- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
The Application Layer
展开查看详情
1 .Chapter 8 Application Layer based on: Computer Networking: A Top Down Approach , 5 th edition. Jim Kurose, Keith Ross Addison-Wesley, April 2009. A note on the use of these ppt slides: We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our slides, and note our copyright of this material. Thanks and enjoy! JFK/KWR All material copyright 1996-2010 J.F Kurose and K.W. Ross, All Rights Reserved Application 2- 1
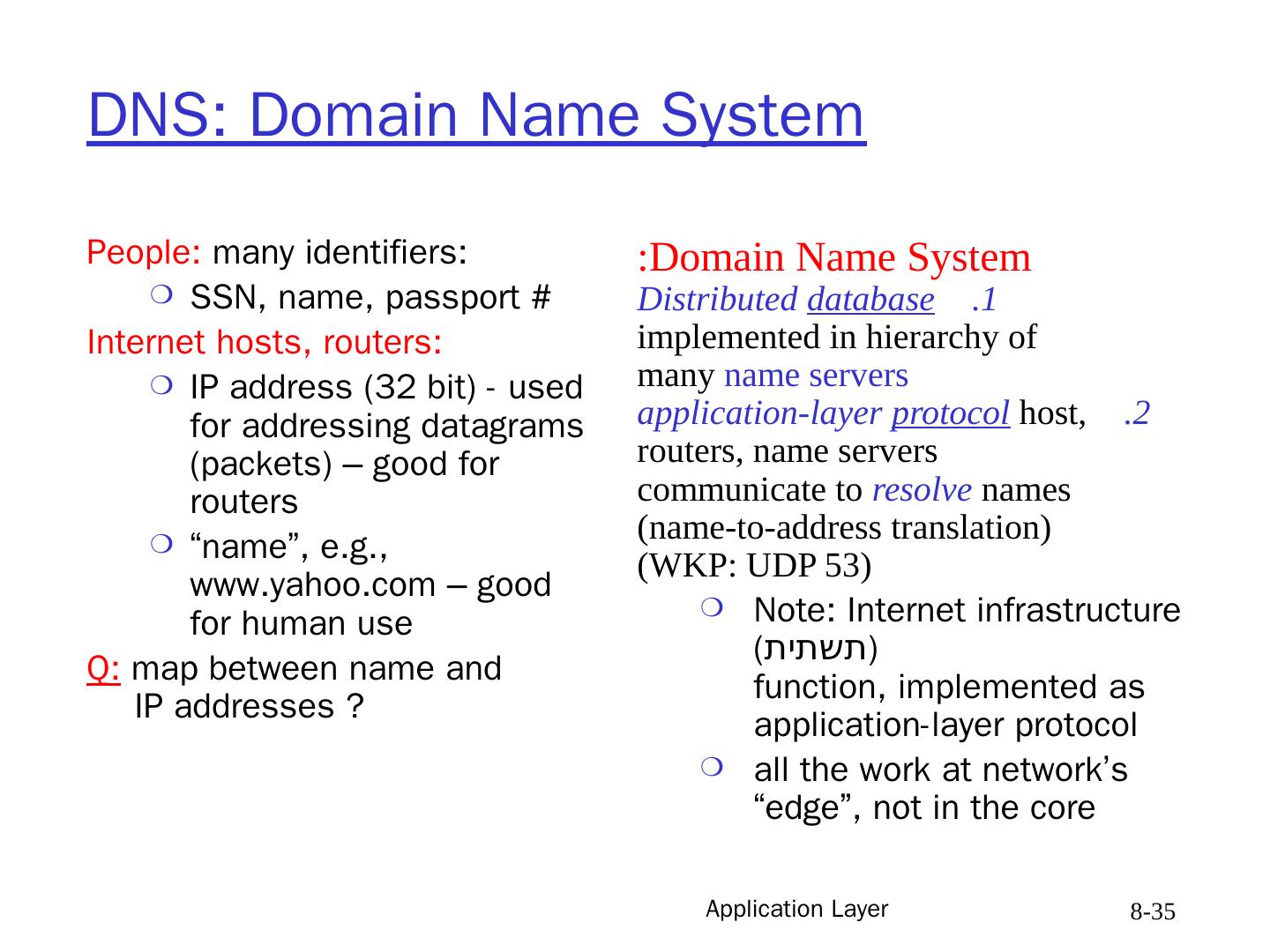
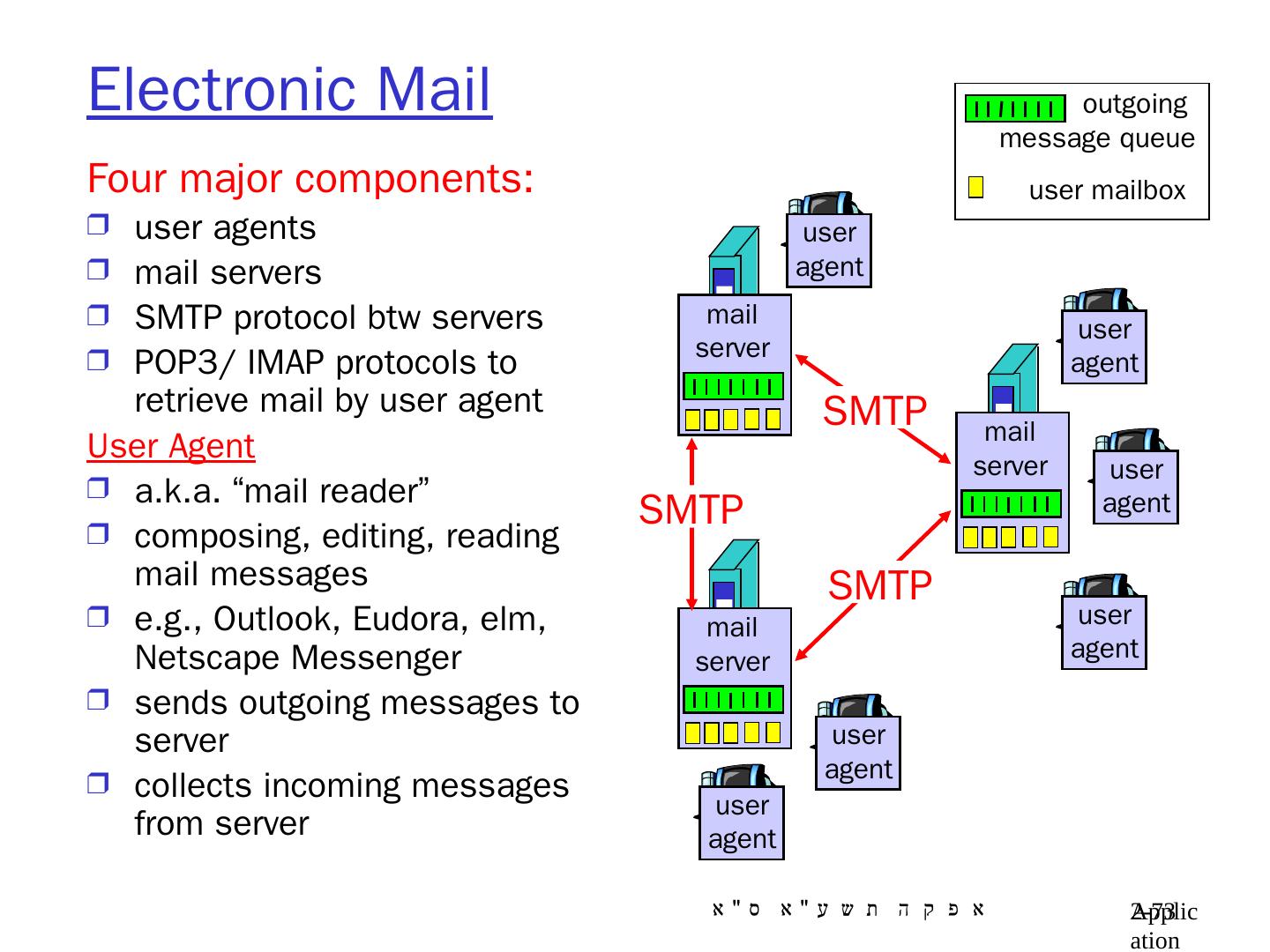
2 .Application Layer 8- 2 Chapter 8: Application Layer Our goals: conceptual / implementation aspects of network application protocols transport-layer service models client-server paradigm peer-to-peer paradigm learn about application-layer protocols by looking at examples: HTTP (web) DNS (web addressing) interface to transport layer
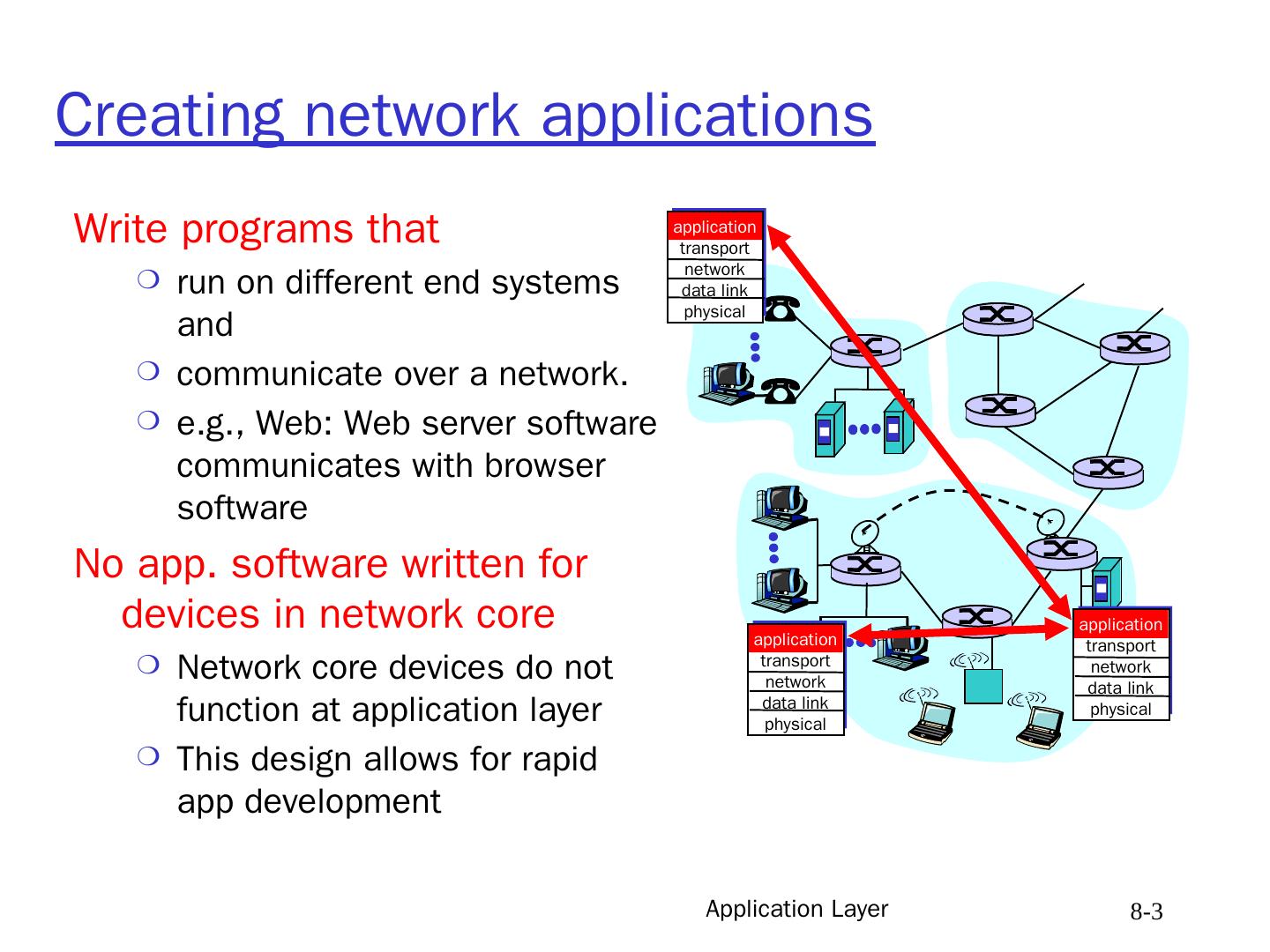
3 .Application Layer 8- 3 Creating network applications Write programs that run on different end systems and communicate over a network. e.g., Web: Web server software communicates with browser software No app. software written for devices in network core Network core devices do not function at application layer This design allows for rapid app development application transport network data link physical application transport network data link physical application transport network data link physical
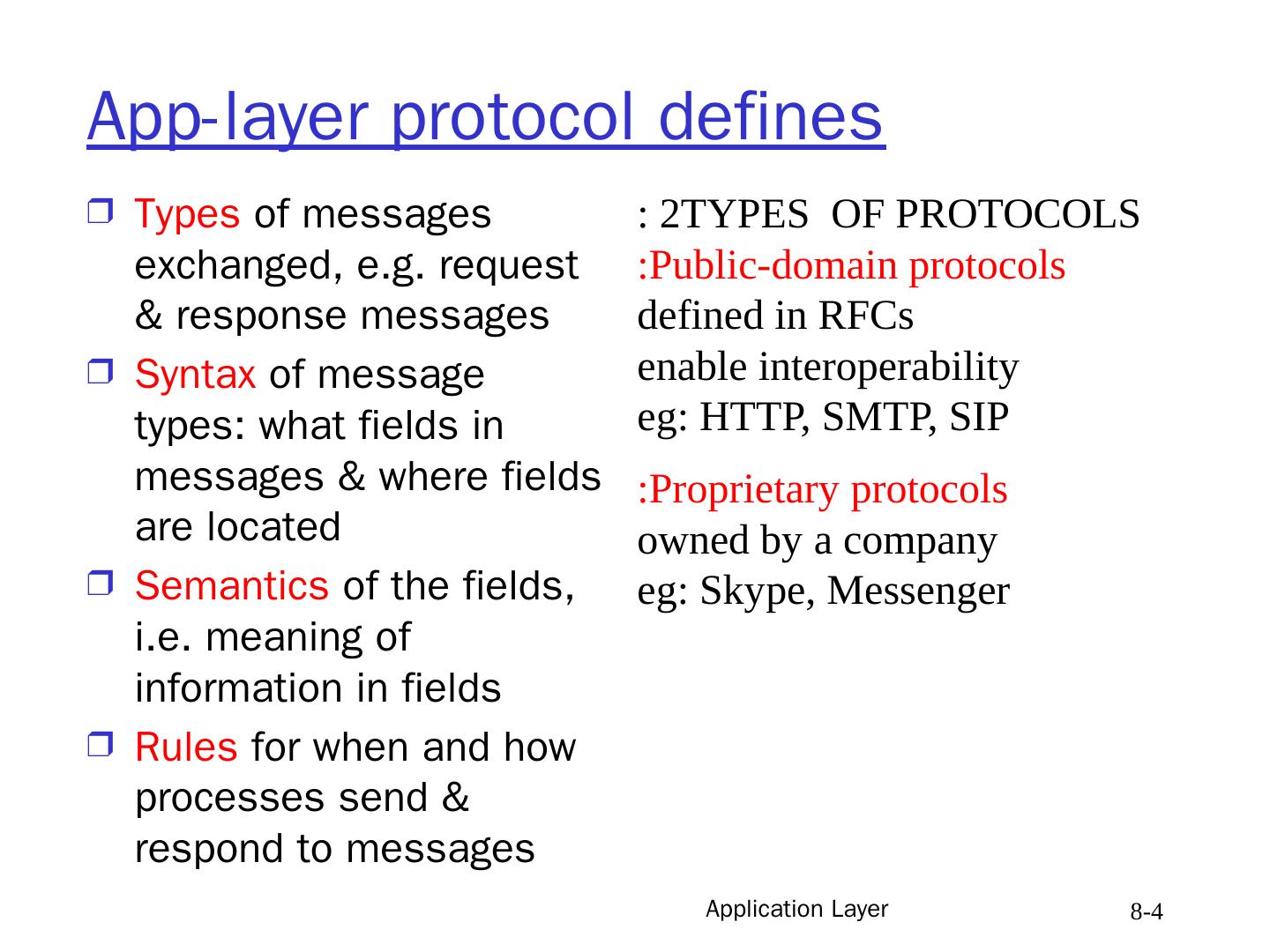
4 .Application Layer 8- 4 App-layer protocol defines Types of messages exchanged, e.g. request & response messages Syntax of message types: what fields in messages & where fields are located Semantics of the fields, i.e. meaning of information in fields Rules for when and how processes send & respond to messages 2TYPES OF PROTOCOLS: Public-domain protocols: defined in RFCs enable interoperability eg: HTTP, SMTP, SIP Proprietary protocols: owned by a company eg: Skype, Messenger
