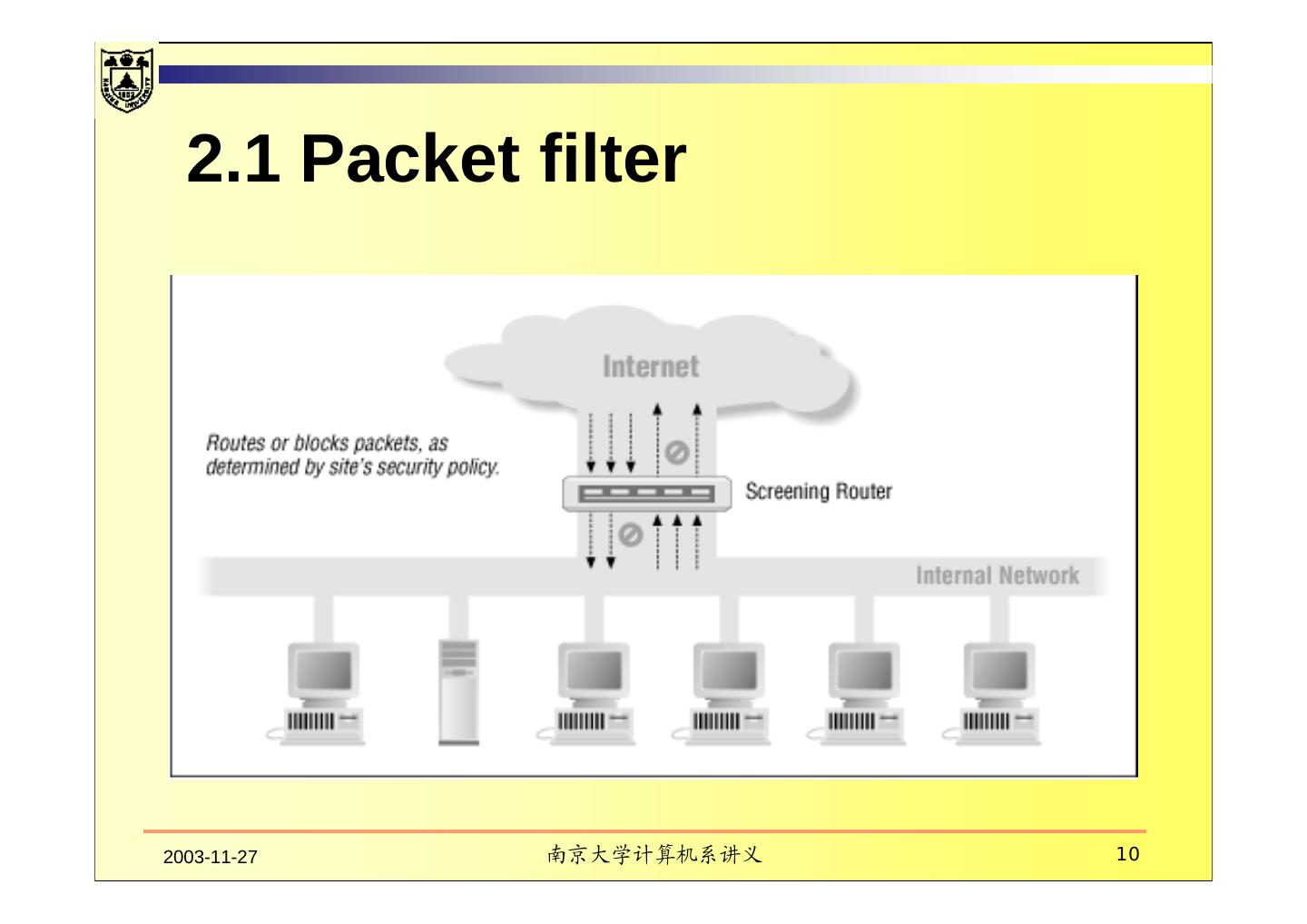
10 . 2.1 Packet filter 2003-11-27 南京大学计算机系讲义 10
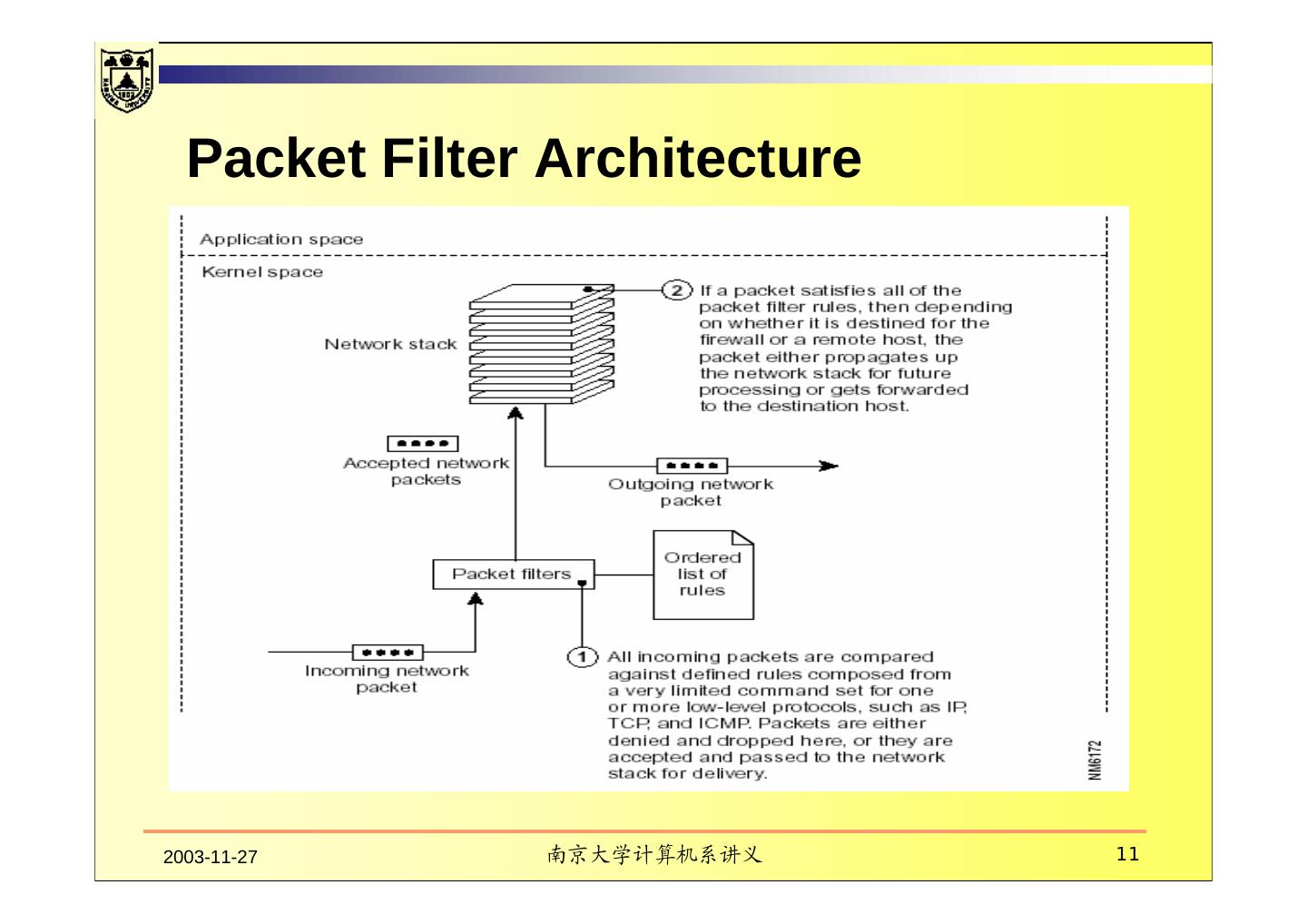
11 . Packet Filter Architecture 2003-11-27 南京大学计算机系讲义 11
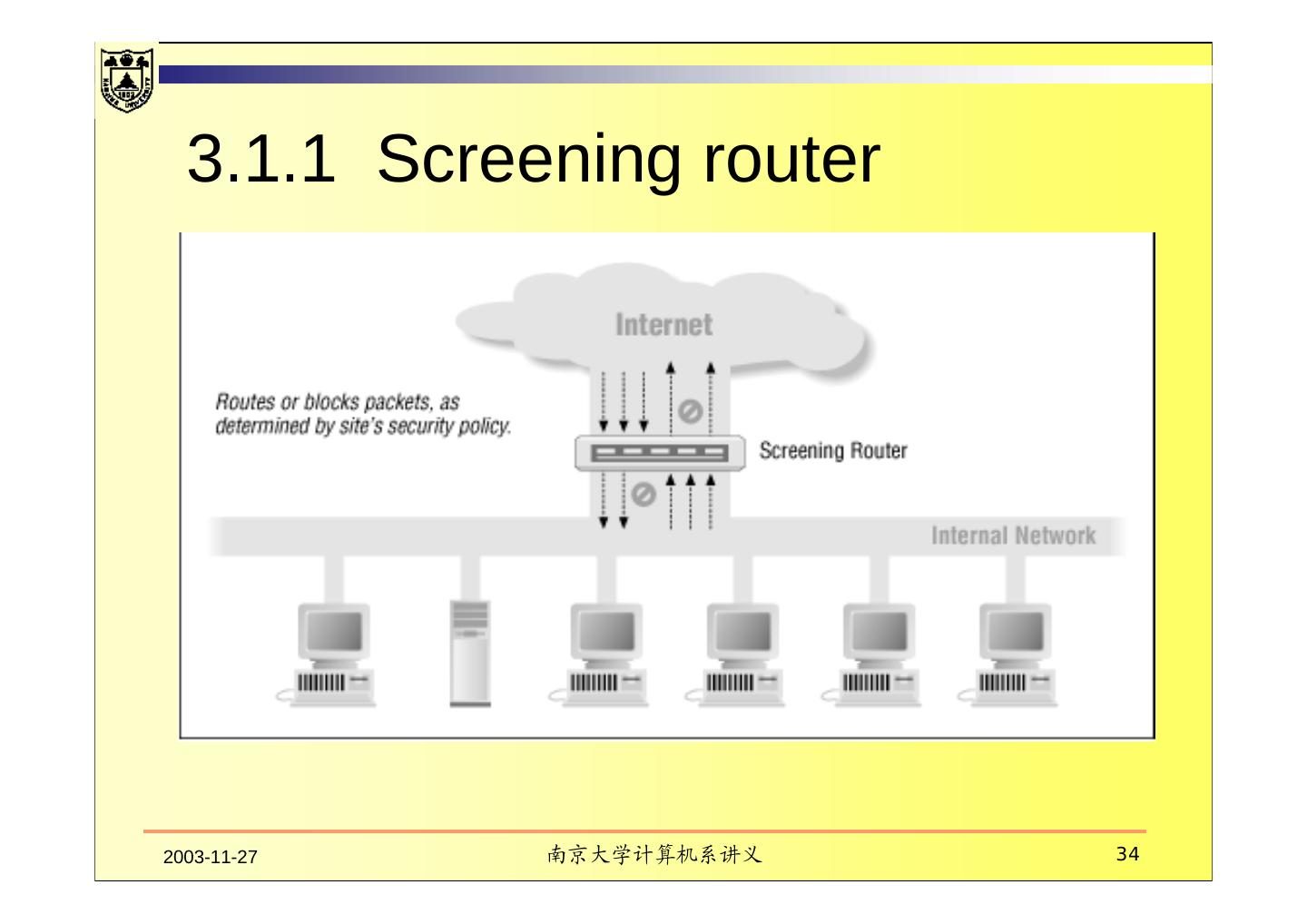
12 . Packet filter control data transfer based on The address the data is (supposedly) coming from The address the data ia going to The session and application ports being used to transfer the data 2003-11-27 南京大学计算机系讲义 12
13 . It let you can say Don’t let anybody use the port used by Telnet to log in from the outside Let everybody send us data over the port used for electronic mail by SMTP. 2003-11-27 南京大学计算机系讲义 13
14 . It won’t let you say This user can Telnet in from outside , but no other users can do so. You can transfer these files byt not those files. Only allow people to send us electronic mail over the port used by SMTP. 2003-11-27 南京大学计算机系讲义 14