5 .Application Layer 8- 5 Client / Server concepts Hardware view Process / interaction view Client-Server architecture Peer-to-Peer architecture
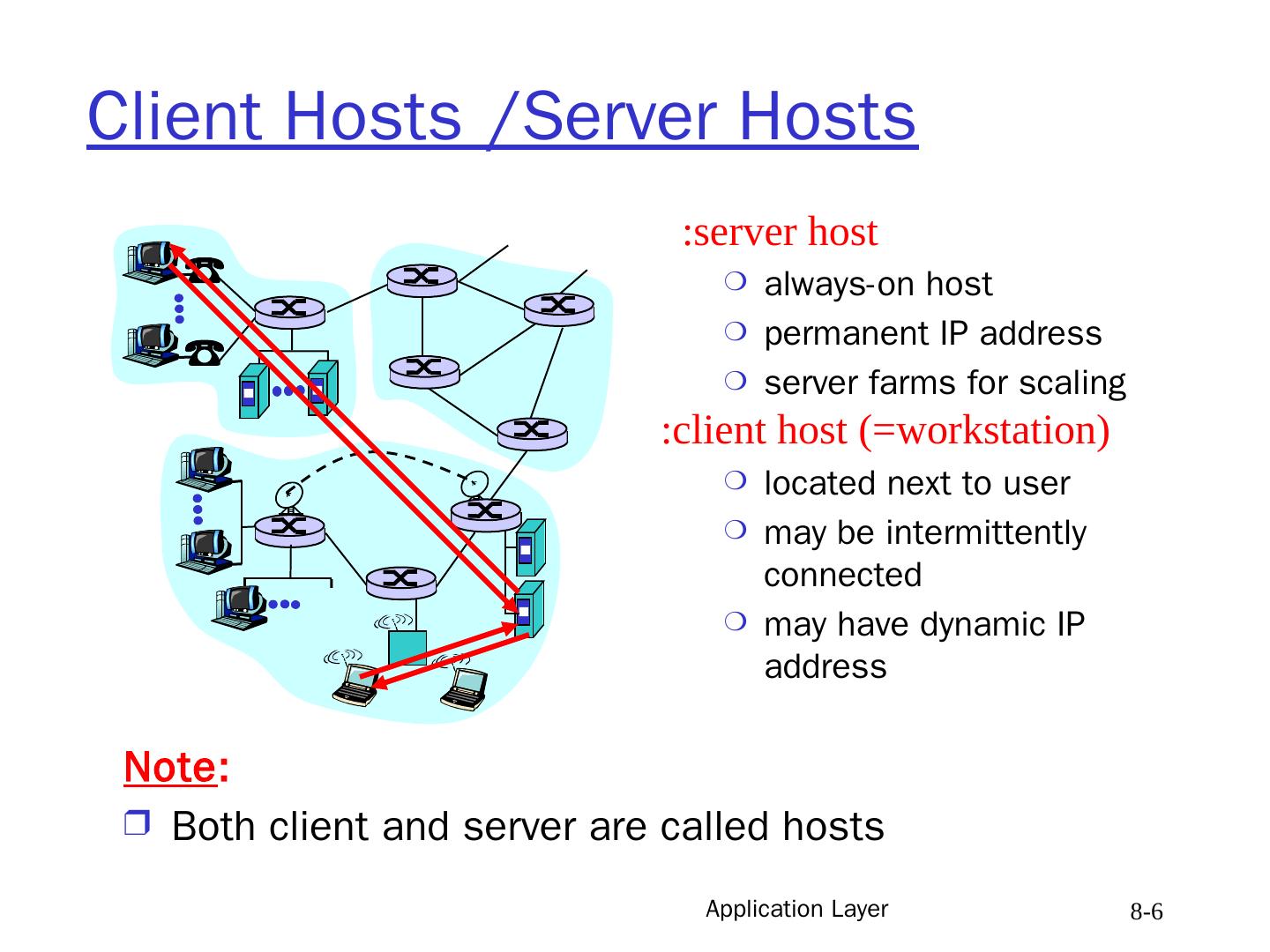
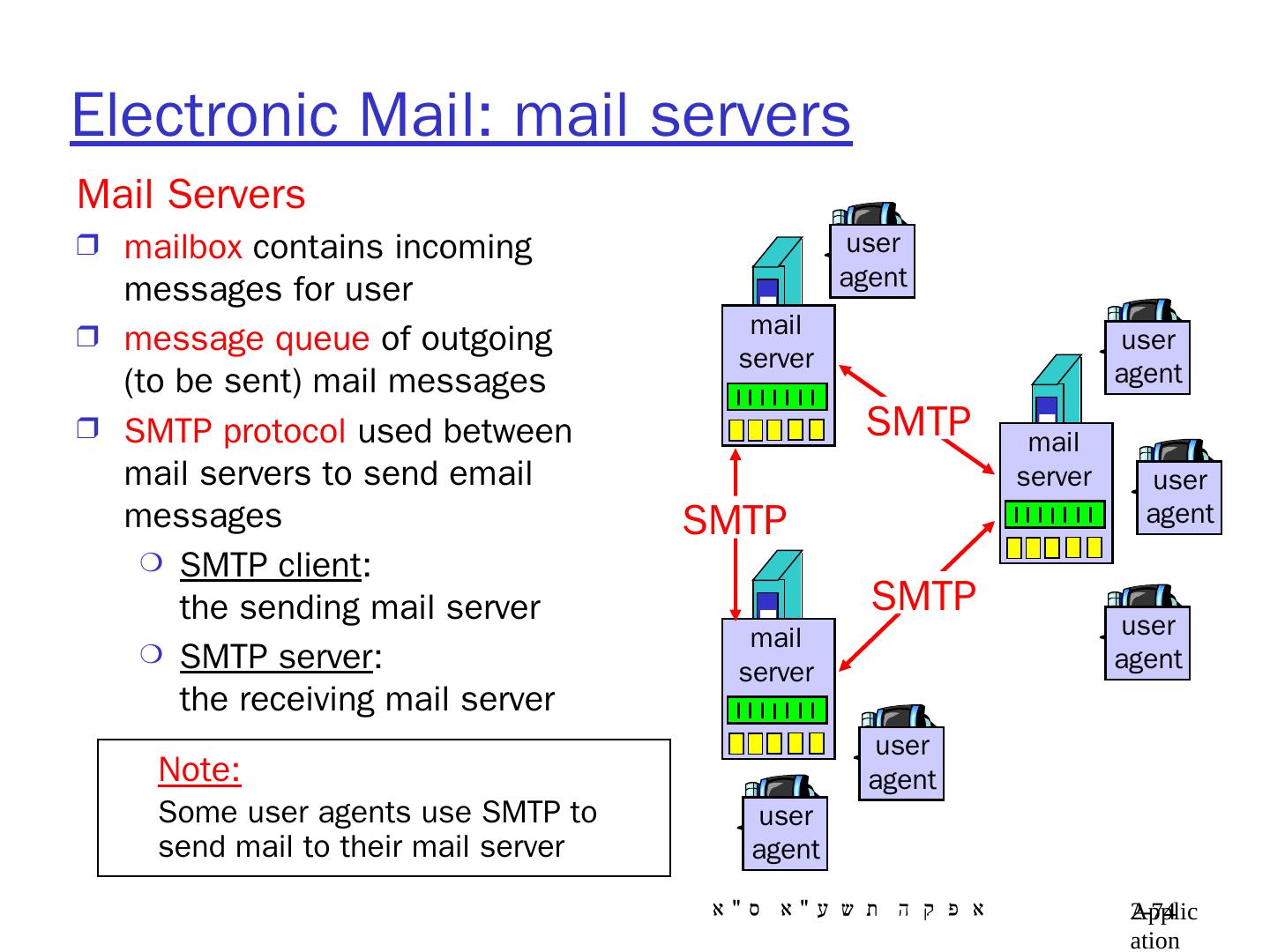
6 .Application Layer 8- 6 Client Hosts /Server Hosts server host : always-on host permanent IP address server farms for scaling client host (=workstation): located next to user may be intermittently connected may have dynamic IP address Note : Both client and server are called hosts
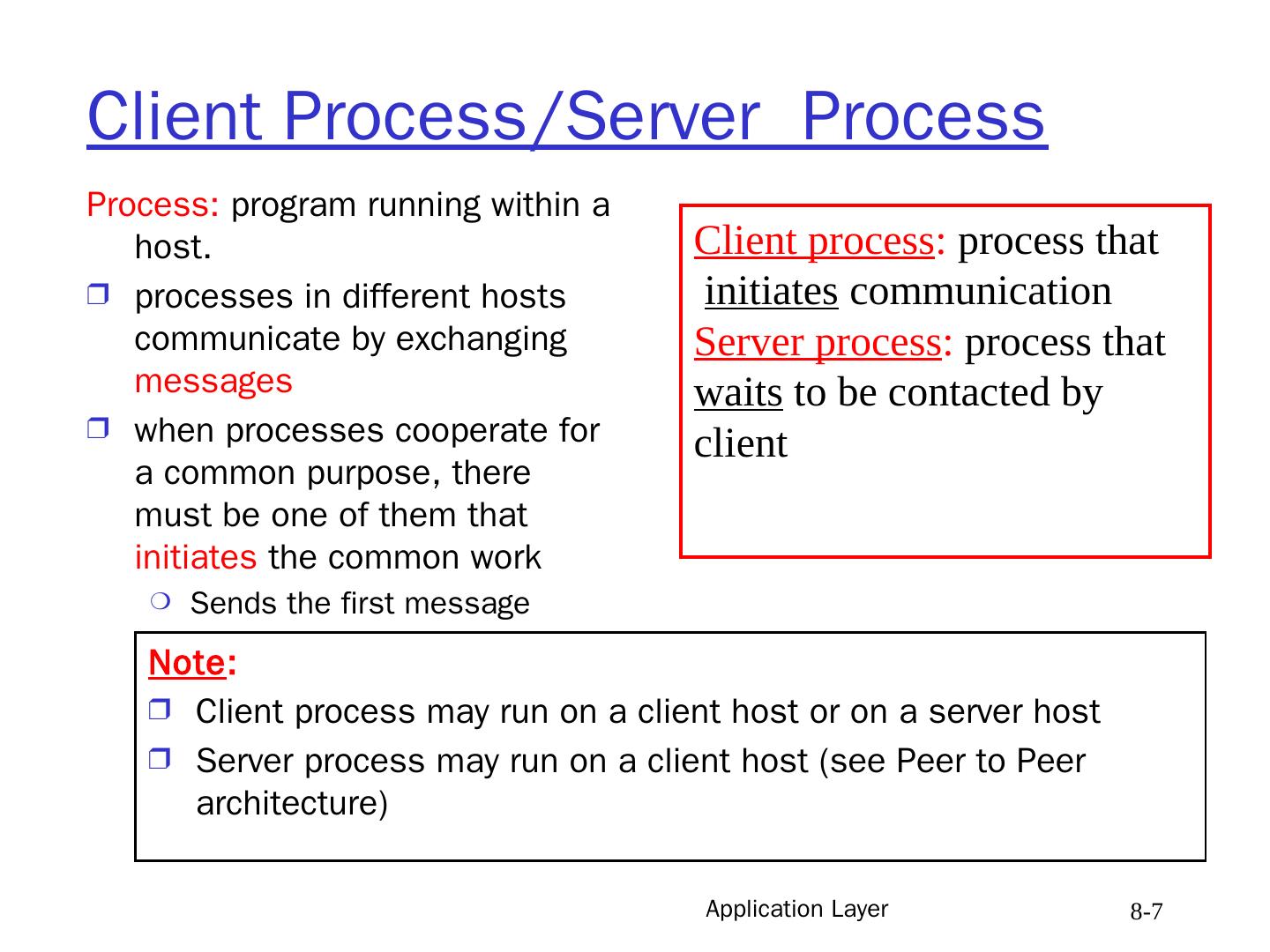
7 .Application Layer 8- 7 Process: program running within a host. processes in different hosts communicate by exchanging messages when processes cooperate for a common purpose, there must be one of them that initiates the common work Sends the first message Client process : process that initiates communication Server process : process that waits to be contacted by client Note : Client process may run on a client host or on a server host Server process may run on a client host (see Peer to Peer architecture) Client Process/Server Process
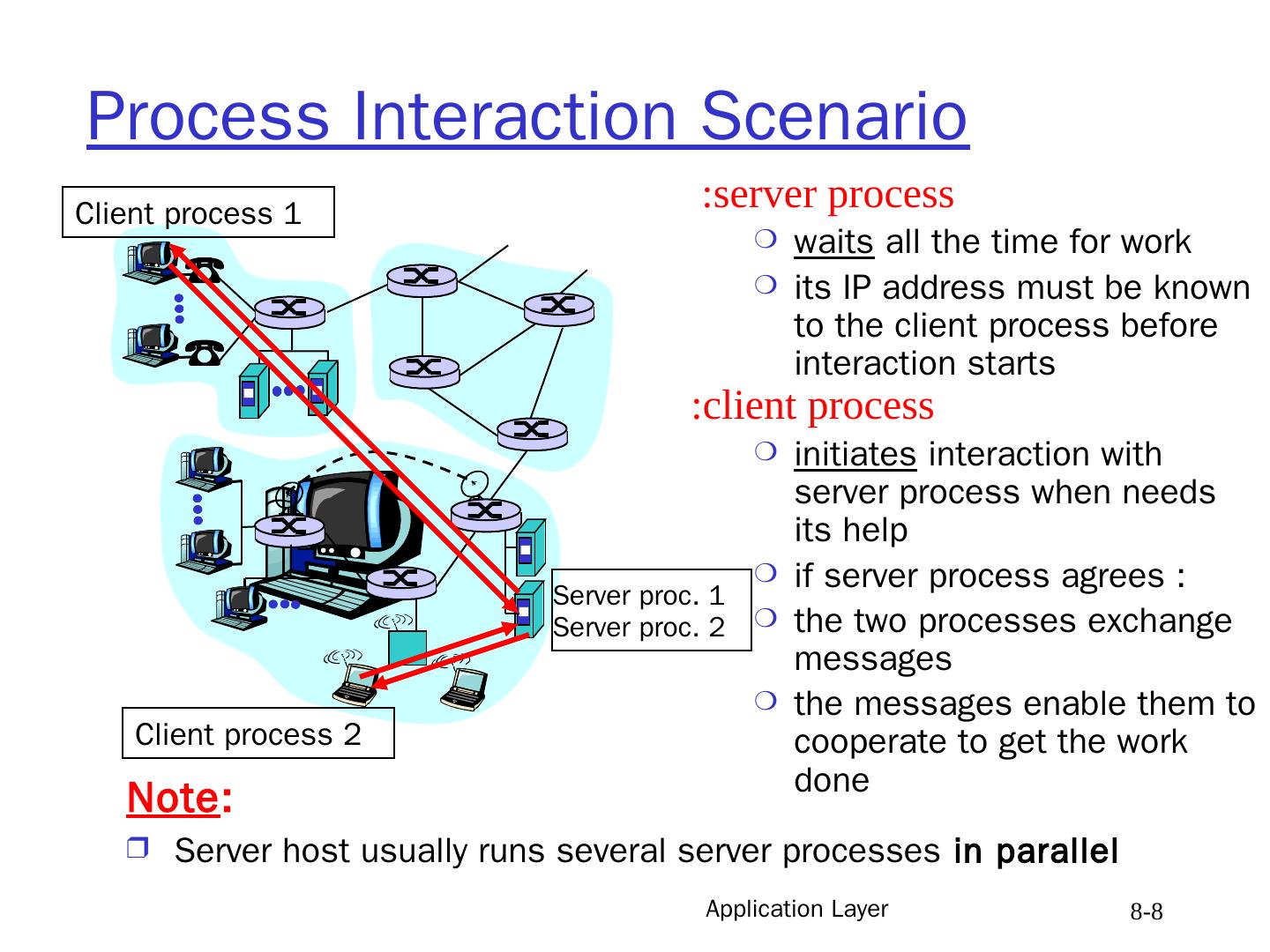
8 .Application Layer 8- 8 Process Interaction Scenario server process : waits all the time for work its IP address must be known to the client process before interaction starts client process: initiates interaction with server process when needs its help if server process agrees : the two processes exchange messages the messages enable them to cooperate to get the work done Note : Server host usually runs several server processes in parallel Client process 1 Client process 2 Server proc. 1 Server proc. 2
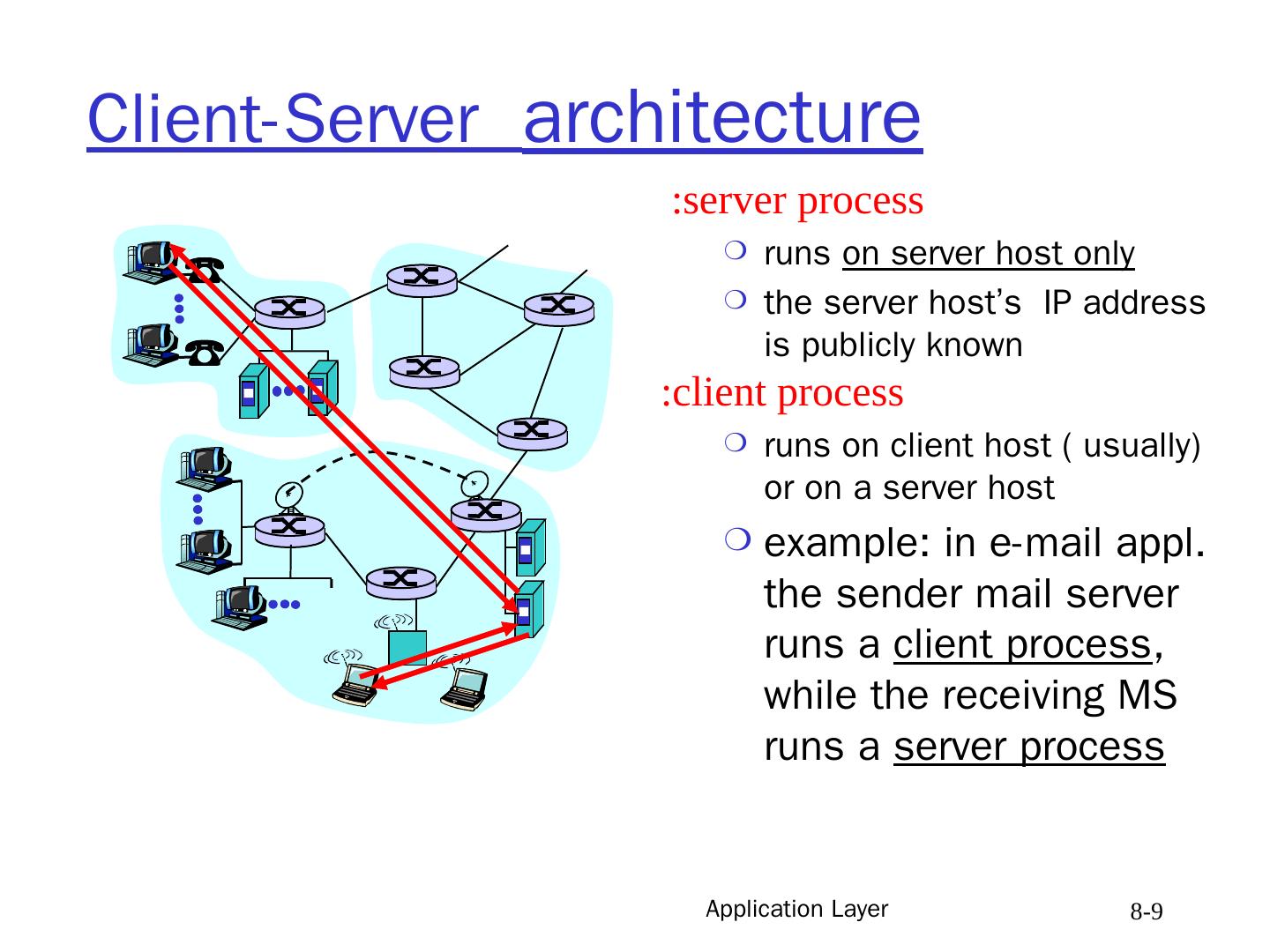
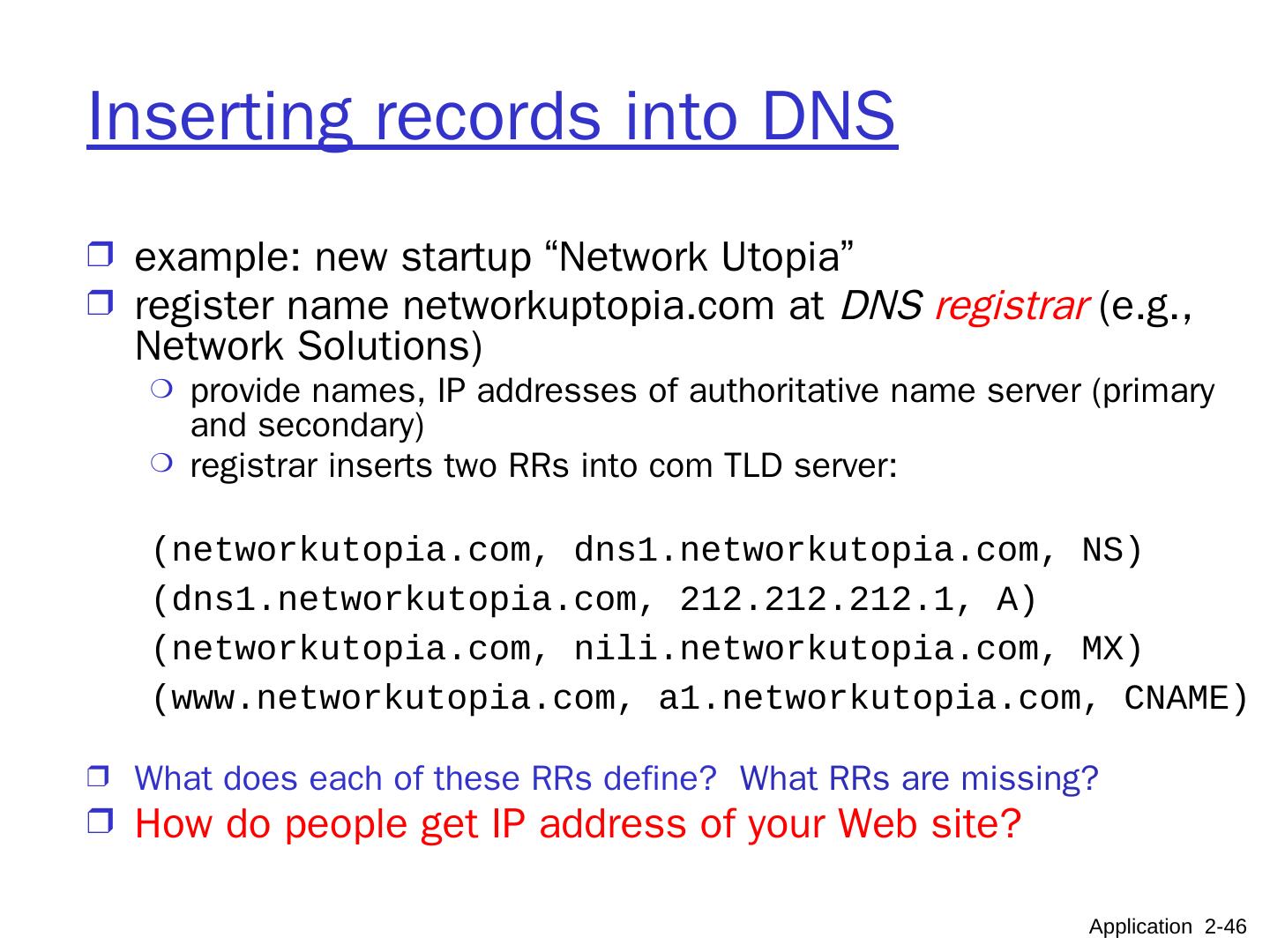
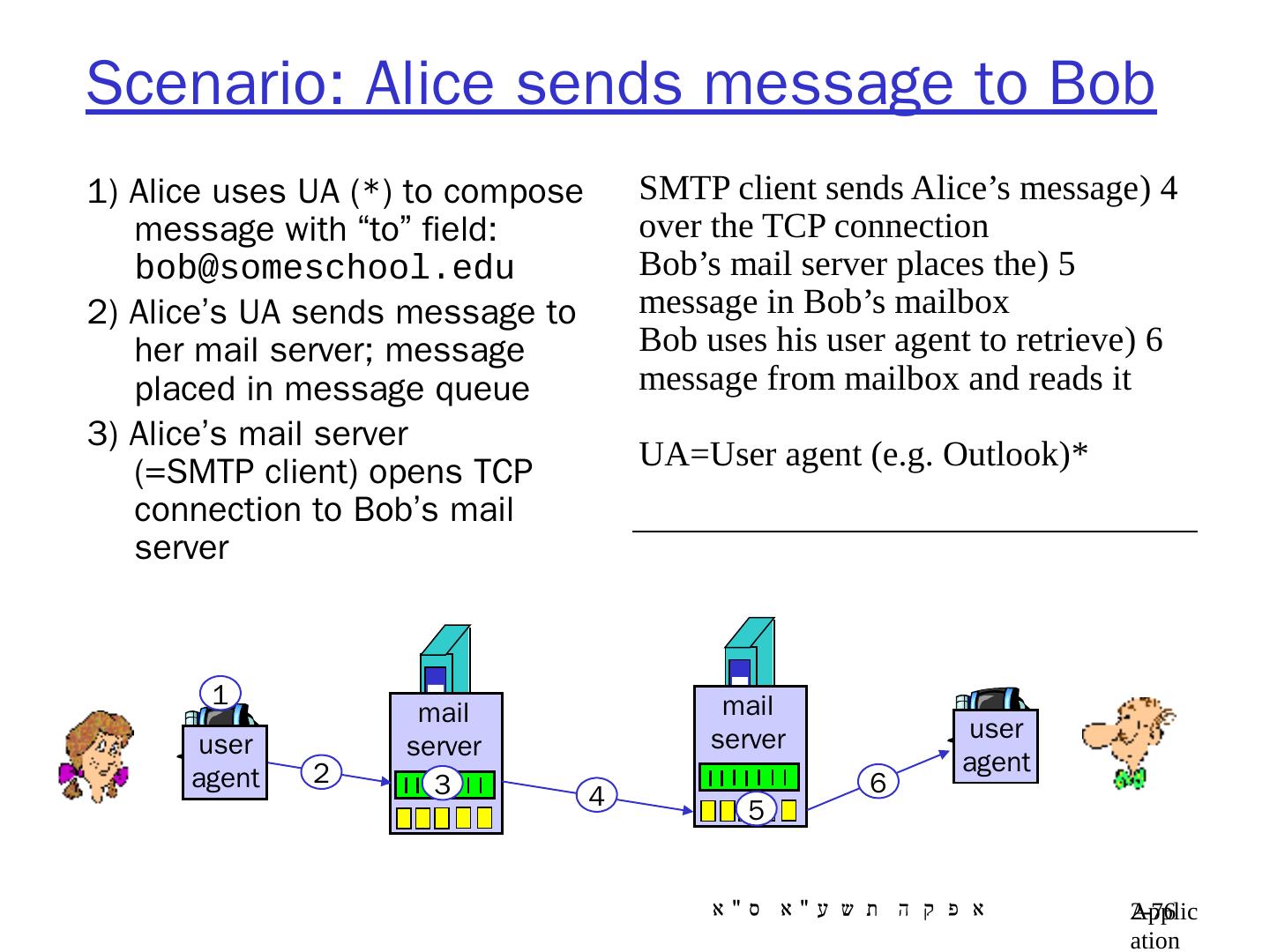
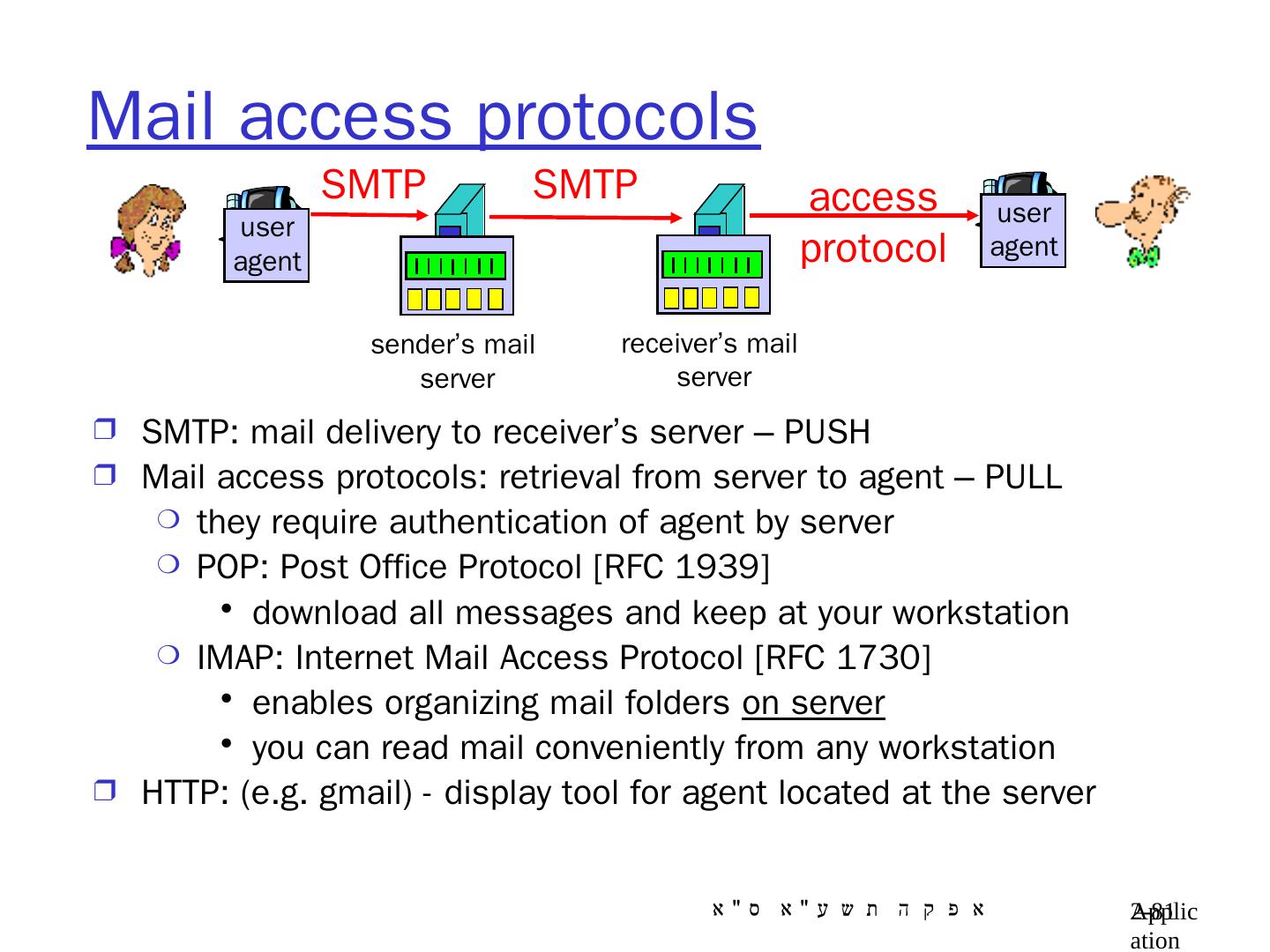
9 .Application Layer 8- 9 Client-Server architecture server process : runs on server host only the server host’s IP address is publicly known client process: runs on client host ( usually) or on a server host example: in e-mail appl. the sender mail server runs a client process , while the receiving MS runs a server process
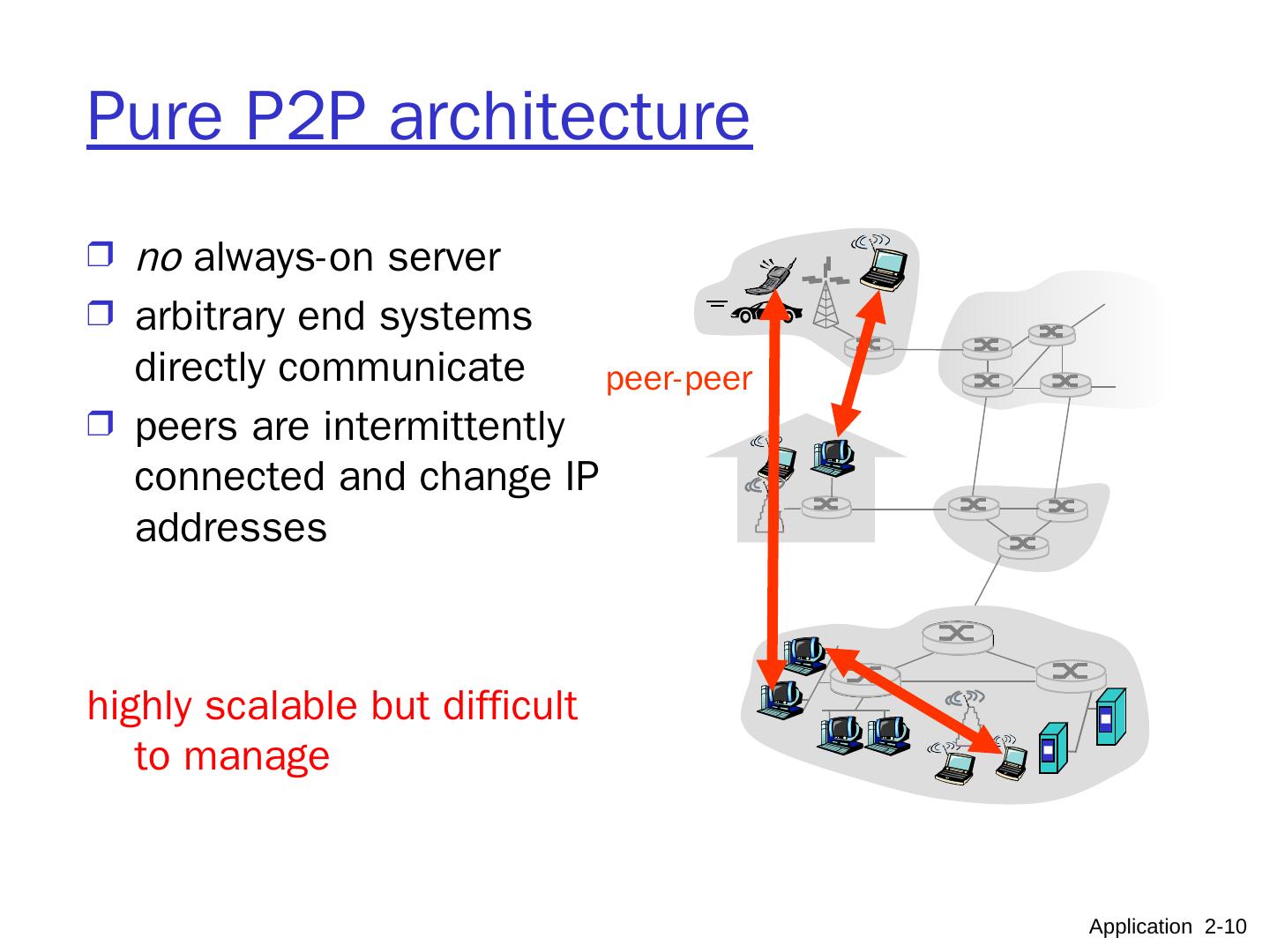
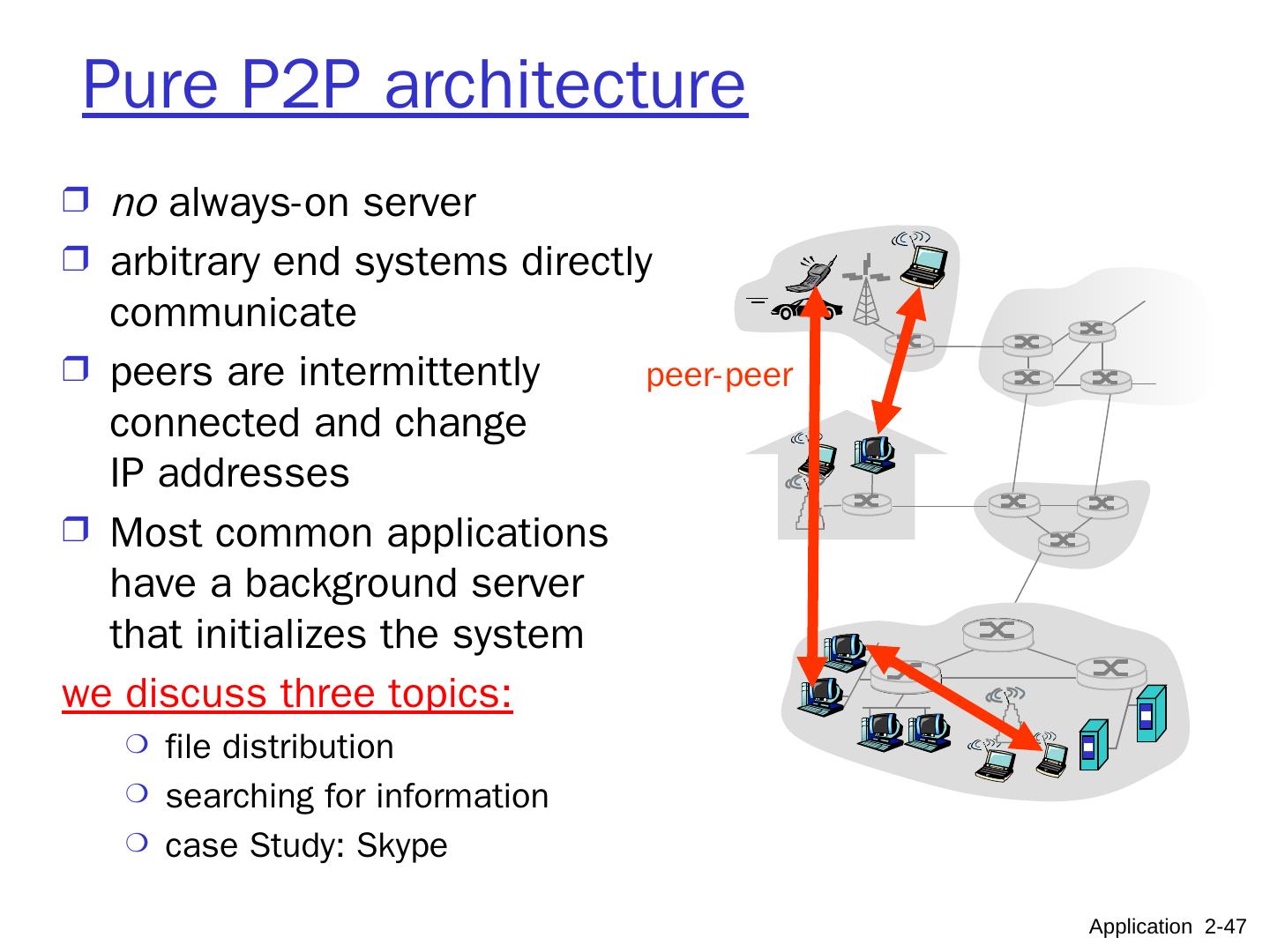
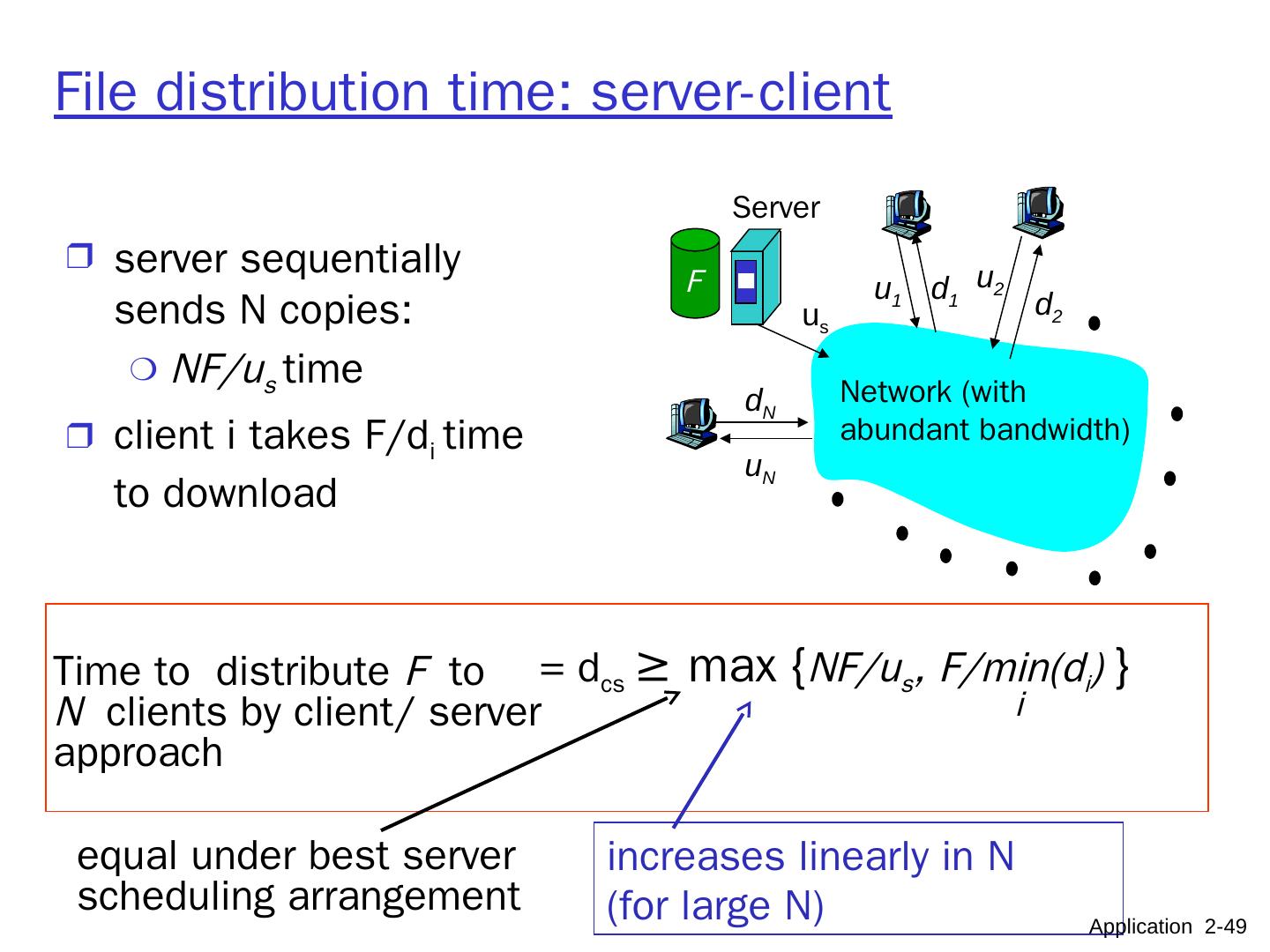
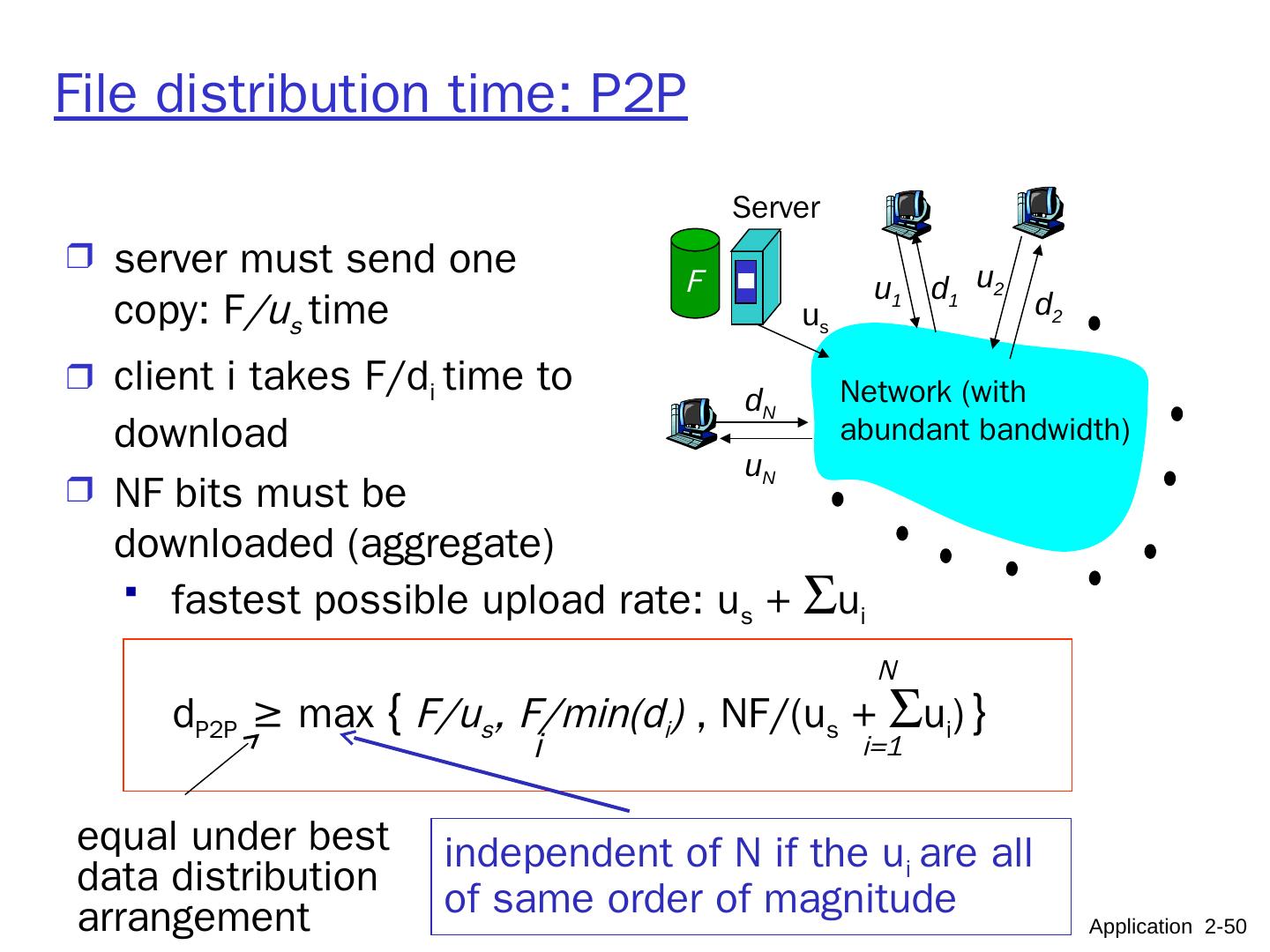
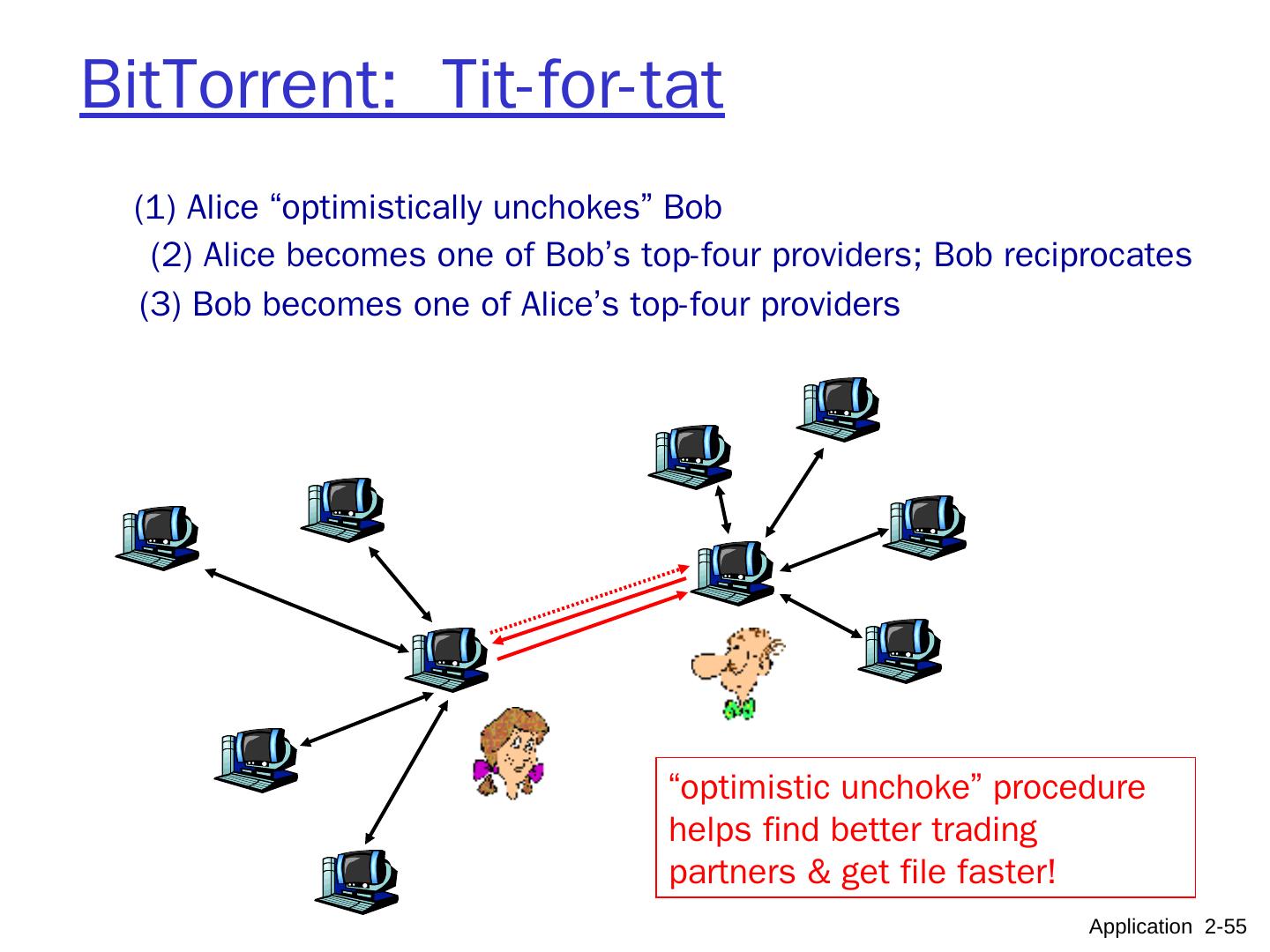
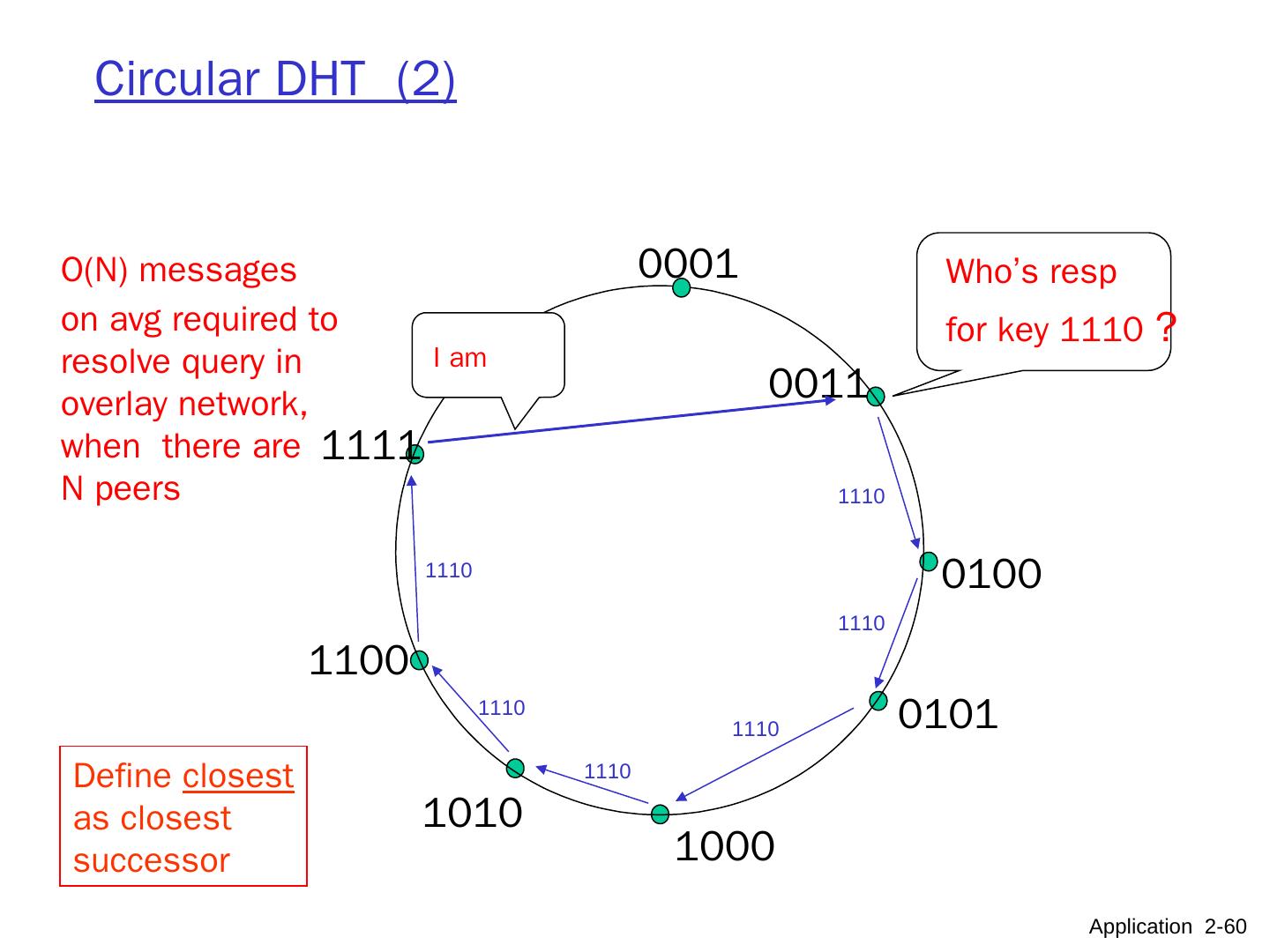
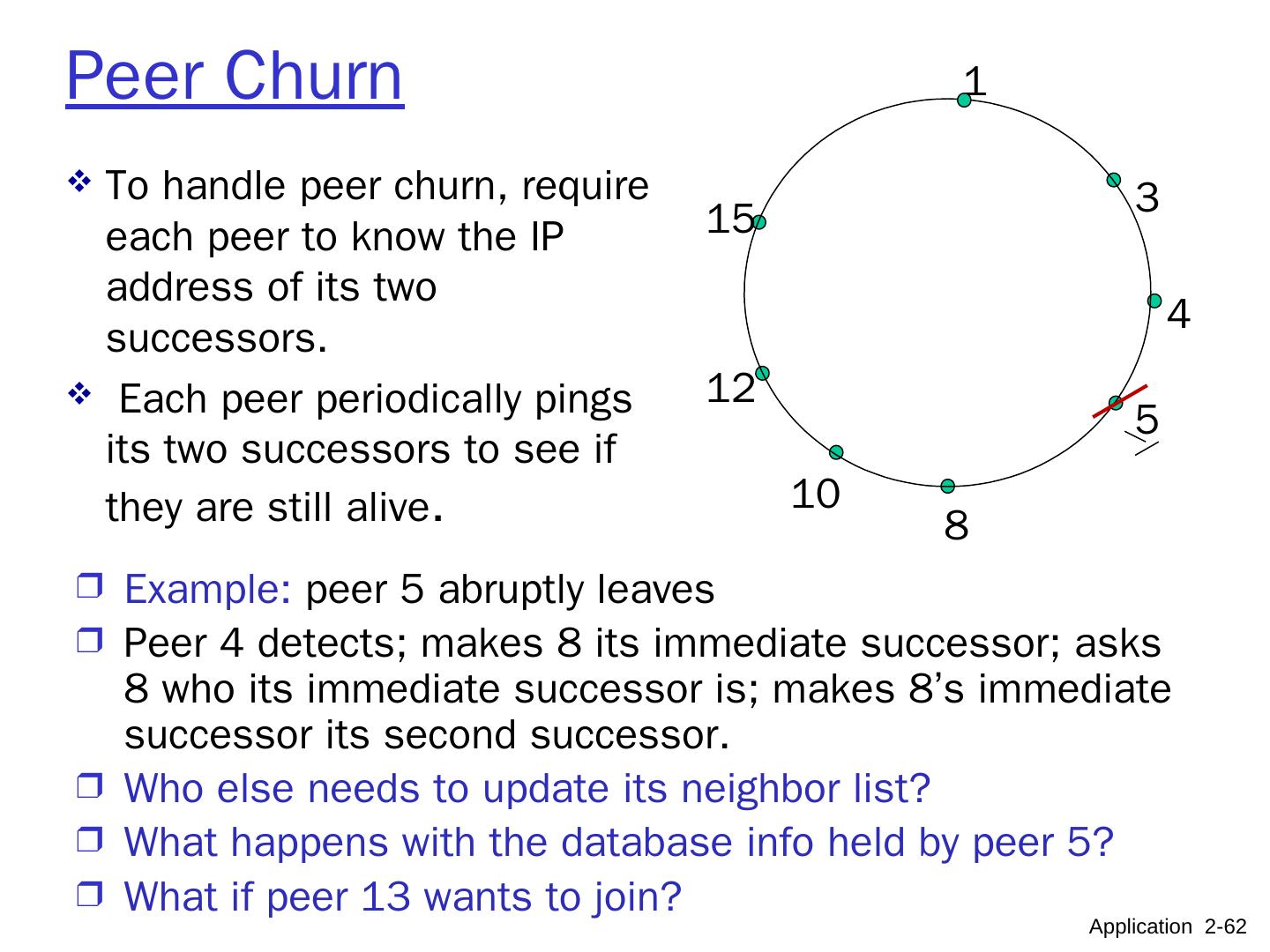
10 .Pure P2P architecture no always-on server arbitrary end systems directly communicate peers are intermittently connected and change IP addresses highly scalable but difficult to manage peer-peer Application 2- 10
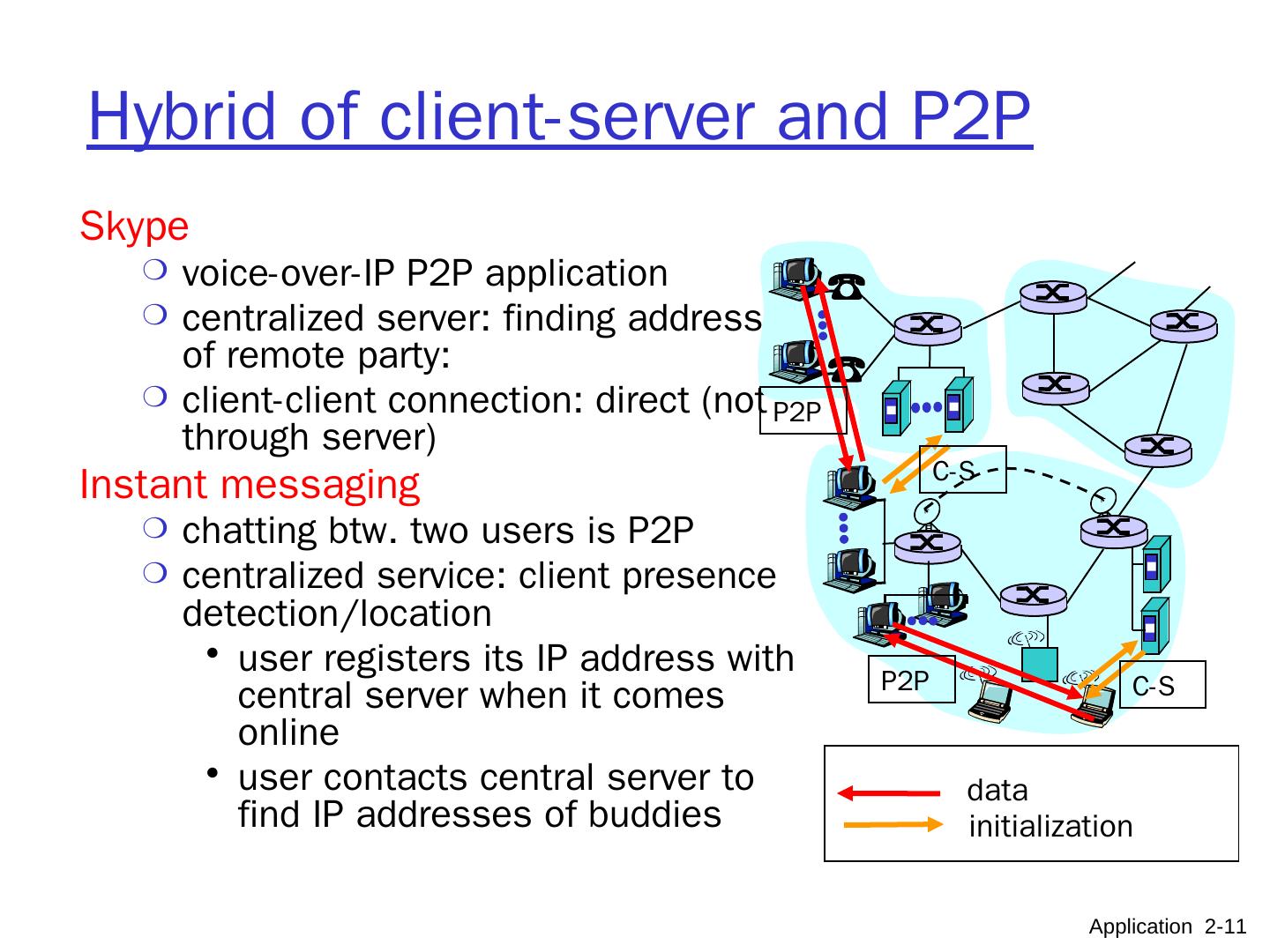
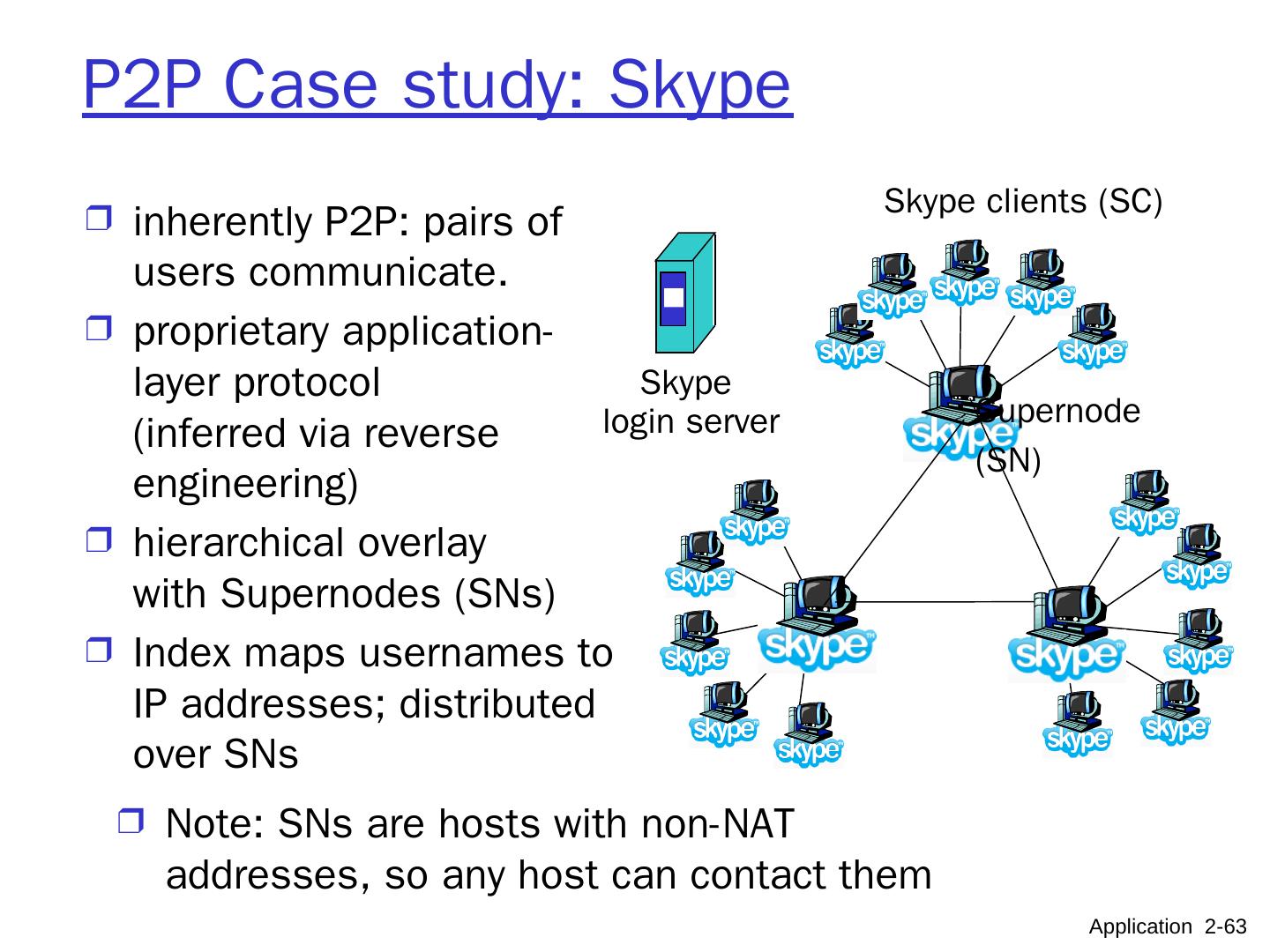
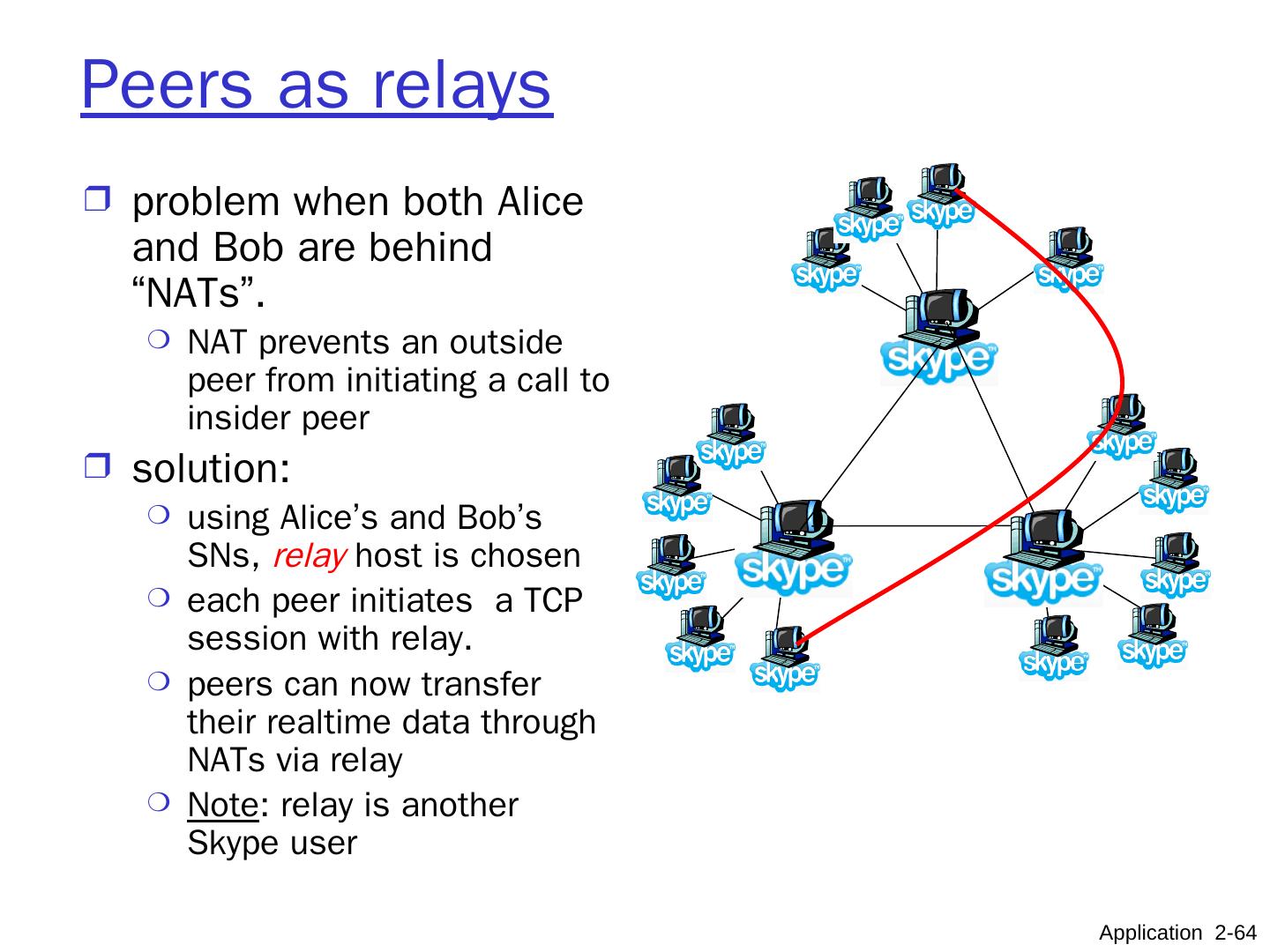
11 .Hybrid of client-server and P2P Skype voice-over-IP P2P application centralized server: finding address of remote party: client-client connection: direct (not through server) Instant messaging chatting btw. two users is P2P centralized service: client presence detection/location user registers its IP address with central server when it comes online user contacts central server to find IP addresses of buddies Application 2- 11 data initialization C-S C-S P2P P2P
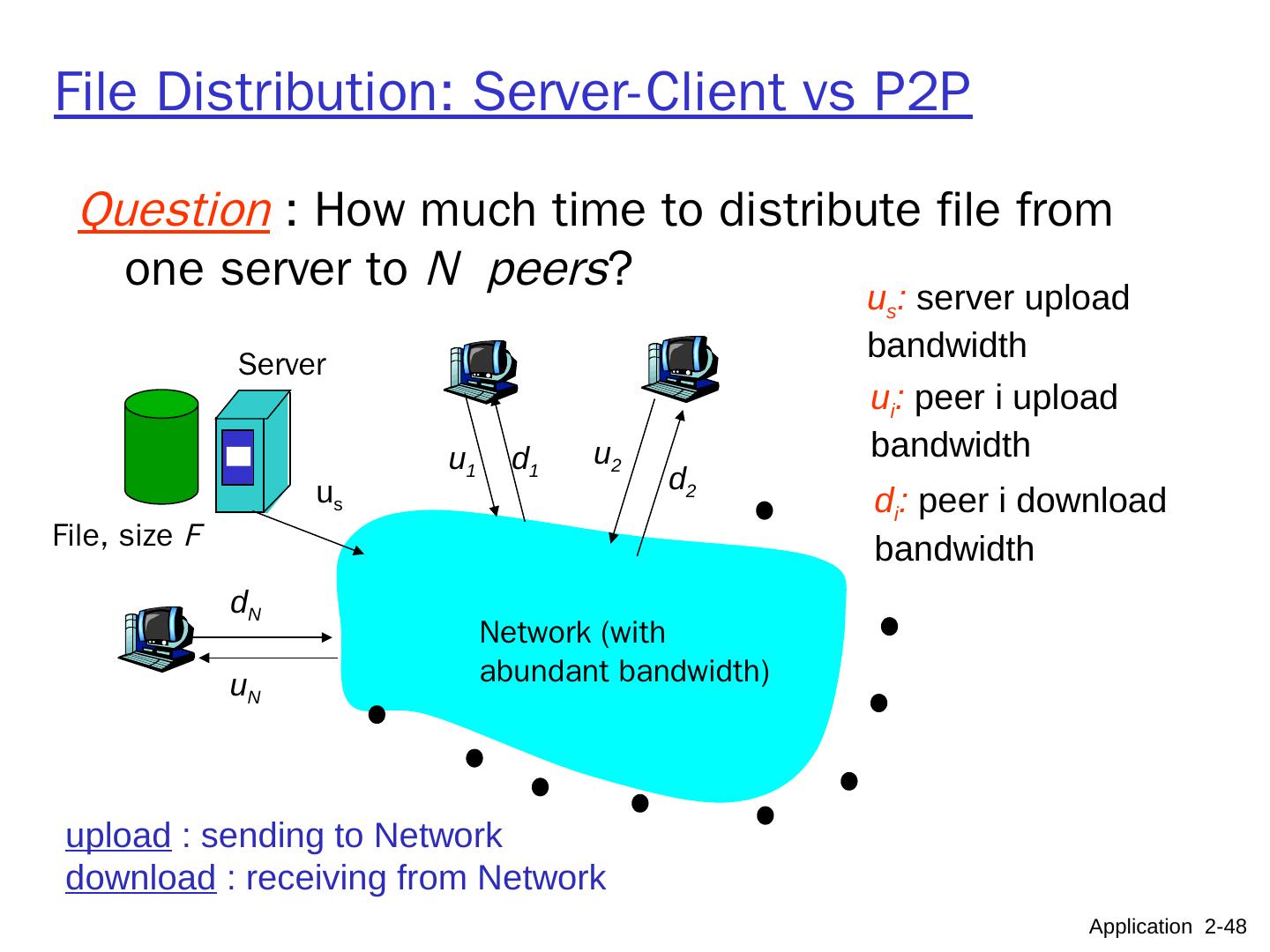