15 . Advantages of the packet filtering Packet filters are generally faster than other firewall technologies; They can easily be implemented as hardware solutions; A single rule can help protect an entire network by prohibiting connections between specific Internet sources and internal computers; Packet filters do not require client computers to be specifically configured; In conjunction with network address translation, you can use packet filter firewalls to shield internal IP addresses from external users. 2003-11-27 南京大学计算机系讲义 15
16 . Disadvantages of the packet filtering They are less secure than application layer and circuit level firewalls. They cannot restrict access to protocol subsets for even the most basic services, such as the PUT or GET commands in FTP. They do not keep information about a session or application- derived information. Packet filters do not offer value-added features, such as HTTP object caching, URL filtering, and authentication because they do not understand the protocols being used and cannot discern one from another. 2003-11-27 南京大学计算机系讲义 16
17 . 2.2 Circuit level firewall Operate at the network transport layer Authorized based on addresses Prevent direct connections between one network and another Cannot look at data traffic flowing between one network and another 2003-11-27 南京大学计算机系讲义 17
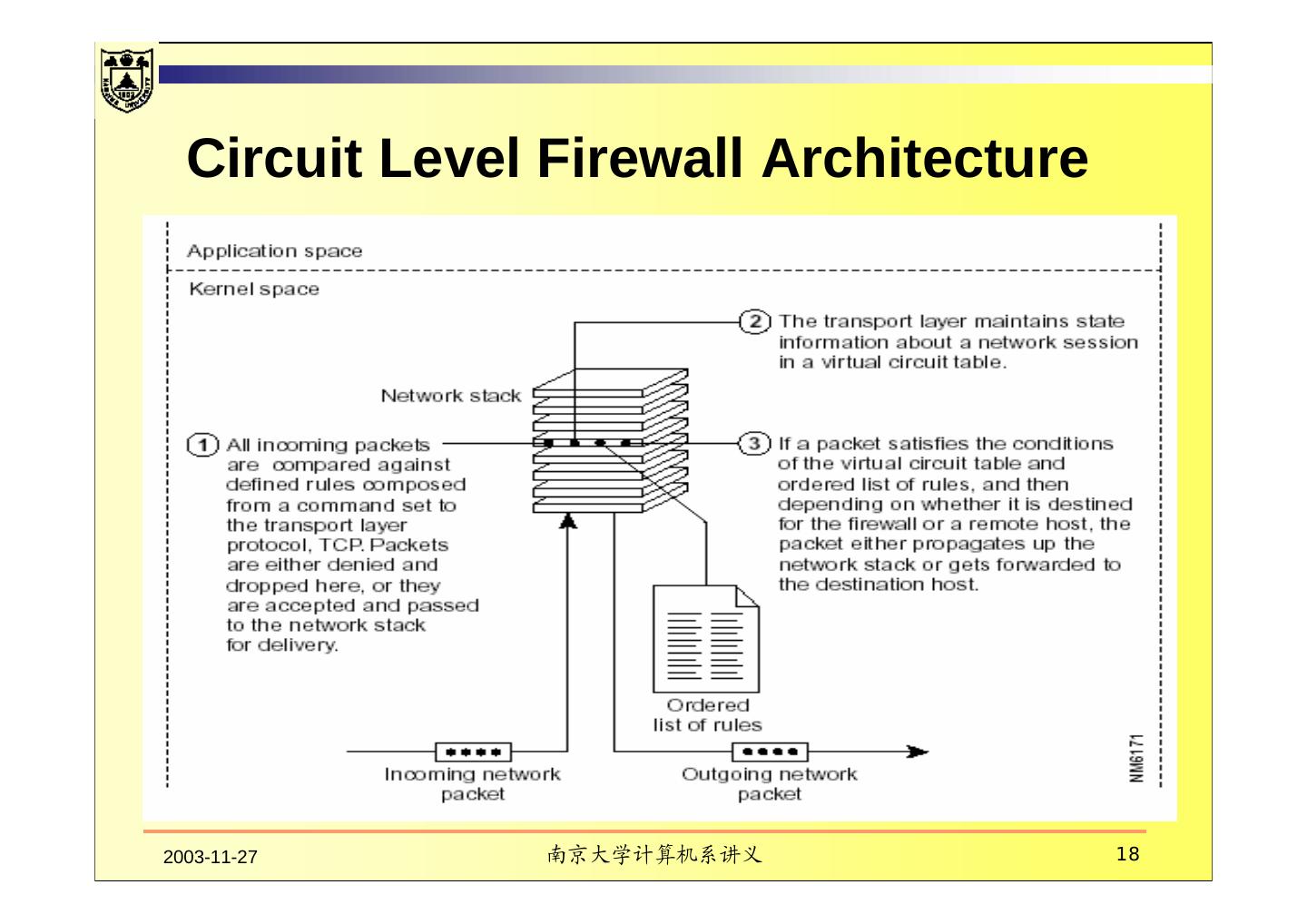
18 . Circuit Level Firewall Architecture 2003-11-27 南京大学计算机系讲义 18
19 . To validate a session, a circuit level firewall examines each connection setup to ensure that it follows a legitimate handshake for the transport layer