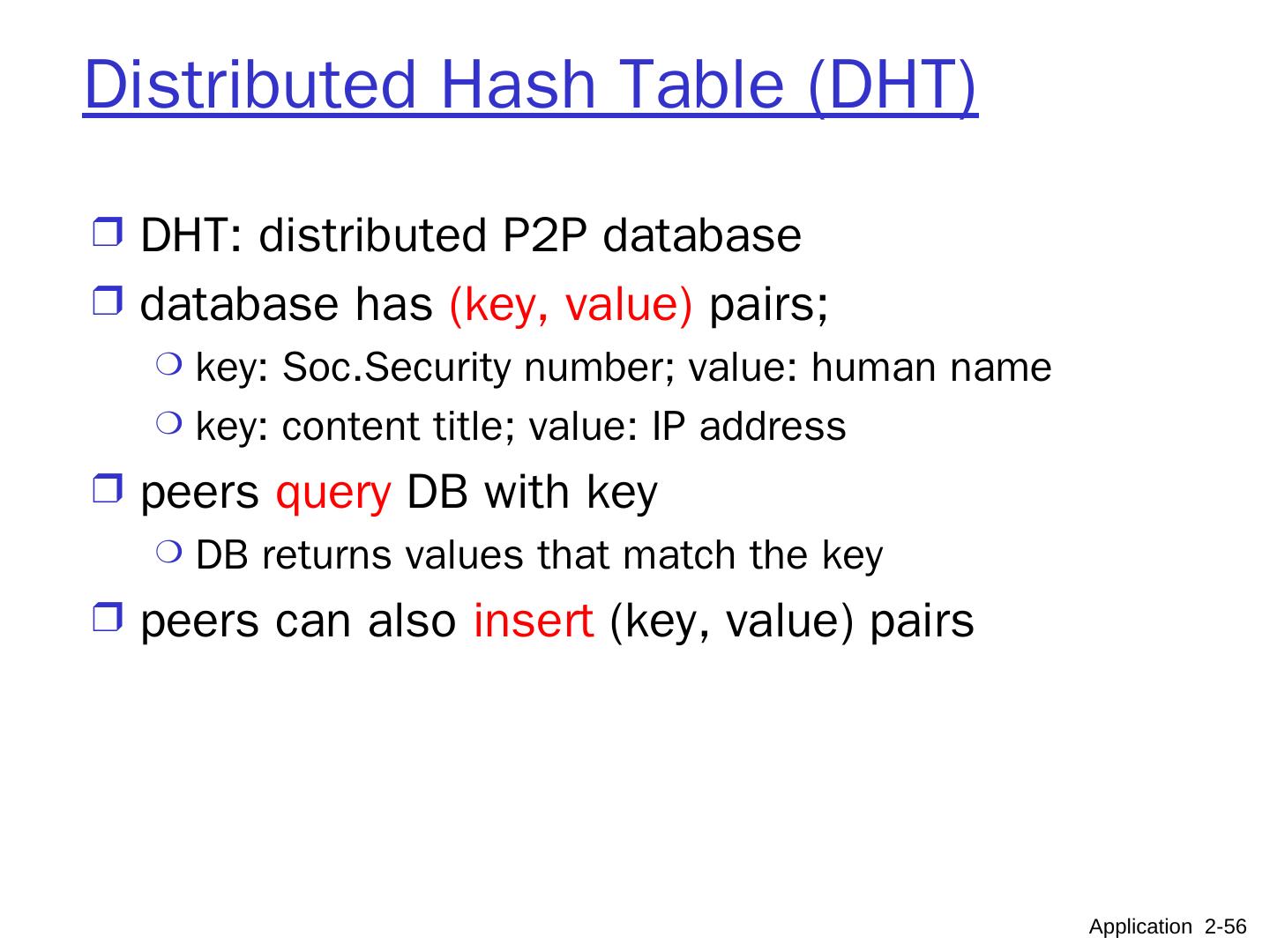
12 .What transport service does an app need? Data loss some apps (e.g., file transfer, telnet) require 100% reliable data transfer other apps (e.g., audio) can tolerate some loss Timing some apps (e.g., Internet telephony, interactive games) require low delay to be “effective” Throughput some apps (e.g., multimedia) require ≥ minimum amount of throughput to be “effective” other apps (“elastic apps”) make use of whatever throughput they get Security encryption, data integrity, … Application 2- 12
13 .Application Layer 8- 13 Transport service requirements of common apps Application file transfer e-mail Web documents real-time audio/video stored audio/video interactive games instant messaging Data loss no loss no loss no loss loss-tolerant loss-tolerant loss-tolerant no loss Bandwidth elastic elastic elastic audio: 5kbps-1Mbps video:10kbps-5Mbps same as above few kbps up elastic Time Sensitive no no no yes, 100’s msec yes, a few secs yes, 100’s msec yes and no
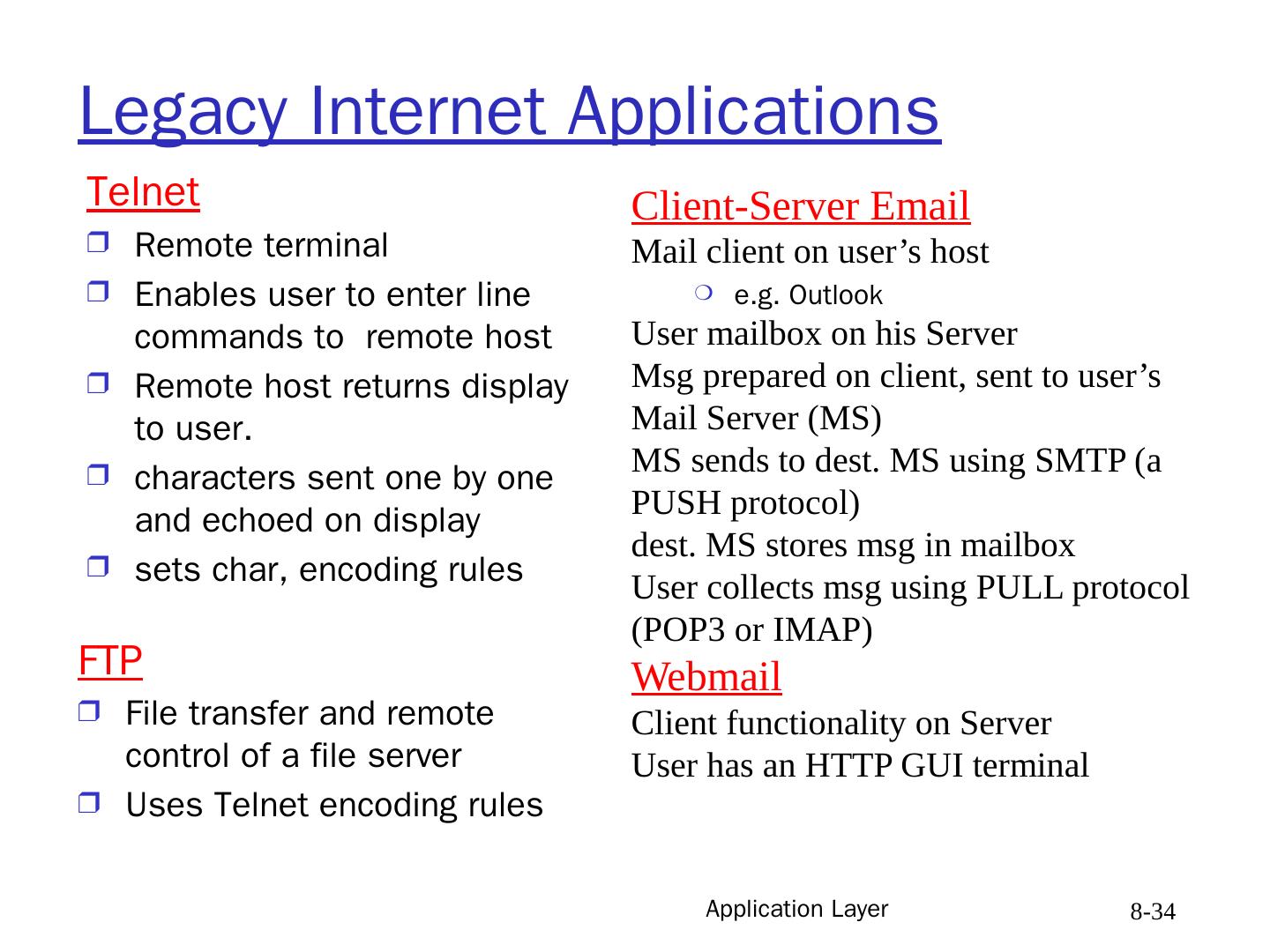
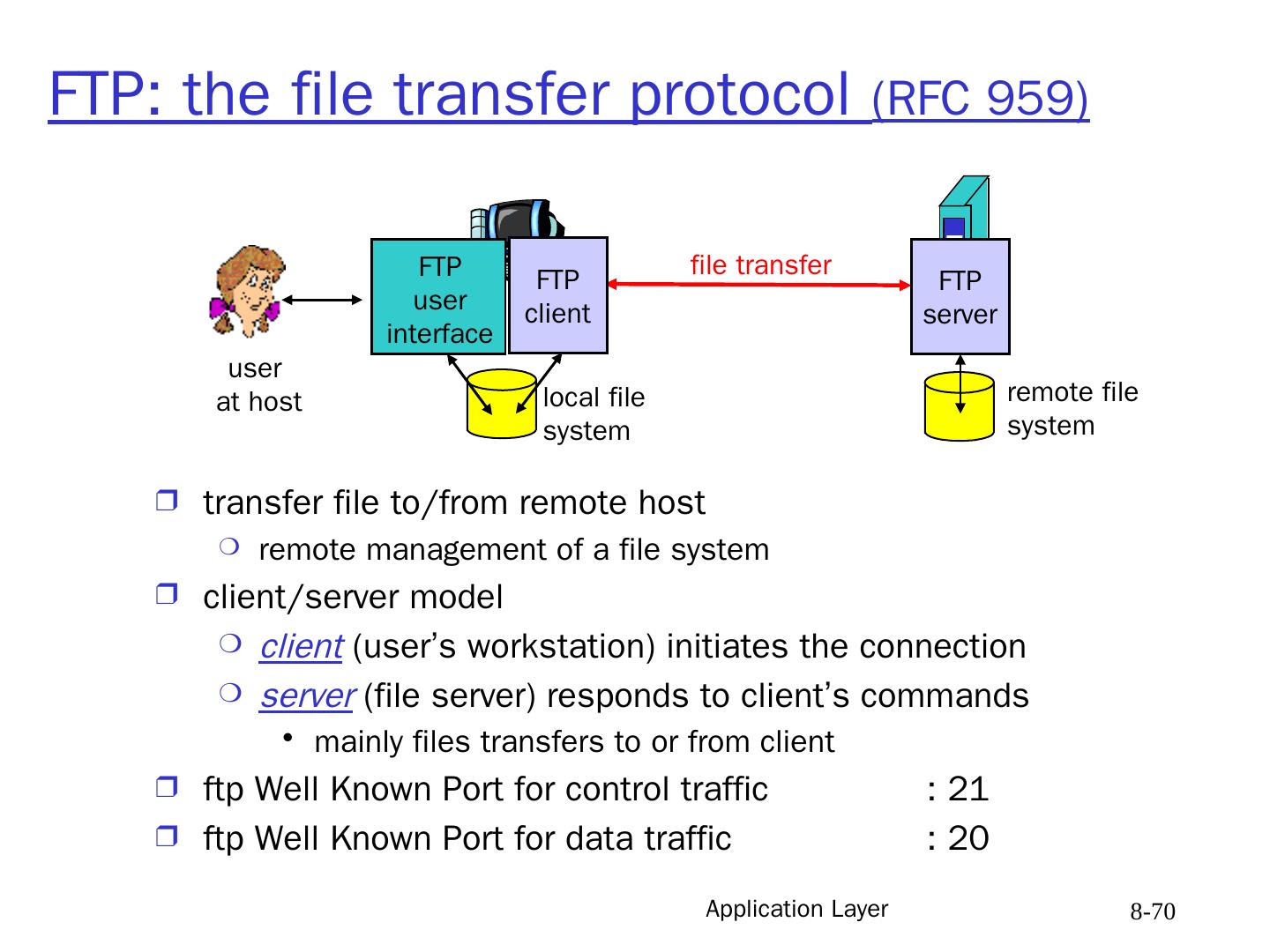
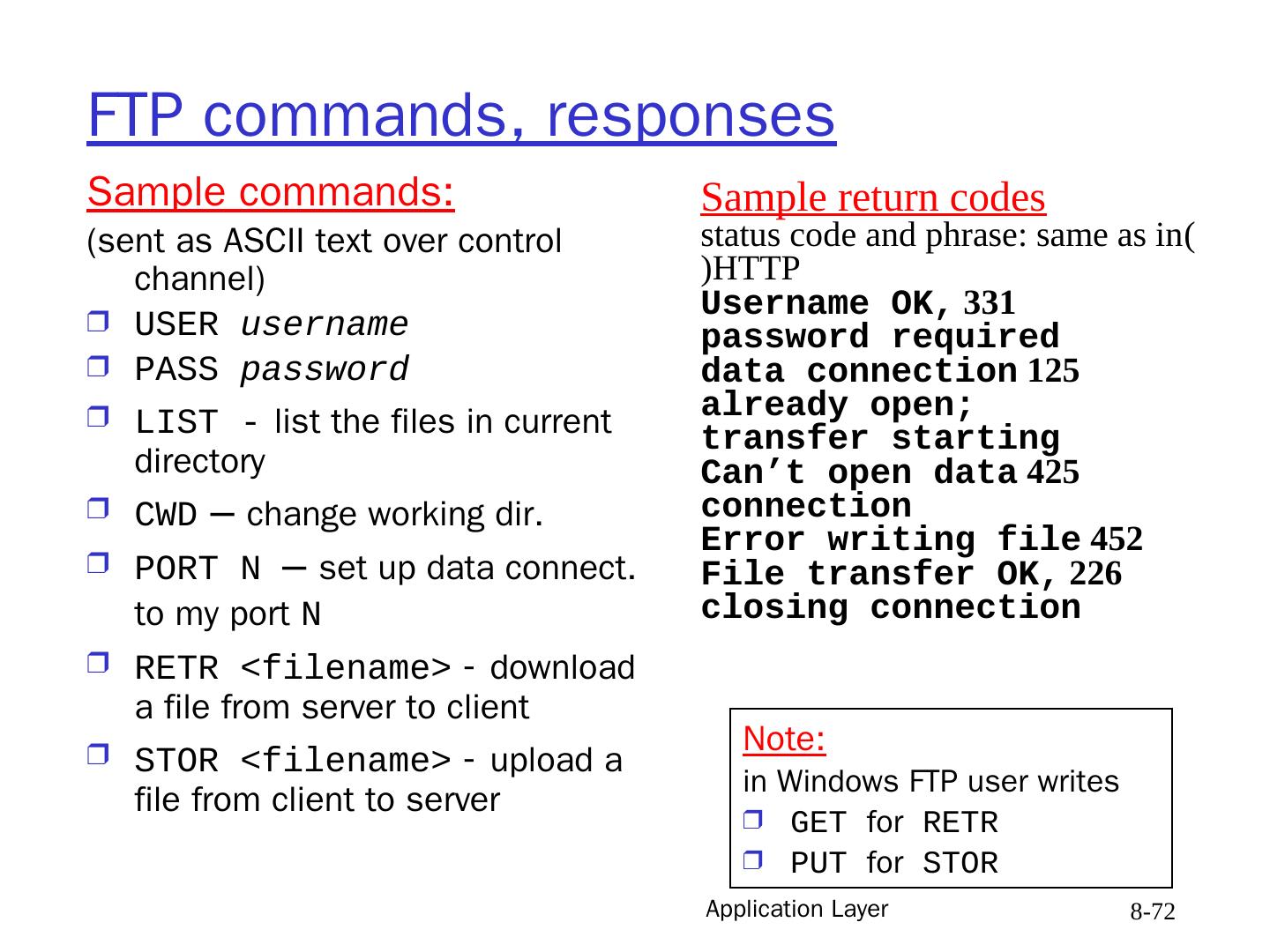
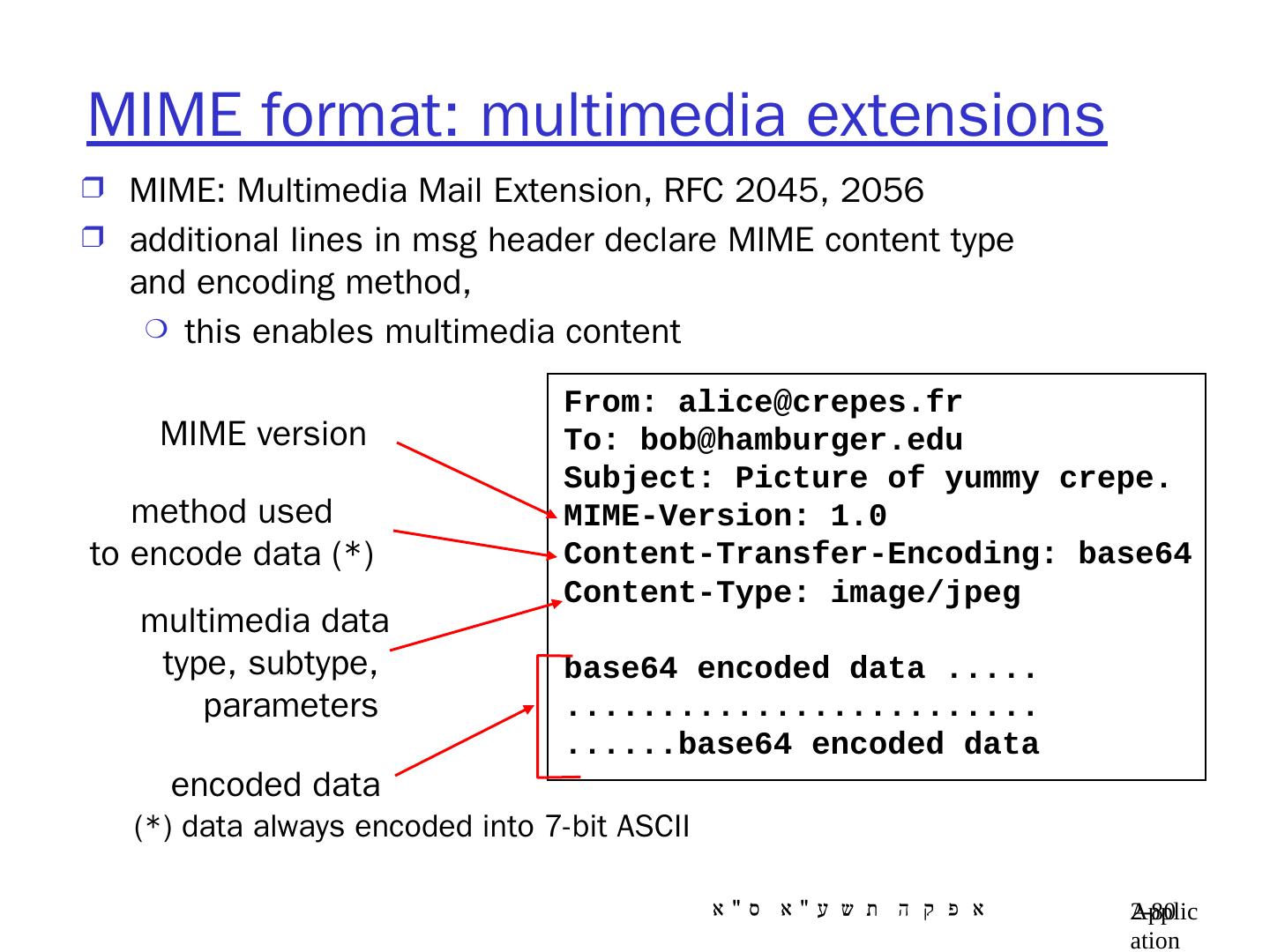
14 .Application Layer 8- 14 Web and HTTP First a review Web page consists of objects Object can be HTML file, JPEG image, Java applet, audio file, … Web page consists of base HTML-file which includes several referenced objects Each object is addressable by a URL Example URL: www.someschool.edu/someDept/pic.gif host name path name
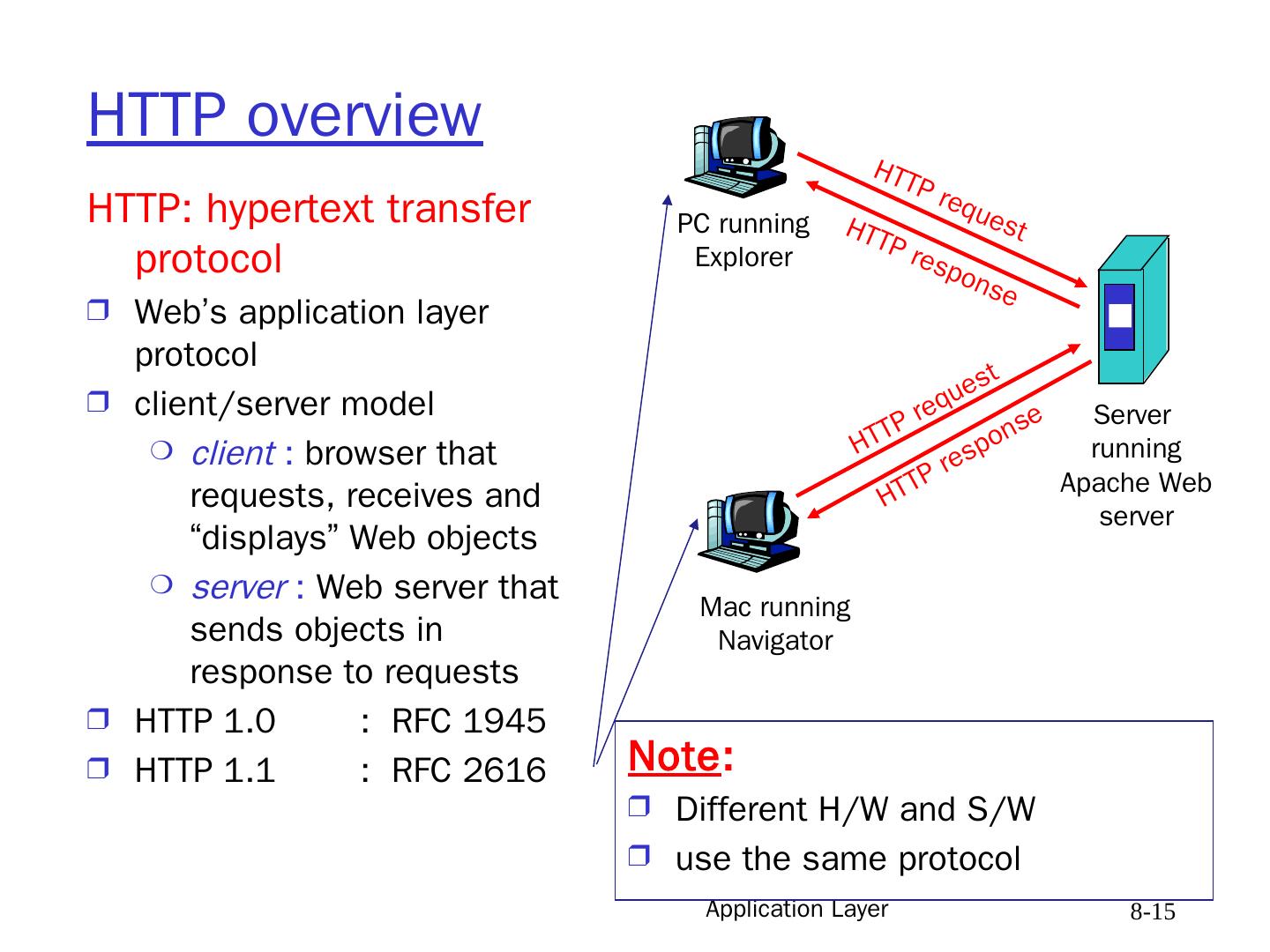
15 .Application Layer 8- 15 HTTP overview HTTP: hypertext transfer protocol Web’s application layer protocol client/server model client : browser that requests, receives and “displays” Web objects server : Web server that sends objects in response to requests HTTP 1.0 : RFC 1945 HTTP 1.1 : RFC 2616 PC running Explorer Server running Apache Web server Mac running Navigator HTTP request HTTP request HTTP response HTTP response Note : Different H/W and S/W use the same protocol
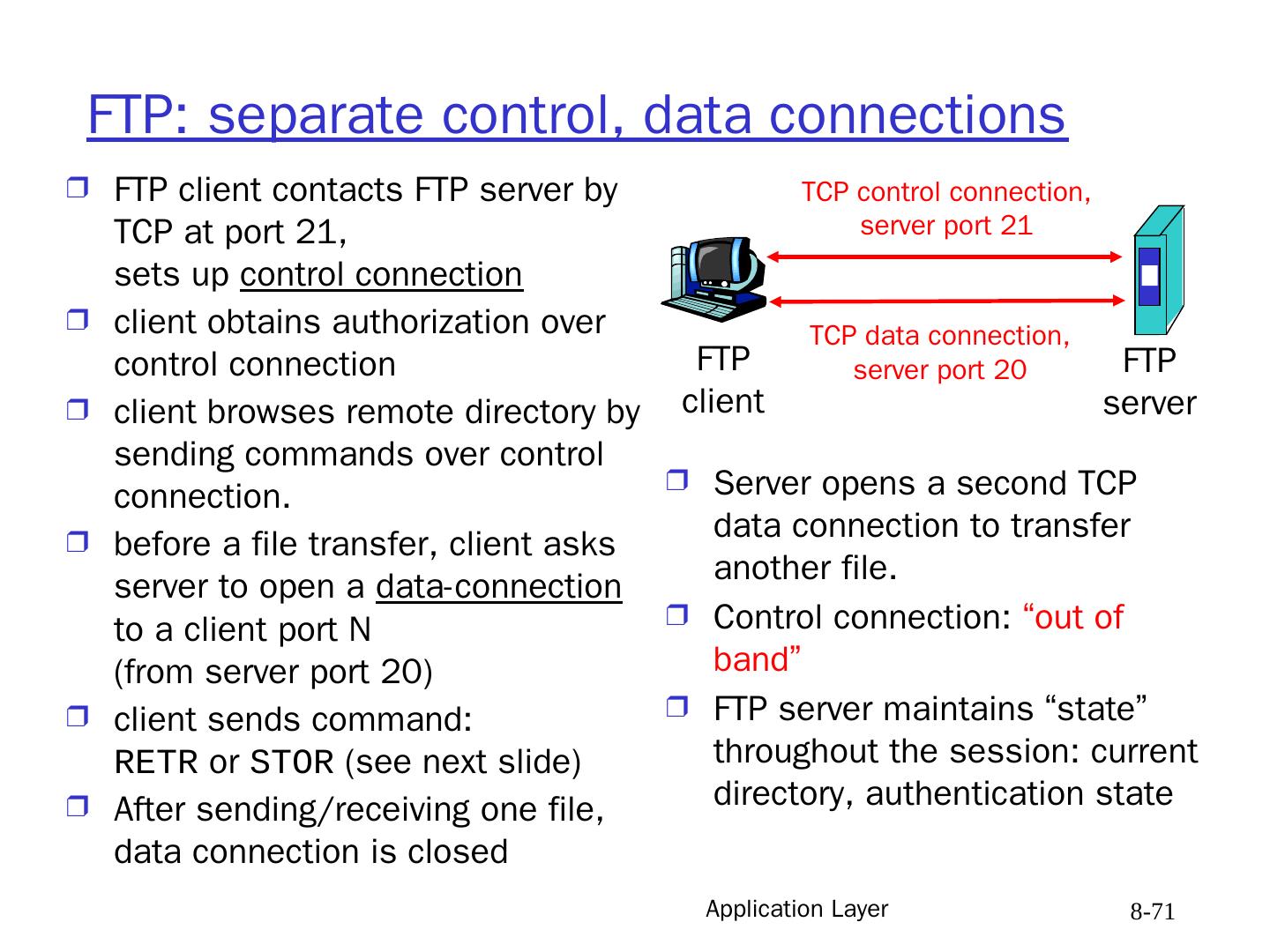
16 .Application Layer 8- 16 HTTP overview (continued) HTTP uses TCP: client initiates TCP connection (creates socket) to server port 80 (WKP) server accepts TCP connection from client HTTP messages (application-layer protocol messages) exchanged between browser (HTTP client) and Web server (HTTP server) TCP connection closed HTTP is “stateless” HTTP keeps no information about past client requests BUT, cookies allow Web server to run stateful applications Protocols that maintain “state” are complex! past history (state) must be maintained if server/client crashes, their views of “state” may be inconsistent, must be reconciled note
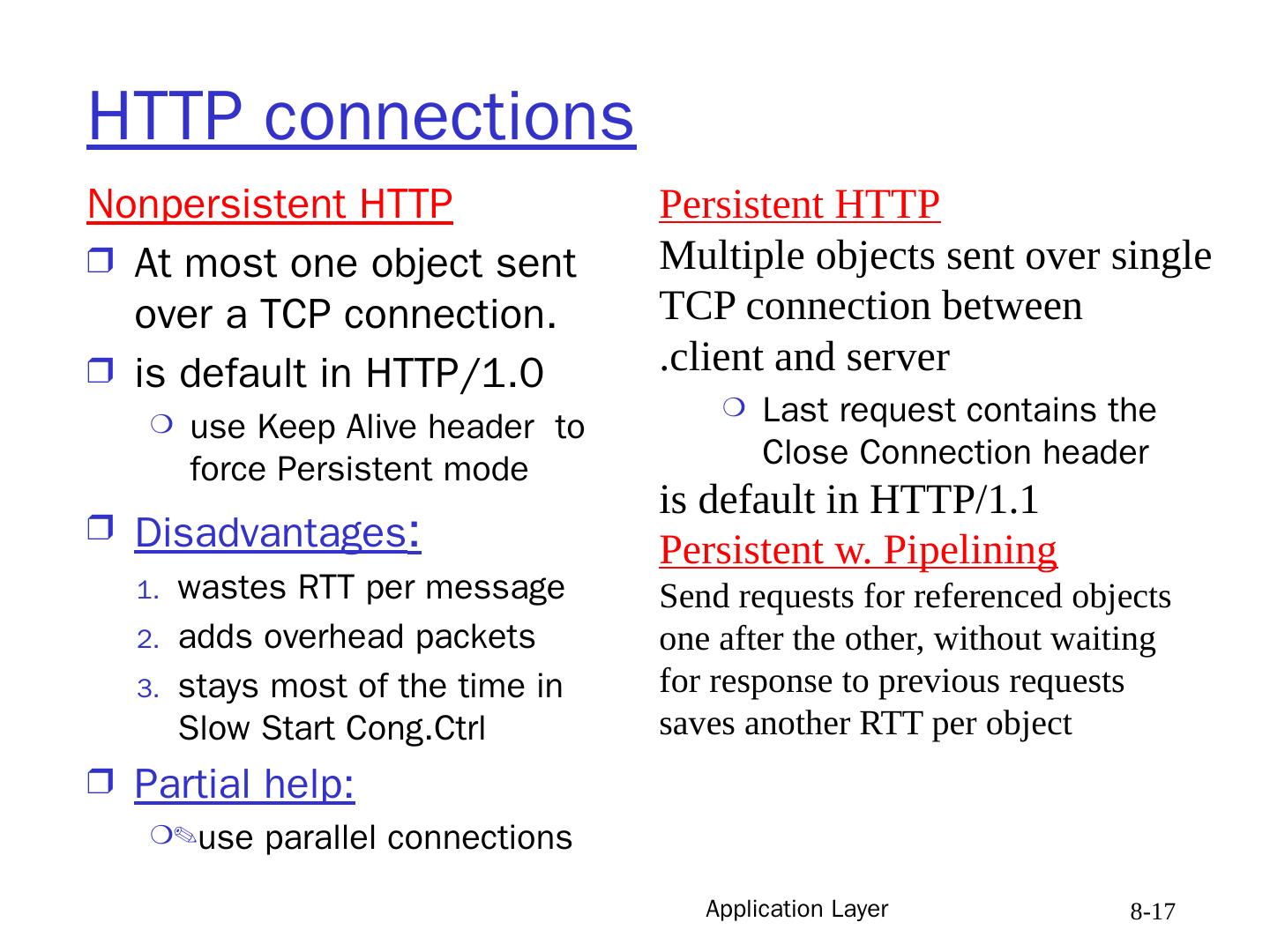
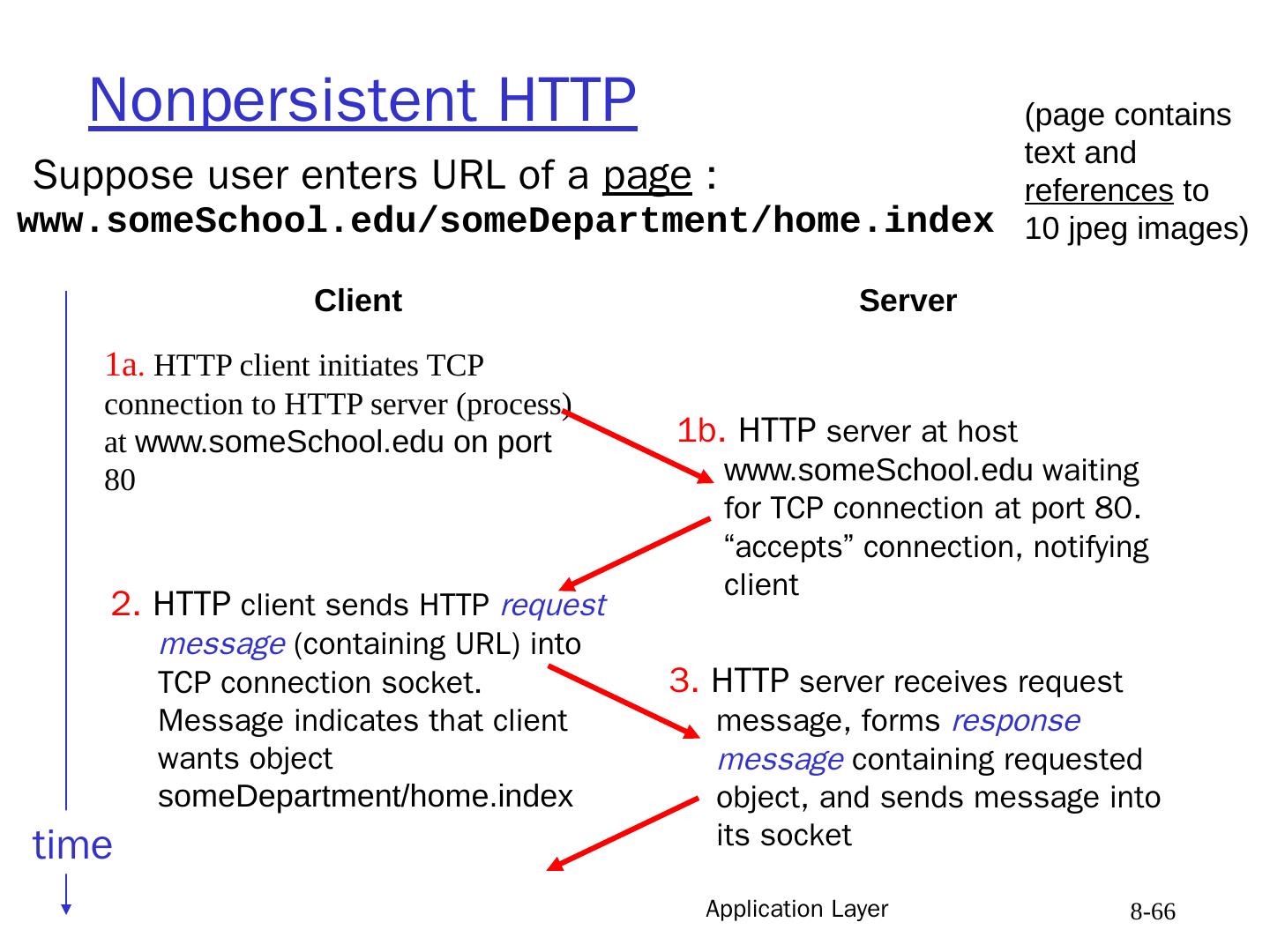
17 .Application Layer 8- 17 HTTP connections Nonpersistent HTTP At most one object sent over a TCP connection. is default in HTTP/1.0 use Keep Alive header to force Persistent mode Disadvantages : wastes RTT per message adds overhead packets stays most of the time in Slow Start Cong.Ctrl Partial help: use parallel connections Persistent HTTP Multiple objects sent over single TCP connection between client and server. Last request contains the Close Connection header is default in HTTP/1.1 Persistent w. Pipelining Send requests for referenced objects one after the other, without waiting for response to previous requests saves another RTT per object
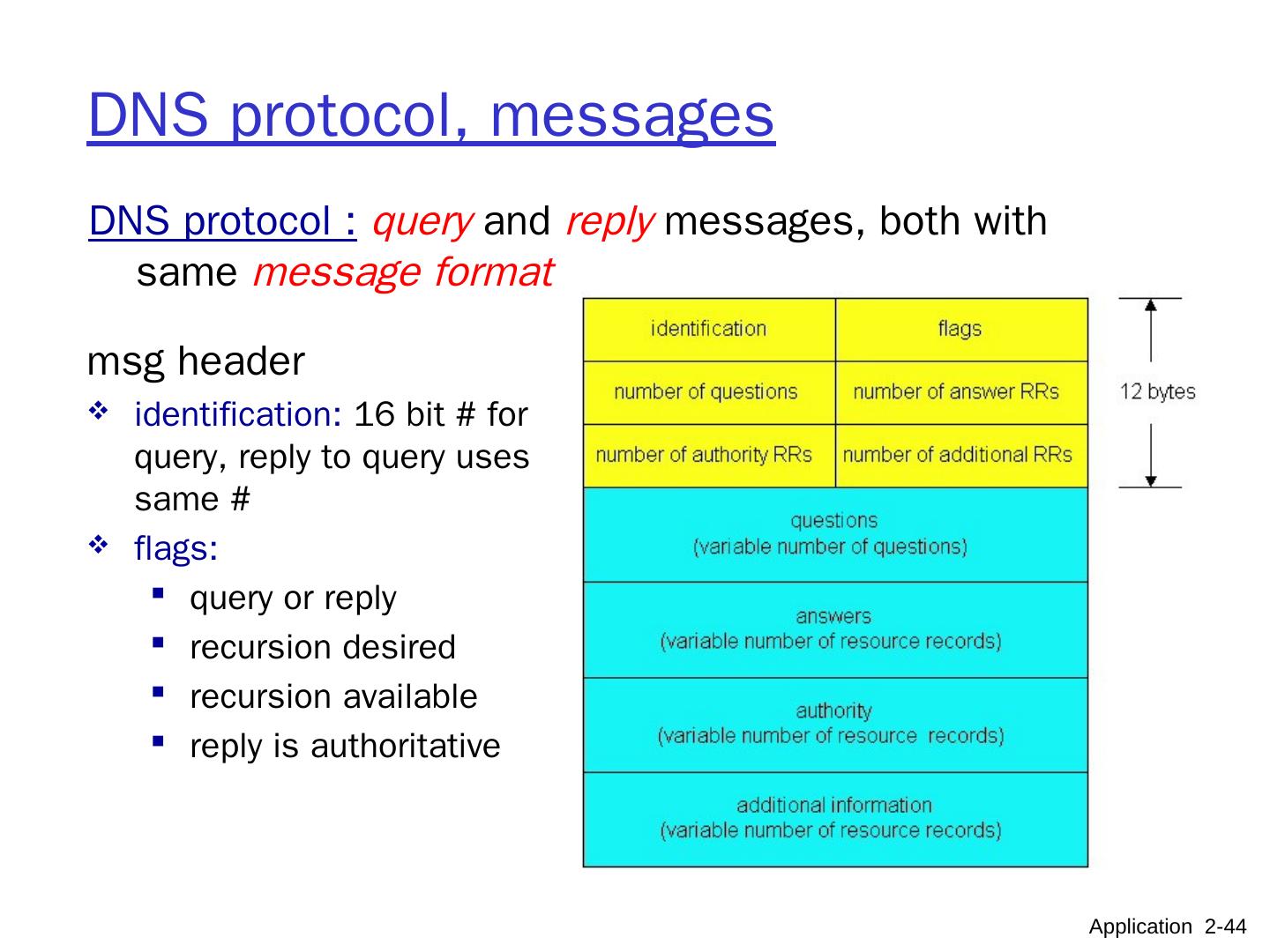