protocol being used The firewall maintains a table of valid connections and lets network packets pass through when it matches an entry in the virtual circuit table. Once a connection is terminated, its table entry is removed, and that virtual circuit between the two peer transport layers is closed. 2003-11-27 南京大学计算机系讲义 19
20 . advantages of circuit level firewalls Circuit level firewalls are generally faster than application layer firewalls. A circuit level firewall can help protect an entire network by prohibiting connections between specific Internet sources and internal computers. In conjunction with network address translation, you can use circuit level firewalls to shield internal IP addresses from external users. 2003-11-27 南京大学计算机系讲义 20
21 . disadvantages of circuit level firewalls Circuit level firewalls cannot perform strict security checks on a higher-level protocol should the need arise. Circuit level firewalls have limited audit event generation abilities but can typically tie a network data packet to an application layer protocol by building limited forms of session state. Circuit level firewalls do not offer value-added features, such as HTTP object caching, URL filtering, and authentication because they do not understand the protocols being used and cannot discern one from another. It can be difficult to test “accept” and “deny” rules. 2003-11-27 南京大学计算机系讲义 21
22 . 2.3 Application Layer Firewall 2003-11-27 南京大学计算机系讲义 22
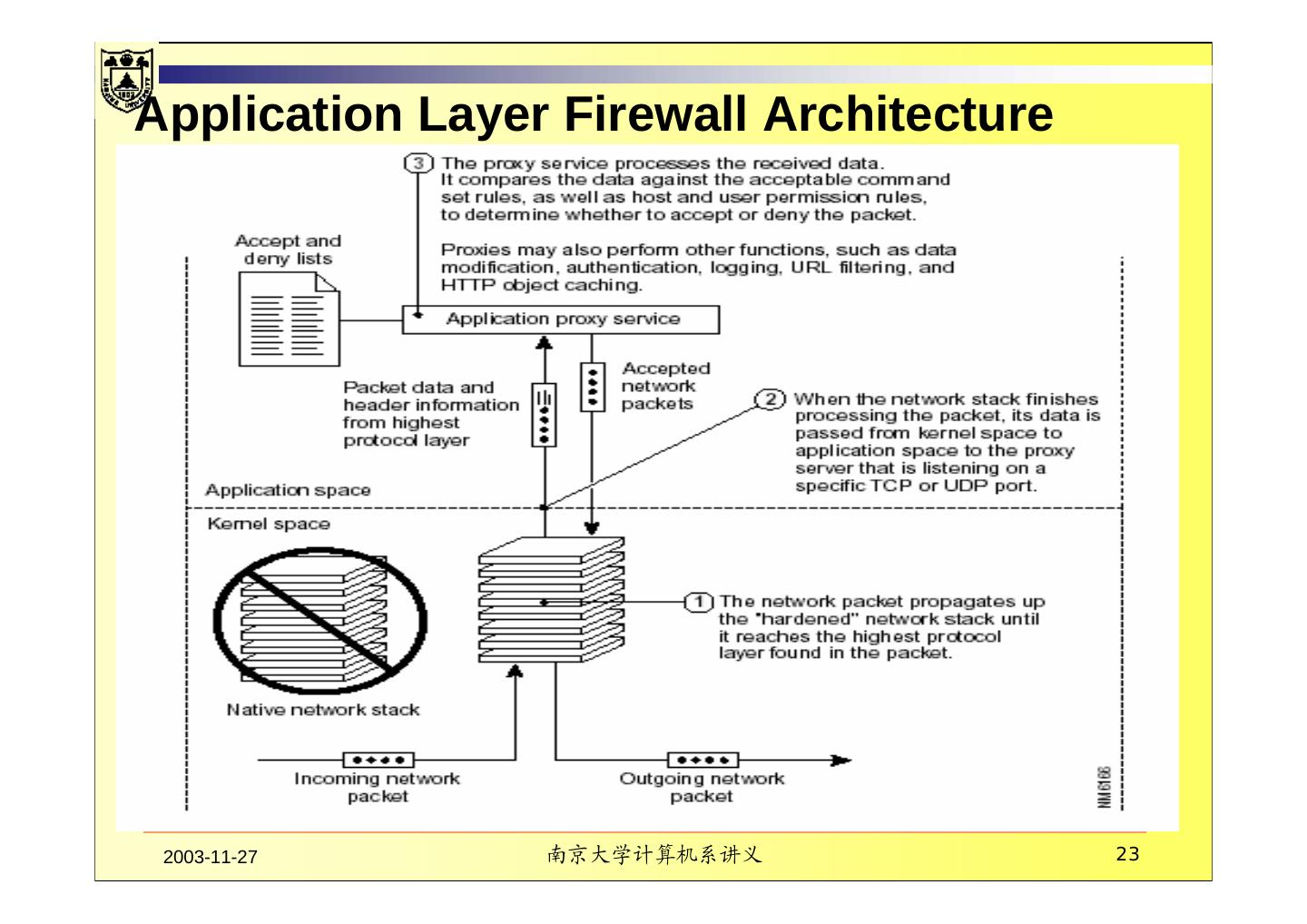
23 .Application Layer Firewall Architecture 2003-11-27 南京大学计算机系讲义 23
24 . How a Proxy Service Works 2003-11-27 南京大学计算机系讲义 24