18 .GET /index.html HTTP/1.1 Host: www-net.cs.umass.edu User-Agent: Firefox/3.6.10 Accept: text/ html,application / xhtml+xml Accept-Language: en- us,en;q =0.5 Accept-Encoding: gzip,deflate Accept- Charset : ISO-8859-1,utf-8;q=0.7 Keep-Alive: 115 Connection: keep-alive Connection: Close carriage return, line feed at start of line indicates end of header lines HTTP request message two types of HTTP messages: request , response HTTP request message: ASCII (human-readable format) request line (GET, POST, HEAD commands) header lines Application 2- 18 carriage return character line-feed character
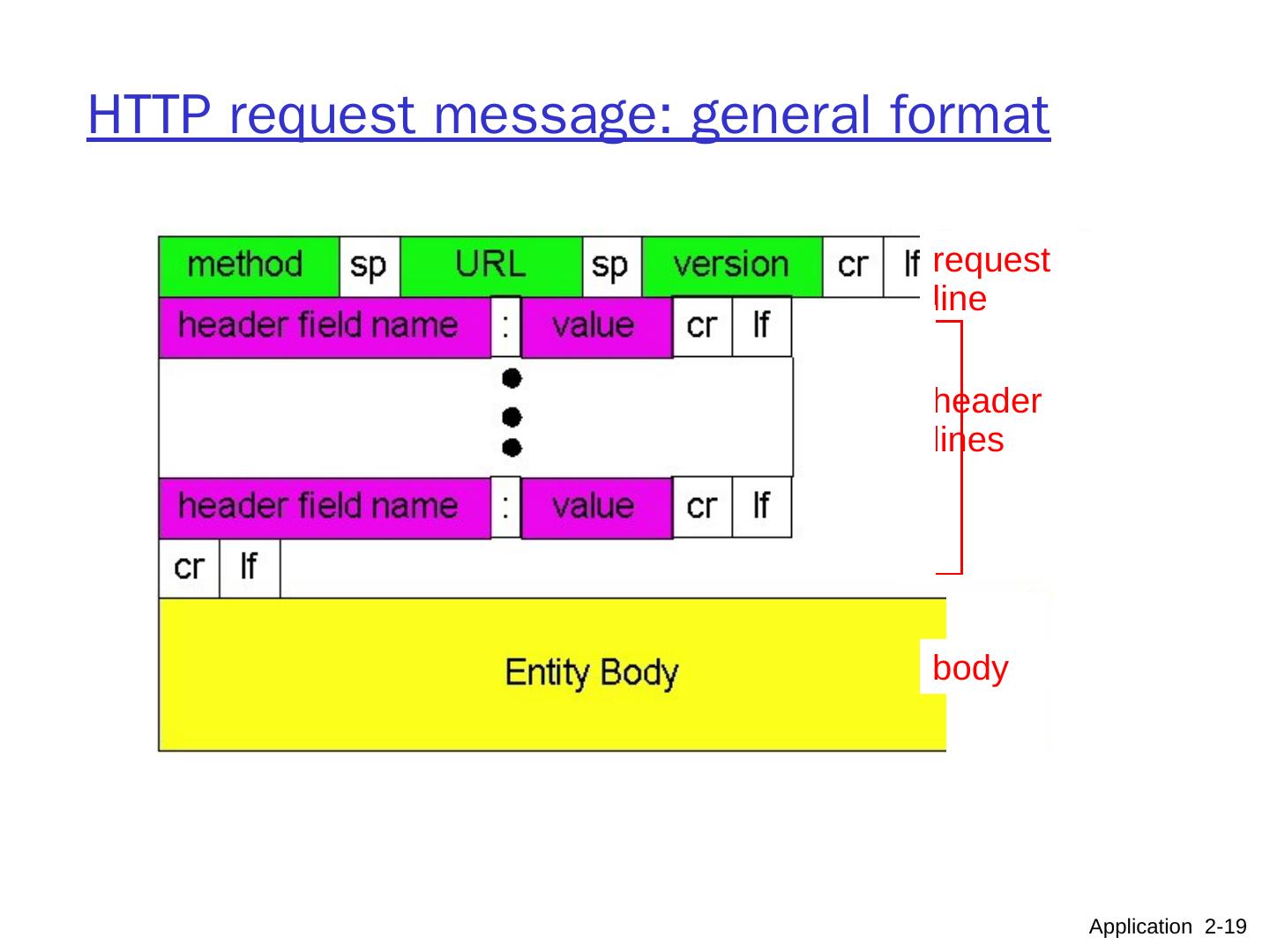
19 .HTTP request message: general format Application 2- 19 request line header lines body
20 .Uploading form input POST method: web page often includes form input input is uploaded to server in entity body GET method with URL parameters: uses GET method input is uploaded in URL field of request line: www.somesite.com/animalsearch?monkeys&banana Application 2- 20
21 .Application Layer 8- 21 Methods HTTP/1.0 GET POST HEAD asks server to leave requested object out of response Used for: debugging troubleshooting HTTP/1.1 GET, POST, HEAD PUT uploads file in the entity body to the path specified in URL field DELETE deletes file specified in the URL field
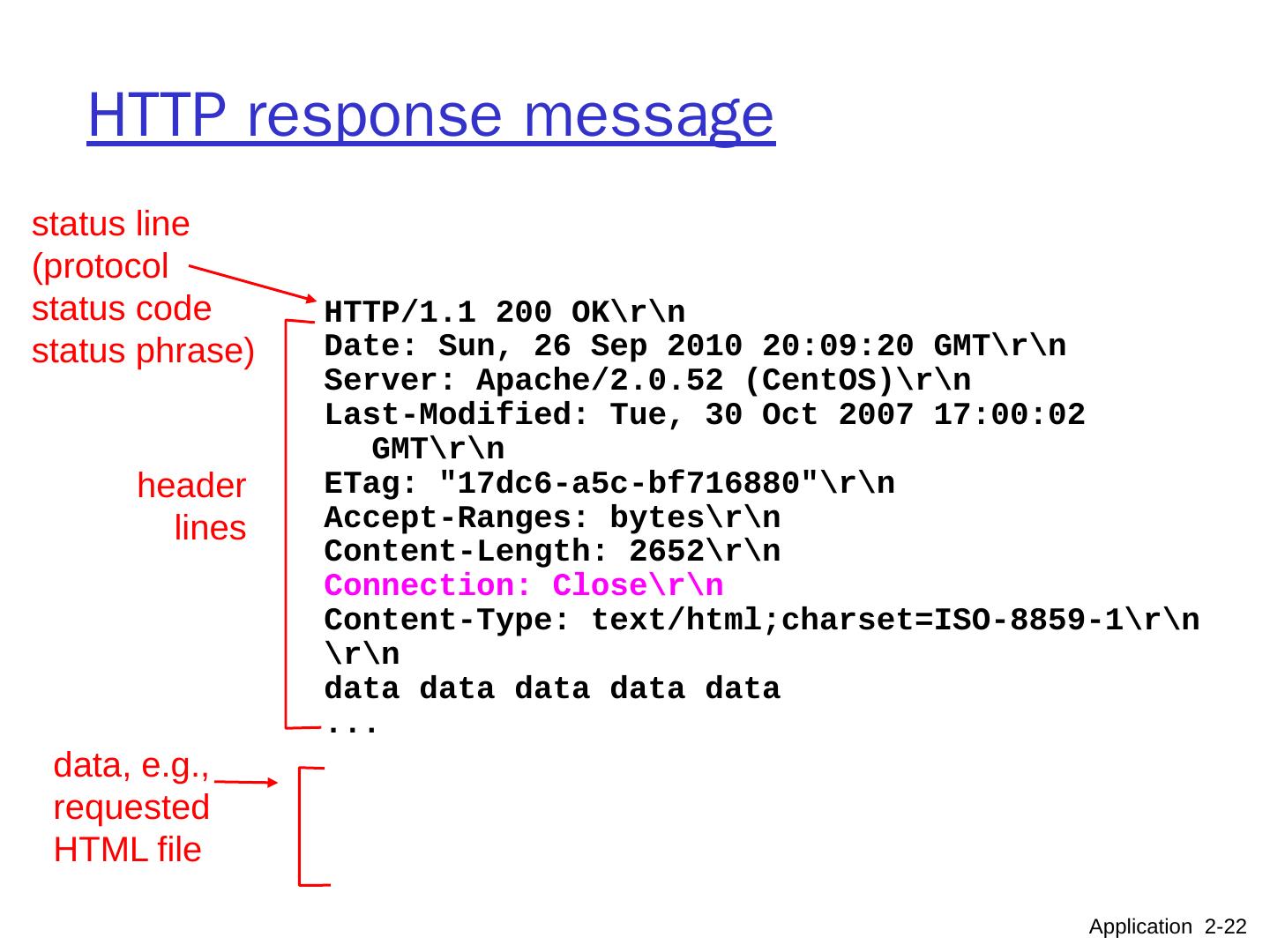
22 .HTTP response message status line (protocol status code status phrase) header lines data, e.g., requested HTML file Application 2- 22 HTTP/1.1 200 OK Date: Sun, 26 Sep 2010 20:09:20 GMT Server: Apache/2.0.52 ( CentOS ) Last-Modified: Tue, 30 Oct 2007 17:00:02 GMT ETag : "17dc6-a5c-bf716880" Accept-Ranges: bytes Content-Length: 2652 Connection: Close Content-Type : text/ html;charset =ISO-8859-1 data data data data data ...