25 . How a Proxy Service Works Proxy services are specific to the protocol Forward provide increased access control careful detailed checks for valid data generate audit records about the traffic 2003-11-27 南京大学计算机系讲义 25
26 . How a Proxy Service Works Each application proxy requires two components that are typically implemented as a single executable: a proxy server and a proxy client. A proxy server acts as the end server for all connection requests originated on a trusted network by a real client. Proxy servers understand the protocol of the service. they only allow those packets through that comply with the protocol definitions. They also enable additional benefits, such as detailed audit records of session information, user authentication, and caching. A proxy client is part of a user application that talks to the real server on the external network on behalf of the real client. 2003-11-27 南京大学计算机系讲义 26
27 . Advantages of proxy services Proxy services understand and enforce high-level protocols, such as HTTP and FTP. Proxy services are also capable of processing and manipulating packet data. Proxy services do not allow direct communications between external servers and internal computers Proxy services are good at generating audit records, allowing administrators to monitor attempts to violate the firewall’s security policies. 2003-11-27 南京大学计算机系讲义 27
28 . Disadvantages of Proxy services Proxy services require you to replace the native network stack on the firewall server. a new proxy must be written for each protocol that you want to pass through the firewall. 2003-11-27 南京大学计算机系讲义 28
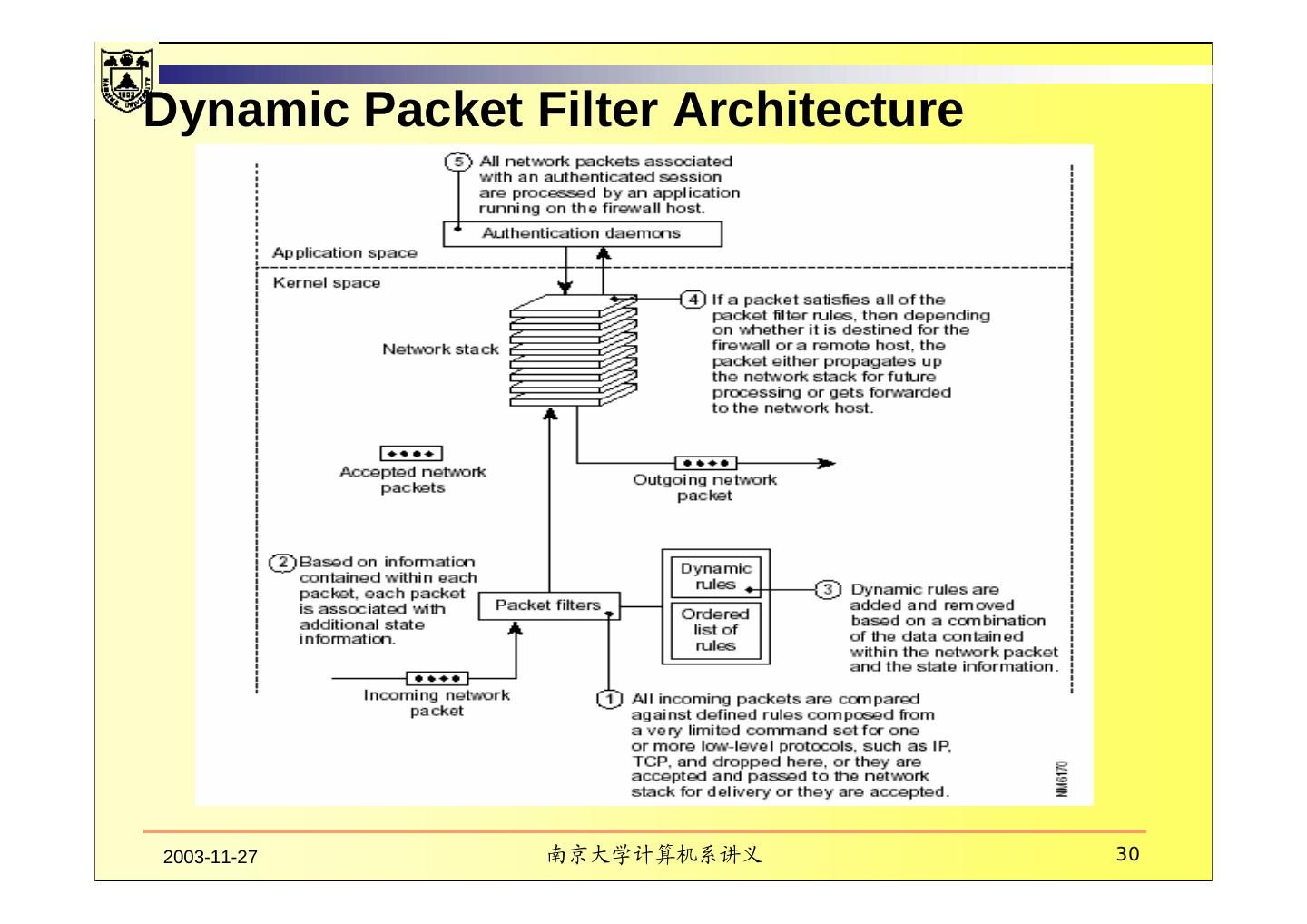
29 . 2.4 Dynamic Packet Filter 2003-11-27 南京大学计算机系讲义 29