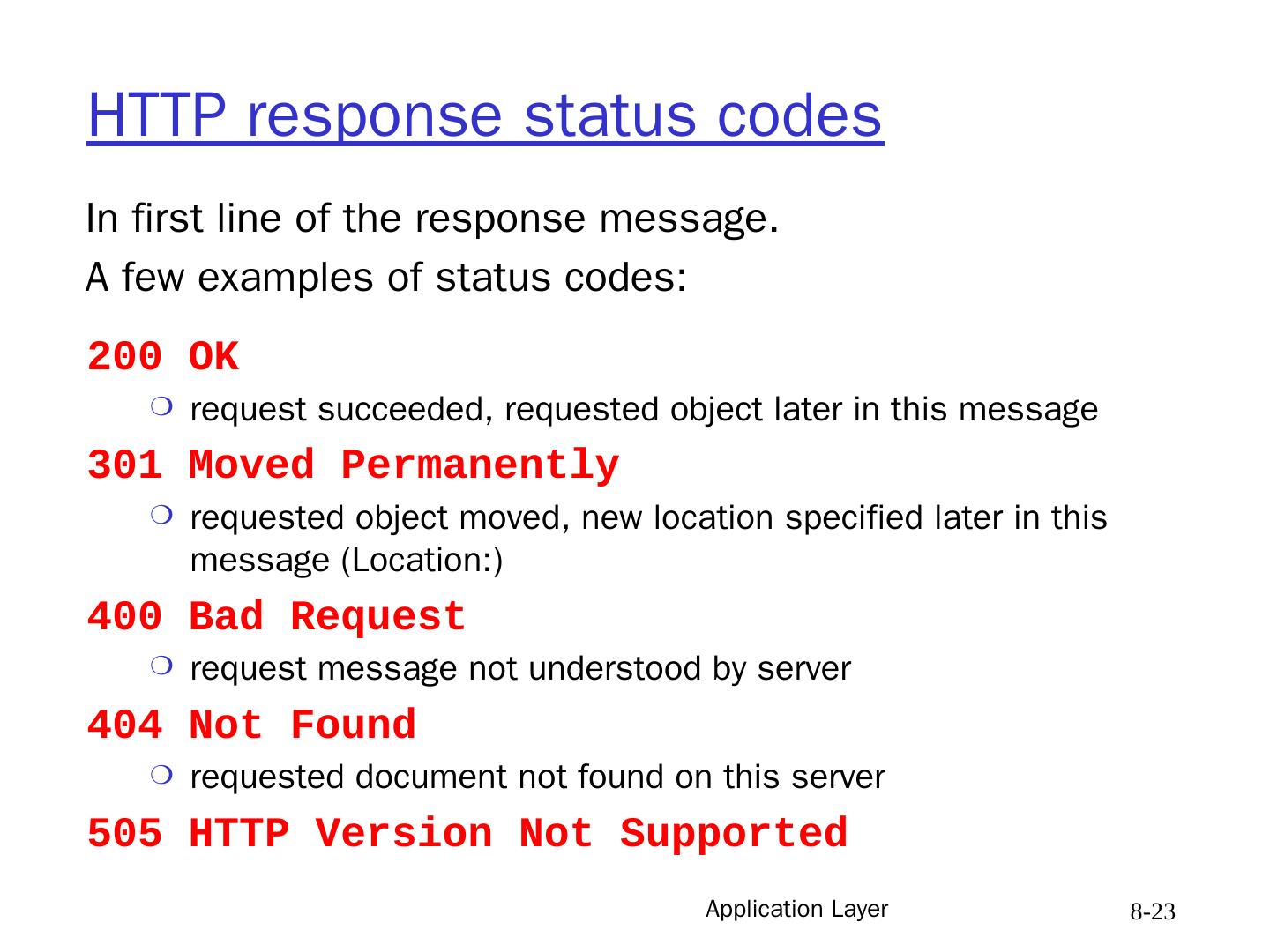
23 .Application Layer 8- 23 HTTP response status codes 200 OK request succeeded, requested object later in this message 301 Moved Permanently requested object moved, new location specified later in this message (Location:) 400 Bad Request request message not understood by server 404 Not Found requested document not found on this server 505 HTTP Version Not Supported In first line of the response message. A few examples of status codes:
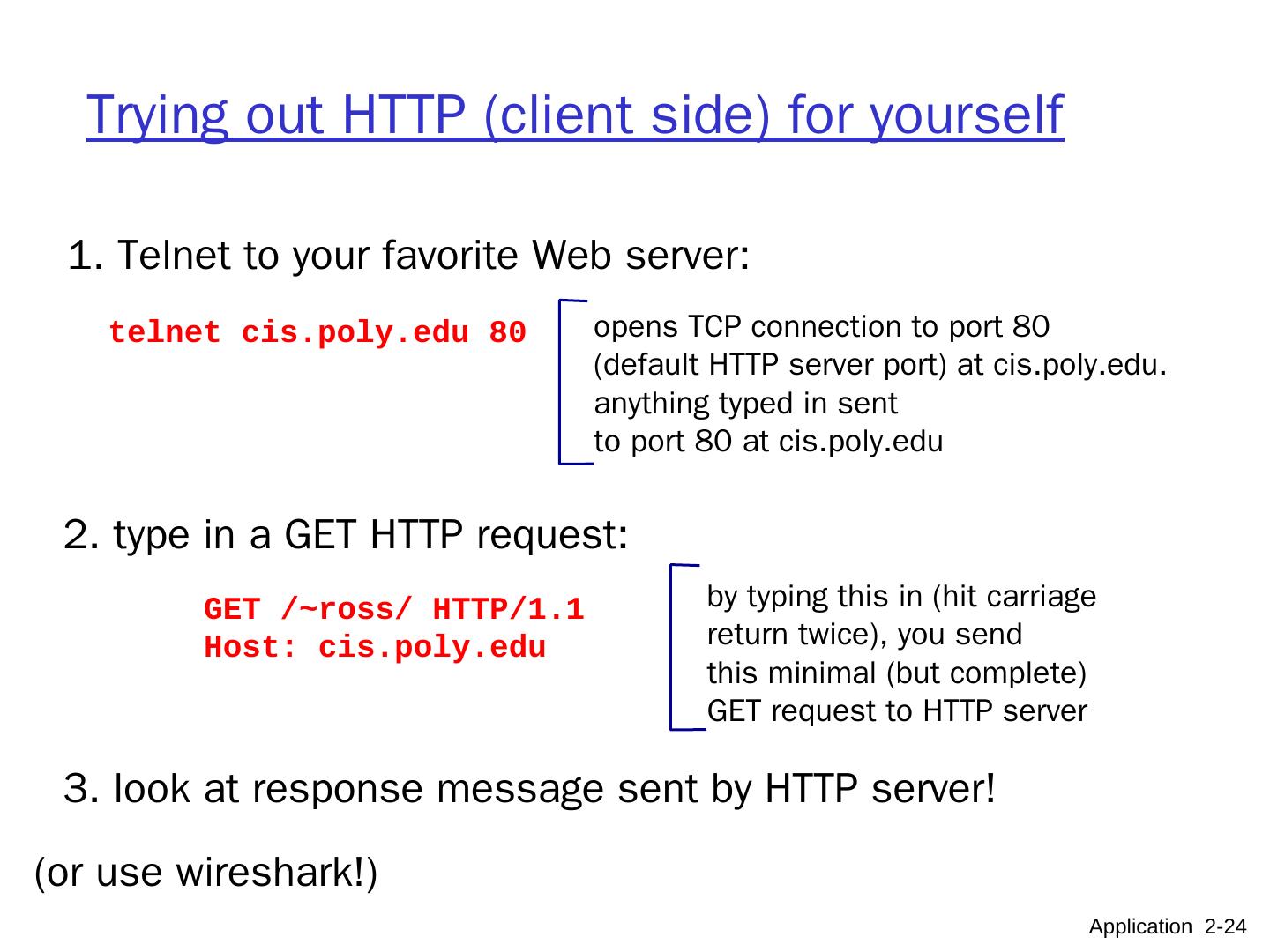
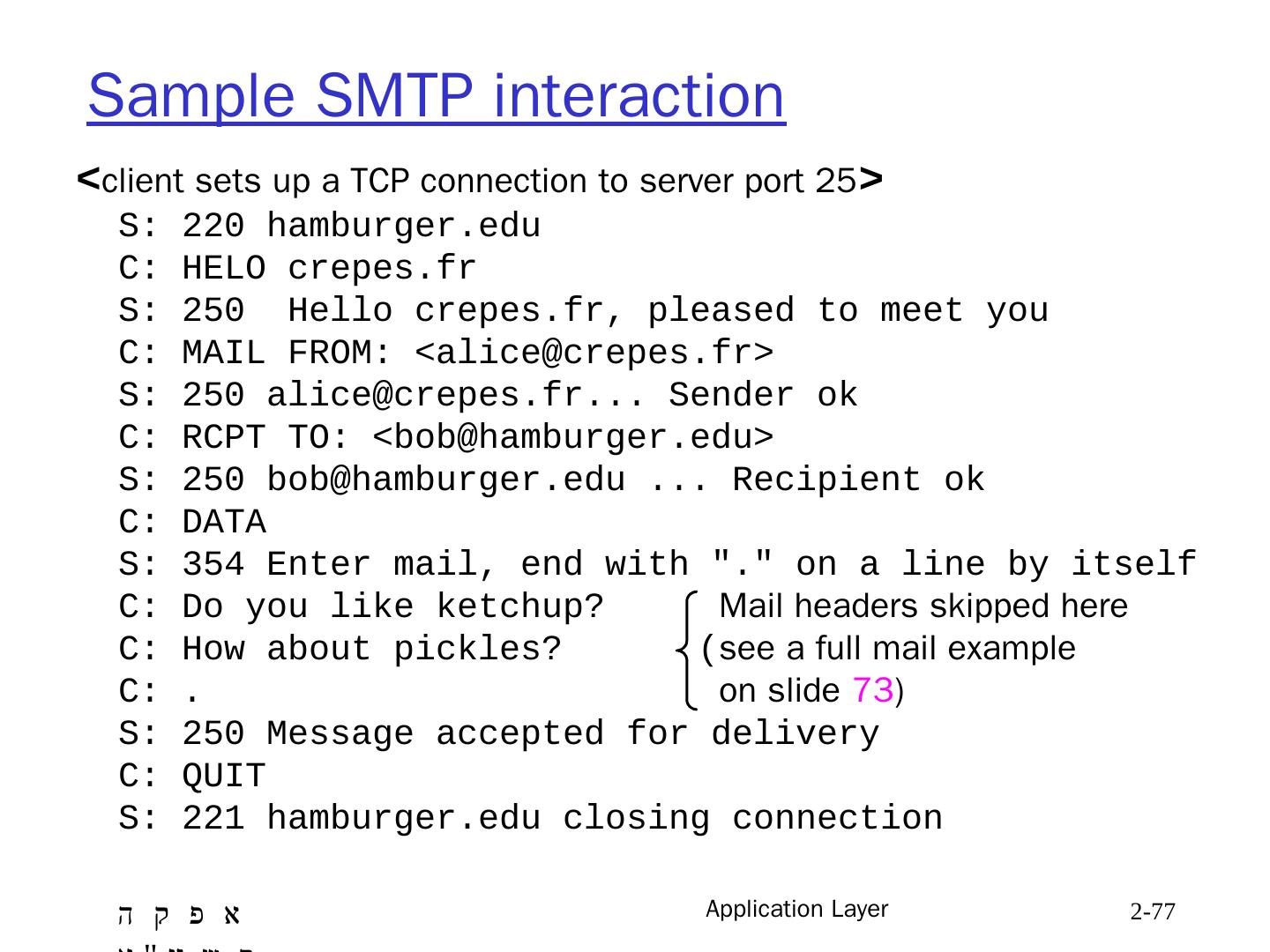
24 .Trying out HTTP (client side) for yourself 1. Telnet to your favorite Web server: opens TCP connection to port 80 (default HTTP server port) at cis.poly.edu. anything typed in sent to port 80 at cis.poly.edu telnet cis.poly.edu 80 2. type in a GET HTTP request: GET /~ross/ HTTP/1.1 Host: cis.poly.edu by typing this in (hit carriage return twice), you send this minimal (but complete) GET request to HTTP server 3. look at response message sent by HTTP server! Application 2- 24 (or use wireshark!)
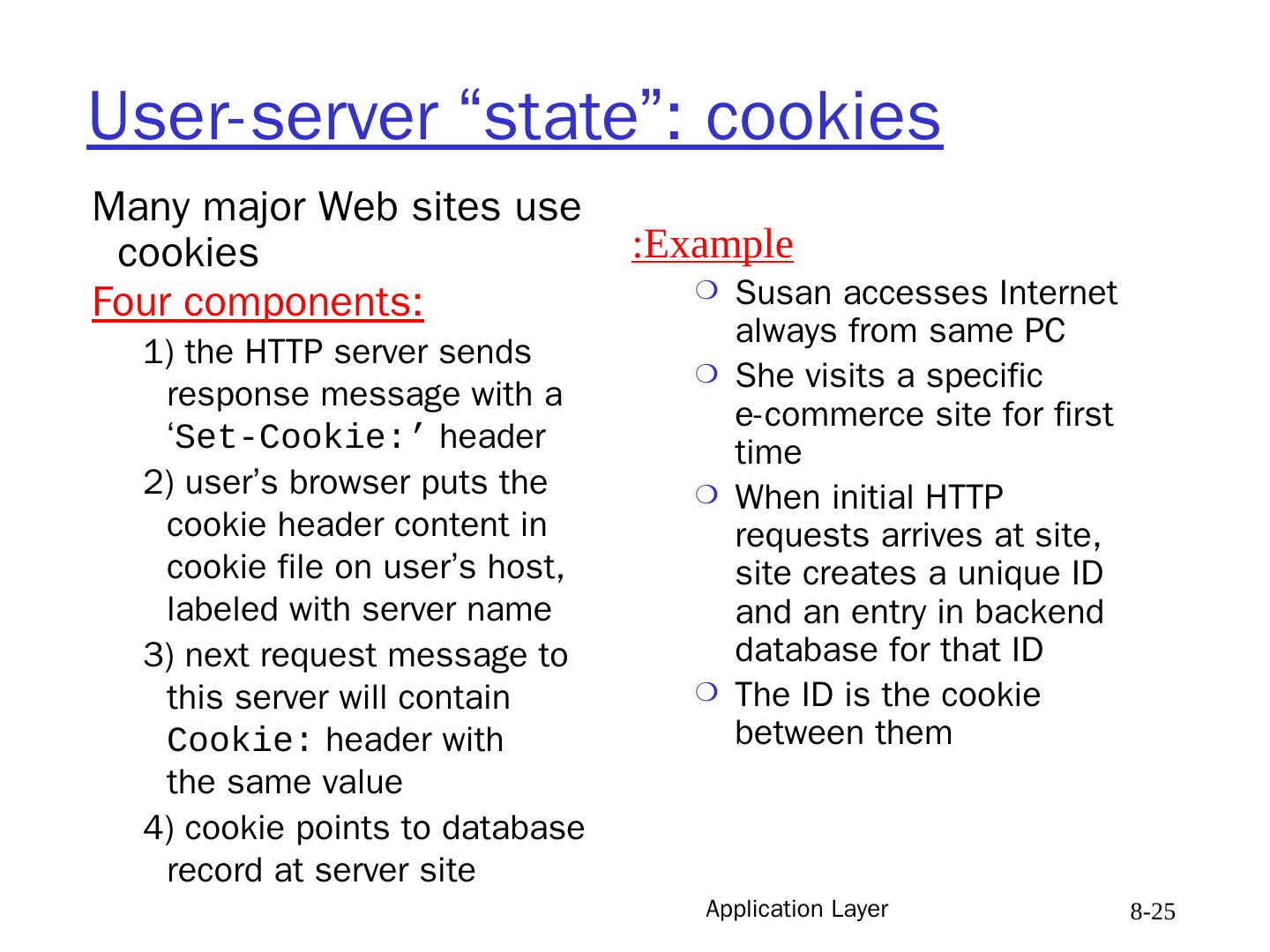
25 .Application Layer 8- 25 User-server “state”: cookies Many major Web sites use cookies Four components: 1) the HTTP server sends response message with a ‘ Set-Cookie:’ header 2) user’s browser puts the cookie header content in cookie file on user’s host, labeled with server name 3) next request message to this server will contain Cookie: header with the same value 4) cookie points to database record at server site Example: Susan accesses Internet always from same PC She visits a specific e-commerce site for first time When initial HTTP requests arrives at site, site creates a unique ID and an entry in backend database for that ID The ID is the cookie between them
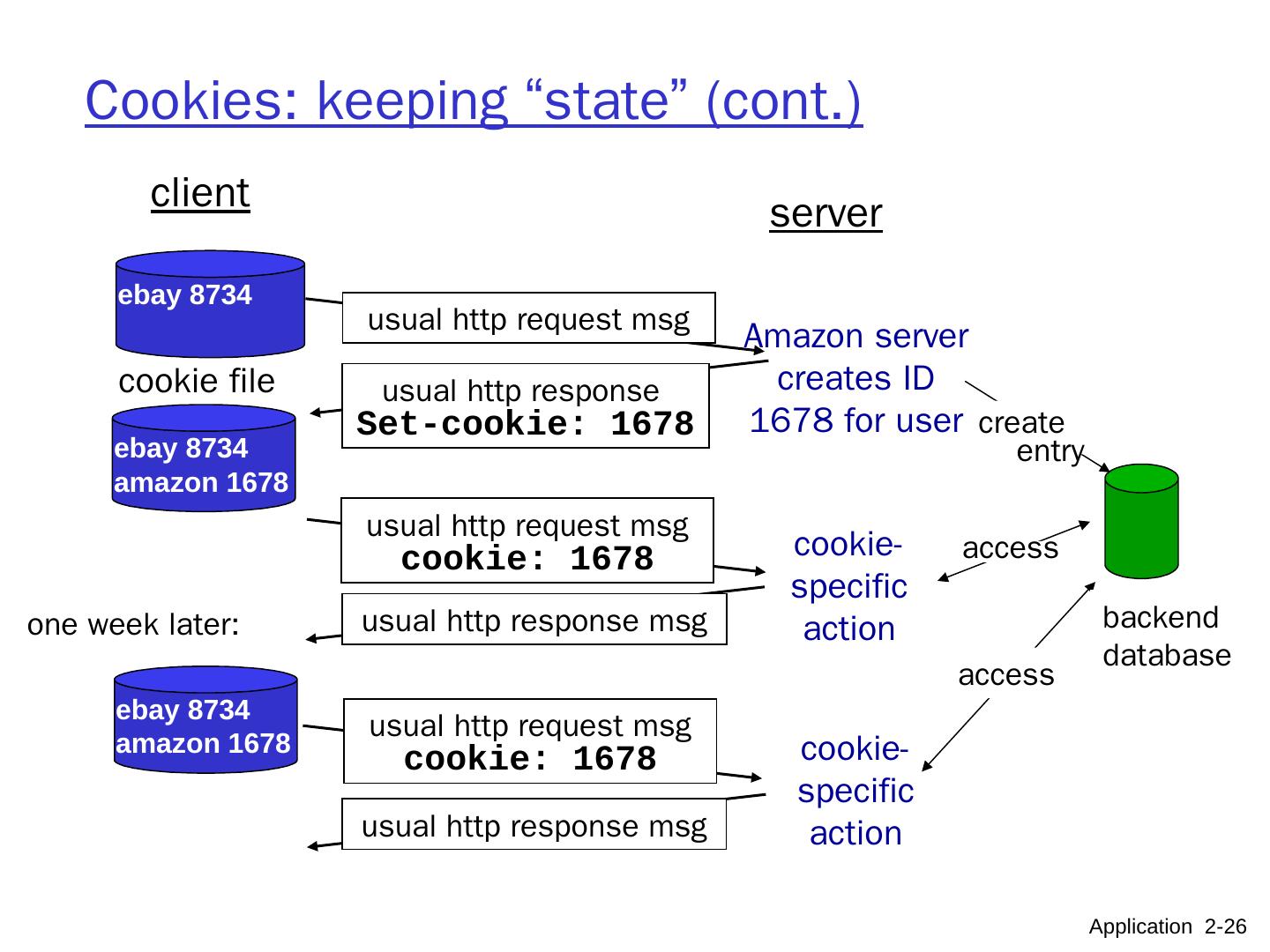
26 .Cookies: keeping “state” (cont.) client server usual http response msg usual http response msg cookie file one week later: usual http request msg cookie: 1678 cookie- specific action access ebay 8734 usual http request msg Amazon server creates ID 1678 for user create entry usual http response Set-cookie: 1678 ebay 8734 amazon 1678 usual http request msg cookie: 1678 cookie- specific action access ebay 8734 amazon 1678 backend database Application 2- 26
27 .Application Layer 8- 27 Cookies (continued) What cookies can bring: user session state (e.g. in Web e-mail) user identification on given workstation shopping carts recommendations Cookies and privacy: cookies permit sites to learn a lot about you you may supply name and e-mail to sites advertising companies obtain info across sites from inserted banner adds info collected by the advertizing server there are regulatory restrictions on releasing it aside
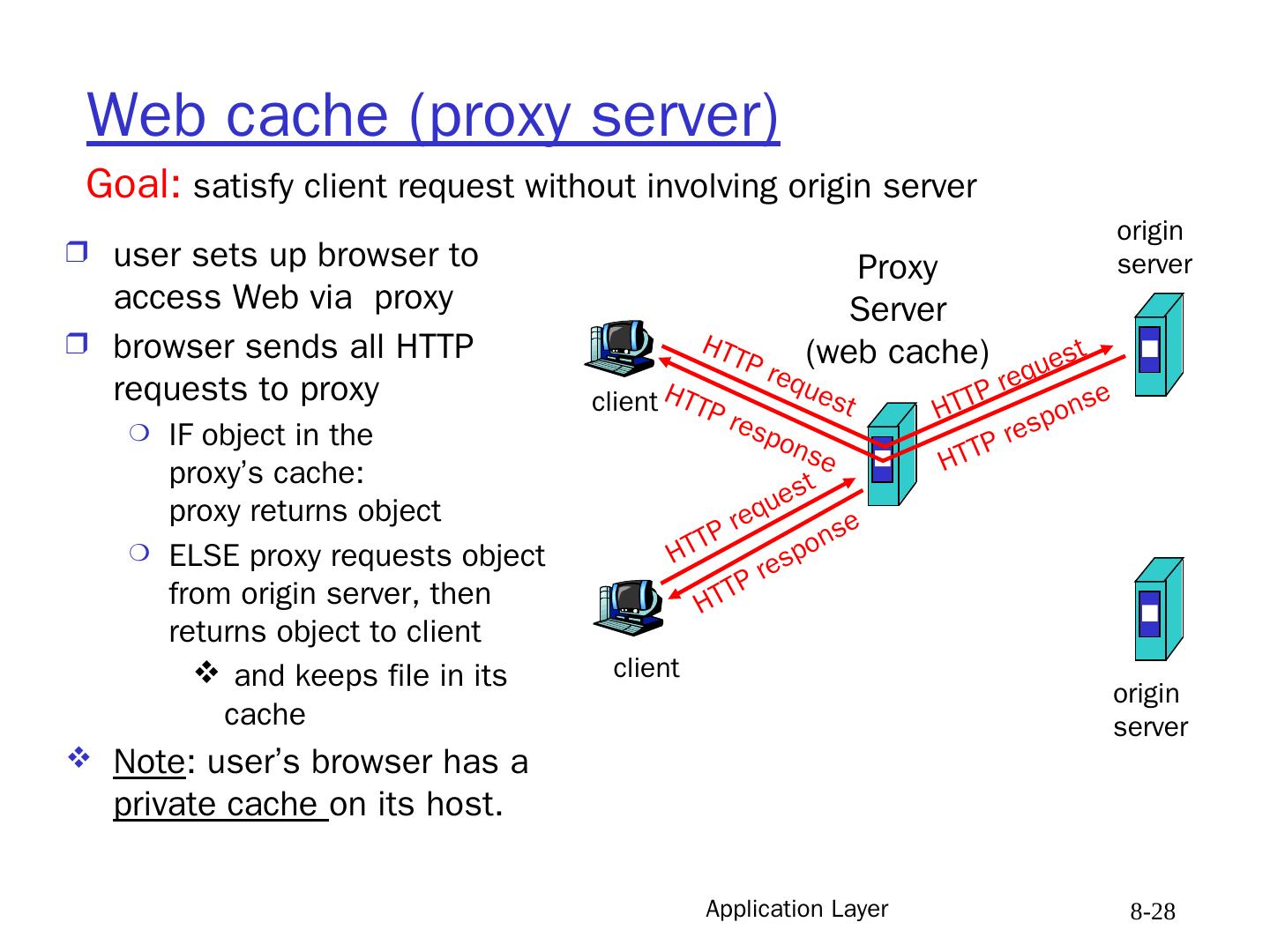
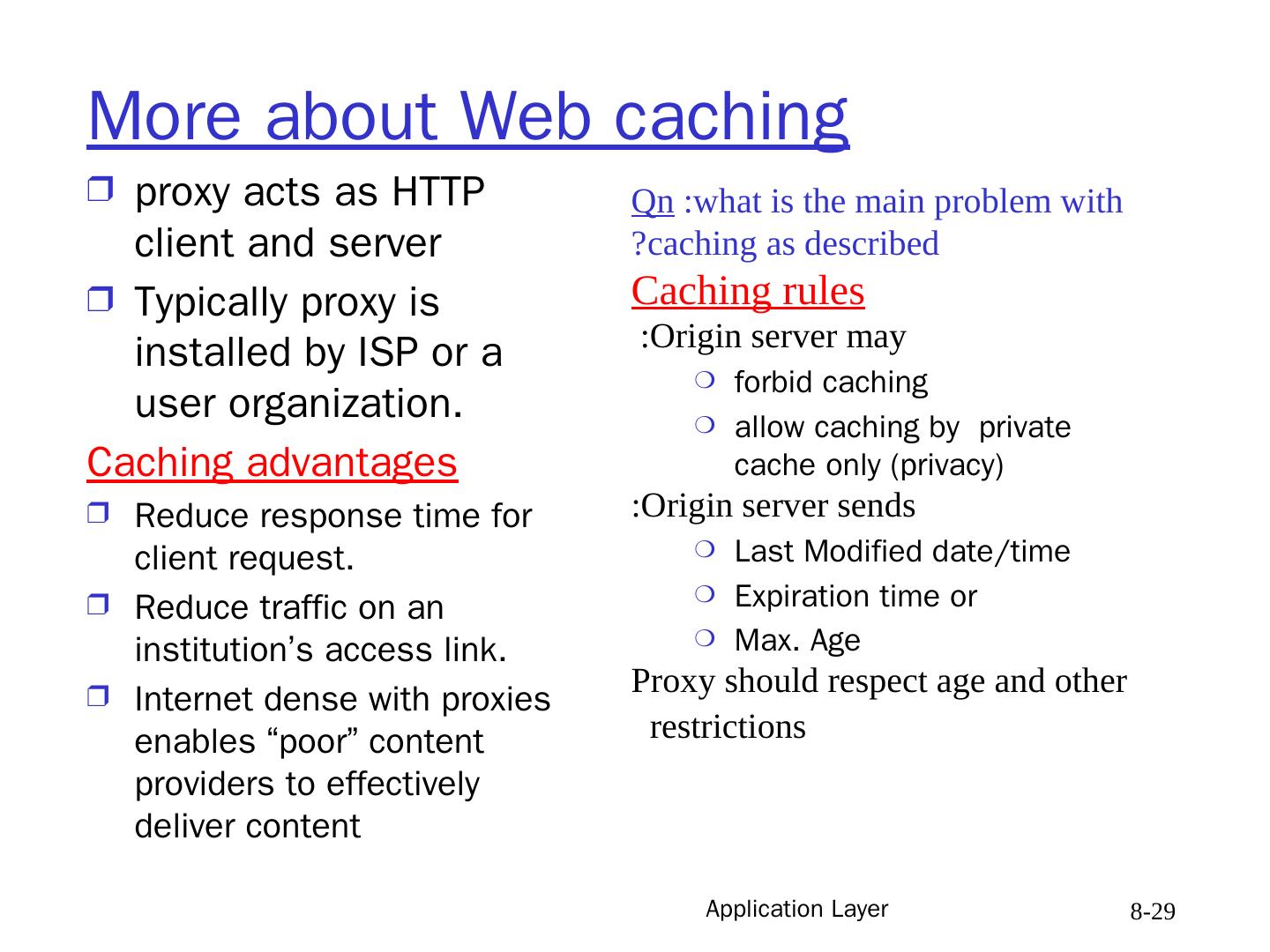
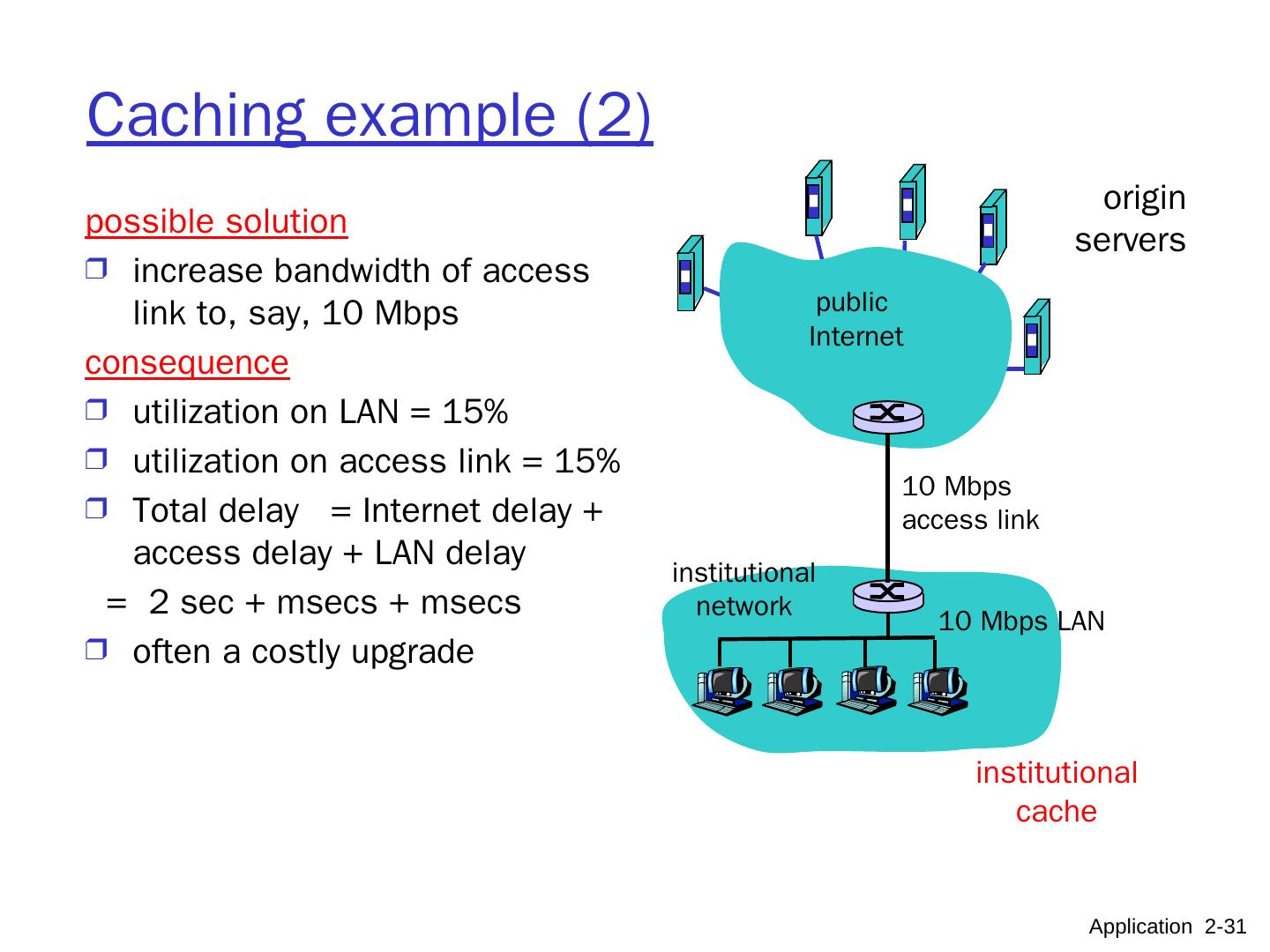
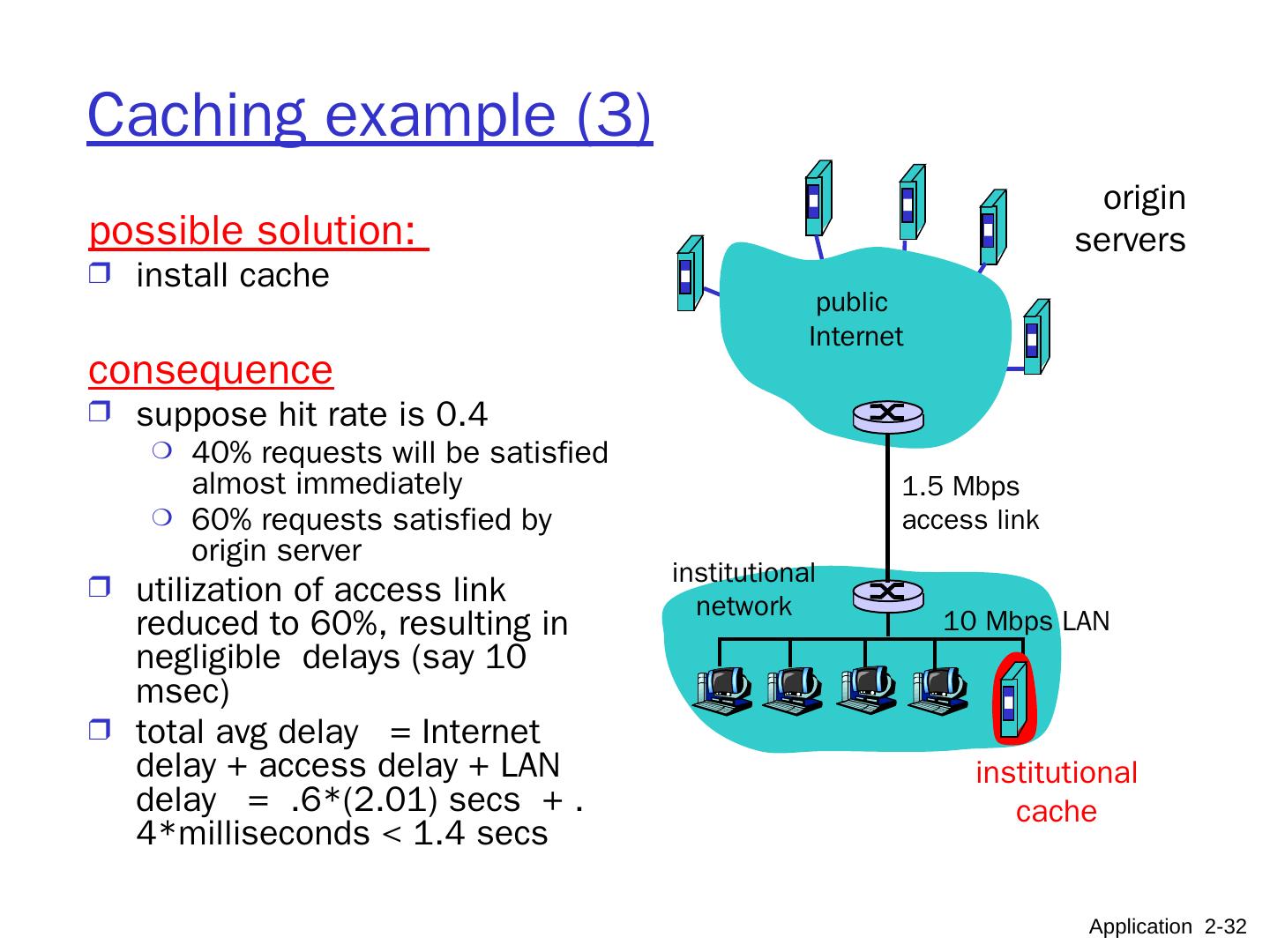
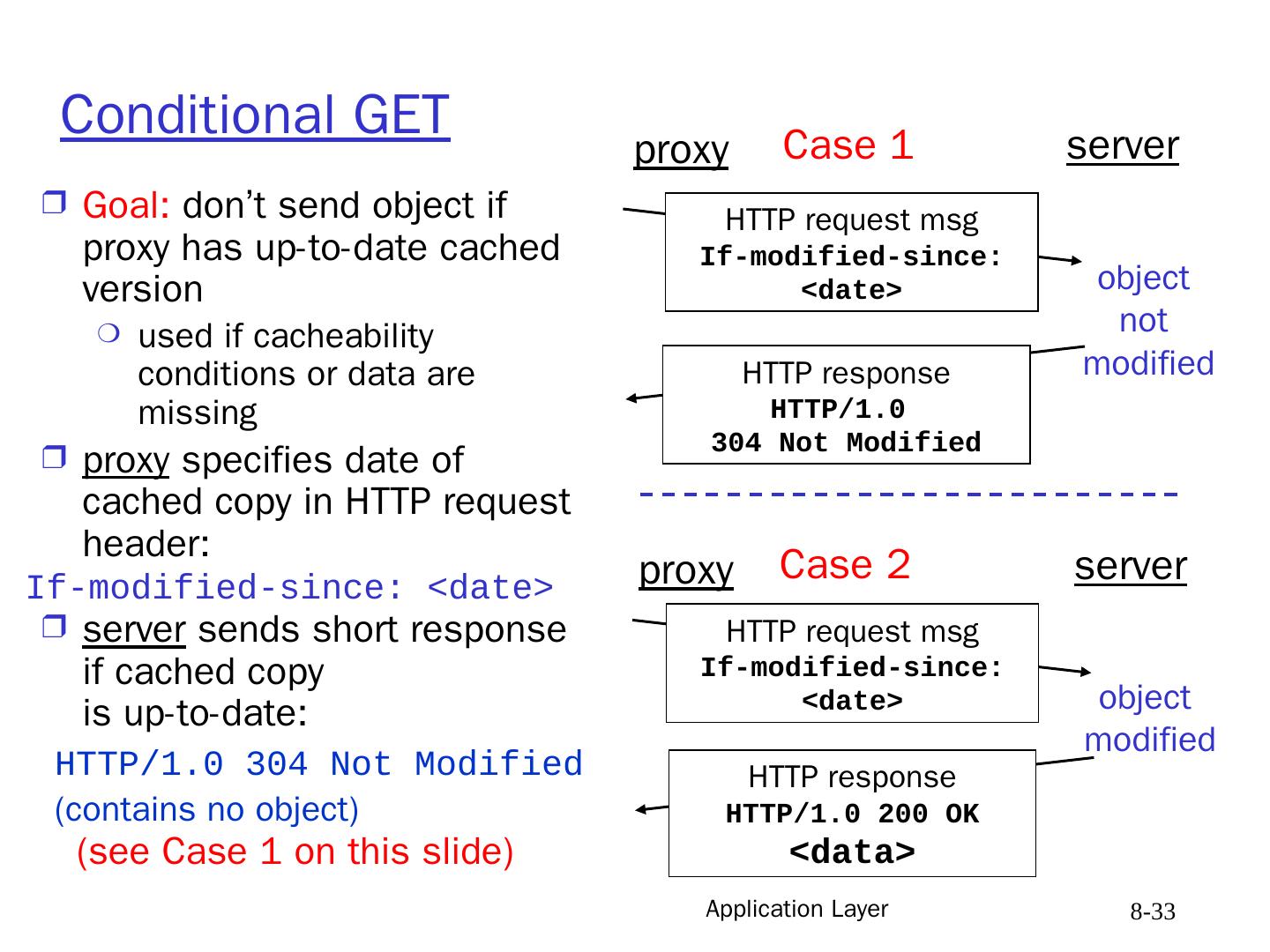
28 .Application Layer 8- 28 Web cache (proxy server) user sets up browser to access Web via proxy browser sends all HTTP requests to proxy IF object in the proxy’s cache: proxy returns object ELSE proxy requests object from origin server, then returns object to client and keeps file in its cache Note : user’s browser has a private cache on its host. Goal: satisfy client request without involving origin server client Proxy Server (web cache) client HTTP request HTTP request HTTP response HTTP response HTTP request HTTP response origin server origin server
29 .Application Layer 8- 29 More about Web caching proxy acts as HTTP client and server Typically proxy is installed by ISP or a user organization. Caching advantages Reduce response time for client request. Reduce traffic on an institution’s access link. Internet dense with proxies enables “poor” content providers to effectively deliver content Qn :what is the main problem with caching as described? Caching rules Origin server may : forbid caching allow caching by private cache only (privacy) Origin server sends: Last Modified date/time Expiration time or Max. Age Proxy should respect age and other restrictions